Event Overview
GuLoader is a malicious software downloader written in VB language, and it often hosts the final malicious files on shared cloud storage services such as Google Drive, Microsoft OneDrive, and MediaFire, etc. The malicious software they often deliver includes LokiBot, Formbook, and Agent Tesla, etc. The GuLoader program itself has a very complex process and anti-features to prevent security personnel from analyzing it. In March of this year, during the severe period of the COVID-19 pandemic in China, Ma Lian had releasedSpreading through phishing emails on the topic of the 'COVID-19 pandemic'.Another article about this malicious software,The Gorgon APT organization also used the GuLoader malicious software downloader to distribute the Formbook spyware., and a comparative analysis of the two has been done, detailed in the links in the reference information.
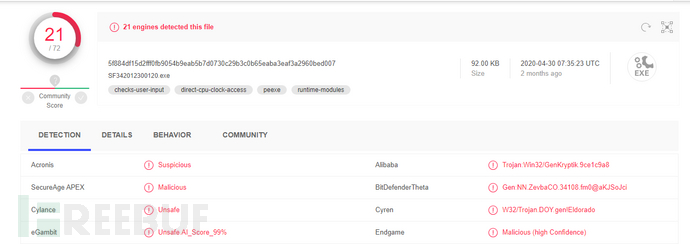
This sample was obtained earlier, but due to various things, I have not written any related articles to report it. There have been other security vendors that have analyzed and released information about this sample. Nevertheless, as Ma Lian believes that this event is still worth everyone's attention, this malicious program is still active and the detection rate is relatively low. In addition, this version of the GuLoader malicious software downloader has added some new anti-features compared to previous versions.

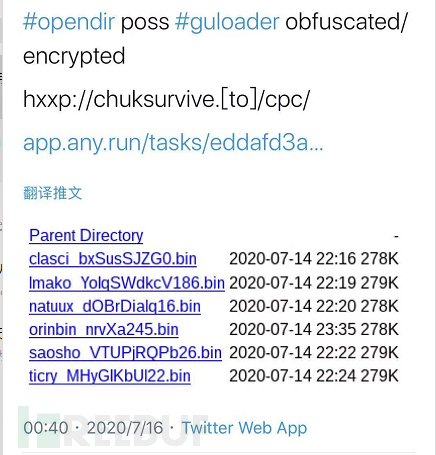
Event Analysis
The GuLoader malicious software downloader analyzed in this study was spread through phishing emails containing 'SF Express', mainly targeting Chinese users. The previous phishing emails related to the 'COVID-19' topic were all in English, mainly targeting English-speaking countries. This time's phishing email uses Chinese language and has obvious regional attacks.

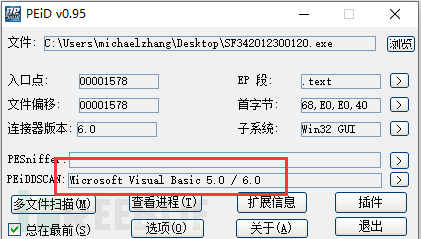
This sample still uses the executable file with the same icon as before, written in VB language. Specific information is as follows:
Dynamically allocate memory, copy the shellcode to the relevant area, and then jump to execute.
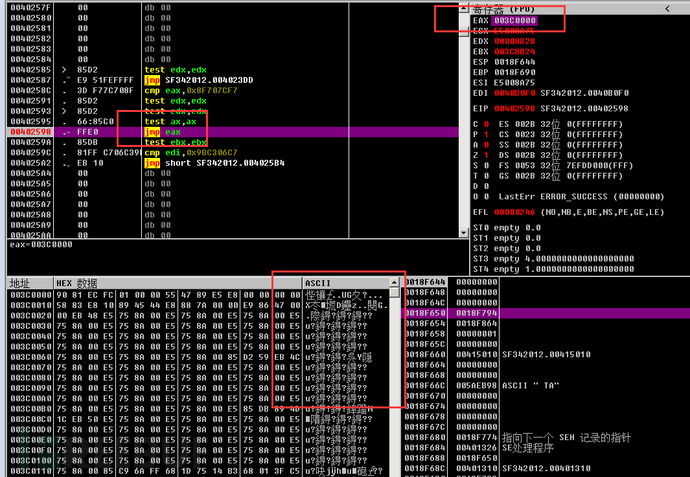
New Countermeasure Function
1. Use the ZwQueryVirtualMemory function to query the virtual memory, with the memory query area being 0x00001000~0x7FFFF000. If a string related to the virtualization environment is found in this memory, the process will be terminated.
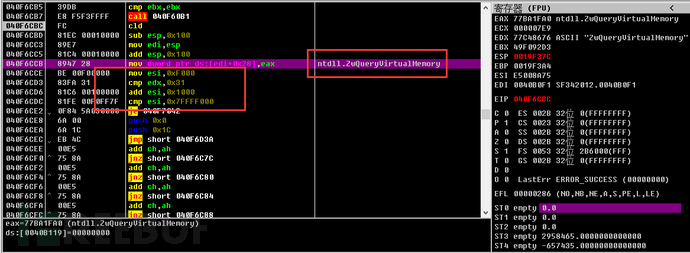
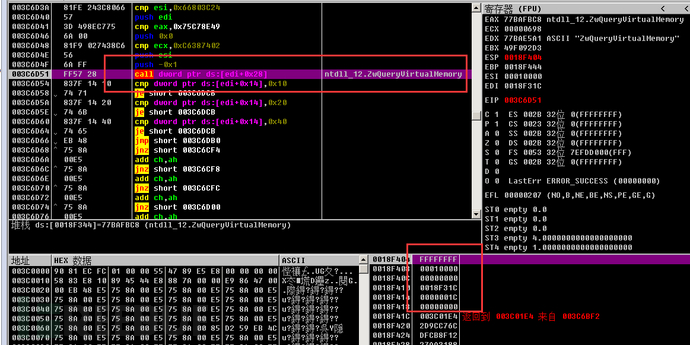
During the query process, query sequentially with memory alignment of 0x1000.
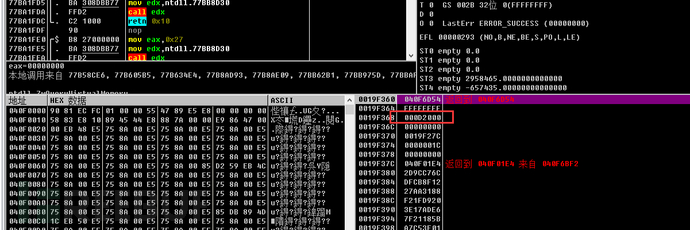
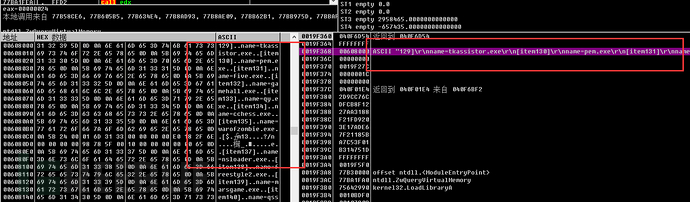 If found, it indicates that the virtual machine environment is present, and a string will be decrypted and provided for subsequent pop-up prompts.
If found, it indicates that the virtual machine environment is present, and a string will be decrypted and provided for subsequent pop-up prompts.
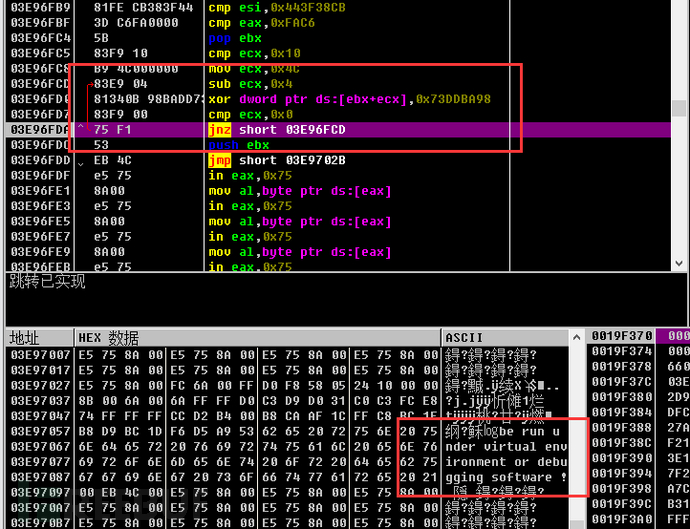
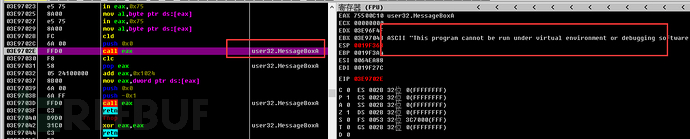
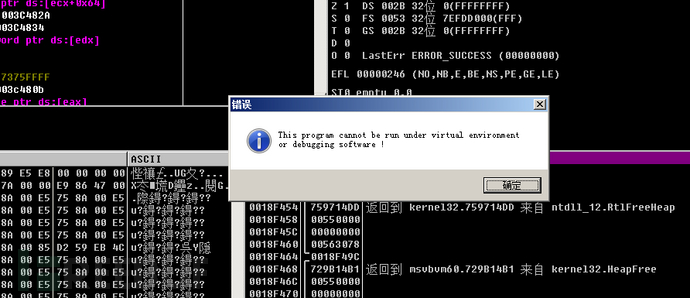
Then call the MessageBox function to pop up a prompt indicating that the program is running in a virtual machine environment, and finally end the process.
2. Enumerate the top-level window handle values, and if the value is less than 0x0C, the process will be terminated.
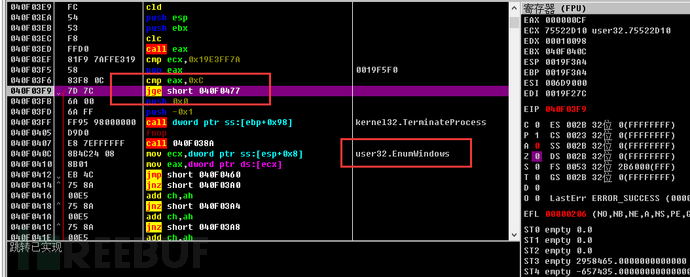
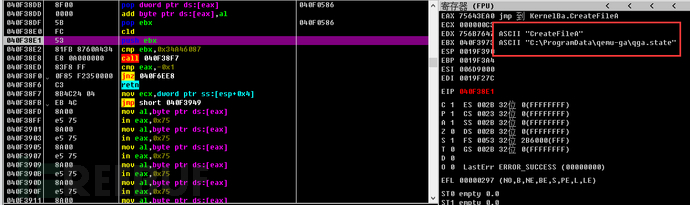
3. Detect Qemu environment by checking for the existence of related files through the CreateFile method.
Other Countermeasures Analysis(For detailed technical descriptions, please refer to the previous analysis articles, see the reference information section)
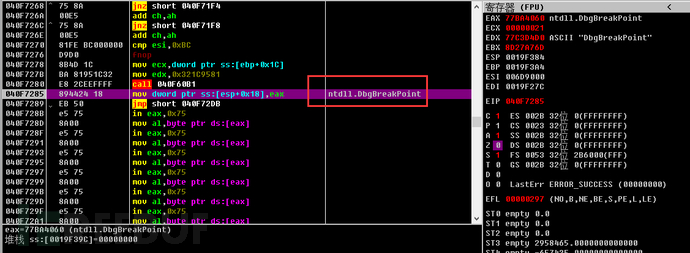
1. Modify the debugging-related function code to prevent additional analysis.
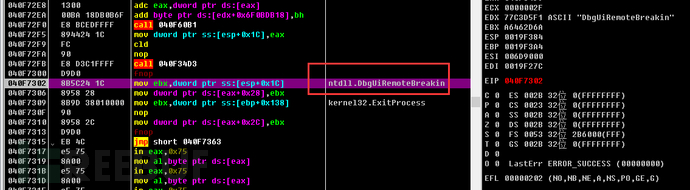
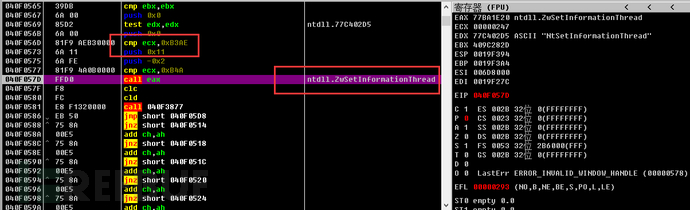
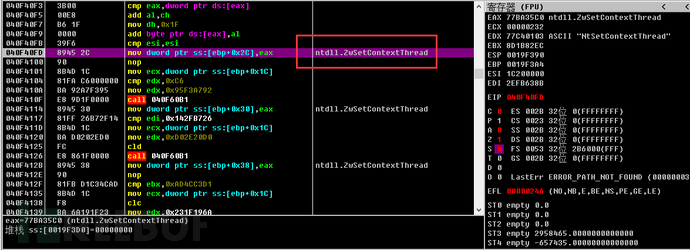
2. Set the parameters of the ZwSetInformationThread function to 0x11.
3. Multiple checks for hardware breakpoints.
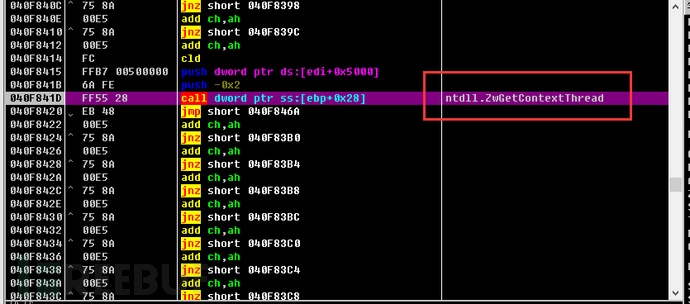
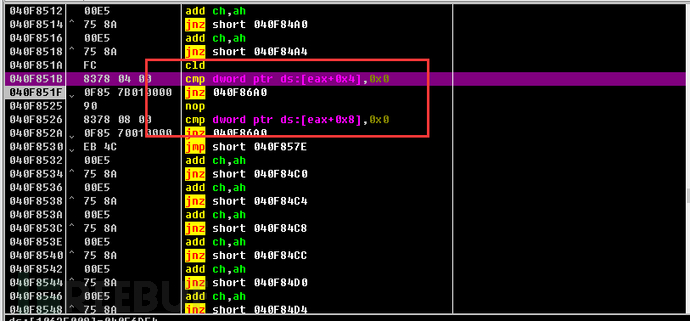
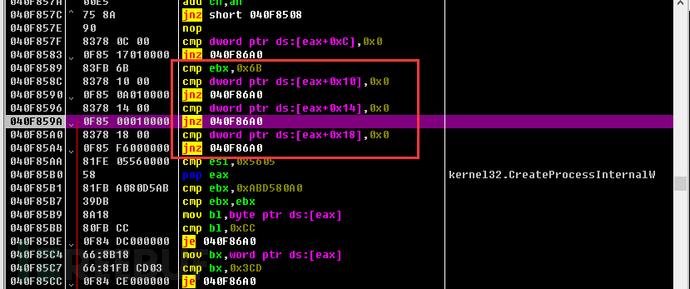
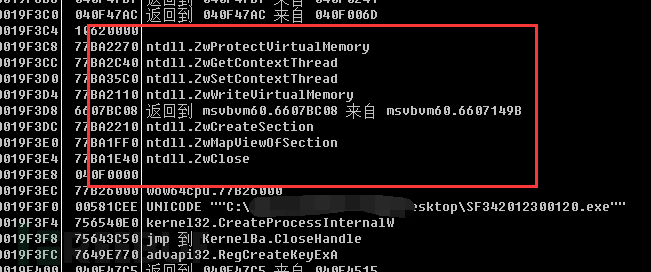
After all these tests are completed, injection operations will be performed, and then malicious software such as remote control trojans and spyware will be downloaded from the hosting site, which is the same as the functionality of the previous version of GuLoader.
Solution
1. Do not click on links and attachments in emails from unknown senders, especially those related to express delivery orders, order confirmation, or information confirmation, etc., which are particularly worth noting.
2. Timely upgrade the virus code version of security products to ensure timely detection and removal of related malicious software.
3. Regularly modify and strengthen your cloud disk password to prevent hackers from using your cloud disk.
Reference Information
Gorgon APT Group in Action: From Google Drive to Formbook Spyware
Spreading FormBook Spyware by Using the Topic of the COVID-19 Pandemic
评论已关闭