Summary: This case mainly analyzes the abnormal internet access phenomena caused by the implantation of malicious programs in the ONU (Optical Network Unit) through a certain port, such as slow internet access perception, substandard speed test results, and being forcibly pushed ads, etc. Helping to locate faults by analyzing network packets and device log print information is currently an important means for troubleshooting ONU. Through logs, one can find out the operating status of the device and whether the processes are normal. By analyzing network packets, one can determine whether the network protocol is running normally and whether there is any abnormal traffic. In this example, it is through the log print information that it is found that the ONU has been implanted with a malicious program, thereby discovering that the ONU CPU is occupied, which prevents hardware acceleration and leads to phenomena such as substandard speed test results and slow internet access.
Keywords: ONU; CPU; Speed test not up to standard; TCP
I. Case Description
1. View and simple analysis of the problematic network topology

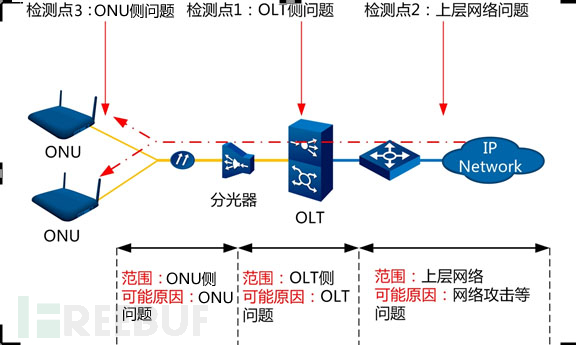
Figure 1 shows the basic network topology and simple analysis
2. Analysis of the cause, main key behavior measures
After analyzing the problematic ONU, it was found that there were several suspicious programs in the running process list, including /bin/init_mon, /bin/protect, and ssk.
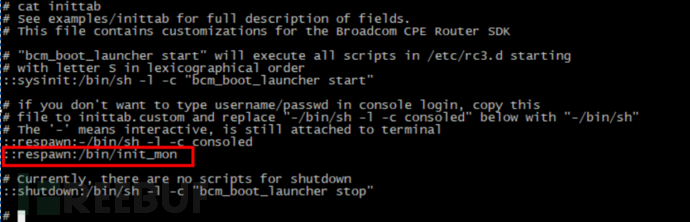
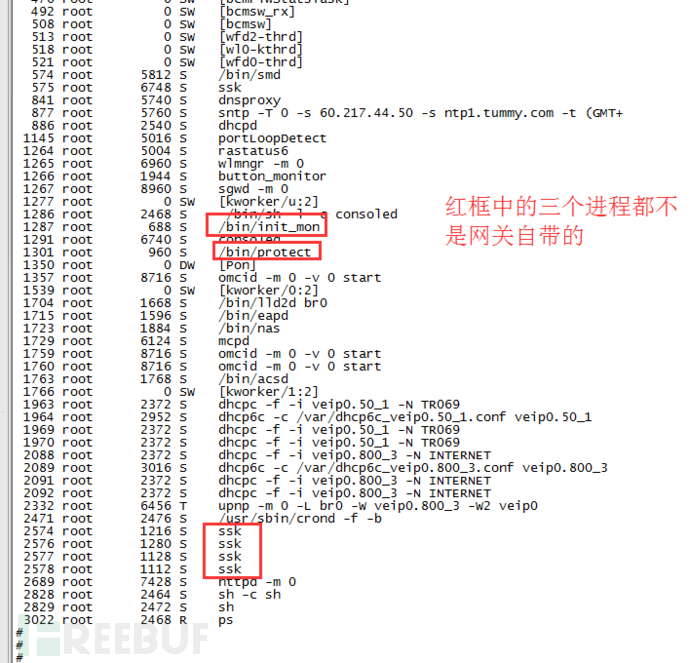 These suspicious programs cannot be killed, and they are immediately restarted each time they are killed. Check the system program startup script inittab, and find that there is an added command /bin/init_mon, which is set to respawn (the meaning of ::respawn is that if the program is closed, it will be restarted). Therefore, init_mon may be a daemon process, and other processes can be restarted by it.
These suspicious programs cannot be killed, and they are immediately restarted each time they are killed. Check the system program startup script inittab, and find that there is an added command /bin/init_mon, which is set to respawn (the meaning of ::respawn is that if the program is closed, it will be restarted). Therefore, init_mon may be a daemon process, and other processes can be restarted by it.
 Check the firewall rules of the problematic ONU and compare them with the rules of a normal ONU, and find that the problematic ONU has been added special processing rules.
Check the firewall rules of the problematic ONU and compare them with the rules of a normal ONU, and find that the problematic ONU has been added special processing rules.
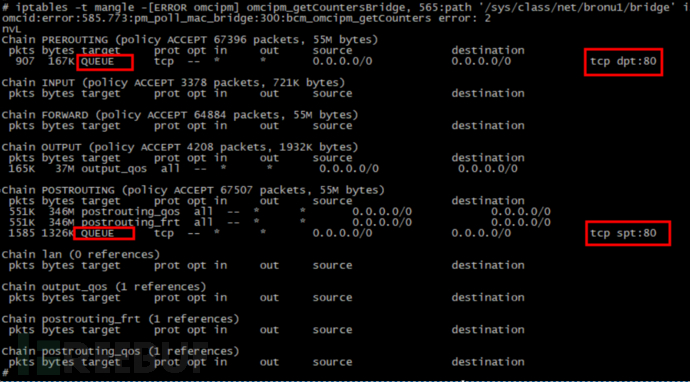 The processing rules in the red box of the figure above will hijack http protocol packets for processing at the application layer.
The processing rules in the red box of the figure above will hijack http protocol packets for processing at the application layer.
When a user accesses a normal web page, the above rules will cause normal internet data to be processed by a suspicious program in the background, resulting in abnormal web page jumps on the user's device.
Secondly, these rules cause http data to no longer pass through the hardware acceleration of the ONU device, but to be processed by the device's CPU. When there is a large amount of http data to be processed, the device will show a high CPU usage rate, and the data cannot be processed in time. Therefore, the web page speed test based on http data does not meet the standard.
Through the above analysis, it can be confirmed that the device has been planted with a trojan. During the regular monitoring of the ONU device, intrusion process packets were captured, and abnormal data interactions from intelligent clients were found, which is also the reason why the user's computer is forced to pop up advertisements.
2.1 Analysis of the intrusion process
During the monitoring process, intrusion packets were captured. The intrusion was completed through a port on the ONU WAN side (this port is mainly used by maintenance personnel to debug the ONU via an APP, this port will be opened on the WAN side when the ONU is in routing mode for internet access, but will not be opened in bridge mode). The APP debugging requires unique authentication information to log in from the LAN side to connect to each ONU, while no such authentication is done on the WAN side. The specific process is as follows:
The attacker accesses the ONU's WAN side 17998 port and interacts with the device's mobileapp process.
The interaction messages embed the wget command to download, deceive the ONU into downloading executable programs to the ONU's /tmp/m, and grant m executable permissions.
After executing the program, the ONU will fromhttp://1.63.XX.XX:19010/tmp/s/flasherDownload another executable program to run.
2.2 Analysis of Behavior of Background Programs After Invasion
After the ONU is invaded, the originally normal programs ftp, samba, mobileapp are closed, and then the background programs init_mon, protect, ssk are planted.
init_mon, protect cannot be killed, the faked process SSK has the same name as the system SSK process. The faked SSK process will establish connections with overseas IP addresses when running, but all connections are encrypted and the specific content of the interactions cannot be obtained.
Faked SSK process:
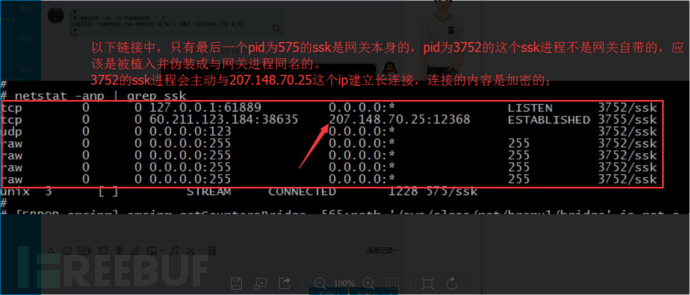
When the faulty ONU starts, it requests addresses from foreign DNS servers:
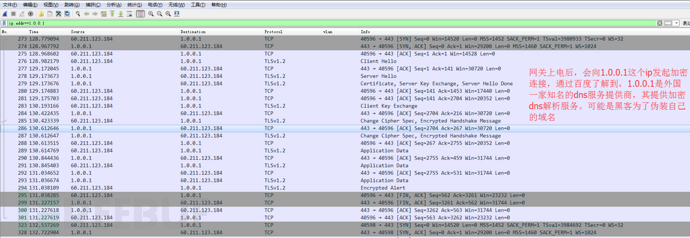
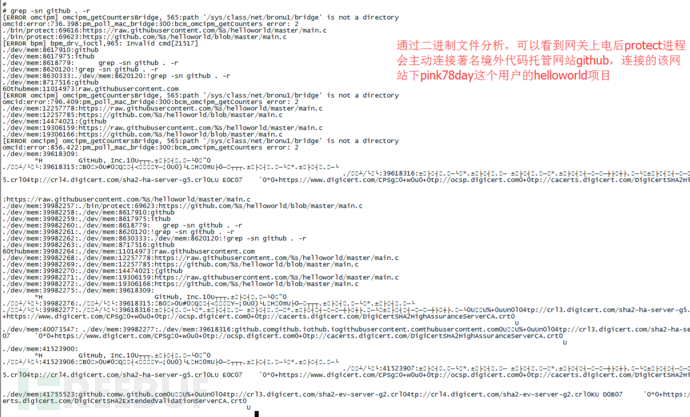
The ONU downloaded and executed a malicious program from github, thereby being completely controlled and becoming a zombie, which is delicious for hackers but has endless troubles for itself.
3. Solutions
(1) Block TCP17998 at the port to prevent the further spread and destruction of malicious programs.
(2) Under the conditions allowed, further tracing the source of malicious programs and locating the source of the attack can help further analyze and solve the problem.
(3) Strengthen the security (firewall) strategy for ONU.
Summary of Analysis
Starting from security, not stopping at security. The development and application of information networks are continuously deepening, bringing progress opportunities to the economy and society while also bringing risks and challenges. Network security threats are becoming increasingly prominent, challenging the order of cyberspace and public and private interests in a concealed, diverse, and complex form.
Broadband ONU terminal equipment (Optical Network Unit) is prone to interference from network data and attacks by malicious programs during operation, leading to security issues. To ensure normal access to services and stable operation of the equipment, attention should be paid to the setting of relevant security protection parameters for networked devices. Analyzing ONU print information and network packets is one of the important means to locate faults. By analyzing the print information, it can be seen what problems exist with the equipment, such as service disk errors, repeated registration of ONU, incorrect data configuration, and security vulnerabilities, etc. In this case, it was through print information and network packets that a Trojan process inside the ONU and network protocol anomalies were discovered, leading to the discovery that the user's ONU had been invaded by a malicious program and had become a zombie, causing abnormal internet access phenomena. It is terrifying to think about it, and network security is national security, network security for the people. Network security relies on the people!
评论已关闭