I. Introduction to Data
1. Data Forms

Data can mainly be divided into two forms, which are the common ways of expressing data in daily life, also known as the carrier of data.
Electronic data: Stored in hard drives and other storage devices, or existing in application databases, can only be read through computers, USB flash drives, or applications. For example: customer information in databases
Paper data: Present data in a very intuitive way on the carrier in the form of paper. For example: insurance policies, application forms, etc.
2. Data Storage Methods
Data is everywhere, permeating every field of our work and life. Common data storage methods include: network storage servers such as DAS, NAS, SAN, etc.; cloud storage; mobile devices such as smartphones, tablets, and devices supporting wireless applications, etc.; paper documents.
3. Data Lifecycle
Data has a complete lifecycle from its initial generation to its destruction.
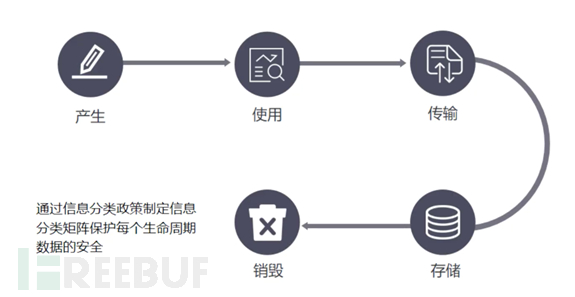
At this point, enterprises need to protect different types of data at each stage of the data lifecycle, and the most commonly used method is to formulate information classification policies.
For example:
In the conventional sense, data can be divided into 4 categories: public, internal, confidential, and highly confidential. The sensitivity of each category of data increases from public to highly confidential, which is the standard for information classification.
Enterprises need to formulate information classification policies, allowing data owners to define which category the data they currently possess belongs to, and according to the classification policy, they also need to formulate an information classification protection matrix.
The information classification protection matrix is similar to Excel, with rows and columns. Taking the above classification criteria as an example, enterprises divide data into 4 categories, which are the 4 columns in Excel. Each row represents the lifecycle of the data, and the cells at the intersection of rows and columns indicate the data protection requirements for this category of data at the current stage of the data lifecycle. This Excel forms the information classification protection matrix.
4. The Value of Data
Any data has value. For companies, or other similar financial institutions such as banks, if any customer information is leaked and exposed by the media, it will pose a great risk to the company, such as regulatory risks, financial risks, and reputation risks, etc. Therefore, confidential data, such as customer information and company financial statements, are crucial for enterprises, being the lifeline of the enterprise.
II. Threats and risks to data security
- Threats and risks to data security
- Threats and risks to data availability
- Threats and risks to data integrity
- Threats and risks to data confidentiality
- Data compliance risks
Information security has three basic characteristics: availability, integrity, and confidentiality. Availability refers to the ability to access and use data at any time without being hindered by hardware failures or other issues. Integrity refers to the protection of data throughout the transaction process from malicious tampering and unauthorized access, ensuring that the data remains in its original form. Confidentiality refers to the encryption of data throughout the process, preventing eavesdropping and unauthorized access, ensuring the security of the data. What we usually refer to as information security protection is the protection of these three basic characteristics of data.
1. Threats and risks to data availability
Malware threats, ransomware viruses, worms, logical risks, etc.
Power failure
Server failure, hardware failure, hard disk damage
User accidental deletion of files without backup
2. Threats and risks to data integrity
Threats from malware, such as trojan files and other virus files
User accidental deletion
Application vulnerabilities
3. Threats and risks to data confidentiality
Malware threats, such as spyware, Trojan horses, keyloggers
Loss of disk or other data storage devices leading to unauthorized access
Intentional disclosure of confidential data by internal personnel
Social engineering attacks, through deception and impersonation to obtain important data, such as: password information
4. Data compliance risks
Laws and regulatory agencies have clear requirements for the collection, storage, use, and transmission of data. Non-compliance with laws and regulations regarding data can lead to financial losses and reputational damage for the company. Therefore, the company must also establish standards for data security protection internally and combine these standards with security awareness training for employees to ensure strict compliance.
III. Data security protection measures
- Data security protection measures
- Management controls
- Technical controls
- Other control recommendations
Management controls refer to administrative laws and regulations and the administrative means of the company. Technical controls, also known as logical controls, refer to the direct use of technical means for security protection. Physical controls are specifically related to physical security controls.
1. Management controls
Establish strategies and standards related to data security;
Information classification standards, information classification protection matrices, and electronic data usage security standards;
Conduct employee data security awareness training and guide employees to handle data properly;
Security professionals must review all relevant laws and regulations and check their applicability to the enterprise;
Enterprises must comply with laws and regulations governing the management of data and system usage, such as the General Provisions of the Civil Law and the Cybersecurity Law of the People's Republic of China, etc.
2. Technical controls
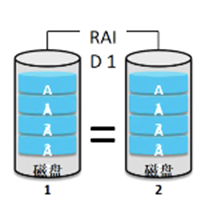
Redundancy technology
- The computational environment retains the attributes of a set of additional resources beyond the main resource set.
- 'One more', it avoids a single point of failure.
- There can be power redundancy, server redundancy, website equipment redundancy, etc.
- Redundancy technology in data centers, such as: hot site, warm site, and cold site
- Disk redundancy, Raid1, Raid5, Raid10, Raid01
Non-persistence
- The attribute of the computing environment being discarded once the assigned task is completed.
- Protect the integrity of the original data.
- VDI non-persistent mode: changes after logging out will be lost, otherwise, it will deviate from the security baseline.
Data backup
- Full backup
- Differential backup
- Incremental backup
- Regularly back up data to prevent accidental data loss, and regularly check the effectiveness of data backups.
Encryption
- Prevent eavesdropping
- Prevent unauthorized access after device loss.
- Protect the confidentiality of data through disk encryption, database encryption, file encryption, USB encryption, email encryption, and voice encryption.
- Use strong encryption algorithms, such as AES, for encryption.
- Protect temporary session security through session keys.
Identity and access control
- Implement strict identity and access control for key assets, such as two-factor authentication.
- Implement login anomaly monitoring through SIEM.
Data destruction
- Delete, right-click 'permanent delete' simply removes the mark, and the data is still on the disk, which can be easily recovered by data recovery software.
- Demagnetize, apply strong magnetic force to the disk drive to lose magnetic charge, but it can also be remagnetized.
- Eliminate, after deleting the data, completely clear the data or re-systemize, and re-divide disk partitions to achieve clearance by repeatedly overwriting the original data with new content.
- Physical destruction is the most thorough method of data destruction, including cutting, crushing, and burning, etc.
Other control recommendations
- Apply data security at all levels of the organization.
- Review how data in the organization may be damaged in different ways and choose the data storage method that best suits the commercial needs.
- Deploy anti-malware and implement IDS at all data storage locations.
- Monitor data security through database monitoring tools, such as Guardium.
- Deploy DLP data leakage protection at all possible data exit points.
- Report the loss of a device immediately, freeze the account by the administrator in the first place, and remotely erase device data if necessary.
- Choose the encryption method that best suits your data security needs, consider full-disk encryption for mobile devices, enable GPS tracking, enable screen lock, and use strong password policies.
- Divide the data management responsibilities into different roles, allocate limited permissions based on roles instead of administrative permissions, and limit the commands that can be executed, such as the SUDO mechanism.
- Update patches in a timely manner through patch management programs to fix vulnerabilities in systems and applications.
- Adjust the privacy settings of social media websites to ensure that personal privacy information is not leaked.
- Do not send company confidential data to personal external email addresses, and try to avoid using USB flash drives to copy important company data. If it is necessary to do so, encrypt your data.
- Ensure that the access permissions of all departing and temporary staff are removed to prevent external access.
hacker hire iiit hyderabad(IIIT Hyderabad)
A brief discussion on enterprise security and the security risks under cloud-native
2 Typical data security scenarios data security risk points
Hidden dangers in the digital age: how to deal with API security risks
In-depth analysis of the security risks and shutdown posture in SEAndroid
5 minutes to understand 'internal threats', the time bomb of enterprise data security
评论已关闭