I. Tool Introduction
Here, we mainly introduce some commonly used tools, mainly for security checks or reverse engineering. They are mainly Windows tools, and the probability of encountering Linux in actual disposal cases is very low. On the one hand, most viruses or ransomware are targeted at Windows, and on the other hand, there are too many versions and branches of Linux, which is also a problem to adapt to.

From top to bottom:
WINHEX--Can directly access process memory (RAM) and perform some dump operations.
FireBlade--No need to explain, there is a single program version, similar to the function of IceSword.
7Z--A relatively small decompression tool. Some clients may appear infected and unable to decompress or not installed decompression software.
HANDLE--A small tool for managing WIN system processes, which can be used as an alternative when the built-in process management is disabled or cannot be used. It can also view some process usage status.
IDA--The famous IDA dynamic program behavior analysis and pseudo-instruction function is very powerful.
LISTDLLS--Main function is DLL usage check list.
Message Analyzer--A small network packet capture and analysis software developed by Microsoft.
NetLimiter pro--Network traffic monitoring tool.
Ollydbg--The famous OD, a necessary tool for unshell and reverse engineering.
PEID--Shell detection tool
Process Explorer--An enhanced task manager that shows more content than the system's built-in process viewer. If you find the built-in one not very useful, this one is recommended.
System Safety Monitor--A software with firewall and monitoring functions, but this is for some older systems below WIN7.
Process Monitor--Process Monitor, the feature is that it can monitor process file writing, network access, registry writing, and other details.
Other packet capture tools recommended:
Coli Network Analysis System--Similar to Wireshark, the feature is that it can classify data according to local processes, and it is purely in Chinese.
Omnipeek--Similar to Wireshark, the feature is good at analyzing a large number of data packets, defining multiple filtering parameters and sorting.
II. Emergency Response Case (a customer in the education industry of a certain district)
1. Background
It was around 5:30 pm on a certain day when we were about to leave work, when we suddenly received a phone call from a customer in a certain district, who said they had been infected with ransomware, and the infected host had been shut down. The supervisory unit of the district was also on the scene, and the customer's existing maintenance team was unable to handle the follow-up. The customer felt a lot of pressure.
However, the customer had not signed a contract with us at that time. Considering the urgency of the event and the opportunity for future projects, we decided to support.
After making a phone call, we learned that there are two emergency issues to be addressed first:
(1) Does the customer need to know if there is any impact on other systems? How to deal with the problematic host after finding it? Restore normal business operations as soon as possible.
(2) The requirements of the supervisory unit are relatively simple: find the IP address near the outbreak of the virus, the general time, the triggering method, etc.
2, Work deployment ideas
A) If the customer is in the county level, we need to go to the county from the city. While on the way, contact the supervisory unit, arrange a person who understands the core switch configuration to be on-site to facilitate the internal network traffic mirror data analysis. Lending a traffic monitoring device is also very useful.
B) Ask the customer to take a photo of the ransomware file name and suffix, send an encrypted sample, and according to the suffix and other characteristics of the ransomware, we will query the public ransomware library to see if it can be directly decrypted.
Websitehttps://www.nomoreransom.org/zh/index.html(Multi-language support is very friendly)


C) It is recommended to change weak passwords and close the SERVER service
It is recommended that the customer change the password strength of all services with weak passwords in the internal network, close the server, and prohibit the ransomware from using ports 135, 139, and 445 for transmission.
Results of preliminary work deployment:
1: The core switch debugging personnel are in place
2: According to the public ransomware keys provided by the above website, no relevant information was found, which means that decryption is basically impossible.
3: Call to confirm that the weak password has been changed and the important business server service has been closed
3, Arrive at the scene
Work思路 on the scene:
Firstly, it is necessary for someone to go to the host infected with ransomware to judge the residual situation of the virus, whether there are any logs left with an impending outbreak time.
Secondly, it is necessary for someone to cooperate to install traffic monitoring equipment to see if there is any ransomware moving laterally within the internal network or brute force cracking.
The order of handling the infected host is as follows:
a) Check whether there is any activity of ransomware on the host.
Method: Create 2-3 blank files with suffixes such as exe, docx, pptx, etc., and you can also change the suffix of a new text file. Pay attention to whether the system process is using a high amount of resources.
If the system CPU usage is very low and the file you created has not been encrypted, it can be basically judged that the ransomware has deleted itself or has stopped activity.
b) Insert your own USB drive into the tool
Tips: If you are worried about the USB drive being encrypted by ransomware, you can compress the required software into an ISO suffix and set it to read-only mode before inserting it into the client.
C) View processes and logs
Routine operations, the default log path of Windows (C:\Windows\System32\winevt\Logs), but most intruders will delete logs, the solution is to understand more about other possible logs that may not have been deleted. By the way, I also recommend a software. Lastactivityview, which can see the recent software execution status of the system, can be used as evidence in the absence of logs (the picture is irrelevant to emergency response).
The general results of handling the infected host:
1: An external port for remote desktop was opened, and it is predicted that the hacker accessed the operating system after brute-forcing from the external network. (Local port viewing command: netstat -ano)
2: The on-site system is the WIN2008 operating system, which Microsoft has stopped maintaining, and many vulnerabilities cannot be updated.
3: Routine operations use public network QQ, Baidu Netdisk,迅雷, and other tools for data exchange, with too many points of leverage.

4: The ransomware utilizes the TCP 445 135 port, and the SERVER service is not closed.
5: The earliest outbreak time on the server was at 0:54 on July 7. (The encrypted suffix can be searched and sorted)
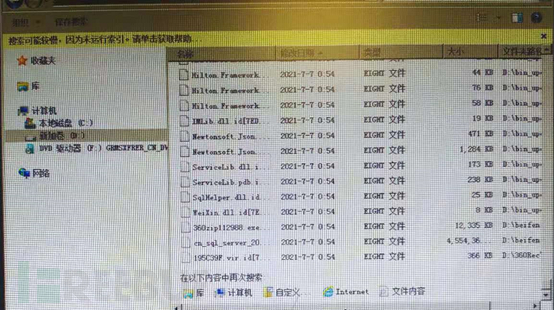
6: The decryption of the existing files cannot be removed (the provided known decryption methods have been tried).
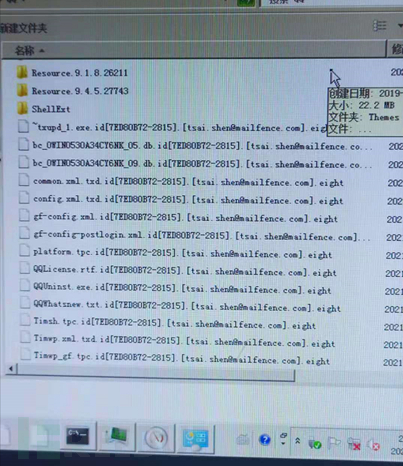
7: The encrypted file suffix is [tsai.shen@mailfence.com].eight.
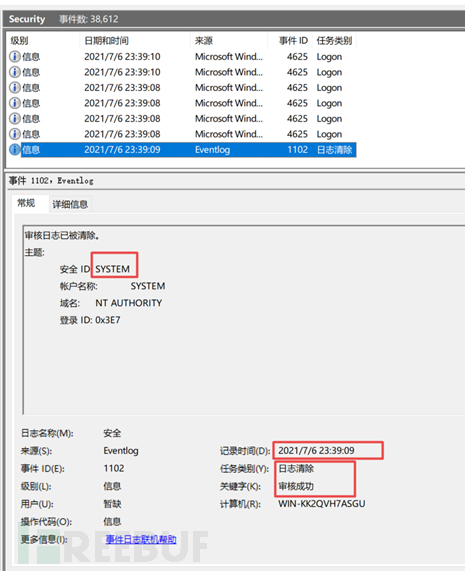
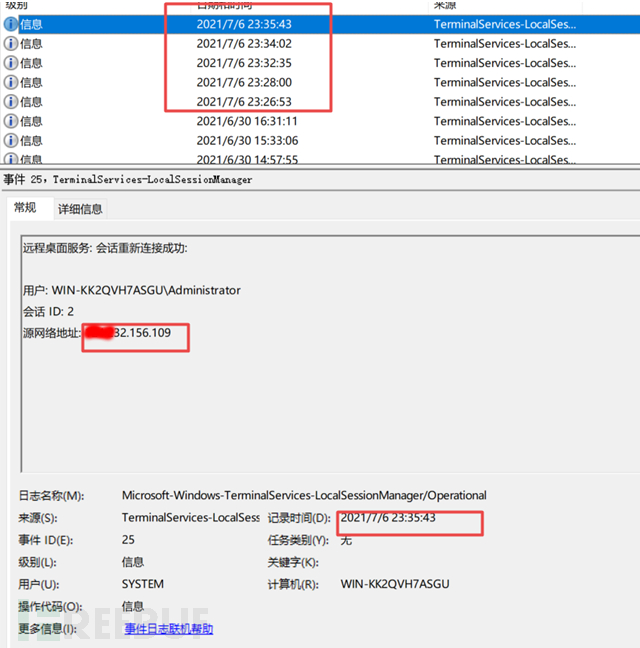
8: It was found that the login log was cleared with system privileges at 23:39:09 on July 6. Fortunately, before that, the remote connection logs had two suspicious IPs (X.X21.116.103, X.X32.156.109), among which X.X32.156.109 had frequent linkages. (Finding the IP can basically hand over to the supervisory unit, and the triggering method should be manual upload and execution)
Trivia: In addition to the security logs, the logs under the log directory
Microsoft-Windows-TerminalServices-LocalSessionManager/Operational can also record remote desktop access logs.
The general timeline of visits is as follows:
X.X21.116.103 (Connected at 23:26:53 on July 6, 2021)
X.X21.116.103 (Disconnected at 23:28:00 on July 6, 2021)
X.X32.156.109 (Connected at 23:32:35 on July 6, 2021)
X.X32.156.109 (Disconnected at 23:34:02 on July 6, 2021)
X.X32.156.109 (Connected at 23:35:43 on July 6, 2021)
X.X32.156.109 (Disconnected at 0:57:08 on July 7, 2021, when file tampering began)
Deployment of traffic monitoring equipment
a) By configuring the core switch mirror port by Huawei technical personnel, all other port traffic is copied to the mirror port. However, the Huawei technical personnel were confused about the observation port, mirror port, and management port for a long time. Most of the time was wasted on communication, and the configuration was finally uploaded without data, later finding out that the problem was with the finished product line connected, and it was resolved after replacing a cable.
b) The traffic has basically been deployed.
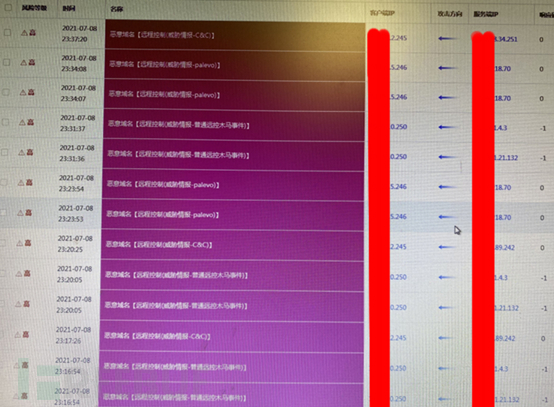
Traffic monitoring equipment observation situation
a) Found two infected hosts with attack behavior, recommended that they disconnect from the network first, and then perform a full disk formatting.
b) After the administrator confirmed that they were not infected, we left. (Other IPs do not belong to the customer's management, they belong to lower-level units, but the lower-level units also have a lot of network attacks, and the customer's internal network lacks defensive means).
Based on the above information, a report can be written.
4Follow-up rectification suggestions for the customer
1: First close the network entry, turn off the core switch and the 135 445 139 TCP network access of key routing.
2: Prioritize system upgrade and patch updates with higher importance. Disable and close the server service on all Windows servers.
3: Increase professional VPN or bastion hosts for operation and maintenance, with source tracing recording function, restrict servers and only allow operation and maintenance from bastion hosts, identity verification should have mobile verification code verification function, used to confirm the identity of the user. The service should install professional terminal protection software such as EDR. Free software may cause missed detection.
4: Strengthen daily security operation and maintenance management, daily vulnerability scanning and patch updates, and for systems that Microsoft has stopped maintaining, it is recommended to upgrade and replace them.
5: Strengthen the control and security area division of the internal network, and the current network defense still focuses on the external network, while the internal network lacks internal control and security measures.
Strengthen daily management and training of technical personnel's safety awareness.
评论已关闭