Introduction: In the field of network forensics, network attack source tracing has always been an important tracing method.
In recent years, cyber security incidents have emerged in an endless stream, and various types of network attacks have caused serious harm to the country, society, and individuals, such as distributed denial-of-service attacks (DDoS), advanced persistent threats (APT) based on botnets, information theft using remote control trojans, etc.Among these attack methods, the attacker will send attack packets to the target host, that is, the victim host,Send specific attack packets.


From the perspective of the victim host, it is possible to observe these attack packets. If these attack packets can be traced to their source and the attacker's actual location can be located, the victim host not only can adopt countermeasures, such as filtering attack packets at appropriate locations, but also can take legal action against the attacker.Therefore, in the field of network forensics, network attack source tracing has always been aImportant Tracing Methods.
Chapter 1: What is Network Attack Source Tracing
In cyberspace, network attack source tracing refers to the ability to trace and locate the host of the real attacker after detecting a network attack event, to help law enforcement personnel take legal action against the attacker. Over the past two decades, researchers have conducted a large amount of research on network attack source tracing technology.
To put it more vividlyNetwork Attack Source TracingThat is, when security personnel detect an attack, how can they trace and locate the attacker's host? Although from the perspective of legal evidence collection, it is more desirable to identify the attacker themselves to take legal measures against suspects, this requires associating the 'host' in cyberspace with 'people' in the physical world.Therefore, in cyberspace, the most important task is to identify the host directly used by the attacker..
Chapter 2: Five Common Issues in Tracing Attackers' Real IP Addresses
Due to the attacker's ability to hide their real IP address in different forms, such as false IP addresses or jump hosts, the problem of tracing the attack source can be divided into the following five issues: false IP tracing, zombie network tracing, anonymous network tracing, jump host tracing, and local network tracing. Thus, trace and trace these five issues.
- Since the attacker can use different forms to hide their real IP address, such as false IP address or jump host, the problem of tracing the attack source can be divided into the following 5 problems: false IP tracing, zombie network tracing, anonymous network tracing, jump host tracing, and local network tracing. Therefore, trace and trace these five problems.False IP Tracing:
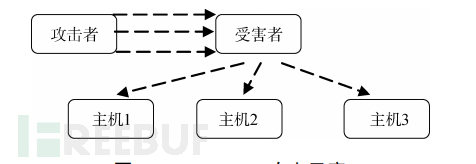
Forensic personnel detect that the source IP address of the attack data packets is forged. For example, a typical SYN Flood attack.
In addition, there is a special type of 'reflection attack', such as Smurf attack, DNS amplification attack, etc. In this type of network attack, the attacker replaces the source IP address in the attack data packets with a forged IP address, and after the victim host receives the packet, it sends the response packet to the forged IP address host. These hosts may exist or may not exist. Therefore, on the victim host side, it is impossible to obtain the IP address of the attacking host.IP addressReplace the victim's IP address and send the attack data packets to the reflection host. After the reflection host receives the packet, the response packet will be sent to the victim host. From the victim host side, it can only be judged that these packets come from the reflection host, and it is impossible to know the true attacker's IP address.
- Zombie Network Tracing:The attacker uses a zombie network to launch attacks, and forensic personnel detect that the source IP address of the attack data packets comes from the bot host in the Botnet. In this case, how can the attacker's host be traced and located?
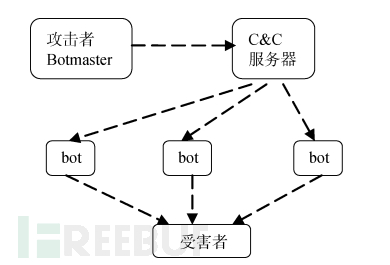
In this type of attack, the attacker uses a C&C or P2P type Botnet, first sends control commands, and the bot host receives the control commands and then launches an attack on the designated target. On the victim host side, it can be seen that the attack data packets come from the bot host, and the true Botmaster cannot be identified.
- Anonymous Network Tracing:The attacker uses anonymous networks, such as 'Tor', to launch attacks, and forensic personnel detect that the source IP address of the attack data packets comes from an anonymous network. In this case, how can the attacker's host be traced and located? The Tor network is a typical attack field for anonymous networks.
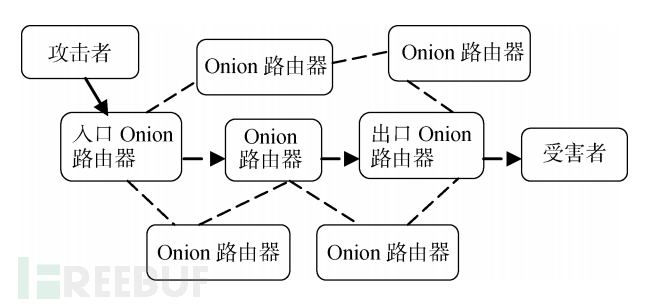
In this type of attack, the attacker's attack data packets are forwarded through anonymous networks, and on the victim host side, only the exit router from which the attack data packets come can be observed, and the true attacker cannot be found.
- Jump Host Tracing:The attacker uses multiple 'jump hosts', that is, by controlling multiple hosts to forward attack data packets, forensic personnel detect that the source IP address of the attack data packets is the IP address of the last-hop 'jump host'. In a recent NAS attack at Northwestern Polytechnical University, 54 jump hosts were used to hide the true IP address.
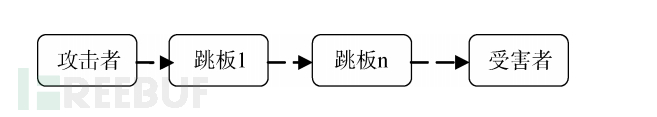
In this type of attack, the attacker controls multiple jump hosts in advance and uses them to forward attack data packets. On the victim host side, only the last-hop host from which the attack data packets come can be seen, and the true attacker cannot be identified. It is obvious that the longer the jump path, the harder it is to trace the attacker.
- Local network tracing:The attacker is located within a private network, and the source IP address in the attack packet has been converted by the NAT gateway's VAT (Network Address Transform) address transformation.
In this type of attack, since the attacker's IP address is a private IP address, only the NAT gateway can be seen on the victim host end.IP addressIn large private networks, especially in wireless local area networks, it is not an easy task to find and locate the attacker.
In actual network attack incidents, it may not strictly comply with the above various attack scenarios, but can roughly be classified into one or more of the above problems.
Three, tracing the source of false IP address attacks
When the source IP address of the attack packet is forged, how to find the real IP address of the sender of the attack packet? This problem is also known as IP tracing (IPTraceback).For this issue,溯源 methods need to be implemented according to different backgrounds, situations, and classification methods.
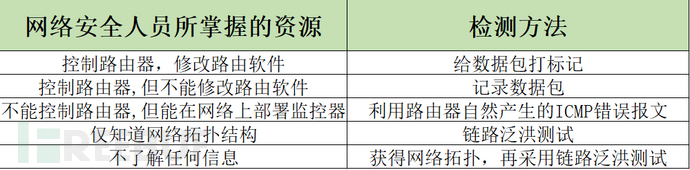
① Background: Forensic personnel can control all or most of the routers on the backbone network and can modify the routing software.
Forensic personnel can add new functions to the routers on the backbone network in advance, modify the standard IP protocol without affecting normal routing, to help find the real IP address.
Methods based on this condition mainly include probabilistic packet marking algorithms, deterministic packet marking algorithms, ICMP marking algorithms, etc. There are also some combined methods, such as a mixed method of packet marking and packet recording; a comprehensive method that combines ICMP and PPM algorithms, where routers mark IP packets with a certain probability and at the same time fill in the IP address in the ICMP packet, etc.
② Background: Forensic personnel can control routers on the backbone network but cannot modify the routing software.
In this case, forensic personnel can observe and record IP packets passing through backbone network routers in advance, but cannot change the standard routing protocol.
The main idea is to record all packets passing through the router, and when an attack occurs, the victim host queries its upstream router. By comparing the recorded packets, the path the packet has passed through can be constructed. The advantage of this method is that it can trace a single packet, but the disadvantage is that it needs to consider the problem of limited storage space in routers.
So, in this case, Alex C. Snoeren, Craig Partridge, and others designed a tracing system called SPIE in their paper 'Single-packet IP traceback', which does not require routers to record the entire packet but instead uses a bloom filter to record packet summaries, significantly reducing the required storage space. Then, by querying the packet summaries on each router, the attack path can be reconstructed.
It is also possible to record packets based on the situation of some routers, and for multiple attack sources, this method only needs to track the packets belonging to multiple attack sources to identify multiple attack sources.
In 'Session based logging (SBL) for IP-traceback on network forensics', a packet recording method based on session is proposed, that is, only record the SYN packets for connection establishment requests and the FIN packets for connection termination in the TCP data stream, and ignore the packets in the middle of the stream, thereby greatly reducing the required storage space.
In 'Passive IP traceback: disclosing the locations of IP spoofers from path backscatter', a method for tracking inter-domain issues is proposed. This method can use the IP packet recording method of routers, combined with the MAC addresses at the link layer, to identify false IP addresses and implement a prototype system.
Since it is not possible to change the existing routing structure in this case, another approach is to build an overlay network (Overlay Network) on the existing routing structure to implement packet tracking through the newly designed overlay network.
③ Background: Forensic personnel cannot control the routers on the backbone network, but they can deploy monitors on the network.
In this case, forensic personnel can only deploy monitors at appropriate locations on the network to collect packets. Here, the network does not refer to the backbone network, but rather the terminal network.
In the case of large traffic packets, due to various reasons such as network congestion, there is a certain probability that routers will generate ICMP packets indicating that the target is unreachable. Since the source IP address of the attack packets is false and generally randomly generated, these ICMP packets will be sent to these false IP addresses, which include the IP address of the router and the source and destination IP addresses of the original packet.
Therefore, the monitors deployed on the network will receive these ICMP packets, and according to the routers that send these ICMP packets, the attack path of these data packets can be constructed. Robert Stone and Centertrack proposed in 'an IP overlay network for tracking DoS floods' that by using the data collected by the Network Telescope project (which can cover 1/256 of IPv4 addresses) combined with the topology of the backbone network, it is possible to discover the source of the attack to some extent.
However, the method of tracing and tracing requires a large amount of attack packet traffic and to be implemented during the attack. Once the attack is over, this method cannot find the real IP address.
④Background: The forensic personnel cannot control the backbone routers, cannot deploy monitors, but know the topology of the backbone network.
In the case where the forensic personnel only know the topology of the backbone network, have no permission to control the routers in the backbone network, and have no conditions to deploy monitors throughout the network, we can adopt the following several methods for tracking and tracing.
an approximate source
However, this method can only detect a single attack traffic, and it is difficult to distinguish different attack traffic if multiple attack traffic exists. This method also requires a large amount of attack packet traffic, and once the attack is over, the method becomes ineffective. In addition, this method itself is a DoS attack, which will affect normal data traffic.
A method based on ant colony algorithms can also be adopted, that is, the victim host sends out some ant colonies, which choose paths according to the degree of load on the links. The higher the link load, the more likely it is to be attack traffic, so the probability of the ant colony choosing this path is higher. When all the ant colonies reach the edge of the monitored network, according to the paths traveled by the ant colonies, the most likely attack path can be constructed.
⑤Background: The forensic personnel cannot control the backbone routers, cannot deploy monitors, and do not know the topology.
If the forensic personnel do not have any resources, it seems impossible to track down the real IP address under this condition. However, certain methods can be adopted to obtain the topology of the backbone network, thus transforming the problem into a topology situation. For example, Dawn Xiaodong Song and Adrian Perrig in 'Advanced and authenticated marking schemes for IP traceback' utilized traceroute to obtain the network topology.
So for the solution of general false IP traceability problems, different detection methods can be adopted according to different situations for tracing. However, with the complexity of the current network attack environment, attack methods, and the continuous upgrade of technology, we also need to upgrade our detection methods, improve the technical level of network attack traceability, so as to better protect our network security.
hacker-earth-thoughtworks-hire(Thoughtworks)
Discussion on Zero Trust Network Construction and Some Details (Part Two)
Indirect attack methods in LLM attacks and defense methods against LLM attacks
Dynamic CNN model for identifying fake personal profiles in online social networks
Common methods for reducing costs and increasing efficiency of ElasticSearch
评论已关闭