In October 2023, a Darktrace customer's network was attacked by ALPHV (i.e., BlackCat) ransomware. After analysis, the attack event was related to Nitrogen malware, such as the release of malicious ads and the distribution of malicious Python packages.
Threat Trend: Malware as a Service
Throughout 2023, 'malware as a service' has remained the main type of threat affecting Darktrace customers, with malware and ransomware becoming increasingly generalized and customizable. In 2024, security teams should be prepared to actively respond to malware as a service (MaaS) and ransomware as a service (RaaS) threats.
What is the ALPHV ransomware?

ALPHV ransomware, also known as 'BlackCat (Black Cat)' or 'Noberus', is one of the most well-known RaaS threats in the past few years. It is a ransomware coded in Rust. Its samples are sold by RaaS 'operators' to other cybercriminals (RaaS 'downstream organizations'), who enter the target unit network, implant ransomware, and demand ransom.
ALPHV is likely to have been first used in the wild in November 2021 and has gradually become one of the most productive ransomware viruses. According to the FBI report, as of September 2023, nearly 300 million US dollars in ransom has been paid for ALPHV.
In December 2023, the FBI and the United States Department of Justice announced the successful crackdown on the ALPHV organization, including the shutdown of its data leak website and the release of decryption tools. In February 2024, the United States Department of State announced a reward of 10 million US dollars for providing intelligence on key leaders of the ALPHV operational organization.
The destructive activities of this organization seem to have been successful, and the frequency of ALPHV attacks has also significantly decreased recently. However, it is not surprising if, like DarkSide and BlackMatter before, the organization returns in a new guise.
How does the ALPHV ransomware operate?
Observations show that the ALPHV downstream organization sets up malicious search engine ads for tools such as WinSCP and AnyDesk, and delivers a Python backdoor implant named 'Nitrogen' to user devices through these malicious ads.
After clicking on an advertisement, users enter a distribution website similar to a legitimate software, and attempt to download software. A backdoor malware sample named 'Nitrogen' is then delivered to their devices. Nitrogen will implant various command and control (C2) implants into the user's device, including Cobalt Strike Beacon and Sliver C2. Criminals use these C2 implants to gain backdoor access for reconnaissance and lateral movement, preparing for the execution of the ALPHV ransomware payload.
How Darktrace counters ALPHV ransomware
In October 2023, Darktrace discovered several cases where ALPHV downstream organizations penetrated the customer's network through malicious advertising, leading customers to download and install Nitrogen from fake websites such as 'wireshhark.com' and wìnscp.net through social engineering.
Although the attacker executed malicious activities through the devices of the customer's IT team, managed to bypass traditional security measures, but Darktrace DETECT™ quickly identified intrusion indicators (IoC) in the first place, plus Cyber AI Analyst™ autonomously investigated various post-intrusion activities, fully restored the attack process for the customer, and helped the customer quickly start corrective and recovery work.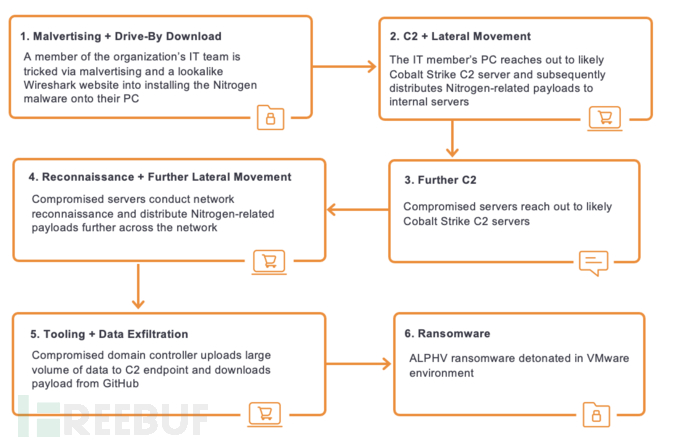
ALPHV ransomware attack timeline
Malicious advertising + Nitrogen download (an IT staff member of the customer was deceived by malicious advertising, mistakenly downloaded Nitrogen from a website similar to wireshark)
C2 + Lateral movement (the employee's PC connects to the Cobalt Strike C2 server and distributes Nitrogen-related payloads to internal servers)
Further C2 (infected servers connect to Cobalt Strike C2 servers)
Network reconnaissance + Deep lateral movement (after infected servers are reconnaissance, Nitrogen-related payloads are distributed throughout the network)
"Weaponization" + Data leakage (infected domain name servers upload a large amount of data to C2 terminals and download payloads from Github)
Ransomware (executing ransomware in a virtual machine environment)
In mid-October, IT staff of a US customer of Darktrace installed the network traffic analysis software Wireshark. Due to the customer's configuration, Darktrace's visibility of the device was limited to its internal traffic, but it was still able to identify suspicious activities related to the device and issue alerts.
Firstly, Darktrace observed that the device issued an A-type DNS request to 'wiki.wireshark.org' immediately before sending A-type DNS requests to the domains 'www.googleadservices.com', 'allpcsoftware.com', and 'wireshhark.com' (note the two 'h's). This pattern indicates that the device user was redirected to wireshhark.com due to interaction with Google-sponsored search results pointing to allpcsoftware.com.
If you directly go to wireshhark.com from the browser search bar, you will see the YouTube video of Rick Astley's song 'Never Gonna Give You Up'. This indicates that the wireshhark.com website has been configured to redirect users to this video, unless they arrive at the website through related sponsored Google search results.
Users who accessed the website through Google sponsored search results are likely to be redirected to the illegal website wireshhark.com. The attackers who developed the website were inspired by the concept of 'rickrolling', giving the target victims a link or video (bait), only to reveal the content of Richard Starkey's song 'Never Gonna Give You Up' from 1987, which has nothing to do with the title.
After being redirected to wireshhark.com, the user unintentionally installed a malicious software sample that placed something that appeared to be Cobalt Strike on their device. The subsequent A-type DNS requests sent to the domain 'pse.ac' proved that Cobalt Strike was present on the user's desktop. These DNS requests may have been responded to by the Cobalt Strike C2 server address 194.169.175.132. Since Darktrace can only see the internal traffic of the device, no C2 connections to the Cobalt Strike endpoint were observed. However, the subsequent behavior on the desktop indicated that the criminals had gained human control over the device through established C2 channels.
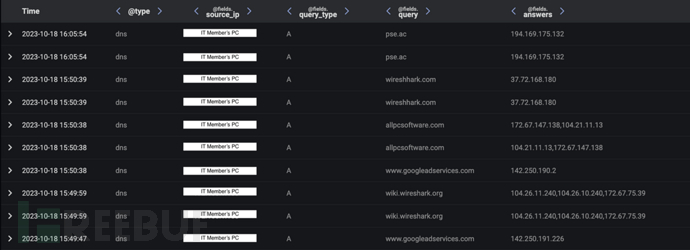
Advanced search data shows that the customer's device accessed the fake website wireshhark.com
Because the criminals have controlled the IT personnel's devices, they are able to abuse privileged account credentials to spread malicious payloads in the network through SMB and WMI services. Darktrace also found that they distributed the Windows Sys-Internals tool PsExec, possibly to assist with lateral movement. The behavior of distributing files from the IT personnel's devices is normal, making it difficult to detect the malicious SMB activity.
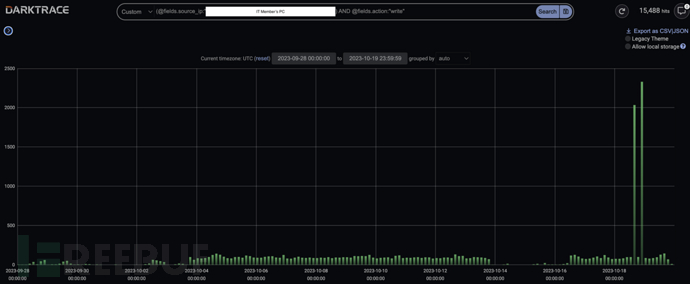
Advanced search data indicated that the device distributed files normally via SMB
However, Darktrace DETECT found an abnormal peak in file writes being executed here, and the executable files being distributed were found to have behavior伪装成 different file types, which may be intended to evade detection by traditional security tools.

Event log data indicated that the SMB write of the Python executable file on the device created multiple Model Breach violations
In addition to the anomalies detected by DETECT, Darktrace's AI analysts initiated an autonomous investigation into the ongoing attack, linking SMB writes and executable payloads to shared resources, viewing them as a single lateral movement event rather than a series of isolated incidents. After completing the investigation, the AI analysts output a detailed summary of the event on the management platform, helping customers identify affected devices and begin the repair process.
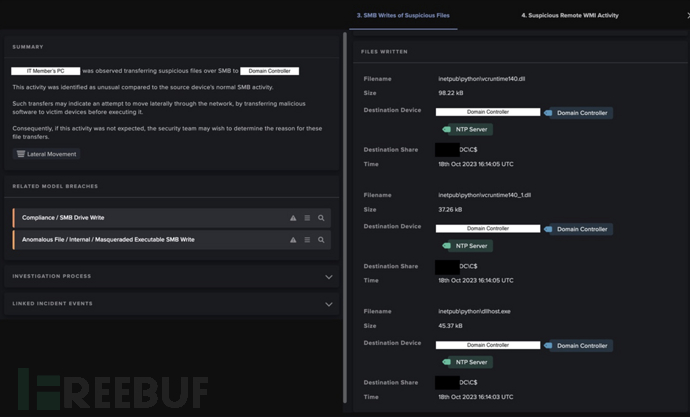 Summary of AI Analyst Investigation (with emphasis on the lateral movement activity of the IT personnel's device)
Summary of AI Analyst Investigation (with emphasis on the lateral movement activity of the IT personnel's device)
C2 Activity
The Python payload distributed by this device is likely related to the Nitrogen malware, as confirmed by the file name and its behavior.
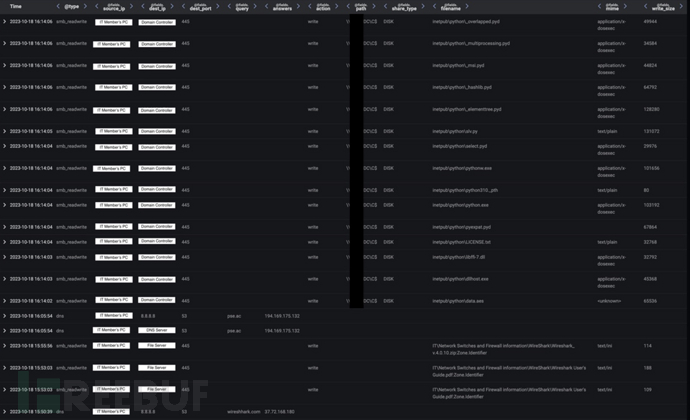
Advanced search data showed that the affected device connected to the C2 endpoint pse.ac and then distributed the Python executable file to the internal domain controller
The internal device that was distributed with the Nitrogen payload immediately connected to the Cobalt Strike C2 infrastructure. These C2 connections were established on ports 443 and 8443 via SSL. Darktrace discovered that the attacker laterally moved to the internal SQL server and internal domain controllers.
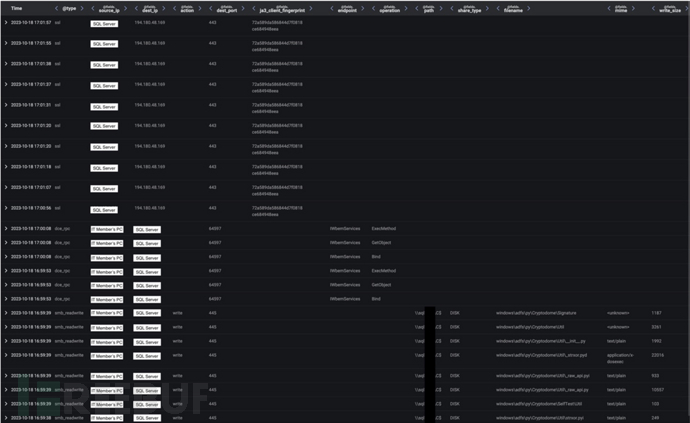 Advanced search data indicated that the internal SQL server established a connection with the Cobalt Strike C2 endpoint 194.180.48.169 after receiving a Python payload from the target device
Advanced search data indicated that the internal SQL server established a connection with the Cobalt Strike C2 endpoint 194.180.48.169 after receiving a Python payload from the target device
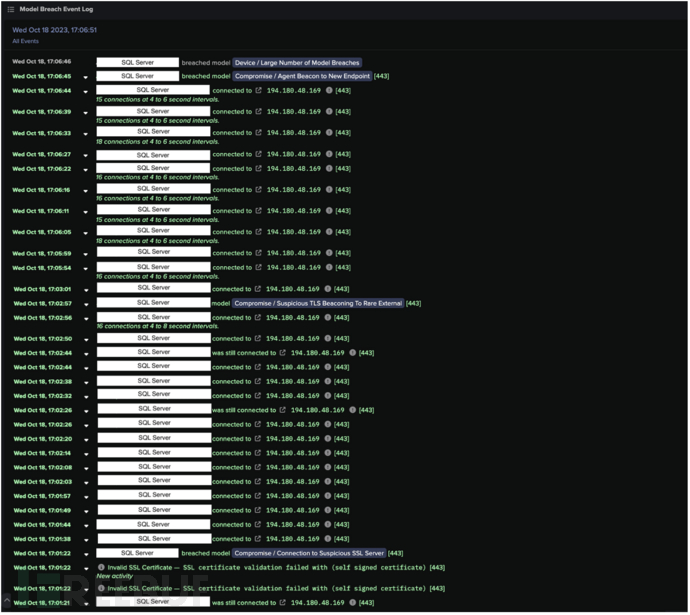 Event log data showed multiple DETECT model violations triggered by the C2 connection between the internal SQL server and 194.180.48.169
Event log data showed multiple DETECT model violations triggered by the C2 connection between the internal SQL server and 194.180.48.169
The AI analyst conducted a further investigation into this activity, successfully identifying a series of independent SSL connections and consolidating them into a complete C2 event.
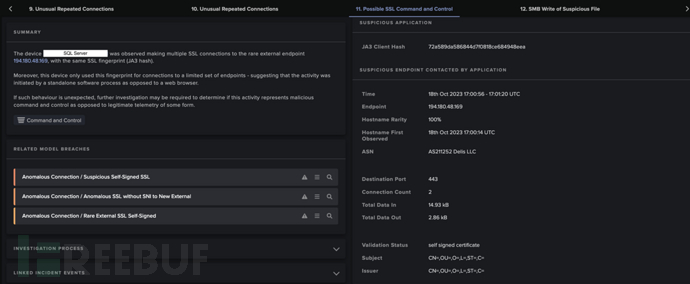 Summary of AI Analyst Investigation (with emphasis on C2 connections from SQL servers)
Summary of AI Analyst Investigation (with emphasis on C2 connections from SQL servers)
Darktrace observed the attacker's actions of manually elevating privileges on these systems, conducting network reconnaissance (mainly port scanning), spreading malicious payloads further within the network, stealing data from domain controllers, and transmitting payloads to domain controllers from Github.
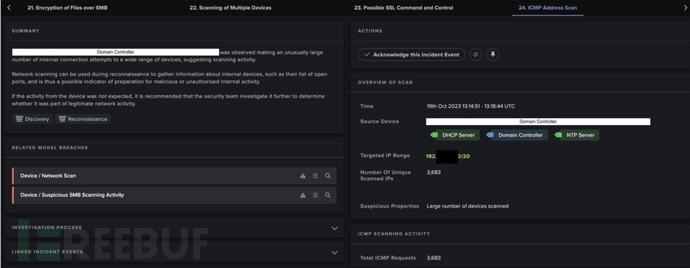 AI analyst investigation summary: IP address scanning executed by the internal domain controller
AI analyst investigation summary: IP address scanning executed by the internal domain controller
 Event log data shows that when the internal domain controller communicated with C2 endpoint 194.180.48.169, it established a connection with GitHub
Event log data shows that when the internal domain controller communicated with C2 endpoint 194.180.48.169, it established a connection with GitHub
 Event log data shows that when the internal domain controller uploaded a large amount of data to C2 endpoint 194.180.48.]169, DETECT created a model violation event
Event log data shows that when the internal domain controller uploaded a large amount of data to C2 endpoint 194.180.48.]169, DETECT created a model violation event
After completing extensive reconnaissance activities and lateral movement, the attackers executed ransomware in the user's VMware environment, successfully encrypting the customer's VMware vCenter server and VMware virtual machines. The entire attack process took about 24 hours.
Darktrace's proactive threat notification (PTN) service timely notifies customers of these suspicious activities through Darktrace SOC, helping them quickly identify infected devices and block intrusions before they escalate.
In the face of high-risk alerts detected by DETECT, Darktrace RESPOND can immediately respond and interrupt intrusion activities, slowing down lateral movement.
Moreover, Darktrace AI analysts comprehensively analyzed multiple events, reconstructed the attack process, and provided detailed explanations to improve post-incident investigation efficiency.
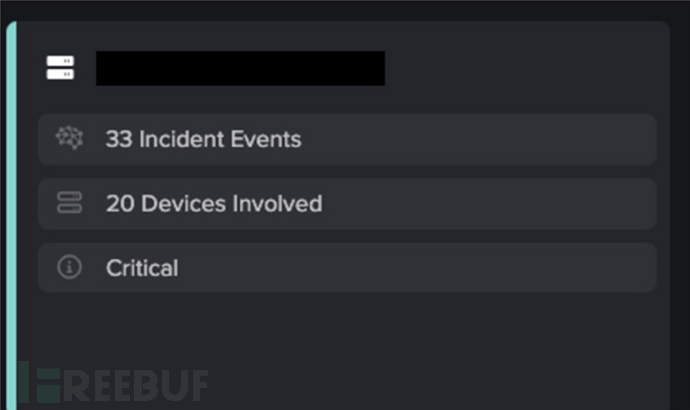 Darktrace AI analysts summarized the 33 events they created into an attacker behavior chain
Darktrace AI analysts summarized the 33 events they created into an attacker behavior chain
Conclusion
Without a doubt, cybercriminal groups will continue to upgrade their 'equipment' to avoid constantly updated cybersecurity measures. The ALPHV ransomware attack further illustrates this trend, with attackers luring users to download the malicious software Nitrogen from a fake Wireshark website, implanting the C2 program into users' devices, and gradually opening the door for the attackers.
Despite the ransomware attackers using non-traditional initial access methods, Darktrace DETECT was still able to identify abnormal traffic patterns. AI analysts conducted independent investigations based on the large number of alerts created by DETECT, analyzing and reconstructing the complete timeline. The first abnormal behavior in this event was executed by the customer's internal IT staff, which is normal for traditional signature-based and rule-based security tools. However, Darktrace's self-learning artificial intelligence discovered subtle deviations. Therefore, this successful detection proves the unique value of self-learning AI in anomaly detection.
Reference the original text
https://darktrace.com/blog/no-bad-luck-for-darktrace-combatting-alphv-blackcat-ransomware
Be alert to the incoming new ransomware, the ransom note information uses German!
Has the 'new king' of ransomware appeared? RansomHub has targeted 600 enterprises in 2024
5. Contact physical devices but have permission to extract firmware:
Hackers unveil the secrets of WiFi phishing, zero trust brings a breakthrough in protection
Anubis banking malware imitates TikTok international version in attack activity
评论已关闭