
CloudSEK's security researchers report that the malware has infected 18,459 devices worldwide, most of which are located in Russia, the United States, India, Ukraine, and Turkey.
CloudSEK's report states: 'A Trojanized XWorm RAT generator has been weaponized and spread.'It is specifically aimed at those who are just starting to touch on cybersecurity, script kiddies.These people directly download and use various tools mentioned in the tutorials, indicating that 'thieves have their code' does not exist.
CloudSEK found that the malware contains a 'kill switch' for uninstalling the malware from many infected devices. However, due to the limitations of actual operations, some devices are still in an infected state.
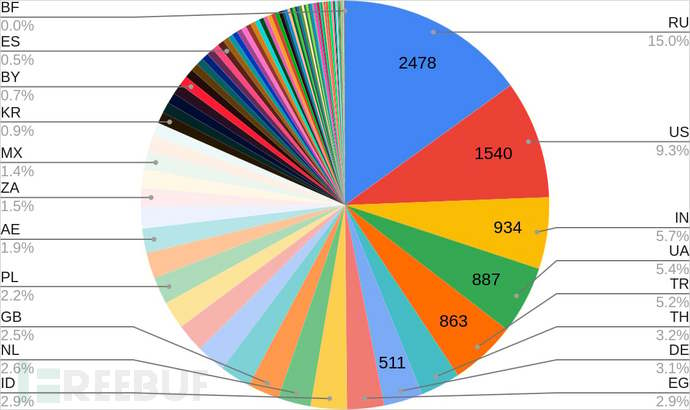 Location of infected devicesSource: CloudSEK
Location of infected devicesSource: CloudSEK
Fake RAT generator implants malware
Researchers say they recently discovered a Trojanized XWorm RAT generator that spreads through various channels, including GitHub repositories, file hosting platforms, Telegram channels, YouTube videos, and websites.
These channels promote the RAT generator, claiming that other threat actors can use the malicious software for free. However, it is not a real XWorm RAT generator but rather an infected device of a threat actor.
Once the device is infected, the XWorm malware checks the Windows registry to determine if it is running in a virtualized environment. If it confirms a virtual environment, the malware will stop running. If the host meets the infection conditions, the malware will make the necessary modifications to the registry to ensure it continues to run after the system restarts.
Each infected system is registered to a Telegram-based command and control (C2) server with a hardcoded Telegram bot ID and token. The malware also automatically steals Discord tokens, system information, and location data (via IP address) and sends them to the C2 server, then waits for the operator's instructions.
Among the total of 56 supported commands, the following are particularly dangerous:
- /machine_id*browsers– Steal passwords, Cookies, and auto-fill data saved in the browser
- /machine_id*keylogger– Record all content entered by the victim on the computer
- /machine_id*desktop– Capture the current screen of the victim
- /machine_idencrypt – Encrypt all files on the system using the provided password
- /machine_idprocesskill – Terminate specific running processes, including security software
- /machine_idupload – Steal specific files from the infected system
- /machine_id*uninstall– Remotely uninstall malicious software from the device
CloudSEK found that malicious software operators stole data from about 11% of the infected devices, mainly by capturing screenshots of infected devices (as shown below) and stealing browser data.
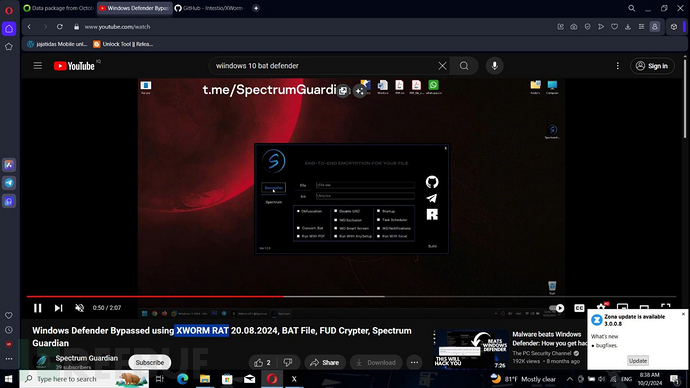 Hacker's desktop screenshotSource: CloudSEK
Hacker's desktop screenshotSource: CloudSEK
Destroying the botnet using the termination switch
CloudSEK researchers unloaded malicious software from infected devices by using hardcoded API tokens and built-in 'termination switches' to destroy the botnet.
For this, they sent batch uninstall commands to all listening clients, iterating through all known device IDs extracted from the Telegram logs. They also assumed that the device ID followed a simple numeric pattern and tried brute-forcing IDs from 1 to 9999.
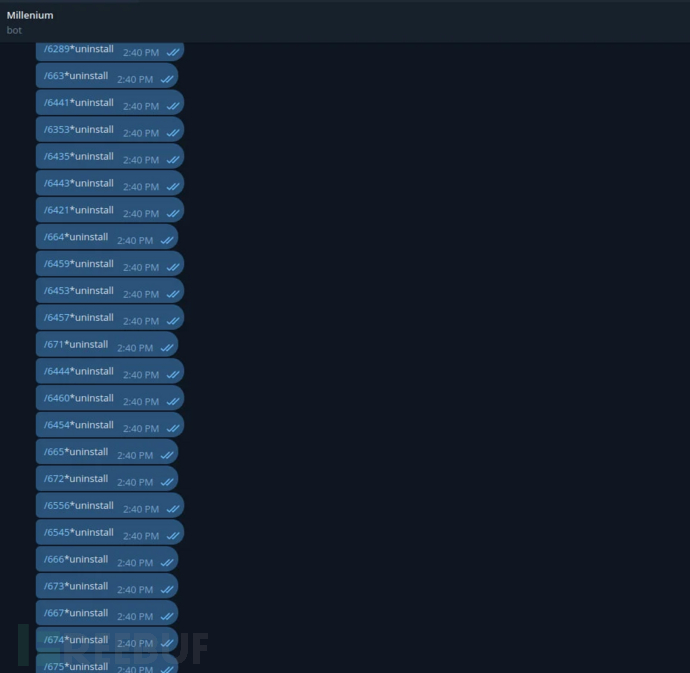 Send uninstall commandSource: CloudSEK
Send uninstall commandSource: CloudSEK
Although this operation successfully removed malicious software from many infected devices, devices that were not online when the command was issued are still infected. In addition, Telegram has a limit on the rate of message sending, so some uninstall commands may be lost during transmission.
The scenario of hackers attacking hackers is not uncommon in reality. The research results of CloudSEK remind us that we should never trust unsigned software, especially those distributed by other cybercriminals, and malicious software generators should only be installed in test/analysis environments.
Reference source:
Hacker infects 18,000 "script kiddies" with fake malware builder
评论已关闭