
A hacker organization from North Korea is using a RID hijacking technique that can deceive the Windows system into treating a low-privileged account as an account with administrative privileges.

Hackers used a custom malicious file and an open-source tool to carry out the hijacking attack. Both tools can execute the attack, but researchers at South Korea's AhnLab said there are some differences between them.
The Working Principle of RID Hijacking
In Windows systems, the Relative Identifier (RID) is part of the Security Identifier (SID), which is a unique identifier assigned to each user account to distinguish different accounts.
RID can take different values to represent the access level of an account, for example, '500' represents an administrative account, '501' represents a guest account, '1000' represents a standard user, and '512' represents a domain administrators group.
When an attacker modifies the RID of a low-privileged account to match the RID value of an administrative account, RID hijacking occurs, and Windows will grant the account elevated privileges.
However, to carry out this attack, access to the SAM registry is required, so hackers first need to infiltrate the system and obtain SYSTEM privileges.
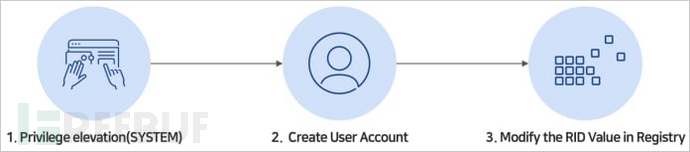 RID Hijacking Process 来源:ASEC
RID Hijacking Process 来源:ASEC
Andariel Attack
Researchers at AhnLab's Security Emergency Response Center (ASEC) attribute this attack to the Andariel threat organization, which is associated with North Korea's Lazarus hacker group.
The attack began with Andariel obtaining SYSTEM privileges on the target system by exploiting a vulnerability.
Hackers use tools such as PsExec and JuicyPotato to start a SYSTEM-level command prompt, thereby achieving initial privilege escalation.
尽管SYSTEM权限是Windows系统中的最高权限,但它不允许远程访问,无法与图形用户界面(GUI)应用程序交互,且非常容易被检测到,并且无法在系统重启后保持持久性。
为了解决这些问题,Andariel首先使用“net user”命令创建一个隐藏的低权限本地用户,并在命令末尾添加“`”字符。
通过这种方式,攻击者确保该账户无法通过“net user”命令显示,只能在SAM注册表中识别。然后,他们执行RID劫持,将该账户的权限提升为管理员。
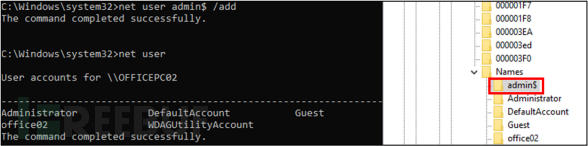 Windows系统上的隐藏Andariel账户 来源:AhnLab
Windows系统上的隐藏Andariel账户 来源:AhnLab
据研究人员称,Andariel将其账户添加到远程桌面用户组和管理员组中。
这种RID劫持是通过修改安全账户管理器(SAM)注册表实现的。朝鲜黑客使用自定义恶意软件和开源工具来执行这些更改。
来源:ASEC
尽管SYSTEM权限可以直接创建管理员账户,但根据安全设置的不同,可能会受到某些限制。提升普通账户的权限则更加隐蔽,更难被检测和阻止。
Andariel还试图通过导出修改后的注册表设置、删除密钥和恶意账户,然后从保存的备份中重新注册来掩盖其踪迹,从而在不出现在系统日志中的情况下重新激活账户。
如何防范RID劫持攻击
为了降低RID劫持攻击的风险,系统管理员应使用本地安全机构(LSA)子系统服务来检查登录尝试和密码更改,并防止未经授权的访问和对SAM注册表的更改。
此外,建议限制PsExec、JuicyPotato等工具的执行,禁用来宾账户,并为所有现有账户(即使是低权限账户)启用多因素认证。
值得注意的是,RID劫持技术早在2018年就已经被公开,当时安全研究员Sebastián Castro在DerbyCon 8上将其作为一种Windows系统的持久化技术进行了演示。
通过以上分析,我们可以看到,RID劫持是一种隐蔽且危险的攻击手段,系统管理员应采取多种措施来防范此类攻击,确保系统的安全性。
参考来源:
评论已关闭