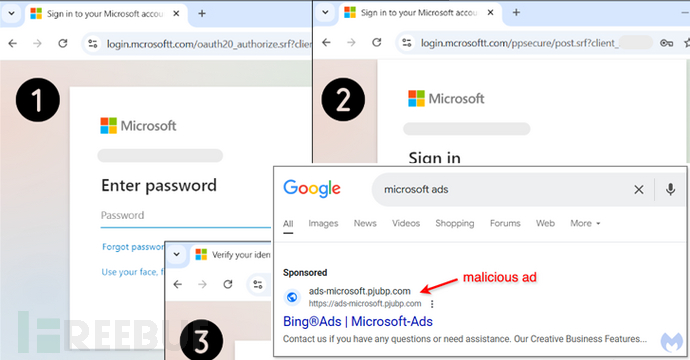
Cybersecurity researchers recently discovered a malicious advertising campaign targeting Microsoft ad users. Attackers guide users to phishing pages through fake Google ads, stealing their login credentials.

Jérôme Segura, Senior Research Director at Malwarebytes, said in a report on Thursday: ‘These malicious ads appearing on Google search are aimed at stealing the login information of users trying to access the Microsoft advertising platform.’
This discovery was made a few weeks after the cybersecurity company exposed similar activities. Previously, attackers used sponsored Google ads to target individuals and businesses advertising through the Google advertising platform.
The latest round of attacks targets users who search for keywords such as ‘Microsoft Ads’ on Google, trying to lure them into clicking on malicious links in the search results pages.
Attack Techniques: Bypassing Detection and Phishing Page Disguise
Attackers have adopted various technical means to bypass the detection of security tools. For example, they redirect traffic from VPNs to a fake marketing website. In addition, website visitors will also receive a Cloudflare verification challenge to filter out robots.
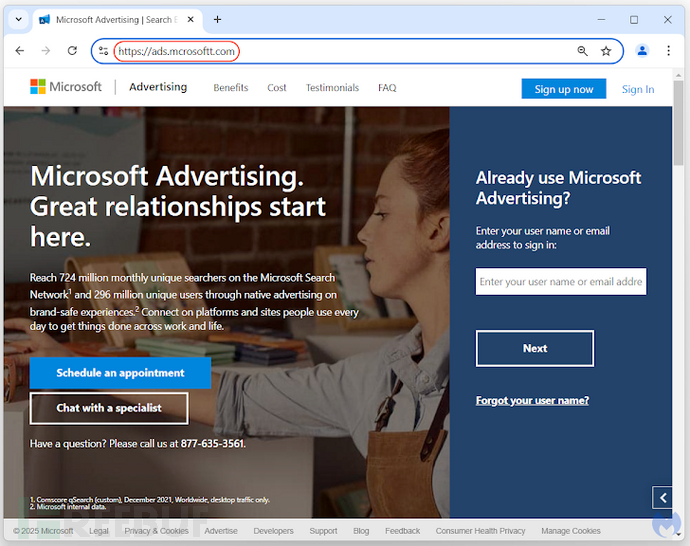
What is more interesting is that users trying to directly access the final login page (‘ads.mcrosoftt[.]com’) will be redirected to a YouTube video related to a famous internet meme.
The phishing page is extremely similar to Microsoft's legitimate page (‘ads.microsoft[.]com’), designed to steal the victims' login credentials and two-factor authentication (2FA) codes, allowing the attacker to hijack their account.
Malwarebytes said they have found some phishing infrastructure targeting Microsoft accounts, which can be traced back several years, indicating that the activity has been going on for some time and may also target other advertising platforms such as Meta.
It is noteworthy that most phishing domains are either hosted in Brazil or use the Brazilian top-level domain ‘.com.br’, which is similar to the attack activities aimed at Google ad users, who mainly use the ‘.pt’ top-level domain.
Hack News has contacted Google for comment, but the company had previously stated that they have taken measures to ban advertisements aimed at deceiving users to steal their information, and are actively committed to implementing countermeasures against such behavior.
SMS Phishing Attack: Pretending to Be the United States Postal Service
This disclosure follows the emergence of a SMS phishing campaign that uses the bait of failed package delivery, specifically targeting mobile device users, impersonating the United States Postal Service (USPS).
Fernando Ortega, a researcher at Zimperium zLabs, said in a report released this week, 'This activity employs complex social engineering strategies and an unprecedented obfuscation technique aimed at stealing credentials and leaking sensitive data through malicious PDF files.'
These SMS messages urge recipients to open the attached PDF file to update their address to complete the delivery. The PDF file contains a 'Click to Update' button that guides the victim to a USPS phishing web page, where they are asked to enter their mailing address, email address, and phone number.
The phishing pages also pretend to be service fees for reshipment to steal users' payment card information. The entered data is then encrypted and transmitted to a remote server controlled by the attacker. This activity has detected up to 20 malicious PDF files and 630 phishing pages, indicating that it is a large-scale operation.
Ortega pointed out, 'The PDF files used in this activity embed clickable links but do not use standard /URI tags, making it more difficult to extract URLs during the analysis process. This method allows known malicious URLs in PDF files to bypass detection by multiple terminal security solutions.'
This activity indicates that cybercriminals are exploiting security vulnerabilities in mobile devices to carry out social engineering attacks, taking advantage of users' trust in well-known brands and seemingly official communications.
Similar USPS-themed SMS phishing attacks also use Apple's iMessage to deliver phishing pages, a technique known to be adopted by Chinese threat actors known as the 'Smishing Triad'.
These messages also cleverly attempt to bypass an iMessage security measure that prevents links from being clickable unless the message is from a known sender or a user replies to an account. This is achieved by including 'Please reply Y' or 'Please reply 1' in the message to disable iMessage's built-in phishing protection.
It is noteworthy that this method was previously associated with a phishing-as-a-service (PhaaS) toolkit called Darcula, which has been widely used to target postal services like USPS and other well-known organizations in more than 100 countries.
Huntress researcher Truman Kain said, 'The scammers built this attack, which may explain why it is so common in the wild. The simple fact is, it works.'
Reference Source:
Malvertising Scam Uses Fake Google Ads to Hijack Microsoft Advertising Accounts
GamaCopy mimics the Russian Gamaredon APT and launches attacks against Russian-speaking targets
Guokr Cloud: Understand the security advantages of IPv6 upgrade and transformation in ten minutes
Full-patch domain forest collapsed in 5 seconds? Trust avalanche after encryption upgrade.
Indirect attack methods in LLM attacks and defense methods against LLM attacks
评论已关闭