Firstly, when it comes to hacker data cables, the product that comes to mind for all hackers must be this one from Hak5.

However, the price is not very friendly.

So what we are talking about today is not him...

Instead, it is the domestic hacker team HACKUSB, who have done a good job. This near-source penetration tool is号称 the first hacker data cable for young hackers, at least in terms of price, it is very attractive, with full functions and a price less than half of OMG.

The appearance is just a common data cable, and it comes with a配套 APP for effective loading.

Hack USB uses built-in Bluetooth 4.0 for connection, which can reach about 30M in normal use, and its distance will be even greater if the PRO version is used.
For the convenience of use and testing, it is equipped with a script repository, which is convenient for quickly calling and executing the perfect script instructions, saving the precious time of near-source penetration. Moreover, the script repository is not only available for you to download freely but also you can upload correct scripts freely for others to use. In order to increase the overall freedom and flexibility of the device while being convenient, a device keyboard is also added, which is convenient for us to simulate keyboard input and transmit our payloads for custom stealth attacks (well, I admit that this paragraph of introduction is copied from the official website hahaha)
But this thing has never been released, how can you test it!!!

But the妙 is that I happen to know their developer XiaoHuoLong, and after a pleasant friendly【P】交【交】流【易】with XiaoHuoLong, I happily got the internal test version of HACKUSB. Next, let's evaluate the specific feelings of use!
Firstly, according to his words, there will be a separate custom package when the official version is released, but it is obvious that I am not qualified for the internal test as a PY!

Is that it? I cried, and so did you!

Then open the package


On the surface, it looks like a data cable, but in fact it is a data cable. And it has been personally tested that it supports fast charging. To be honest, this detail of supporting fast charging is really good. The reason for replacing the cable of others when渗透 is that this fast charging charges fast, use this one.

Next, let's try to see the function of its near-source penetration

Insert the computer, open the APP for detection
Connected successfully, load a test payload to try the effect
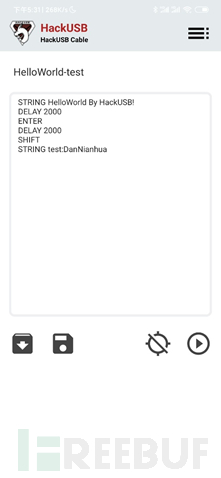
It's good, it's really fragrant
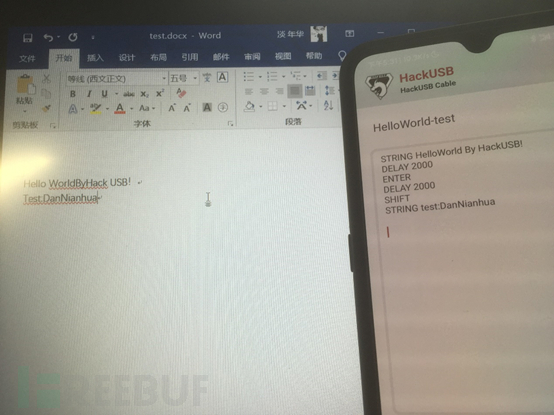
Next, I also randomly tested other scripts
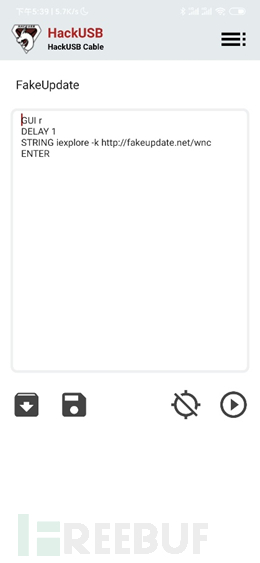
The things are basically problem-free, and in addition to the script library that the developer is gradually improving, it uses duck language, which is simple and easy to understand, and you can also build your own payload. The two scripts tested this time do not have any malicious content. When school starts, I will test my roommates in the dormitory and write another article to record how I performed near-source penetration testing.
Summary
Overall comments on HACKUSB, personally feel that it is a very good near-source penetration tool, with portability, camouflage, and in addition to the convenience and simplicity of the duck language used to write scripts, the developer also built a script repository, making it convenient for scriptless enthusiasts to call scripts and make changes.
However, I also pointed out the shortcomings to XiaoHuoLong, one is that it can only be operated through the mobile APP. If I replace the data cable of the penetration target and observe from a distance, when he inserts the computer, because the distance is too far, my phone cannot connect when it is out of range, if there is a computer-side, I can connect an external high-power Bluetooth signal receiver to HACKUSB for operation. But after I proposed it, he has already started to develop the computer version of the software, and said that he would increase the distance later through some means, and then wait for the official version to be released.
*Author: Danyuanhua, please indicate the source as FreeBuf.COM when转载.
评论已关闭