
In addition to many other research projects, HAL is also applied in university security courses: 《Introduction to Hardware Reverse Engineering】.
Function introduction
1. Natural directed graph representation of the network device list and its links;
2. Supports custom gateway libraries;
3. Optimized C++ core for high performance;
4. Modular: You can write your own C++ plugins for effective netlist analysis and operation;
5. Provides a rich user interface with support for visual detection and interactive analysis;
6. Integrated Python Shell, which can be used to interact with netlist elements and access the GUI interface;
7. The tool (v1.1.0) now supports Xilinx Unisim, Xilinx Simprim, Synopsys 90nm, GSCLIB 3.0, and UMC 0.18μm libraries;
API documentation
C++ documentation:【Gateway】
Python documentation:【Gateway】
Tool installation
Ubuntu
HAL's release version is released through ppa, you can get it from【Here】to obtain.
macOS
Use the following command andhomebrewInstall HAL:
brew tap emsec/hal
brew install hal
Build instructions
Run the following command to download and install HAL:
git clone https://github.com/emsec/hal.git && cd hal
https://www.freebuf.com/articles/endpoint/install_dependencies.sh
mkdir build && cd build
cmake
make
make install
macOS Build
A compiler that supports OpenMP is required, and we can install it using the following command:
brew install llvmThen run the following command to let cmake use our custom compiler:
cmake .. -DCMAKE_C_COMPILER=/usr/local/opt/llvm/bin/clang -DCMAKE_CXX_COMPILER=/usr/local/opt/llvm/bin/clang++Quick Start
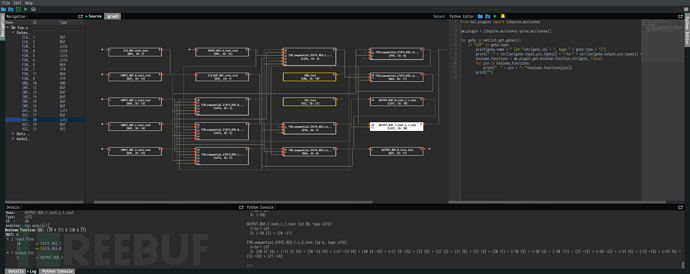
Researchers can install or build HAL using the command "hal -g" and start the GUI interface. Use the command "hal [--help|-h]" to view all available options of the tool. Sample netlists and sample libraries for analysis are provided in the examples directory, located at the path plugins/example_gate_library.
Load a code library from the examples directory and enable the graphical analysis feature. Use the integrated Python Shell or Python script window to interact with the target.
We can enumerate all lookup tables and output relevant information:
from hal_plugins import libquine_mccluskey
qm_plugin = libquine_mccluskey.quine_mccluskey()
for gate in netlist.get_gates():
if "LUT" in gate.type:
print(gate.name + " (id " + str(gate.id) + ", type " + gate.type + ")")
print(" " + str(len(gate.input_pin_types)) + "-to-" + str(len(gate.output_pin_types)) + " LUT")
boolean_functions = qm_plugin.get_boolean_function_str(gate, False)
for pin in boolean_functions:
print(" "+pin+": "+boolean_functions[pin])
print("")
For example, for the fsm.vhd sample, the output result is as follows:
FSM_sequential_STATE_REG_1_i_2_inst (id 5, type LUT6)
6-to-1 LUT
O: (~I0 I1 ~I2 I3 I4 ~I5) + (I0 ~I2 I3 I4 I5)
FSM_sequential_STATE_REG_0_i_2_inst (id 3, type LUT6)
6-to-1 LUT
O: (I2 I3 I4 ~I5) + (I1 I2) + (I0 I1) + (I1 ~I3) + (I1 ~I4) + (I1 ~I5)
FSM_sequential_STATE_REG_0_i_3_inst (id 4, type LUT6)
6-to-1 LUT
O: (~I1 ~I2 I3 ~I4 I5) + (I0 I5) + (I0 I4) + (I0 I3) + (I0 I1) + (I0 ~I2)
OUTPUT_BUF_0_inst_i_1_inst (id 18, type LUT1)
1-to-1 LUT
O: (~I0)
OUTPUT_BUF_1_inst_i_1_inst (id 20, type LUT2)
2-to-1 LUT
O: (~I0 I1) + (I0 ~I1)
FSM_sequential_STATE_REG_1_i_3_inst (id 6, type LUT6)
6-to-1 LUT
O: (I0 I2 I4) + (~I1 I2 I4) + (I0 ~I3 I4) + (~I1 ~I3 I4) + (I0 I4 ~I5) + (~I1 I4 ~I5) + (I2 I5) + (I2 I3) + (I1 I5) + (I1 I3) + (I0 I1) + (~I0 I5) + (~I0 I3) + (~I0 ~I1) + (I1 ~I2) + (~I0 ~I2) + (~I3 I5) + (~I2 ~I3) + (~I4 I5) + (I3 ~I4) + (I1 ~I4)
Reference Citation
If you need to use HAL in an academic or research environment, please use the following citation format to mark and use this framework:
@misc{hal,
author = {{EmSec Chair for Embedded Security}},
publisher = {{Ruhr University Bochum}},
title = {{HAL - The Hardware Analyzer}},
year = {2019},
howpublished = {\url{https://github.com/emsec/hal}},
}
You can also directly cite the original paper:
@article{2018:Fyrbiak:HAL,
author = {Marc Fyrbiak and
Sebastian Wallat and
Pawel Swierczynski and
Max Hoffmann and
Sebastian Hoppach and
Matthias Wilhelm and
Tobias Weidlich and
Russell Tessier and
Christof Paar},
title = {{HAL-} The Missing Piece of the Puzzle for Hardware Reverse Engineering,
Trojan Detection and Insertion},
journal = {IEEE Transactions on Dependable and Secure Computing},
year = {2018},
publisher = {IEEE},
howpublished = {\url{https://github.com/emsec/hal}}
}
License Agreement
The development and release of HAL follow the MIT Open Source License Agreement.
Project Address
HAL:【GitHub Gateway】
* Reference source:emsecFB editor Alpha_h4ck compiled, please indicate the source as FreeBuf.COM when转载
GoldDigger: a powerful file sensitive information search tool
Instaloctrack: A powerful OSINT open-source intelligence tool for Instagram.
CenoCipher: a powerful and easy-to-use encryption and steganography tool
graphw00f: A powerful GraphQL server engine fingerprinting tool
评论已关闭