In 2024, with the two major ransomware organizations ALPHV and LockBit being targeted, a new emerging threat named RansomHub quickly rose to prominence. The latest research by Group-IB shows that RansomHub has become an active player in the ransomware as a service (RaaS) field and has emerged as a major threat in a short period of time.
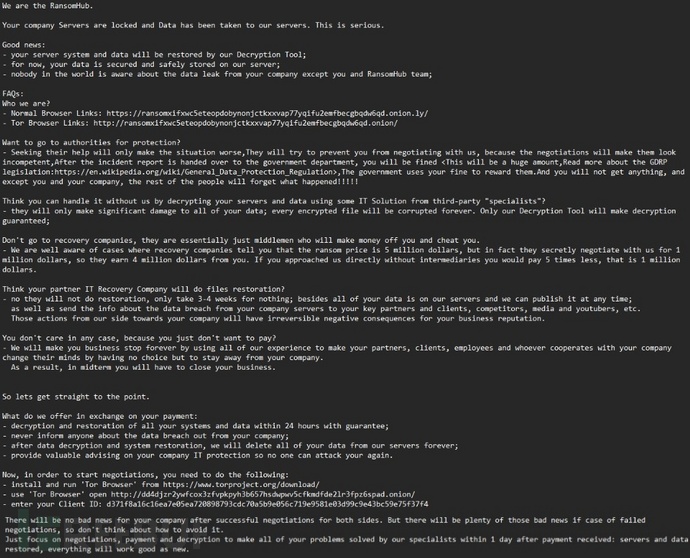
Ransomware organization's ransom note of RansomHub (Source: Group-IB)
The rise and operation strategy of RansomHub

RansomHub emerged in early 2024 and quickly became an important player in the ransomware field. Group-IB's investigation found that RansomHub strategically promoted its collaboration plans on underground forums (such as the RAMP forum) and actively recruited members from dissolved ransomware organizations, thereby rapidly expanding its influence.
In addition, research by Group-IB indicates that RansomHub likely obtained the source code of ransomware and web applications from the Knight organization (also known as Cyclops), highlighting the interconnectedness of the cybercrime world. By leveraging existing resources, RansomHub accelerated the development and deployment of its ransomware, quickly becoming a major threat.
The ransomware design of RansomHub has cross-platform compatibility and can target a variety of operating systems and architectures, including Windows, ESXi, Linux, and FreeBSD. This versatility allows it to maximize its potential targets.
Highly complex attack methods
The operation of RansomHub shows a high degree of complexity. They use advanced technologies, such as exploiting zero-day vulnerabilities and using tools like PCHunter to bypass endpoint security solutions. Their adaptability is reflected in their ability to weaponize newly discovered vulnerabilities quickly, often faster than defenders can patch. In addition, they are also proficient in traditional attack methods, such as brute-forcing VPN services.
After the initial reconnaissance and exploitation of vulnerabilities, RansomHub will establish persistence in the compromised network, conduct internal reconnaissance, identify and target key assets such as network-attached storage (NAS) and backup systems. Data leakage is their main goal, and they will use tools like Filezilla to transmit sensitive information to external command and control servers.
Final Stage of the Attack: Encryption and Ransom
The final stage of RansomHub attacks typically involves data encryption and ransom. They disable backup services and deploy ransomware to make data inaccessible, effectively paralyzing the victim organization. This ransomware has advanced features, including the ability to terminate virtual machines, delete shadow copies, and clear system event logs. This comprehensive approach aims to maximize the impact of the attack and increase the likelihood of a successful ransom.
Group-IB's report indicates that different variants of ransomware are optimized for specific platforms, each with its own set of command-line options. The Windows variant, in particular, provides extensive control over execution, including secure mode execution and network propagation features.
"RansomHub has targeted over 600 organizations worldwide, covering multiple industries such as healthcare, finance, government, and critical infrastructure, making it the most active ransomware organization in 2024."
——Group-IB
Typical Attack Case Analysis
Group-IB conducted a detailed investigation of a RansomHub attack that lasted less than 14 hours. The attackers initially exploited a vulnerability in the Palo Alto firewall (CVE-2024-3400), then gained access by brute-forcing VPN credentials. Subsequently, they exploited vulnerabilities CVE-2021-42278 (sAMAccount deception) and CVE-2020-1472 (ZeroLogon) to compromise domain controllers, laterally move to access NAS servers and shared folders, and leak data using Filezilla.
This attack ended with the disabling of backups, deployment of ransomware, and encryption of critical data. The attackers then left, leaving traces of their activities, which the Group-IB digital forensics and incident response (DFIR) team further investigated.
Outpost24's Chief Information Security Officer Martin Jartelius emphasized the importance of patching known vulnerabilities: "It is difficult to blame the victim in the case of zero-day vulnerabilities or supply chain attacks. However, if an organization is attacked due to a vulnerability that has been patched for over four years, it is clear that someone in the team deliberately took on a significant risk."
Reference Source:
RansomHub: The New King of Ransomware? Targeted 600 Firms in 2024
评论已关闭