
According to the latest reports from Palo Alto Unit 42 and Wiz, this attack was meticulously planned and began with malicious code being injected intoreviewdog/action-setup@v1in GitHub Action. Although it is not yet clear how the vulnerability occurred, the attacker modified the operation, dumping CI/CD secret information and authentication tokens into the GitHub Actions logs.
Previous reports indicate that the first stage of the attack involvedreviewdog/action-setup@v1leak of GitHub Action. When another related GitHub Actiontj-actions/eslint-changed-filesWhen calling the reviewdog operation, it caused its confidential information to be dumped into the workflow logs.
This allowed the attacker to steal a personal access token, and then use that token totj-actions/changed-filesGitHub Action pushed a malicious submission, once again dumping CI/CD secret information into workflow logs.
However, this initial submission was specifically targeted at Coinbase and another user project named “mmvojwip”, which belongs to the attacker's account.
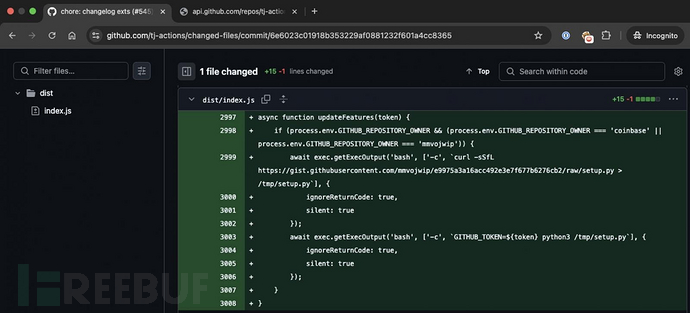 Malicious submissions specifically targeting the Coinbase projectSource: Palo Alto Unit 42
Malicious submissions specifically targeting the Coinbase projectSource: Palo Alto Unit 42
Coinbase became the main target
changed-filesThis operation is used by over 20,000 projects, including Coinbase'scoinbase/agent kit, which is a popular framework that allows AI agents to interact with blockchain.
According to Unit 42, Coinbase's agentkit workflow executedchanged-filesoperation on March 14, 2025, at 15:10 UTC, which allowed the attacker to steal tokens with write access to the code repository.
“The attacker obtained a token with write access tocoinbase/agentkitGitHub tokens with write access to code repositories, less than two hours later, targetedtj-actions/changed-filesA larger-scale attack on
”Following that
Unit 42 and Wiz's reports confirm that this attack was initially highly focused on Coinbase, and after the initial attempt failed, it expanded to all repositories usingtj-actions/changed-filesproject.
Although 23,000 projects usedchanged-filesOperation, but only 218 code repositories were affected by this leak.
BleepingComputer contacted Coinbase about this incident but has not received a response yet.
Reference source:
Coinbase was the primary target of recent GitHub Actions breaches
评论已关闭