1.How do you understand IAM?
In simple terms, IAM does only two things:

1) Identity proof and confirmation;
2) Grant permissions to access resources.
Using a vivid analogy, IAM is like when we want to enter a building, at this point we need to show our identity proof to verify our identity before we can enter the building.
The building administrator will manage and control your identity and permissions to ensure that only authorized individuals can enter specific areas or use specific resources. The administrator will assign different access cards to you based on your identity and needs to control which rooms or floors you can enter.
In this analogy,The building is like the innate digital world within the enterprise.Each floor or room represents the various informatization and digital systems and resources of the enterprise.It can even be refined continuously to the level of a certain system's menu, a certain function, or a certain resource; in certain specific scenarios, it may need to go even deeper into the control of data at the level of rows and columns.
The Identity and Access Management (IAM) system is like the management system of a building.It is responsible for creating, verifying, and managing user identity information, as well as distributing and controlling their access permissions.
It ensures that only authenticated and authorized individuals can access the required resources, while also recording and monitoring their entire access behavior for security audits and compliance checks.
How does the enterprise IAM system manage these identities and corresponding access permissions that need to enter the digital world of the enterprise?This is where we need to go back to IAM itself for an explanation.
2.What is the core content of IAM?
Firstly, let's take a look at the definition of IAM, English name: Identity and Access Management, Chinese translation: Identity and Access Management.
Literally, it can be broken down as identity + identity management + access control management.So what is identity? What is identity management? And what is access control?
Identity (Identity)refers to the way a person or entity is recognized and confirmed in a specific environment. It is usually composed of some elements such as features, attributes, roles, and permissions, used to determine the uniqueness and distinguishability of a person or entity. It is the twin copy of a physical world person or entity in the digital world.
Identity Management (Identity Management)refers to the processes and systems for managing and maintaining user identity information. It includes the lifecycle management of identity, such as creation, verification, authorization, updating, and revocation of user identity, to ensure that changes in identity information are mapped to the digital world in a timely and correct manner.
Access Control (Access Control)It is a security mechanism used to control access permissions to systems, applications, networks, or resources. It determines who can access what resources and under what conditions they can access. The purpose of access control is to protect sensitive information and prevent unauthorized access and data leakage.
According to the above definition, we can see thatThe core security management主线 of IAM is to ensure that the correct identity accesses the correct enterprise system or resource under the correct authorization.
But the core capabilities of IAM are not as simple as introduced above. According toGartner's introduction, the core capabilities of IAM include Identity Governance and Administration (IGA), Access Management (AM), User Authentication, and Privileged Access Management (PAM).
Behind each capability lies complex management concepts, security strategies, and technical implementations. In the other theme sharing of the book interpretation, IGA and PAM will be introduced in detail, and here we mainly introduce user authentication to everyone.
User AuthenticationIt refers to the real-time verification of identity requests that have been created, based on implicit or nominal confidence or trust, to enable access to digital assets. The essence of user authentication is to help identify known users and verify whether the requested identity belongs to the user who made the request.
Currently, many enterprises and institutions are increasingly interested in passwordless authentication technology for digital business, because it provides a better user experience and can avoid attackers exploiting the inherent weaknesses of passwords. For example, passwords may be stolen, and it is not uncommon for people to use the same password on multiple websites.
Currently, there are many methods that can realize passwordless authentication,For exampleFast Identity Online (FIDO) authentication, 'SMS token' authentication, OTP authentication, and so onIt is widely used to replace passwords.
3.What problems does IAM aim to solve?
Returning to practical applications, the invention and emergence of each technology is to solve practical problems in real life.Why do enterprises need IAM? What practical problems does IAM aim to solve?
The following figure very simply and accurately shows the role of IAM in practical applications.
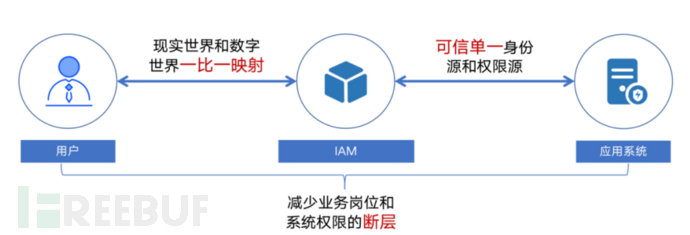
In simple terms, IAM is the link between the real world and the digital world. In order to map people or entities in the real world one-to-one to the physical world, it is convenient to establish a basis for mutual recognition in the digital world. Just like two people in the real world (whether they are familiar with each other or strangers) communicating and interacting, they often need to establish a basis for identity recognition.
However, having a one-to-one mapped identity is not enough; it is also necessary to establish a single credible and authoritative identity information.Otherwise, if either party lies or forges identities, effective comparison and authentication in the digital world will not be possible. Therefore, IAM also needs to provide credible and authoritative identity information for digital businesses and systems.
After ensuring the credibility of the identity, the next problem IAM needs to solve is the mismatch or disconnection between the access permissions of entities and objects and the business system resources.which is also the previously mentioned allowing the correct identity, under the correct authorization of permissions, to access the correct resources, thereby ensuring the security of enterprise data.
That isWhat kind of management idea or access control model does IAM base on to help enterprisesCan it effectively comply with laws and regulations and enterprise management requirements, thus safely and effectively controlling the identity and access control of the entire enterprise's internal digital world?
4.Access Control Model
Currently, there are two popular access control models in the industry, which can provide basic management ideas and frameworks for enterprise identity and access control management:
01 RBAC Model
Full English Name: Role-Based Access Control, translated as Role-Based Access Control.
That is, through defining a set of related permissions and access rules for different roles, each user is allocated one or more roles according to actual needs, and the executable operations and access resource permissions for the user are determined and granted based on the corresponding permission rules of the role.
This model simplifies the work of permission allocation and maintenance, reduces human errors and risks. However, at the same time, as the scale and complexity of the organization grow, the management of roles also becomes complex, and it is easy to have a role explosion phenomenon, even forming a unique role for each person (one person, one post), thereby increasing the complexity of management.
In addition, the RBAC model has limited control over permissions at a fine granularity, which is difficult to meet certain complex access control needs. Therefore, it is generally suitable for internal enterprise management, for users such as employees, partners, and suppliers, to manage permissions and access control.
02 ABAC Model
Full English Name: Attribute-Based Access Control Model, translated as Attribute-Based Access Control.
By describing the characteristics and attributes of users, resources, environments, and contexts, access rules and strategies based on these attributes are defined, such as 'Only senior management can access sensitive data during working hours.' Therefore, access control decisions are made based on the set attributes and strategies.
This model has high flexibility and can make dynamic access control decisions based on different attribute conditions, support fine-grained access control, and make access control decisions based on multiple attribute conditions, which is suitable for scenarios that require access control based on more complex attribute conditions.
For example, dynamic access decisions based on user attributes, resource attributes, and contextual information. However, this also causes the complexity of implementation and the increase in management and maintenance costs.
Currently,The popular zero-trust security architecture in the industry needs to be based on the ABAC model for access control management to meet the security concept of 'never trust, always verify'.
These theoretical systems and models provide different methods and frameworks for managing identity and access permissions to ensure the security and compliance of systems and resources. Enterprises can choose a suitable model based on their own needs and situations, and implement identity and access management in combination with best practices and security control measures to protect sensitive enterprise data and system security.
5.IAM Development History
Finally, let's take a look at the development of IAM. With the deepening of digital transformation, the increasing demand of enterprises for identity and access control, IAM technology is also evolving and upgrading gradually.
From the 3A level of identity and access managementAchieving authentication (Authentication), authorization (Authorization), and accounting (Accounting).
Among them, authentication is used to confirm the user's identity, authorization determines the user's access permissions in the system, and account management involves the creation, configuration, update, and deletion of user accounts, authentication, and permissions, etc.
Subsequently,4A adds Auditing to the 3A.This enables the recording and monitoring of user operational behavior for security auditing and compliance checks.
5A adds Analytics to the 4A.By continuously collecting and processing identity-related configuration, allocation, and usage data, we gain deep insights into operations and security, thus providing a basis for identity security governance and even predictive analysis.
From the development history of IAM, we can see that IAM is constantly being improved and strengthened. Therefore,In the process of implementing IAM projects, enterprises need to change their thinking and understand that the positioning of IAM should be as a driver of digital business, not just a security technology project.It requires continuous and long-term investment and cannot be treated as a one-time project.
In the future, IAM will continue to strengthen, especially with the support of new technologies such as AI, blockchain, big data, and algorithms.IAM will make corporate identity and access control management more efficient, automated, and intelligent.
评论已关闭