If you need to check more guest shares, please follow the 'Lord Brother's Experience' public account.
He Yi has always been the security director of Wánměng Shìjiè, sharing the 'The Path of Zero Trust Security Architecture Practice', which has high practical reference significance for security professionals in the gaming industry, and is recommended for reading.
Nie Jun
Tip: This article has 8421 words, and it takes about 40 minutes to read.
【Activity Preview】The Path of Zero Trust Security Architecture Practice
【Share Guest】He Yi
【Guest Introduction】Has been engaged in the security work of Party A for sixteen years, has built walls and built earth, and is currently responsible for the security work of Wánměng Shìjiè. Currently, mainly focuses on enterprise security construction, security architecture, zero trust, security analysis and response, APT counterattack, and data security. Changes jobs rarely, has more in-depth insights into enterprise security, and has a personal public account 'Xiaoyi Security', used for some output.
【Activity Time】Friday, April 24th, 7:00-8:00 PM, 60 minutes.
【Activity Form】Guests will share live on the topic of 'The Path of Zero Trust Security Architecture Practice' in the 'Financial Industry Enterprise Security Construction Practice' WeChat group in text form (about 40 minutes), followed by interactive questions and answers, about 20 minutes.
Please arrange your time, prepare your questions, and actively participate.
----------------------------------------------------------------
ByBelow is the transcript:
First of all, thank you, Lord Brother, for inviting me to have this opportunity to share something here. Now I will officially start. If anyone has any questions, they can communicate later.
The theme I share today is 'The Path of Zero Trust Security Architecture Practice', because it is a relatively large topic in itself, so I will focus on several issues, hoping that through the sharing, I can answer the following three questions:
Why to do it
How to do it
How is it going
In terms of the specific content of the analysis, it is divided into 6 chapters, namely:
Why the zero trust architecture is implemented
Analysis of zero trust architecture (Google BeyondCorp)
The essence of zero trust architecture as I understand it
Our design philosophy of zero trust architecture
Security Operations Based on Zero Trust Architecture
Subsequent issues
Why the zero trust architecture is implemented
Every time someone asks me this question, I always answer very unnaturally, because my answer is:We need to preventAPT

Yes, it's about Pig Hero and the screenshot of the group owner's WeChat circle, everyone can laugh for three minutes first, while I type.
Because when it comes to preventing APT, it is often laughed at, which is very normal. Someone even sent me a Baidu Encyclopedia about viruses and Trojans, patiently teaching me to distinguish between viruses, Trojans, and APT.
My personal understanding of APT is that APT is a targeted, persistent attack with strong concealment and incubation period. The attack has a strong purpose, and APT attacks do not necessarily use 0day, and APT teams are also分级, not all APT teams are GJ-level.
Many who do corporate security actually have no opportunity to truly encounter APT attacks, so I remember once during a meal, the rich general said that,can meetAPTHow fortunate an event is an attackThe reason for this is that if the value of the target of the attack is not high, the APT team has no need to spend a high cost to implement the behavior. For example, the most valuable asset of some internet companies may be user information, but such data is not purchased through APT but through the dark web, which is cheaper.
But there is a characteristic in the gaming industry, that is, the assets in the gaming industry are too easy to 'monetize'. Whether it is game code, game program, game server permissions, GM background permissions, player data, etc., these are high-value targets. The underground industry behind them has a huge annual output value.
We actually had multiple APT scenarios, and at that time, we even sought the help of flashsky and killer大佬 to analyze the samples. So, the biggest impact on us is that the difficulty of our security confrontation has increased. In this way, our previous security construction approach was like most people, mainly focusing on security analysis and bypass, trying not to interfere with business operations.
However, this approach requires a huge investment of resources to be done well, only companies with the scale of Alibaba can do it, so I turned to the construction of proactive protection. When doing protection, there were also some practical difficulties in front of me at that time, mainly the following points:
IT infrastructure governance is relatively primitive: it is unclear how many assets there are, how many accounts there are, and how many systems there are.
The attack surface is exposed in large quantities: firewall rules are virtually non-existent, NAT exposes services to the outside, each department has its own business, and the internal network can be compromised in one fell swoop.
These were the great challenges at that time.
During this process, in 2015, domestic security media were promoting Google's non-discrimination between internal and external networks, and even our company's CEO asked me about it. Then, I conducted a thorough assessment of BeyondCorp.
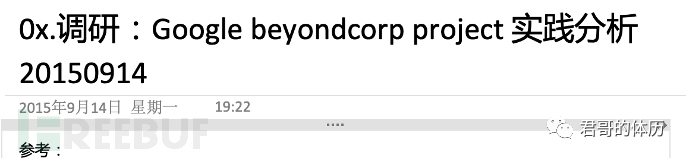
This was the evaluation report at that time, and the conclusion was actually pessimistic; we were completely unprepared.
Analysis of Zero Trust Architecture (Google beyondcorp
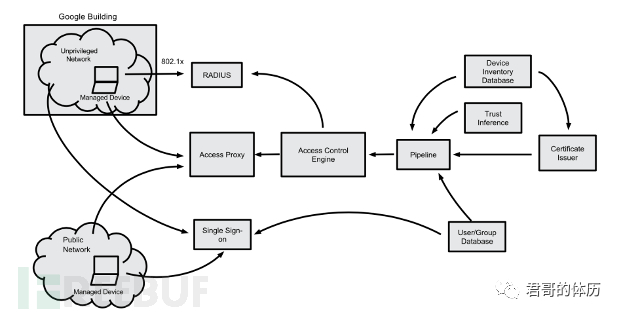
This is a diagram from Google's white paper at that time. After analysis, the conclusion was:
Not distinguishing between internal and external networks is not the core; it is just one of the results.
The core is the establishment of a trust chain, the continuous dynamic verification of security, and the reduction of the attack surface.
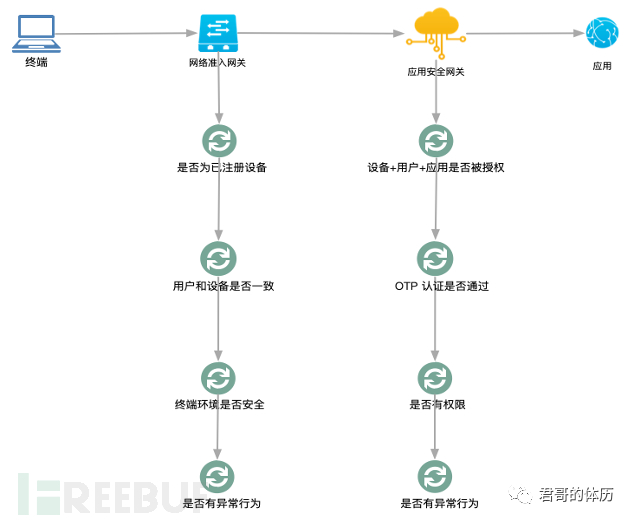
This is a diagram drawn previously, depicting the verification process experienced during a single visit application, from which one can see my understanding.The essence of Zero Trust architectureThat is to sayThe issues to be discussed in the third chapter
There are two gateways in this, namely the network access gateway and the application security gateway. Then, in a single access from the terminal to the application, there will be the following judgment logic on these two gateways.
In the network access gateway, the following points need to be evaluated:
Whether it is a registered device, unauthorized devices are prohibited from accessing the network;
Confirm whether the user and the device are consistent to prevent Zhang San from using Li Si's device;
Check whether the environment is secure, whether there are serious vulnerabilities, and whether security components have not been deployed;
Whether there are abnormal behaviors on the terminal, such as C2 access, etc.
This process is the judgment of the network access process. Here, we actually establish the first step of trust chain of 'user + device'.
In the application security gateway, there will be the following types of evaluations:
Whether the device + user + application has been authorized, if not, the process is interrupted;
Whether the strong authentication using OTP during login is successful;
Whether the user has access restrictions on some specific resources within the application;
Whether the user's behavior is abnormal, such as unauthorized attempts, data crawling, etc.
In this process, we actually establish the most important point in Zero Trust: the trust chain of device + user + application.
The above diagram is mainly used to explain the essence of Zero Trust, which is easy to understand. Below, we will talk aboutDesign of Zero Trust architecture
Design of Zero Trust architecture
When I first evaluated Google's solution, I gave up. In fact, it should be normal to think so, because Google is a big company with strong IT infrastructure and personnel. From any perspective, we are not equipped with such capabilities.
But later, I tried to decompose the BeyondCorp architecture based on my own understanding of security, and treat it as 5 issues.
User and device authentication and authorization management issues;
User authentication and authorization management issues with the application;
Network access management issues for user devices;
Issues with dynamic analysis and detection;
After the above implementations, can we assemble a trust chain of user + device + application?
After decomposing the issues, it is actually found that Google's BeyondCorp is not a black technology or a brand new technology, but a solution or integration based on the upgrade of traditional security technology.
So I think it can be done, and we officially started the Zero Trust architecture project internally in 2016. Of course, at that time, Zero Trust was not popular, so our internal code name was BeyondCorp.
Then when it comes to the project planning, considering our own resource situation, we have few people, lack of experience, and nothing to refer to, so I divided the entire architecture into 3 stages for implementation according to the above issues. The plan is to complete it within 2-3 years, but actually it was closed in 2019.
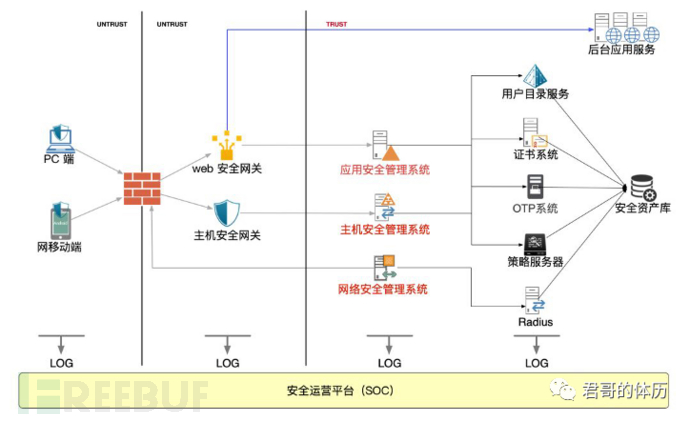
This is our architecture diagram, which can be referred to for the several issues I mentioned just now:
User and device authentication and authorization management issues:Host security management system
User authentication and authorization management issues with the application:Application Security Management System
Network Access Management Issues for User Devices:Network Security Management System
Issues with Dynamic Analysis and Detection:SOC
Assembly Problem: Overall Architecture Map
Due to time constraints, I will not go into detail about the functions in it. Subsequent articles will continue to write related articles for in-depth analysis, and those who are interested can go and see at that time.
Security Operations Based on Zero Trust Architecture
Because security operations and maintenance is also a very large topic, I focus on several scenarios to do some cases after using zero trust.
Scenario 1: Changes Brought by Asset Sorting
In the past, when dealing with security issues, emergency response, or APT countermeasures, the most afraid is to find problems but can't find people or locations, and it takes a lot of time to find through mac addresses.
So after deploying zero trust, we can establish:
"Person" -> Asset -> Asset Attributes -> Event
With such a multi-layered structure, it can be known how many assets a person has under his name, and the security status of the asset, and the events that have occurred to this asset. This query process is timely and can greatly improve efficiency.
Of course, during this process, many unknown assets will also be sorted out.
Sorry, it seems that the content is prepared too much, the time may be delayed a little
Scenario 2: Passwordless
Static passwords are very problematic things, in many APT incidents, we will find that the key moment is to obtain the administrator's password, such as operations and maintenance, network management, and then everything is lost.
So, I have been thinking about whether we can eliminate static passwords, and later, with the help of zero trust, I have also achieved this to some extent, because zero trust has converged many entry points, and we have done centralized authentication.
This topic will also cover a lot of content, those who are interested can read my previous article.
Zero Trust Architecture Practical Series: Kill Passwords, Passwordless Solution Implementation
He Yi talks about security, Public account: Talk about SecurityZero Trust Architecture Practical Series: Kill Passwords, Passwordless Solution Implementation
Scenario 3: Remote Work
Remote work should also be a content that many people are concerned about now, but we actually implement zero trust architecture not for remote work, in fact, we have not opened public network access for a long time.
The reason is actually very simple, after all, the confidence of small factories is not that strong, but because of the epidemic, we were forced to open, and the reason for the opening is actually because the basic conditions have been established in daily operations, including the uniqueness of users, the mapping of the relationship between users and devices, and the distribution of user permissions.
Therefore, the implementation of zero trust remote work has been supported for the whole group in a very short time from the decision to the opening, and I have also written an article about this.
Practical Application of Zero Trust Architecture in Remote Work
He Yi, Public Account: Talking SecurityPractical Application of Zero Trust Architecture in Remote Work
Subsequent issues
In general, my personal opinion is that it is still shallow, the framework has been set up, some plates have been added, but there are still many problems, and the cost and difficulty brought by each step forward are exponential, such as the zero trust shared by Zhang Ou last time, they have achieved the trust relationship between services, which we still can't do, and may not be able to do for a long time.
The deeper the later, the more deeply I realize that systems, architectures, and platformization are all tools. With good tools, you can achieve twice the result with half the effort. However, if you can't use the tools well, you may even hurt yourself. Therefore, the improvement of security operation capabilities and lean management are one of our important goals this year, and this is something we still need to learn from everyone.
In essence, the anxiety in the heart is growing, because the more I look ahead, the more I see deficiencies and problems, and I am also in urgent need of adding personnel and resources to strengthen the team, continue to fill in the gaps. This is also why the recent call for recruitment is so loud. But on the other hand, there is also a sense of seeing the dawn, believing that through these large amounts of practice and theoretical knowledge, security can be done better, and I also hope to go further.
Finally, in response to the previous question 'You are actually preventing APT attacks'. I believe we still can't prevent high-level APT attacks, but making APT more difficult and increasing the opportunity for detection should have been enhanced. I hope this iterative improvement process can be faster and increase more attack costs.
In the end, looking up to the big shot and looking down to work diligently, hoping to make some gains and some feedback along the way. Thank you all, and that's all for my sharing for now.
It seems to have exceeded the time limit, and it should be the time for questions now. Welcome everyone to ask questions!!!
Question and Answer Session
Q: General He, you are so tired. Ask, in the process of terminal access to the application, will the network access gateway and application security gateway as the front-end check points of access, that is, the first step of the trust chain, cause some loss to the user's access experience or latency? Will it affect the business?
A:There will be authentication login and the process of accessing the network, but the one-time login is valid for a long time, and the impact will not be too great.
----------------------------------------------------------------
Q: Thank you, General He, for sharing. I would like to ask if the beyond corp integration solution is based on VPN technology upgrade? Will it replace VPN in the near future?
A:It is not an integrated solution based on VPN, there are essential differences, and I have written detailed analysis articles on the differences, you can take a look at this article.
Zero Trust Architecture Practical Series: How to Choose Zero Trust Architecture
He Yi talks about security, Public account: Talk about SecurityZero Trust Architecture Practical Series: How to Choose Zero Trust Architecture
----------------------------------------------------------------
Q: Hello, General He, I have carefully read your sharing record and thank you very much. Because I have only read some documents, and do not have actual experience in implementing zero trust, so the assumptions of some of the questions I raised may not be correct.I feel that zero trust seems to be striving to ensure that each terminal entity is trustworthy, or trustworthy at the time of access. So, what effective and easy-to-promote methods do you have in the actual implementation process to build a trust chain (node trust) and how to effectively ensure the trustworthiness of the root node?
A: This understanding is correct, in addition to terminal trust, there is also user trust and permission trust.
----------------------------------------------------------------
Q:May I ask, in reality, there are many access paths for terminals or applications, and there are also mutual visits between applications, and accesses initiated by internal network devices. In network design, how to ensure that the normal access path must pass through the zero trust application security gateway.
A:Actually, we can do an interesting experiment. If you resolve the DNS of some Google internal systems, you will find that the addresses resolved are all the same. Therefore, web types can be resolved through reverse proxy. Other protocols need to do global proxy, and we have not yet implemented it.
----------------------------------------------------------------
Q:May I ask General He, from the functional perspective, in the future, should the access devices and zero trust gateway be merged for the zero trust?
A:This depends on the architecture direction you consider. The advantage of merging is that it is relatively simple, but the disadvantage is that it is not flexible enough. We are currently separated due to historical reasons, as it was done in stages, and it can also match different scenarios.
----------------------------------------------------------------
Q:General He is so helpful. May I ask you whether all the key elements in the implementation of zero trust are self-developed, or do you also purchase some existing security products?
A:Mainly relying on self-research, we have never purchased any products.
----------------------------------------------------------------
Q:May I ask General He, during the practical process, we also encountered considerable resistance at the convergence protocol, as our company has too many business application systems. How can we effectively promote the business to access the application gateway? Are there any tricks? If we want to implement the access of application systems and carry out authentication for each request, the transformation of the business system will be quite large, or if the gateway architecture is well designed, it can be adapted to application systems quickly.
A:Two aspects:
1. Check whether security is strong. If it is strong, do not connect. After three days, you will be disconnected from the Internet, and naturally it will come.
2. Authentication is a double-edged sword; the more secure it is, the more complex it becomes, and the higher the access cost; the more convenient it is, the less secure it is. It depends on how you choose.
----------------------------------------------------------------
Q:First of all, I would like to thank General He for his接地气的 explanation. Small factories are not daring to think about zero trust for internal applications and services yet. Regarding the authentication relationship between users and devices, is it necessary to bind them mutually? In reality, there are situations where one person uses multiple terminals and shared terminals. Both terminal access control and user access control are acceptable, of course, the authority is still based on the user. What should we mainly avoid to prevent Zhang San from using Li Si's terminal? What is the purpose?
A:We mainly aim for strong authentication, such as for specific systems, it must be this device, the request initiated by this user, and othersLaw prohibits.
----------------------------------------------------------------
Q:I would like to ask two questions:
1. What are the differences in the functions that can be realized by the fortress machine from the production and operation of the just introduced scheme (excluding remote access);
2. Lately, zero trust has received a lot of attention, mostly likely due to the need for remote access, and the scenarios of zero trust are more often used in office internal network or production internal network
A:1. The fortress machine is mainly used for the login access to the backend system, the authentication is based on user + password (static or dynamic), zero trust is the authentication relationship of user + device + permission, and the protection of business access
2. We do not differentiate between production and internal networks.
----------------------------------------------------------------
Q: I would like to ask, 1. The authentication and authorization of data flow at the network layer, application layer, and detailed level will bring a large amount of integration work and audit work. What issues should we pay attention to in the selection of implementation solutions, or good open-source solutions?
2. The asset relationship database also faces the same problem, whether to choose an open source solution or to develop independently?
A: 1. Our network access is a modified 1x solution;
2. We mainly rely on self-research.
-------------------------------------------------------------
Q: I would like to ask, how long did it take to sort out and map people and assets? What is the position of security here, is it a checker/supervisor (specifically done by IT)? Or an operational staff? How to ensure the effect?
A: This depends on your strategy, whether you sort it out yourself or rely on user self-awareness. For example, send notifications to allow users to register and bind themselves.
-------------------------------------------------------------
Q: I would like to ask, where are the key technical points or difficulties of passwordless core technology? How long did the promotion take? Where are the most business complaints?
A: The biggest difficulty is user habits, the most complaints are that I can't record my password, and I have to log in every day. The promotion time is very long, we are a small part of forced otp to most otp, with a 1-2 year cultivation period in the middle.
-------------------------------------------------------------
Q: One more question, how many system groups need to be built to build a zero trust architecture? Are they all self-developed?
A: We currently have more than 20 systems of various sizes, and there are dozens of servers including SOC, mainly self-developed.
-------------------------------------------------------------
Q: I would like to ask Mr. He, how to solve the access problem for non-computer devices such as printers and cameras in such a unit's internal network?
A: Access is not available, and dumb terminals are all allowed to pass on the whitelist.
-------------------------------------------------------------
Q: One more question, how many system groups need to be built to build a zero trust architecture? Are they all self-developed?
A: We currently have more than 20 systems of various sizes, and there are dozens of servers including SOC, mainly self-developed.
-------------------------------------------------------------
Q: I would like to ask, how far can the dynamic detection of terminal environments be achieved now?
A: Generally speaking, it is not as good as commercial EDR products.
-------------------------------------------------------------
Q: In the sharing mentioned, how are the abnormal behaviors of users, such as unauthorized attempts and data crawling, set by the application gateway rules or UBA联动?
A: We analyze through SOC, and the application gateway does not have complex rule engines.
-------------------------------------------------------------
Q: I would like to ask, about network access gateway confirming user identity and device matching, how can user, device, and authorization be authenticated through the authentication of network access similar to wifi portal authentication? Are there any solutions that can authenticate at the same time? Or does the network transmit identified and authenticated MACs after authentication? Similar to wifi portal authentication network access, if an attacker connects to a free wifi, performs an arp to obtain the MACs of devices that have been authenticated in the surrounding network, can forging MAC access bypass the network access gateway?
A: There needs to be an agent deployed to the terminal, and access is granted by the agent + device certificate, and the access authorization is not based on MAC address.
-------------------------------------------------------------
Q: Thank you for Mr. He's wonderful sharing. My question seems to have been passed over, and I would like to know the following specific questions:
1. Is micro-segmentation a necessary condition in the implementation of zero trust?
2. Currently, the granularity of zero trust gateway permission management is at the application server level or down to the URL level.
3. If the application has a need to display data classified by user security level, how can the existing zero trust solution achieve the transmission of user security status?
A: 1. It is not a necessary condition, but can add more value;
2. Usually to the application, specific situations can be based on URL, depending on the needs and cost;
3. We have a hierarchical authorization setting, but there is no application that displays content based on the security level. However, this is a good idea, but the scenario may not be too many, and more applications are internally classified.
-------------------------------------------------------------
Regarding the sharing mentioned in “About multi-layer structure relationships: people -> assets -> asset attributes -> events. If different business lines all have such a structure relationship, and further refine and extend based on this relationship structure, the asset structure tables maintained by different business lines are not unified. It is very convenient for each branch to maintain independently, but it is also a problem for the overall security of the group. The investigation will still take time.
Q:I would like to ask how to unify the asset structure for different departments or business branches?
A: Currently, we handle the relationship between users and office terminals well, because zero trust can strongly bind them, but there are still significant problems with the relationship between administrators and servers, which cannot be strongly bound, leading to high maintenance costs.
-------------------------------------------------------------
Q: Please ask two questions:
1. The access authentication and authorization at the application layer, data flow network layer, and details will bring a lot of integration work and auditing work. What issues should the selection of the implementation plan pay attention to, or what are good open source solutions?
2. The asset relationship database also faces the same problem, whether to choose an open source solution or to develop independently?
A: 1. The bastion host is mainly used for logging in to the backend system, and authentication is based on user + password (static or dynamic). Zero trust is an authentication relationship between user + device + permissions, and protection of access to the business.
2. We do not differentiate between production and internal networks.
-------------------------------------------------------------
Corporate security construction cannot do without "mutual assistance". The WeChat group for corporate security construction in the financial industry,Group entry method: Please add the following WeChat as a friend, and note: Name-Company-Domain of Responsibility.Sales personnel are temporarily not invited into the group, and we cannot guarantee that every applicant will be admitted to the group. Please understand.
评论已关闭
