Historical articles:
Firmware analysis technology (1) - Introduction

Firmware analysis technology (2) - Tool usage
Firmware analysis technology (3) - Vulnerability reproduction
The article was first published on the official account: Weld the car door shut
First, overview:
Generally, the problem will provide a firmware of an IOT device for analysis to obtain the flag. There are relatively few CTF questions related to firmware analysis on the network, so here are three questions listed as an introduction.
Second, reproduction of the contest:
BUUCTF-firmware
(1) Firmware Extraction
Download the firmware and use binwalk to extract.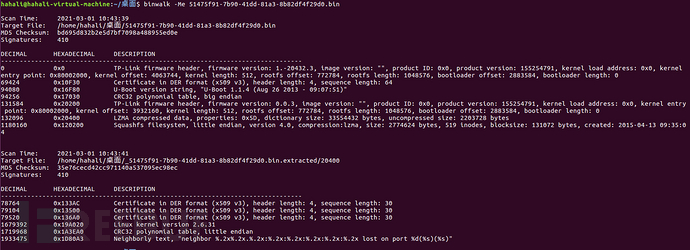
After unpacking, it is found that there is still another 120200.squashfs file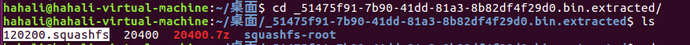
After unpacking, it is found that there is still a 120200.squashfs file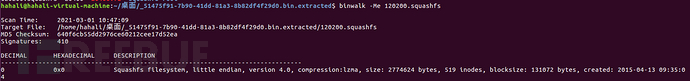
The problem requires analyzing the remote server and port used by the backdoor program.
The tmp folder contains the backdoor program we want:
Put it into IDA for analysis, and it can be seen that it is an ARM architecture
(2) Shell detection and stripping
Before putting it into IDA for analysis, use a shell detection tool to check whether it is packed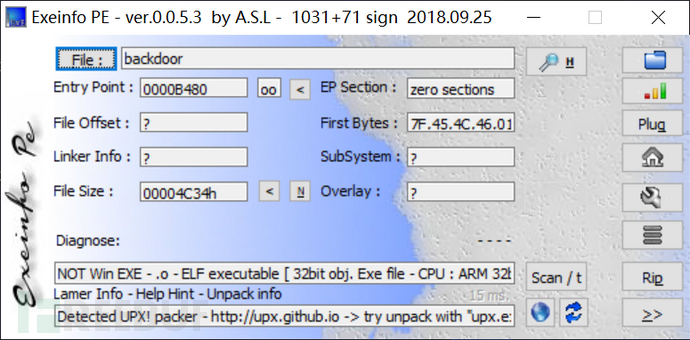
Prompt that there is a shell, we can use upx to strip the shell
Install upx on Unbuntu: apt-get install upx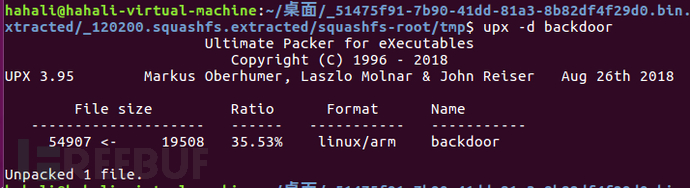
After stripping, we put the backdoor file into IDA for analysis.
(3) Code analysis
Since the problem asks us to find the MD5 encrypted result of the URL + port, we only need to find the URL and port in the String window.
View strings
View --> Open subviews --> Strings
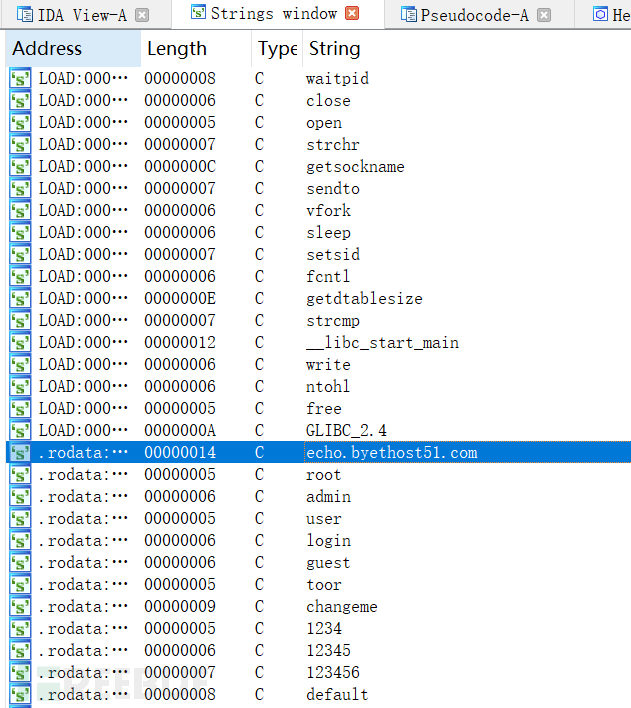
The flag is for the remote server and port. Find the server address first and then find the port.
Use F5 to decompile and find the initConnection function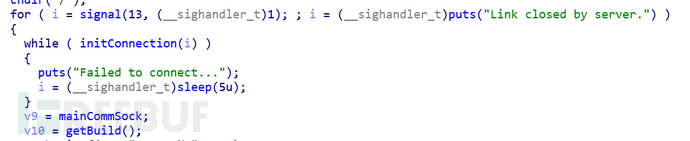
Double-click to enter, find the port: 36667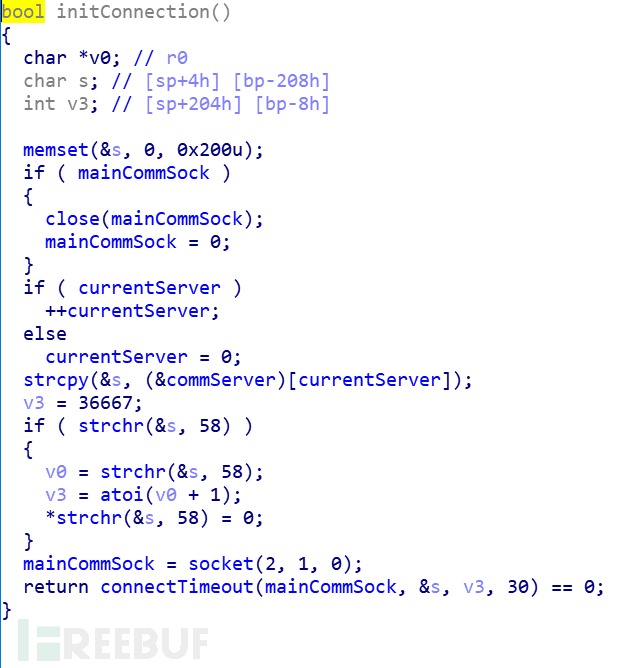
Finally, convert the URL and port to MD5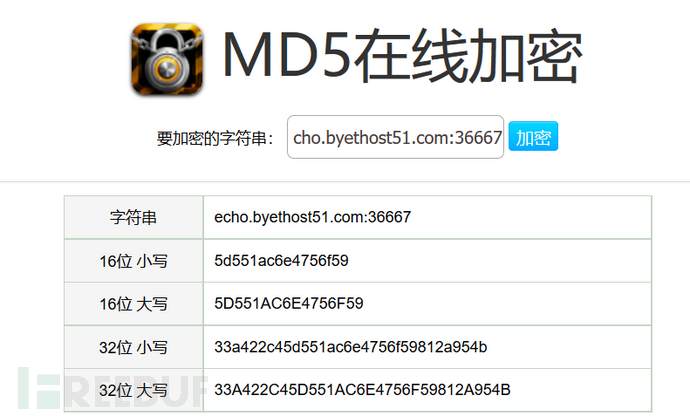
flag{33a422c45d551ac6e4756f59812a954b}}
CTFHUB-Secondary device firmware reverse engineering
(1) Firmware Extraction
Download and unzip the firmware.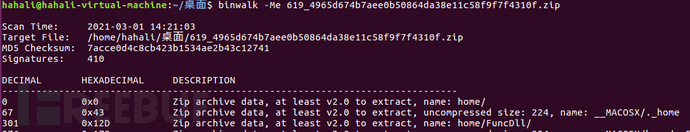
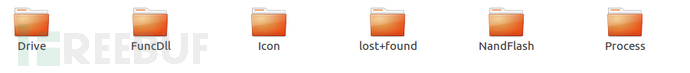
After unzipping, it exists in the home folder.![]()
FuncDll # Dynamic link library
Icon # Icons and configuration files
NandFlash # Storage
Process # Running program code
lost+found # Empty
According to the requirements of the question, we need to find hardcoded or vendor backdoor passwords and search using keywords.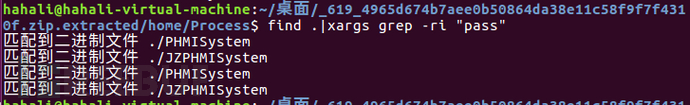
After analysis, it was found that the flag exists in the JZPHMISystem file:
https://www.freebuf.com/articles/endpoint/Process/JZPHMISystem: inputPassword
https://www.freebuf.com/articles/endpoint/Process/JZPHMISystem: passWd.c
https://www.freebuf.com/articles/endpoint/Process/JZPHMISystem: rootPasswd
https://www.freebuf.com/articles/endpoint/Process/JZPHMISystem: passWdPID
https://www.freebuf.com/articles/endpoint/Process/JZPHMISystem: inputPassword
https://www.freebuf.com/articles/endpoint/Process/JZPHMISystem: InputPwd_pro
https://www.freebuf.com/articles/endpoint/Process/JZPHMISystem: InputPwdPro
(2) Code Analysis
Drag the JZPHMISystem file into IDA for analysis.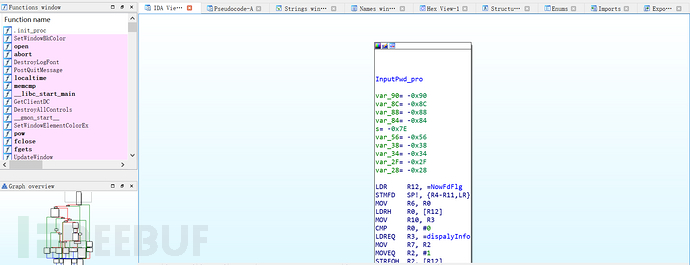
Based on the keyword search from before, I found the inputPassword and InputPwd_pro functions, and InputPwdPro is located at a bss section.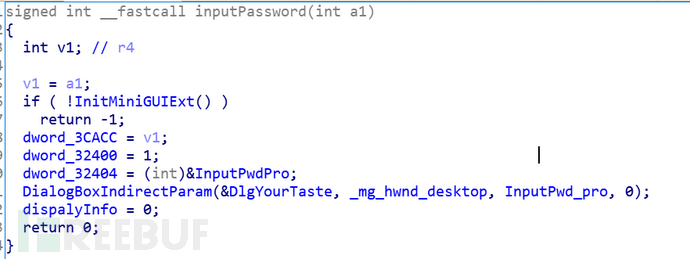
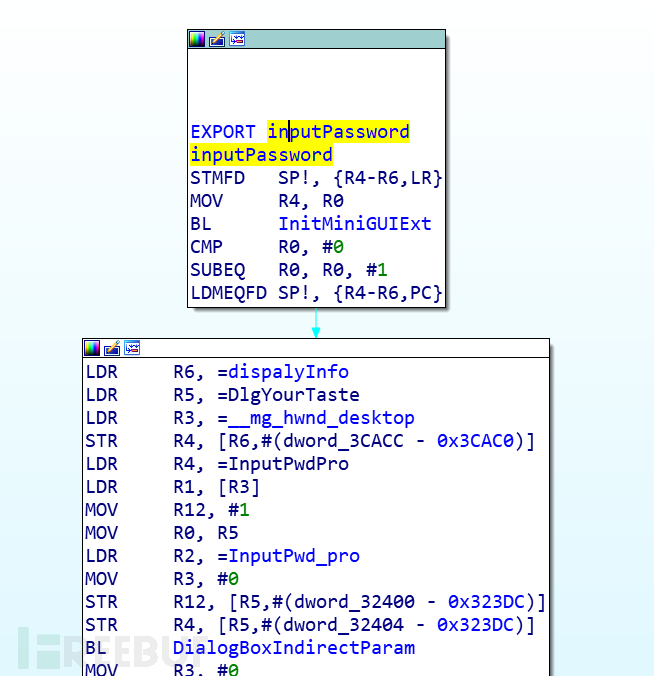
However, rootPasswd, passWdPID, and passWd.c could not be found, and searching the global memory of hex-view did not yield any results either. It was only after watching the explanation by the big shot that I realized it was a symbol. By selecting view->opensubview->Names in the IDA toolbar, I finally found rootPasswd.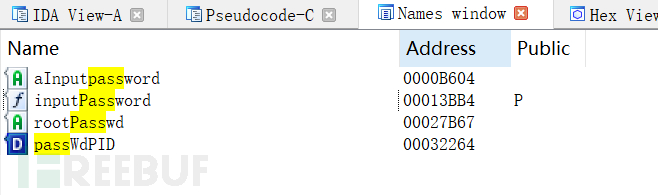
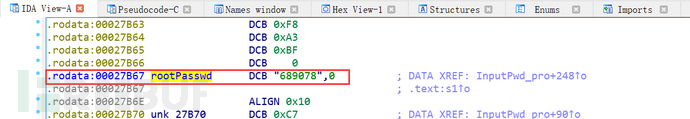
The password is 689078
CTFHUB-Simple firmware reverse engineering
This firmware uses the Schneider PLC Ethernet module firmware noe77101, and the solution refers to 'Firmware Analysis Technology (3) - Firmware Vulnerability Reproduction'.
评论已关闭