Overview
At the beginning of 2023, the 360netlab team published an article titled 'Be Alert: The Modified Hive Attack Suite from the Leaked CIA Project Enters the Black and Grey Production Field', which described how attackers used the leaked source code of the Hive project from the CIA, modified the Hive attack suite under the CIA organization, and not only further protected the trojan communication traffic but also added many functional commands based on the original code.
In a review, it turns out that the source code of the Hive attack suite was publicly released by WikiLeaks as early as 2017. The public information released included part of the source code and executable programs of the early version of the HIVE project, and also introduced that the HIVE project is a remote implant trojan used internally by the CIA, developed by the EDB department, communicating via HTTPS protocol, mainly used for controlling target machines and stealing sensitive information.

Although several years have passed since the leaked source code of the Hive project, I have conducted research on the CIA Hive project from the following perspectives, adhering to the attitude of technical research and learning from the world's top trojan attack suites:
Based on the leaked source code of the Hive platform, I simulated the production compilation environment of the CIA Hive attack suite: by building the cross-compilation environment, I can freely build different architecture samples suitable for mt-x86, mt-mips, mt-mipsel, mt-ppc, linux-x86, sol-x86, sol-sparc, and other platforms;
Based on the leaked information and the newly compiled Hive attack suite, I simulated the attack scenario of the CIA Hive attack suite: the server trojan can run secretly on the controlled host, and it will only start network behavior and go online when it receives the
Based on reverse engineering, packet encryption and decryption technology, I simulated how to restore the attack chain of the CIA Hive attack suite from the perspective of data packets when the behavior of the CIA Hive attack suite is detected: I conducted a detailed analysis and comparison of the encryption and decryption algorithms used in the CIA Hive attack suite, and proposed my thoughts on the extraction of encryption keys;
Cross-compilation environment setup for Hive platform
There are many analysis articles about the leaked information of the CIA Hive platform on the network. Everyone can read them by themselves and extract different branch version codes from the leaked projects. The relevant screenshots are as follows:
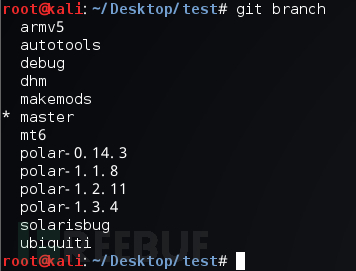
After successfully extracting the source code of the CIA Hive attack suite, I analyzed the source code and found that there are Makefile files in the client, server, ilm-client, and common directories. The Makefile file in the common directory is used to compile server-side programs suitable for mt-x86, mt-mips, mt-mipsel, mt-ppc, linux-x86, sol-x86, sol-sparc, and other systems. The relevant screenshots are as follows:
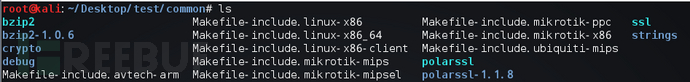
Further analysis of the Makefile file in the common directory reveals that this Makefile file is mainly used to configure the compiler required for compilation. From the Makefile file, I extracted and analyzed that this project uses buildroot (an open-source toolset for embedded systems that can automate the construction of embedded Linux systems) to build the cross-compilation toolchain. The relevant screenshots are as follows:
After gaining a general understanding of the cross-compilation environment framework of this project, I attempted to simulate the construction of the buildroot cross-compilation environment to compile the project source code, and the detailed operation process is as follows:
Configure and run the buildroot cross-compilation environment
The operation steps to build the buildroot cross-compilation environment are simple, but the construction process is not very smooth. The author has tried many times before successfully building the buildroot cross-compilation environment.
Since the version of buildroot used in the source code is 'buildroot-2010.11-x86', in order to avoid abnormal situations caused by version mismatch during the subsequent compilation of the source code, the author has chosen a 32-bit operating system and a compromise version of buildroot for testing. The actual compilation environment operating system used by the author is 'ubuntu 16.04 LTS 32-bit', and the buildroot version is 'buildroot-2017.11.tar.gz'. The buildroot cross-compilation tool can be downloaded from 'https://buildroot.org/downloads/'.
The steps to build the buildroot cross-compilation environment are as follows:
Basic library environment configuration
When building the buildroot cross-compilation environment, due to the lack of some library environments, the compilation may fail. Therefore, it is recommended to install some library environments in advance.
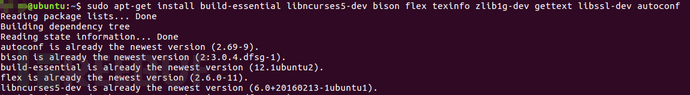
sudo apt-get install build-essential libncurses5-dev bison flex texinfo zlib1g-dev gettext libssl-dev autoconf gcc-multilib
The relevant screenshots are as follows:
Configure buildroot
Before the official compilation, it is necessary to configure buildroot first, and the following command can be used for compilation configuration.
make menuconfig
The relevant screenshots are as follows:
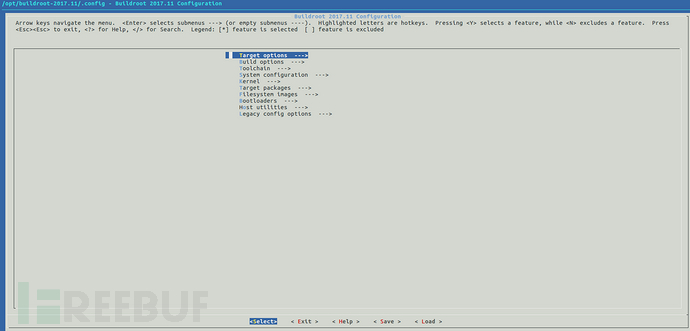
The functional meaning of each tab in the configuration menu is as follows:
| Option menu | Function meaning |
|---|---|
| Target options | Target options: This tab includes some configuration options related to target platforms and architectures, such as target processor architecture and target device model. |
| Build options | Build options: This tab includes some configuration options related to the build process, such as the build method and parallel compilation options. |
| Toolchain | Toolchain: This tab is used to configure options related to the cross-compilation toolchain, such as selecting the toolchain type and setting paths. |
| System configuration | System configuration: This tab includes some basic system configuration options, such as the root filesystem type and init system selection. |
| Kernel | Kernel: This tab is used to configure options related to the Linux kernel, such as selecting the kernel version and configuring kernel parameters. |
| Target packages | Target packages: This tab is used to select and configure the software packages to be built into the target system. |
| Filesystem images | File system images: This tab is used to configure the format and content of the generated file system image, such as selecting the file system format, adding additional files, etc. |
| Bootloaders | Bootloaders: This tab is used to configure options related to the bootloader, such as selecting the bootloader type, configuring bootloader parameters, etc. |
Through comparison, configure the Target options to meet the basic compilation requirements, as shown in the relevant screenshots:
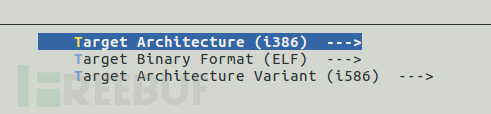
Compile buildroot
You can start the compilation with the following command, the compilation process will take a long time, it may take several hours, because the entire Buildroot toolkit is only about 5MB in size, so a lot of third-party libraries need to be downloaded during the compilation process. Moreover, abnormal situations may occur during the compilation process, and handling these may further extend the compilation time. (Tip: Try building a proxy environment, which can effectively improve the download speed of third-party libraries.)
make
The relevant screenshots are as follows:
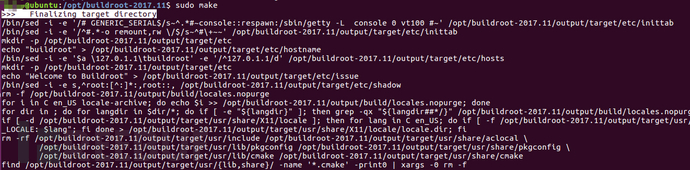
Compilation output files
After compilation, Buildroot will store the final generated files in the output directory. Under the output directory, there will be 4 directories, used to store different data.
| Directory | Meaning |
|---|---|
| images | Used to store the generated system image files. These may include root file system images, kernel images, bootloader images, etc. These image files can be directly burned to the storage medium of the target device to start and run the final embedded system. |
| host | Used to store the host toolchain generated by Buildroot during the build process. The host toolchain is a collection of tools used to compile and run the target system on the development host, such as cross-compilers, debuggers, etc. |
| staging | Used to store the basic file structure of the target system after cross-compilation, including header files, library files, and symbolic links, etc. These files can be used as the basic file system of the target system or for developers to use when cross-compiling applications. |
| target | Used to store the complete file system of the target system. This file system can be directly copied to the storage medium of the target device and used in conjunction with the corresponding kernel image and bootloader image to start and run the final embedded system. |
Through comparison, focus on the host directory, where we find the cross-compile tools we need. The relevant screenshots are as follows:
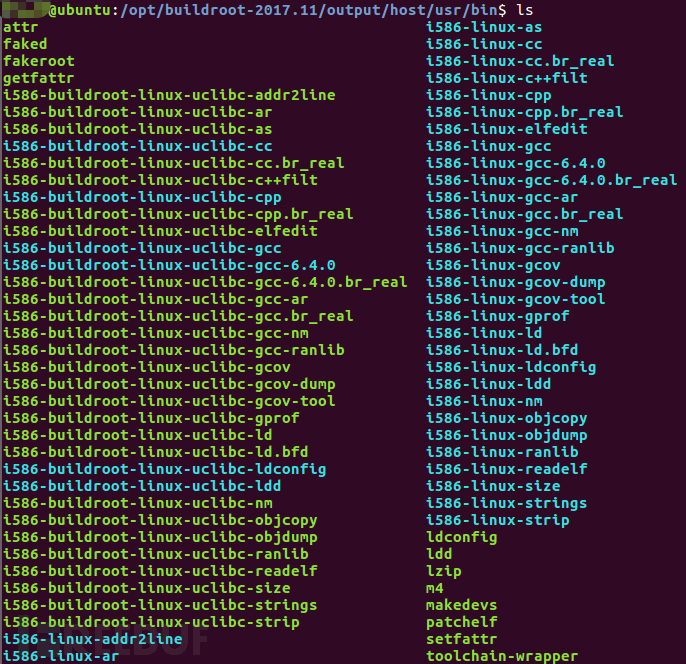
Compile the Client
Note: Since the client-side program can be compiled directly based on the compiler provided by the operating system, there is no need to modify the Makefile file to compile the program normally.
Firstly, enter the client directory and execute the make command to view detailed compilation parameters, as shown in the following screenshots:
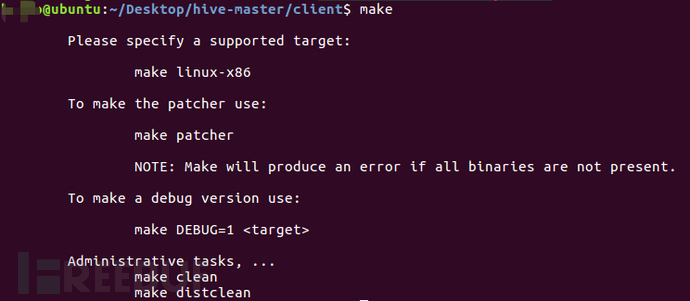
According to the prompts, sort out the supported commands as follows:
make linux-x86 #Compile 32-bit client program
make linux-x86_64 #Compile 64-bit client program
make patcher #It is necessary to build all supported versions of the server program before executing the build
make DEBUG=1 linux-x86 #Compile 32-bit dbg version of the client program
make clean #Clean up intermediate files generated during the build process
make distclean #Restore the build environment to its initial state completely
After the client program is built successfully, the screenshot is as follows:
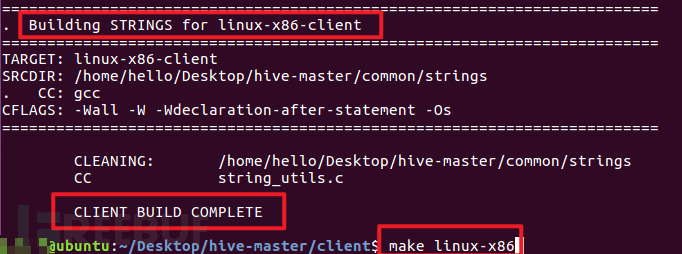
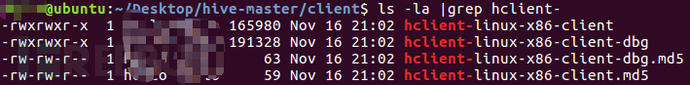
After executing the 'make linux-x86' command, the default will build 2 ELF executable files and 2 md5 checksum files, as shown in the following screenshots:
Compile the Server-side
Note: Since the server-side program requires cross-compilation, the Makefile file on the server side needs to be modified in order to compile the server program normally.
Firstly, enter the server directory and execute the make command to view detailed compilation parameters, as shown in the following screenshots:
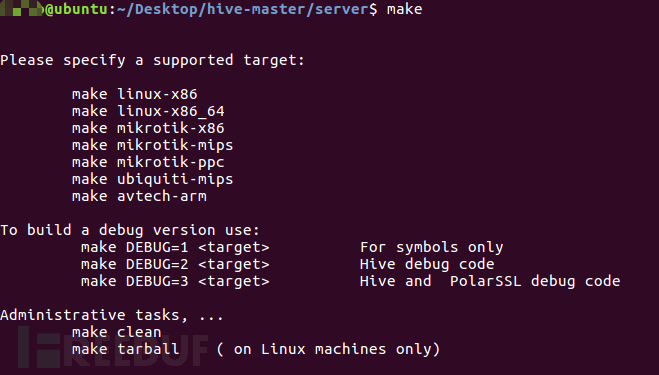
According to the prompts, sort out the supported commands as follows:
#Compile the server program for the corresponding architecture
make linux-x86
make linux-x86_64
make mikrotik-x86
make mikrotik-mips
make mikrotik-ppc
make ubiquiti-mips
make avtech-arm
#Compile the dbg version program for the corresponding version
make DEBUG=1 <target> For symbols only
make DEBUG=2 <target> Hive debug code
make DEBUG=3 <target> Hive and PolarSSL debug code
make clean #Clean up intermediate files generated during the build process
make distclean #Restore the build environment to its initial state completely
linux-x86
Modify the Makefile file
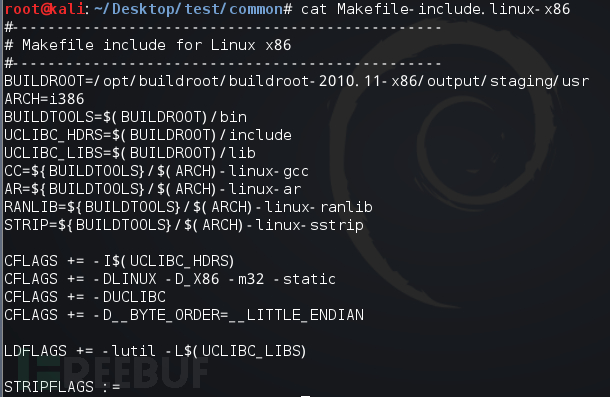
When compiling the server program under linux-x86, it is necessary to reconfigure the Makefile-include.linux-x86 file under the common directory, as shown in the following screenshots:
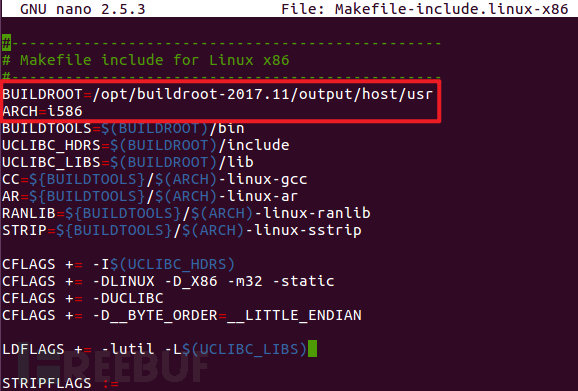
Compile the server program
After modifying the Makefile file, simply execute the 'make linux-x86' command to compile the server program, as shown in the following screenshots:
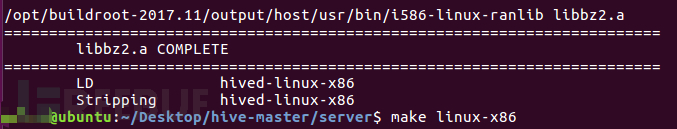
执行”make linux-x86“命令后,默认将构建1个ELF可执行文件,1个md5校验文件,相关截图如下:
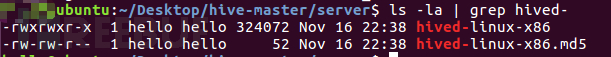
After executing the 'make linux-x86' command, by default, 1 ELF executable file and 1 md5 checksum file will be built, as shown in the relevant screenshots below:
Exception handling
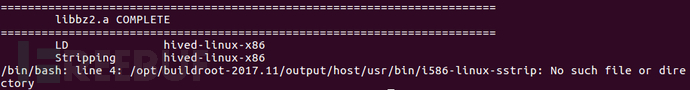
During the compilation process, the following errors may occur, indicating that the i586-linux-sstrip file cannot be found. The relevant screenshots are as follows:
#Compile to generate sstrip file
xxx@ubuntu:~/Desktop$ tar -zxvf ELFkickers-3.2.tar.gz
......
xxx@ubuntu:~/Desktop$ cd ELFkickers-3.2/
xxx@ubuntu:~/Desktop/ELFkickers-3.2$ ls
bin COPYING ebfc elfrw infect Makefile objres rebind
Changelog doc elfls elftoc INSTALL MANIFEST README sstrip
xxx@ubuntu:~/Desktop/ELFkickers-3.2$ make
......
xxx@ubuntu:~/Desktop/ELFkickers-3.2$ ls bin/
ebfc elfls elftoc infect objres rebind sstrip
xxx@ubuntu:~/Desktop/ELFkickers-3.2$
#Handle exceptions
xxx@ubuntu:~/Desktop/ELFkickers-3.2$ sudo cp https://www.freebuf.com/articles/system/bin/sstrip /opt/buildroot-2017.11/output/host/usr/bin/i586-linux-sstrip
xxx@ubuntu:~/Desktop/ELFkickers-3.2$
mikrotik-mips
By building a MIPS architecture cross-compiler, it is possible to normally compile server programs under the MIPS architecture.
The output screenshot of the host directory under buildroot is as follows:
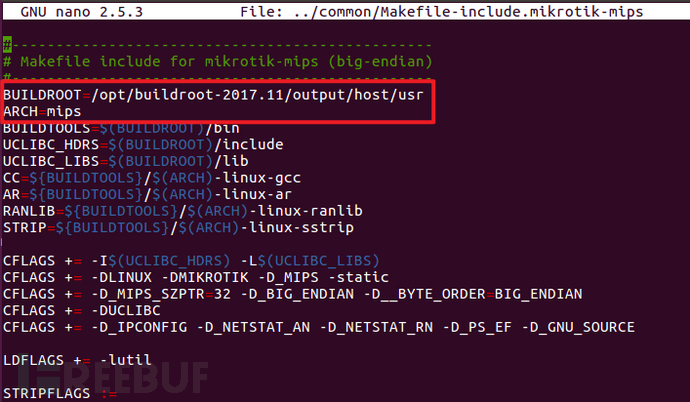
Makefile file screenshot is as follows:
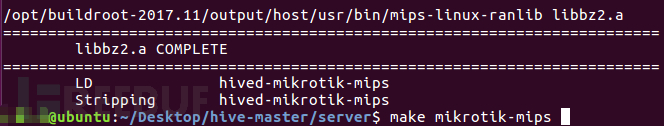
After compilation is successful, the relevant screenshots are as follows:
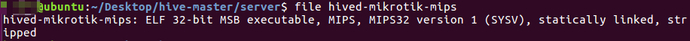
solaris-sparc
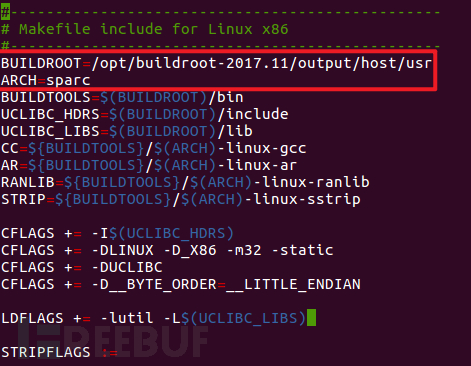
By building a sparc architecture cross-compiler, it is possible to compile server programs under the sparc architecture normally. Since there is no solaris-sparc option in the makefile, it is also possible to successfully compile server programs under the sparc architecture by directly modifying the Makefile-include.linux-x86 file.
The output screenshot of the host directory under buildroot is as follows:
Makefile file screenshot is as follows:
After successful compilation, the file information screenshot is as follows:
Sample usage scenario reproduction
Through analysis, it was found that executable programs exist in the directories snapshot_20141017-1409、snapshot_20141217-1052、snapshot_20141107-1345 under the leaked source code, and attempts were made to simulate and reproduce them, but they failed to run successfully directly. Further analysis found that this was due to multiple reasons such as the version of the executable program and the expiration of the certificate.
Further sorting out the usage methods of the CIA Hive attack suite, the detailed situation is as follows:
Replace SSL certificate
Since the built-in SSL certificate has issues such as expiration, it is necessary to update the certificate files, and the relevant command screenshots are as follows:
openssl genrsa -out ca.key 2048
openssl req -new -key ca.key -out ca.csr
openssl x509 -req -days 3650 -in ca.csr -signkey ca.key -out ca.crt
openssl genrsa -out server.key 2048
openssl req -new -key server.key -out server.csr
openssl x509 -req -CA ca.crt -CAkey ca.key -CAcreateserial -days 365 -in server.csr -out server.crt
rm ca.csr ca.key ca.srl server.csr
Trojan online
The CIA Hive attack suite supports two methods for online trojans:
Generate the built-in command line server-side program using the hive-patcher program;(Through testing, it was found that the hive-patcher file contains built-in server programs for various architectures, so it can be run independently to output the server program)
Run the server-side program directly using the command line method;
Patcher
评论已关闭