Operational summary
- Boundary erosion has caused serious trust issues within the security community. If you cannot trust the message you receive, you must trust the person who sends the message. This means you must figure out who this person is, why they are trying to interact with you, and whether you should open the message.
- As of 2023, 75% of security vulnerabilities are caused by poor identity, access, or permission management. A report from 2020 found that 79% of organizations have experienced identity-related breaches in the past two years. If identity-related issues could be resolved once and for all, then most other security products would no longer be needed. However, it is very difficult to completely resolve identity-related issues.
- Almost half of organizations use more than 25 systems to manage identity and access permissions. As companies grow, acquire, and are acquired, and as there are changes in the identities and permissions of middle-level managers in a short period of time, and as the adoption from the bottom up continuously weakens in centralized procurement, identity complexity will only get worse.
- Novell was founded in 1979 and became an early pioneer in managing identity and access through file-sharing systems, which allowed administrators and users to control access at the file level (instead of the entire disk volume level). This meaningfully changed the industry's view of access control.
- Novell's annual revenue reached its peak in 1994, with an annual revenue of over 2 billion dollars and a staff of 10,000. However, in the end, Microsoft would succeed, and Novell would collapse. In 1999, Microsoft previewed its Active Directory (AD), which is essentially a database with business logic for service directory requests. This product would support Microsoft's future in the enterprise field and was proven to be a fatal blow to Novell's business.
- By the end of 2001, the Enron scandal broke out, leading to the passage of the Sarbanes-Oxley Act (SOX) in 2002. This new regulation requires enterprises to monitor and audit logins, user activities, and information access permissions. As a result, almost all U.S. publicly listed companies began to purchase Identity and Access Management (IAM) solutions.
- Microsoft's Active Directory is becoming increasingly difficult to use. Nevertheless, it is still hard to摆脱 it and switch to another product. The migration process is lengthy and frustrating, and the directory is so integrated into business processes that dependency management is a headache.
- Todd McKinnon and Frederic Kerrest are senior figures at Salesforce, and they have some very specific insights: (1) Local identity tools are becoming a bottleneck for teams, (2) Cloud applications are hindered by fragile identity systems, and (3) Microsoft will face difficulties in migrating customers to the cloud version of Active Directory. This led to the founding of Okta in 2009.
- As more and more company assets continue to move outside the firewall, policies such as Bring Your Own Device (BYOD) have emerged. The multi-modal security needs across mobile, cloud, and other areas have led to the expansion of the security landscape. This has accelerated the development of new categories such as Mobile Device Management (MDM), Customer Identity and Access Management (CIAM), and Machine and Workload Identity.
- Now, the identity market is in a peculiar situation. There are more suppliers than ever before, each committed to solving an important part of the identity lifecycle, but over 60% of security leaders believe that the field is consolidating as of August 2022.
- Identity has become the new boundary, leading to some catastrophic consequences (according to the 2023 report, three-quarters of breaches are caused by identity issues). To solve this problem, a lot of innovation is needed at both the ultra-large-scale platform level and the individual product launch level.
Cybersecurity Series

In recent years, the cybersecurity ecosystem has become increasingly fragmented. This report is part of the Contrary Research cybersecurity series, aimed at unraveling this complex ecosystem.
In our previous in-depth exploration of this topic, we looked at the broader picture from the perspective of cybersecurity, providing readers with a framework to understand the industry. Our second report covered endpoint security and related industries such as security operations and SIEM platforms. We also covered emerging startups that need to be monitored within the ecosystem. In our third report, we analyzed the world of cloud security, which is relatively new and constantly changing. In the final article of this series, we analyzed the role of identity in the rapidly changing digital competitive environment in detail.
Identity is a complex beast, partly because it involves many different aspects of the organization. Each functional area has its own concept of identity tracking, whether it is sales, human resources, or finance. Most importantly, identity has long been considered primarily an IT issue. However, identity is increasingly becoming the core of the cybersecurity field.
In November 2023, Okta issued an alert to its customers that it had encountered a vulnerability. Although this was a terrifying message for any customer that might be affected, most people just hoped they were not one of the affected customers. Unfortunately, in this case, 100% of customers were affected. A month ago, Okta estimated that only about 1% of its customers would feel the impact. The actual number was far off.
But Okta is not alone. Up to 80% of breaches are caused by identity issues (such as credential leaks). In the second half of 2023 alone, companies like MGM, Caesar's, Atlassian, and New Relic experienced incidents of identity information leaks in conjunction with Okta. The losses caused by these breaches may reach several billion dollars.
The purpose of this in-depth study is to accurately reveal how identity has become such an important threat surface and how it has evolved to counter these threats.
Why identity?
In March 2023, Rak published an article about Palo Alto Networks ($PANW). In it, he observed that the network as a useful enterprise boundary has disappeared:
'When [PANW] [2005] started, the network defined the enterprise boundary. Therefore, protecting network security was the most valuable place. In the following decades, network boundaries disappeared with remote work and cloud-distributed applications. Palo Alto's firewall products used to account for over 90% of revenue, now accounting for 60% of the business. We expect that as companies expand their Prisma products, provide security through the cloud, and invest in new products, the revenue share will decline.'
Boundary erosion has caused serious trust issues within the security community. If you cannot trust the message you receive, you must trust the person who sends the message. This means you must figure out who this person is, why they are trying to interact with you, and whether you should open the message.
The identity field consists of public companies such as Okta and CyberArk, private companies such as Centrify, ForgeRock, Sailpoint, and Ping Identity, as well as dozens of startups. The development of these startups is partly due to the billions of dollars in venture capital each year. It is obvious to everyone that as a company, you want to control who has access to which files and applications. There is no dispute that employees must verify that they are employees before they can damage your system. It is well known that you have set some strategies to audit who uses what and why, and publish some announcements to your organization every few months ('Guys, stop inviting your friends and family to use our Jira instance') you are safe! Just kidding.
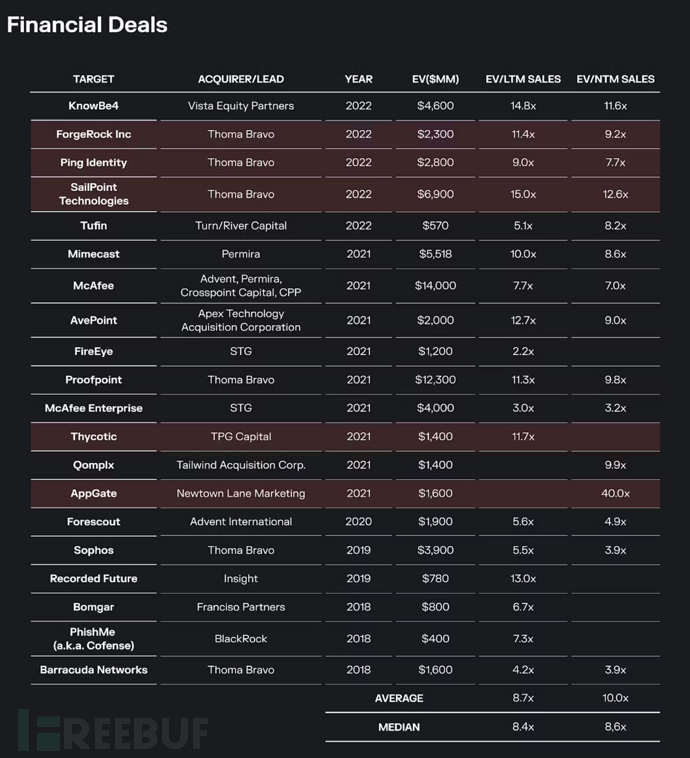
Source: J.P. Morgan, Launch Security Software (January 2023); Contrary Research; famous identity or access-related companies acquired by PE in recent years
As of July 2023, 75% of violations were caused by poor identity, access, or permission management. In 2020, 79% of organizations reported incidents related to identity leaks. Given the leverage that identity security can provide, identity has given rise to many large companies. If identity can really 'solve' things once and for all, then you would not need many other security products! If only trusted workloads, trusted APIs, and trusted users can access the data, who would care if the S3 bucket is misconfigured?
But it is very difficult to get there. Partly because the enterprise footprint is becoming more complex, and partly because the attackers are constantly changing their methods. Companies that solve identity security issues usually have to solve two problems: (1) Authentication (for example, who are you?); (2) Authorization (for example, are you allowed to do what you are doing?). But there are some key areas where this often occurs.
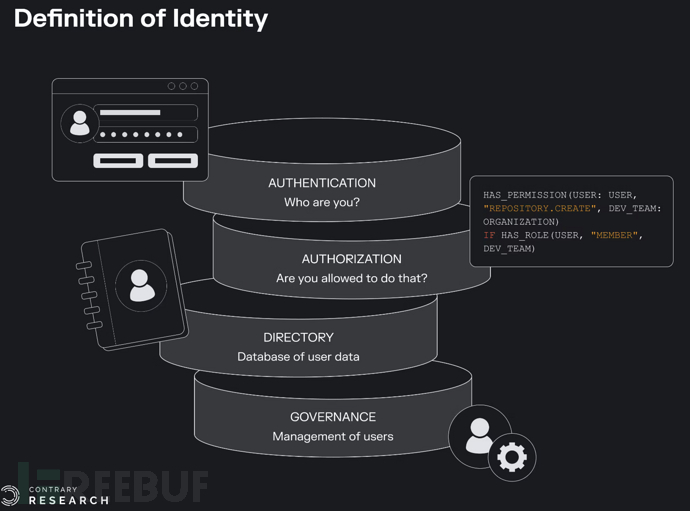
Source: SSL2BUY; Contrary Research
Crisis
After meeting with hundreds of IT and security leaders, identity product owners, and entrepreneurs, we observed three core issues in the identity field:
- Most identity products are managed statically, based on group policies. Whether in physical locations or positions within the organization, users are constantly moving. Therefore, the software or functions they need to use change daily, and they should be allowed to perform operations in the software as time goes by. Policies specify who can do what in what circumstances, but formulating policies is boring, and updating policies to adapt to the ever-changing environment is almost impossible.
- Infrastructure behaves like users. From a security perspective, there is little difference between user operations on applications, third-party API tokens, temporary functions in Lambda environments, and LLM agents. However, there is no functional abstraction layer to control the behavior of these infrastructure participants without impeding the agility of developers.
- The IT department (the most empowered department to own identity) is not the decision-maker. This motivates product teams engaged in management to reach parity with competitive products, and then it ends. In other words, if no one chooses your product because you built a better SSO, then you might as well deliver it and move on to more interesting things. SaaS founders know this; when we ask them how they plan to monetize existing products, many shrug and say 'Maybe single sign-on'.
The existing identity recognition companies today are not established to address reality; administrators, Chief Information Security Officers, and founders, among other users, have to face an increasing number of problems.
Identity suppliers are aging
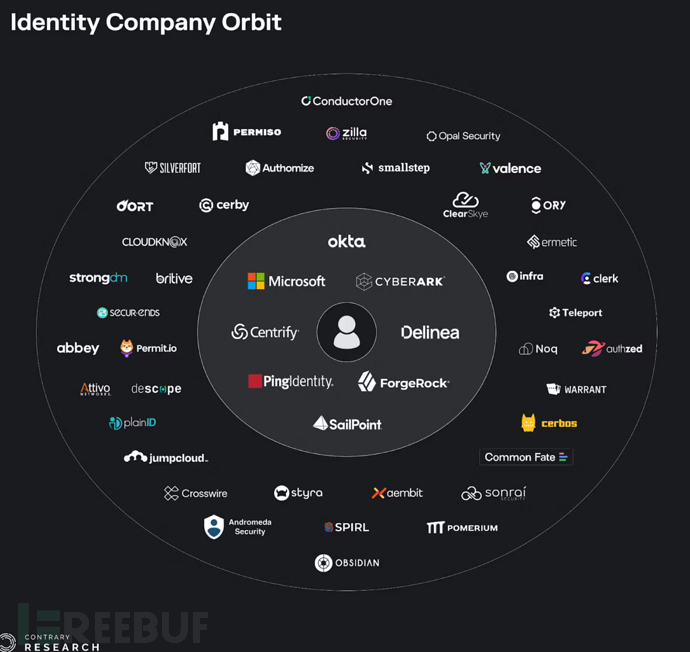
Currently, some of the most valuable independent identity companies include Okta (founded in 2009), CyberArk (founded in 1999), Delinea under the TPG umbrella (Thycotic founded in 1996 + Centrify founded in 2004), Ping Identity under the Thoma Bravo umbrella (founded in 1996), and ForgeRock (2010). Among all these companies, only Okta was born in the cloud and has made progress in transforming the world into a cloud directory, but has not expanded it meaningfully.
Almost half of organizations use more than 25 systems to manage identity and access permissions. As companies grow, acquire, or are acquired, and with middle management personnel experiencing changes in identity and permissions over a short period of time, and with the adoption of centralized procurement from the bottom up continually weakening, the complexity of identity will only worsen. When complexity exists, bad actors have the opportunity to exploit the system. The more people using the software, the wider the attack surface for credential stuffing and password spraying attacks. In August 2022, a Slack account of an employee at Rockstar Games was compromised in this way.
The rise of remote work means there is no comprehensive IP address protection, making it unsafe for suppliers to try to work anywhere, anytime. The more infrastructure providers a company uses, the more likely it is to face cross-platform risks, such as session hijacking, which is exactly what happened to Office 365 users in July 2022. Not to mention the emergence of new threats, such as the foundational models for large-scale social engineering attacks that mimic voices perfectly, increasingly complex phishing emails, and so on.
So let's go back to the beginning. How did the identity space come to be today?
Chapter 1: Novell (1980s)
The Rise of Novell
In 1979, two senior figures in the mini-computer industry, George Canova and Jack Davis, founded Novell Data Systems in the snow-covered city of Provo, Utah, with seed funding of 2 million US dollars. The company initially engaged in designing and selling mini-computers and printers, but progress was not smooth. The capital-intensive nature of the business was incredible, while sales were negligible. The company had to quickly find different, more profitable businesses. A group of Brigham Young University students calling themselves SuperSet were hired as consultants to implement a system that could connect these printers and mini-computers to exchange files. Ten years later, their system would support LANs and lead to the widespread adoption of directories, user authentication, and transmission encryption.
Unfortunately, the effect was minimal at the time. When Ray Noorda, a senior executive at General Electric, stumbled upon the company (then known as Novell Data Systems) at a trade show in 1982, the company was on the brink of bankruptcy. He joined the struggling company as CEO and shortened the company name to Novell. The file-sharing product was the center of the company's new strategy. Today, it's like Satya Nadella encountering a seed-stage startup with a product that fits the market pre-launch at KubeCon and saying, 'Yes, I'll come help you solve this problem.'
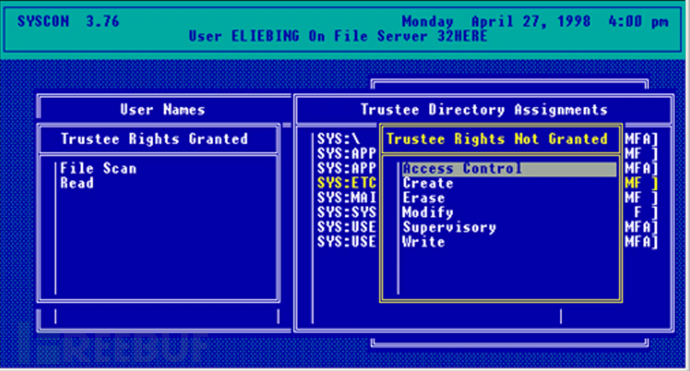
Success. By 1994, when it reached its peak, Novell's annual revenue had exceeded 2 billion US dollars, with 10,000 employees. NetWare 4.0 (a file-sharing system developed for Novell before SuperSet) allowed administrators and users to control access at the file level rather than at the entire disk volume level. This meaningfully changed the industry's view of access control.
Around the same time, companies like Apple, IBM, DEC, and others were competing to commercialize personal computers, which created a huge potential demand for Novell NetWare. The company wisely positioned the product as an agnostic advocate for secure collaboration between various printers, computers, and other networked machines within the company. NetWare was one of the earliest companies to support access control based on users and groups, which was very attractive to administrators because as PCs eroded the multiplexed central computers, administrators were increasingly faced with a decentralized computing infrastructure.
Forty years later, two dynamics in the identity recognition industry still persist:
- Core applications and governance systems tend to have more granular permissions to provide administrators with more control. Each generation of access governance is descending in the stack, from disk volumes to files to applications, to permissions within applications, and then to the microservices below.
- Identity tools won because they could work well with each application, service, container, and other entities in the known enterprise domain. Noorda called this 'cooperative competition' in the 1980s.
Competition likes to be complacent
Netware 4.0 was launched in 1993, including Novell Directory Service (NDS), which is a distributed replicated database that stores directories at the network level. Users could log into the network and view the files they have access to without having to try to access specific resources at specific locations. At this time, authentication and access were still mainly centered on resources rather than participants.
That same year, Tim Howes, Gordon Good, and Mark Smith of the University of Michigan released the first LDAP (Lightweight Directory Access Protocol) specification, which was groundbreaking for its openness, vendor neutrality, performance, and reliability. The core of this protocol was to create a standardized method for directory servers to locate, retrieve, and provide the appropriate resources or information requested by users. This work was mainly academic until 1996, when the three were hired by Netscape, sparking a LDAP arms race.
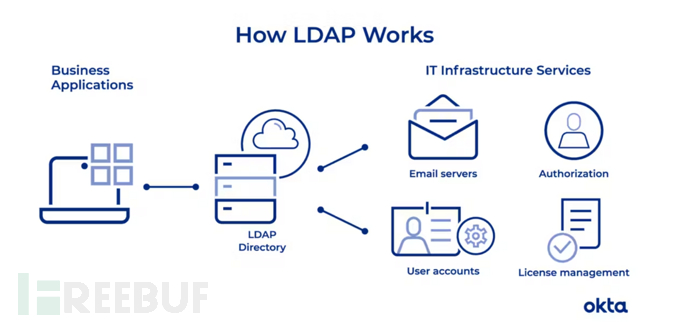
In January 1998, Netscape released the first commercial implementation of LDAPv3, including SASL (Simple Authentication and Security Layer), which would become the foundation for MFA and other challenge-response authentication examples. Just six months later, Sun Microsystems launched a similar directory server. With each product launch, Novell's position in the directory service market seemed to be weakening, but it turned out that no product was as disruptive as Microsoft's new product Active Directory.
Chapter 2: Microsoft (1990s)
Some assembly required
Around 1995, Novell’s previously unassailable position began to become more fragile, when the agile Bill Gates realized that if everyone had a personal computer, identity did not need to exist outside of core business applications (such as in NetWare). In the 1980s, Microsoft had tried twice to challenge Novell in the network field through MS-NET and LAN Manager, but both attempts failed. At the time, networking was one of the fastest-growing markets in technology, giving rise to companies like Cisco and Juniper Networks. Gates did not try to fight for the network, but decided to let Novell fight for the administrators.
During this period, Novell’s CEO was Eric Schmidt, who served from 1997 to 2001. He resigned from his position as Chief Technology Officer of Sun Microsystems to join this struggling internet giant and faced the daunting task of turning the company around. Microsoft provided TCP/IP stack free of charge as part of the operating system, thus eroding Novell’s profits. Nevertheless, Novell remained steadfast in the early years of Schmidt’s tenure. He refocused Novell on directory service products and abandoned all other products. Their idea was that it was not the time for diversification, but to double down on effective business. Schmidt said at the time:
‘You must stop the bleeding and stabilize the patient’s condition. We reduced the seven-level management to four levels. We initiated an active public relations campaign, releasing new products or product upgrades every month. We refocused on our core strengths. The biggest challenge is to retain our key talent - the 'smart people' - and keep them motivated. A company can survive even if it loses many people, but if it loses the smart ones, it is doomed.’
At the same time, in 1999, Microsoft previewed Active Directory, a product that would support Microsoft's future in the enterprise field and toll the bell for Novell. Active Directory (AD) is essentially a database with business logic for service directory requests. The AD structure can be objects (printers, servers, etc.), subjects (users, accounts, groups), or various arrangements of objects and subjects. Administrators can edit the schema, but each change is propagated throughout the system, and improper operation can lead to large-scale disruptions and changes.
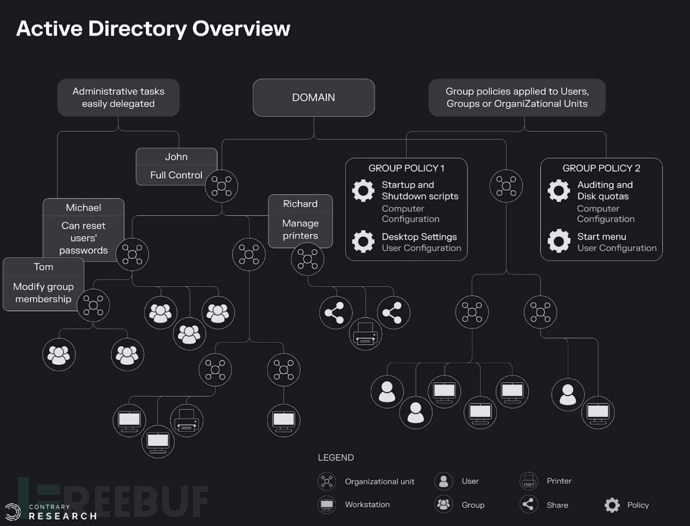
The Distribution King
Microsoft AD was bundled with Windows Server 2000 in the way Microsoft does. As the server operating system began to run dominantly, Microsoft AD quickly became the standard way for enterprises to verify and store information about users and assets. As our friends on Slack are well aware, Novell's early product leadership was replaced by Microsoft's powerful distribution advantage, starting an irreversible downturn until 2014 when Novell was finally acquired by MicroFocus. Eric Schmidt performed better, leaving Novell in 2001 to join Google after its Series A financing.
The IT department was initially excited about the arrival of Active Directory; they could finally implement password reset and length requirements for all users in a centralized and easy manner, even as the types of devices and applications used became increasingly complex. As the ecosystem developed, frustration began to spread: integration was fragile, managing AD became a full-time job for the IT management team, and it was difficult to incorporate non-Microsoft applications and devices, and interacting with objects outside the firewall was a challenging situation outside the network. It took days or even weeks to allow new users to access applications, and business users began to resent the IT department for hindering their work efficiency.
However, Microsoft still became the undisputed leader in the field of enterprise management. When you are the only game in town, even your mistakes become features! Microsoft launched a certification
2.3 Security vulnerabilities similar to cross-site scripting
Analysis and defense of XSS cross-site scripting attacks
Retail cyber threats- Increased shopping drives increased risk
Burpy + frida to implement automatic encryption and decryption on Burp
1. Use BurpCrypto for爆破 with parameters of prefix + AES encryption
评论已关闭