Overview
Anubis (Anubis) is a mainly active Android banking Trojan in Europe, America, and other places. Its attack method mainly involves infiltrating mainstream APPs and APPs with a large number of users, such as financial applications, chat applications, mobile games, shopping applications, software updates, email applications, browser applications, etc., by disguising as some mainstream APPs and APPs with a large number of users. Since its outbreak, Anubis has swept across more than 100 countries around the world, causing considerable trouble to more than 300 financial institutions.
Recently, the Qianxin Virus Response Center has captured a malicious software that counterfeits the international version of Douyin 'TikTok'. After analysis, it was found that this malicious software is a variant of the Anubis Trojan. Douyin has a large number of users in China, even can be said to be extremely popular, for domestic users is not unfamiliar, just the Douyin download volume on the AppGallery platform has reached 550 million times, Douyin international version 'TikTok' is also very popular abroad, and also has a large number of users in the international market.

Douyin download volume from AppGallery:
Google Play Douyin related software and download status:


This Anubis spreads through the counterfeit international version of Douyin 'TikTok', which is due to the large number of users of 'TikTok'. Although the counterfeited is the international version of Douyin 'TikTok', because of various reasons, this application will still be tried to install and use by domestic users. The Qianxin Virus Response Center's mobile security team has indeed found that some domestic users were infected with Anubis malware through this channel based on data analysis.
Sample analysis
Although the Anubis banking Trojan has a variety of counterfeits, its core code structure has not changed significantly. The core of the Anubis code is remote control, with phishing, ransomware, and other functions as auxiliary, with the purpose of obtaining users' key information and stealing users' property.
This Anubis Trojan that counterfeits 'TikTok' has made some changes in terms of functionality and added and optimized some functions according to actual needs.
Counterfeit 'TikTok' running interface:

Distribute remote control commands by concatenating URLs:

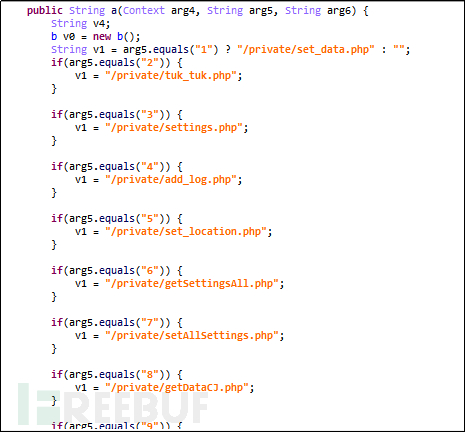
Remote control command fragment:
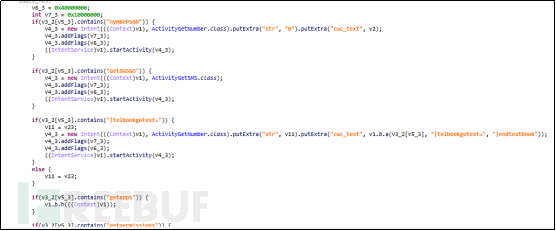
Main remote control command and corresponding function:
| Main remote control command | Command corresponds to the function | |
|---|---|---|
| state1letsgotxt | Settings | |
| ALLSETTINGSGO | Configure relevant information | |
| Send_GO_SMS | Send text messages | |
| nymBePsG0 | Get phone contact list | |
| GetSWSGO | Get phone text messages | |
| |telbookgotext= | Get phone contact list | |
| getapps | Get installed apps | |
| getpermissions | Get the corresponding permissions | |
| startaccessibility | Apply for accessibility | |
| startpermission | Start permissions | |
| =ALERT| | Set alarm | |
| =PUSH| | Open the fishing page | |
| startAutoPush | Pop up different phishing information based on different countries | |
| RequestPermissionInj | Request injection permission | |
| RequestPermissionGPS | Get location | |
| |ussd= | Call a specified number | |
| |sockshost= | Connect to server | |
| stopsocks5 | Stop socks | |
| |recordsound= | Record | |
| |replaceurl= | Replace URL | |
| |startapplication= | Start application | |
| killBot | Kill process | |
| getkeylogger | Obtain keyboard recording | |
| |startrat= | Obtain new operation instructions | |
| opendir: | List all files | |
| downloadfile: | Download file | |
| deletefilefolder: | Delete file | |
| startscreenVNC | Enable remote control | |
| stopscreenVNC | Close remote control | |
| startsound | Start recording | |
| startforegroundsound | Enable foreground sound | |
| stopsound | Close recording | |
| startforward= | Enable call forwarding | |
| stopforward | Close call forwarding | |
| |openbrowser= | Open browser | |
| |openactivity= | Open URL | |
| |cryptokey= | Encrypt file | |
| |decryptokey= | Decrypt file | |
| getIP | Obtain user IP address |
Impact analysis
The domain for sending commands and transmitting data from the trojan: tratata.space, registered on June 26, 2019. Based on the data from the Qianxin Threat Intelligence Center, it was found that most of the victims are from Russia, and there are also some domestic users who have been affected.
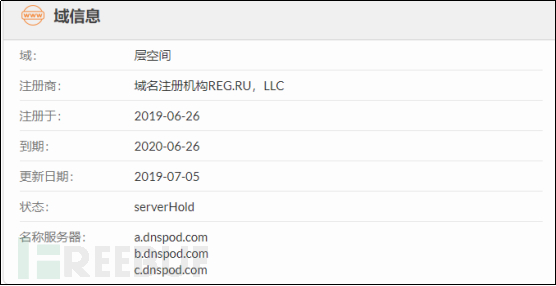
Same-origin analysis
Since the outbreak of Anubis, we have been monitoring it. We have found that the main code structure of Anubis has not undergone major changes in recent years, but each new variant will have corresponding changes in functionality, adding or optimizing some features. Its delivery methods and types of imitation have always been prioritized for Google Play, imitating popular applications and financial applications.
Evolution of Anubis code structure:
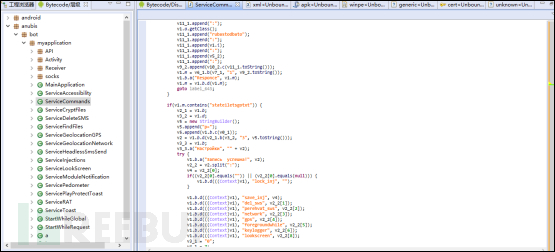
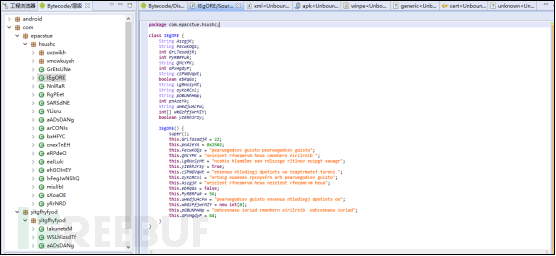
The code structure after reinforcement treatment:
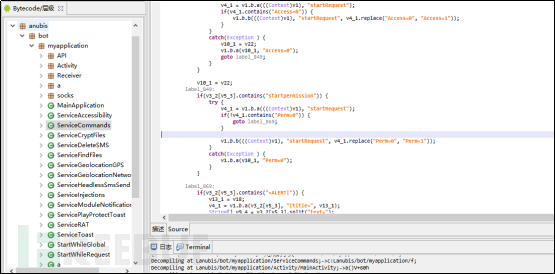
The imitation code structure of TikTok this time:
The following imitation main icons were found in the Janus mobile security threat information platform of the PanGu team:

Summary
The Anubis banking malware was originally mainly distributed outside of China, but with domestic netizens becoming more familiar with internet technology and attempting to install some applications from foreign sources, this time the imitation of the international version of TikTok led to some domestic users being affected.
Here we remind all users to download mobile applications from official platforms to minimize risks, thereby preventing the risk of personal information and property theft. The Qianxin Virus Response Center's Mobile Security Team will continue to track the latest variants of Anubis, and PC and mobile terminal security products will support timely detection and elimination of such threats.
IOC
940F562DED0DD9**8235FB9EA738F405
http://tratata.space/private/checkPanel.php
http://tratata.space/private/settings.php
http://tratata.space/private/add_log.php
http://tratata.space/private/set_location.php
http://tratata.space/private/getSettingsAll.php
http://tratata.space/private/setAllSettings.php
http://tratata.space/private/getDataCJ.php
http://tratata.space/private/setDataCJ.php
http://tratata.space/private/add_inj.php
http://tratata.space/private/locker.php
http://tratata.space/private/datakeylogger.php
http://tratata.space/private/sound.php
Reference
*Author of this article:Qianxin Threat Intelligence Center, please indicate the source as FreeBuf.COM when转载
How to use TikTok Scraper to quickly collect user-posted video data
Analysis of Cleanfad mining malware's attack activities on cloud hosts
In the new year, spy wars are resuming: several mobile malware targeted at India.
It turns out that the online banking experience machine can still measure like this.
Dubbo Architecture Design and Source Code Analysis (Part Three) Chain of Responsibility Pattern
How to use SystemInformer to monitor system resources, debug software, and detect malware
4 Combining Strategy Design Pattern and Chain of Responsibility Design Pattern
评论已关闭