*The relevant vulnerabilities mentioned in this article have been reported to the manufacturer and have been repaired. This article is only for technical research and discussion, and is strictly prohibited from being used for illegal purposes. Otherwise, all consequences shall be borne by the user.
At the end of the last century, in the market competition among European car manufacturers, Volvo (Volvo) was regarded as a relatively safe car brand due to its invention of seat belts and thicker car body steel plates, which was favored by older consumers.

BMW (BMW) focuses on the strong maneuverability and emphasizes 'driving pleasure' for young people, but gradually, people pay more attention to the safety performance of cars, prioritizing their safety when purchasing a car.

At this moment, BMW (BMW) proposes an innovative concept in the market called 'Active Safety', which particularly emphasizes the maneuverability and acceleration of its vehicles, enabling them to quickly remove the car and people from dangerous situations, thus reducing the likelihood of traffic accidents. It can be concluded that safety protection should be placed above all other functions.
Recently, the 'Three Email Infiltration Methods Most Used by Hackers' released by Softnext Security. In fact, if you look closely, these vulnerabilities and methods are not particularly novel. Many companies' information network systems are invaded because of their own unhealthy network security environment.
If one's own network is not healthy and is exploited by people with malicious intent, problems will naturally arise, just like people with sub-health are more prone to illness. Regular network checks, education, and exercises are effective for safety prevention, and one can be prepared without fear. People with sub-health also need regular physical examinations at hospitals to detect health problems early.
How to create a safe and healthy network environment?
First, patch vulnerabilities and develop the good habit of regular updates.
In previous articles, we mentioned that hackers like to exploit Microsoft Office's OLE vulnerability or Equation vulnerability. In addition to Microsoft, other commonly used software can also have vulnerabilities, such as the 0-day zero-day vulnerability (CVE-2018-4878) in Adobe Flash Player widely used by hackers in 2018.

This vulnerability exists in versions of Adobe Flash Player prior to 28.0.0.161, allowing attackers to spread malicious Flash content through network or email in Office documents, gain system control, and execute arbitrary code.
In terms of operating systems, all versions except Windows 7 are affected.
According to the disclosure of the South Korean Computer Emergency Response Team, this vulnerability has been discovered since the middle of November 2017, and South Koreans have already used this vulnerability to launch attacks, mainly targeting research departments in South Korea and North Korea.
Although Microsoft and Adobe released a new patch numbered KB4074595 immediately, specifically designed to fix the latest 0-day zero-day vulnerability in Adobe Flash Player, many users have not updated due to reasons such as not having developed the habit of regular updates, or being unable to update due to the use of pirated software, or worrying that some functions may not work after the update, etc., thus giving hackers an opportunity to take advantage.
Second, carry out social engineering exercises.
In addition to using technical means to infiltrate users' computers, the most formidable hackers are adept at exploiting the weaknesses of human nature, using methods such as诱导 and intimidation to achieve their goal of infiltration.
An article titled 'Account was hacked! Have you received a threatening letter?' published by Softnext Security and ASRC Research Center on November 5, 2018, discusses how the ASRC Research Center has detected many 'threatening' emails in succession. The subject of these emails directly mentions that the recipient's account has been hacked, and the sender's email address is forged to be that of the recipient. This method, in addition to breaking through improperly set personal email whitelist settings (such as adding one's own email address to the whitelist), also has the effect of making the recipient believe that this letter was sent through their own email account, forcing the recipient to believe that their email account has indeed been hacked!
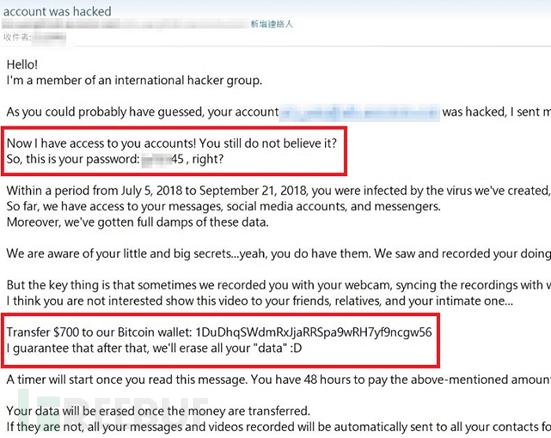
Threatening emails use the recipient's fear to carry out fraud.
Then, the attacker demands that the recipient pay Bitcoin within a certain period of time, and these emails themselves do not contain any malicious attachments or attack codes. They are purely through psychological intimidation, forcing the victims who receive such emails to comply with the instructions out of fear.
Therefore, enterprises should strengthen the security awareness training of employees and establish a social defense strategy system to effectively prevent social engineering attacks. Although many enterprises have realized the importance of social engineering exercises, they do not know how to proceed. Here are some methods for reference:
1. Collect, develop, and maintain various social engineering attack cases, listing a variety of possible outcomes, including correct response measures.
2. Use concise plain language to educate employees on how to prevent social engineering attacks, such as reminding employees to think about 'whether they have the right to provide information? Does the other party have limited access to information?'.
3. Establish a social engineering attack response and experience sharing system. This is a very innovative and easy-to-implement strategic measure. A simple way is to establish an email list and encourage employees to write down suspicious experiences or personal encounters with social engineering attacks and send them to a specific email address, such as security@company.com. Through this email list, other employees can prepare for responses before they are attacked by the same social engineering attack method.
4. Implementing irregular simulation social engineering attack tests. In fact, most current hacker attacks combine technology with social engineering. Therefore, when conducting technical vulnerability scanning and penetration testing on internal information systems, it is also necessary to strengthen social engineering penetration attack testing on the personnel level. The test is also a simulated exercise, which does not cause actual losses and obtains valuable practical experience. More importantly, it improves the ability to respond to social engineering attacks during the educational process.
With the above health awareness, the immune system of enterprise employees is strengthened, reducing the likelihood of security incidents.
Similarly, when enterprises discuss network security, they also need to have a new thinking of proactive security and ensure the health of the enterprise internally first. In case of a real network attack or fraud, appropriate measures can be taken in time to minimize losses.
In 2018, some friends were exhausted both physically and mentally because their companies were attacked by ransomware phishing emails. Some were busy for several days without going home due to email operation issues. The work pressure for all IT personnel engaged in information security is quite heavy. In the new year, we hope everyone will pay more attention to their own health, become healthy first, reduce the likelihood of illness and increase their ability to withstand stress, so that they can cope with the sudden and overwhelming pressure caused by information security incidents. Companies should conduct more information security health checks to enhance their immunity, and it will be easier to implement and comply with regulations during the execution of the security protection requirements.
*Author: softnext internal security, please indicate the source from FreeBuf.COM when转载
Five ways to safeguard your brand after your organisation gets hacked
Indirect attack methods in LLM attacks and defense methods against LLM attacks
A new vulnerability in Apple Safari browser rings the alarm bell for cross-site user tracking.
Anubis banking malware imitates TikTok international version in attack activity
评论已关闭