Gartner's new research on mobile target defense (dynamic defense, MTD) finds that MTD is an important part of a cybersecurity strategy that prioritizes prevention. Similarly, their predictions also indicate that MTD will be rapidly adopted by suppliers and security teams in the near future. Most importantly, Gartner's findings on MTD validate Morphisec's mission: to use the power of mobile target defense to defeat modern cyber attacks, especially those that have never been seen before, thus bringing peace of mind to IT and security experts.
How does GARTNER define mobile target defense (dynamic target defense, MTD)?
“Mobile target defense (dynamic defense, MTD) is a technology trend that shifts the attacker's attack techniques through dynamic or static arrangement, transformation, or obfuscation.”
This definition is the content of Morphisec's work. Morphisec's vulnerability prevention solution utilizes the power of its patented mobile target defense technology to block advanced attacks within the boundary through zero-trust methods - mobile target defense technology (MTD), by hiding the attack surface to transfer attacks on application runtime. Morphisec's MTD also provides credential protection on the terminal by adjusting the credential structure in parallel. Applying complementary MTD technology on application resources to minimize the attack surface on user account management.
Why is mobile target defense (dynamic target defense, MTD) effective?

“Suppose a master thief can pick any lock. The goal of MTD is not to build a better lock. There is no doubt that this is a commendable and necessary goal to improve the security of the door, but this task is left to other security solutions. Instead, the goal of the MTD security strategy is to make the door and its lock difficult or impossible for thieves to find.”
The working principle of mobile target defense is to move assets from where hackers think they will appear to an unknown location. When the attack cannot find what it intends to exploit, it becomes benign. By subverting expectations and hiding sensitive assets, MTD successfully diverts the attack and prevents (not mitigates) damage.
In addition to defensive capabilities, MTD can combat unknown zero-day and fileless malware attacks, memory vulnerabilities, and other threats that even the most advanced terminal detection and prevention tools cannot capture. Since MTD does not rely on attack signatures to identify threats like next-generation antivirus (NGAV) tools, nor does it need to detect malicious intent to eliminate these threats, such as endpoint detection and response (EDR) solutions, it can block both new and old threats with the same proficiency.
Why is mobile target defense (dynamic defense) important?
The exploitation technique of the attacker relies on the predictability of vulnerabilities in software, systems, system services, or applications during execution. For example, the attacker must write exploitation code targeting a specific area of data stored in memory, use known application runtime parameters, or exploit the parsing of network application code to execute exploitation of these elements.
Almost all network attacks have a common point, that is, relying on a precise attack plan. As network risks rise rapidly, causing trouble to these plans is a reasonable and effective defense strategy. With the growth of a company's technical footprint and the worsening of attack situations, companies are more vulnerable than ever. With network intrusion becoming a monthly headline news, there is only one conclusion: it is time to rethink cybersecurity tools and technologies. MTD offers a new perspective on both of these situations.
In fact, in a recent report, Gartner identified the most influential emerging technologies driving security market innovation and pointed out that mobile target defense is a key technology to improve the security of memory, network, applications, and operating systems. (Refer to Figure 1 below)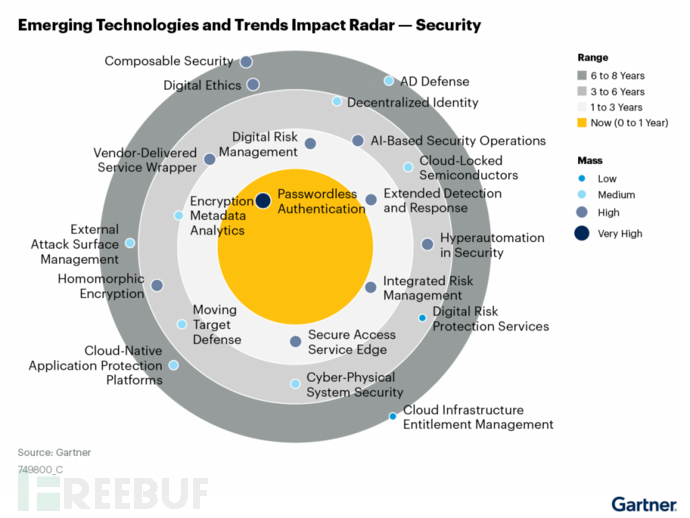
Four, what makes MTD different?
Gartner emphasizes that compared with other vulnerability assessment and management methods, MTD has three obvious advantages:
Accessibility– Implementing MTD requires almost no reconstruction or interruption, especially when applied at the endpoint or application level, 'the use of MTD technology can be implemented immediately.'
Complementarity– MTD tools are not a replacement for existing security solutions, but an additional defense supplement that does not cause redundancy or performance issues.
ScalabilityScalability - since MTD tools can resist attacks, the security team needs to detect and respond to fewer situations, making it easier to expand the system without being overwhelmed by security requirements.
In addition to the technical advantages of MTD, it also represents a new (long overdue) approach to cybersecurity.It is based on the reality that no one can fix every security vulnerability or stop every threat.On the contrary, they must supplement these efforts with what Gartner calls the 'pragmatic nature of attack redirection' to keep up with the level of modern network threats.
Today's security teams cannot expect to see or stop every attack at the defense boundary, so they need to set security layers within this boundary to protect sensitive assets frequently attacked (such as application memory). In this way, even if the attack succeeds in subsequent security layers, it will fail when it reaches the final target due to the evasive techniques applied by mobile target defense.
Five, the future of MTD predicted by Gartner
By 2025, at least 30% of business network, host, and software security solutions will adopt mobile target defense technology, but now it is less than 5%.
Gartner predicts that MTD will spread rapidly for two reasons. First, security vendors may integrate MTD into existing and emerging security platforms, both to upgrade these platforms and to differentiate them from competitors. Second, companies like Morphisec will continue to innovate in this field, making mobile target defense more accessible and powerful. In any case, customers will flock to these solutions in search of advanced defense measures to counter the increasingly complex cyber attacks.
Dynamic CNN model for identifying fake personal profiles in online social networks
Exploration and practice of optimizing the file size of Android dynamic link libraries
GamaCopy mimics the Russian Gamaredon APT and launches attacks against Russian-speaking targets
2. How to define whether the goal of vehicle work is completed? How to choose a research direction?
Android penetration testing 12: IDA dynamic debugging so
Cloud Migration Security (Part 1): Gartner's 5R Security Migration Model
评论已关闭