One, common equipment types - classified by external and internal ROMs
In fact, many CPUs support both internal and external ROMs at the same time, such as the old C51 to the popular STM32 now. Why do we need to divide these two types? Mainly because the external ROM firmware can be extracted by brute force, directly welding the storage chip and using the corresponding reading device to read it.
Programs or systems stored inside the chip generally do not have external storage, for example, as follows:

The ROM outside the chip, such as mobile phones and routers we commonly see, are all external ROMs:
Two, common system classification
NON-OS: This type of embedded system does not contain any operating system and may contain an event scheduler.
RT-OS: This type of embedded system runs a compact but highly real-time RTOS.
Rich-OS: This type of embedded system runs a very complete operating system.
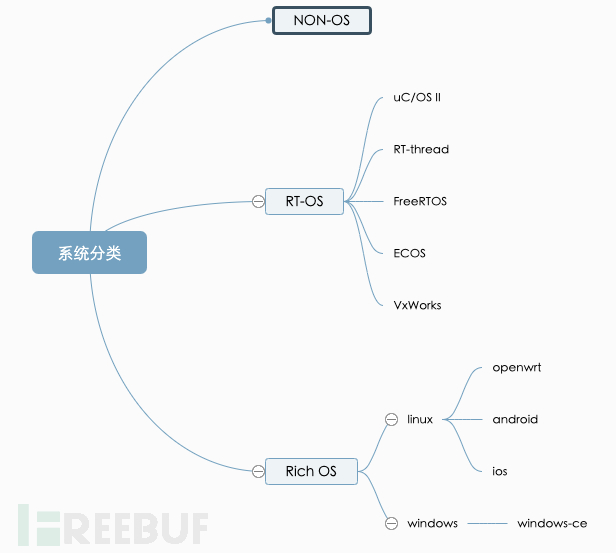
The following figure only lists some common systems:
Three, the method of extracting the ROM program inside the chip:
3.1 Software method
This requires the chip itself to support reading and debugging, for example, if the fuse bit of the avrdude series chip is not locked for ISP, use usbasp to connect to the corresponding interface of the board
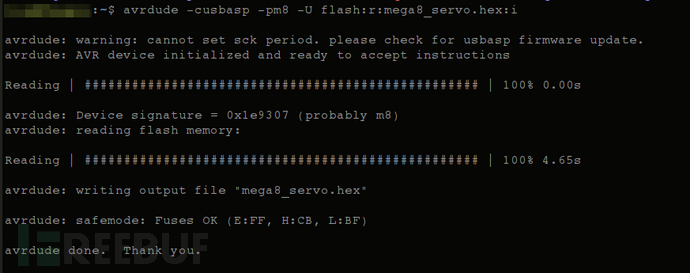
Extract the firmware using avrdude -cusbasp -pm8 -U flash:r:mega8_servo.hex:i
3.2 Physical cracking method
The hardware cracking method is to directly physically damage the chip for cracking, for example, STM32 series chips can be physically cracked. If the AVR series chips have the fuse bit locked for ISP, they can also be cracked by physical means. Here we take STM32 as an example:
Firstly, we need to open the chip.
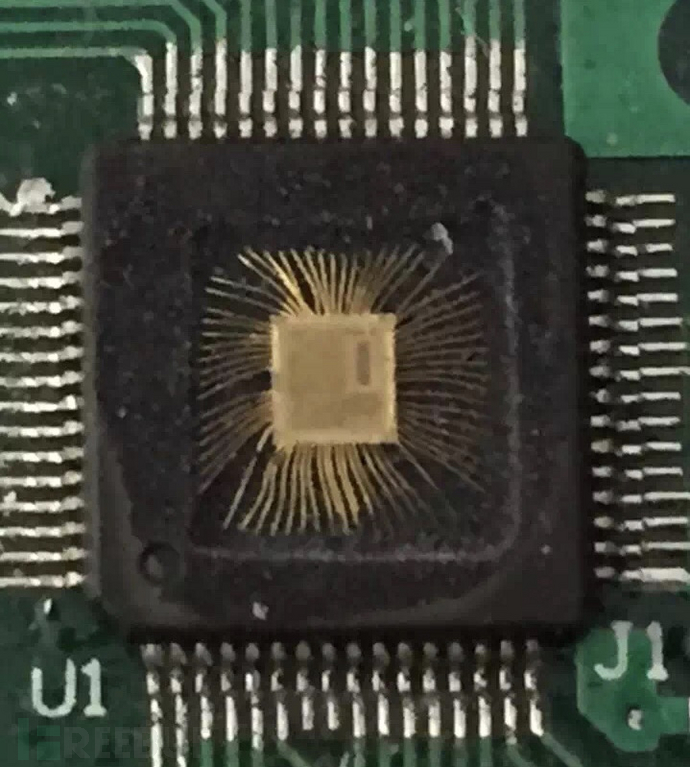
When the chip is exposed, we need to use a high-power microscope and FIB (Focused Ion Beam equipment), using these two devices to find the encrypted location of the chip, change its circuit to make the encrypted chip into an unencrypted state, and then use a programmer to read out the program inside the chip.
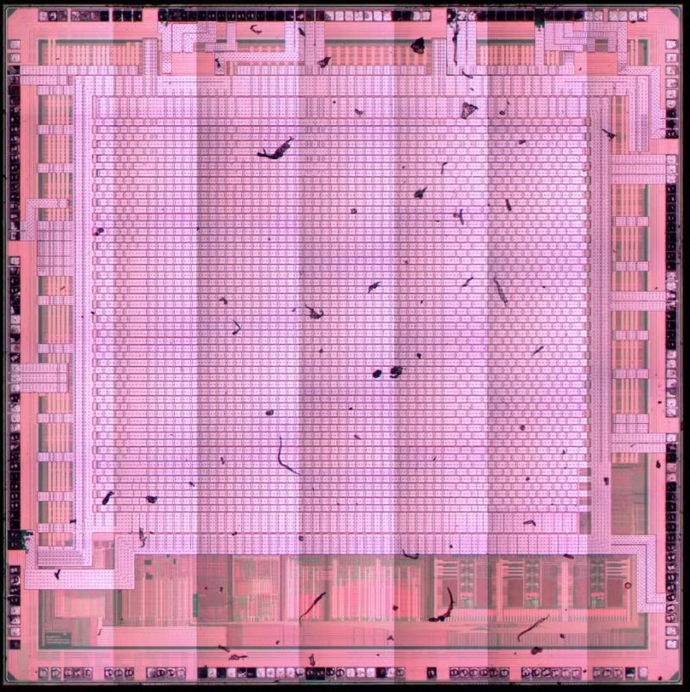
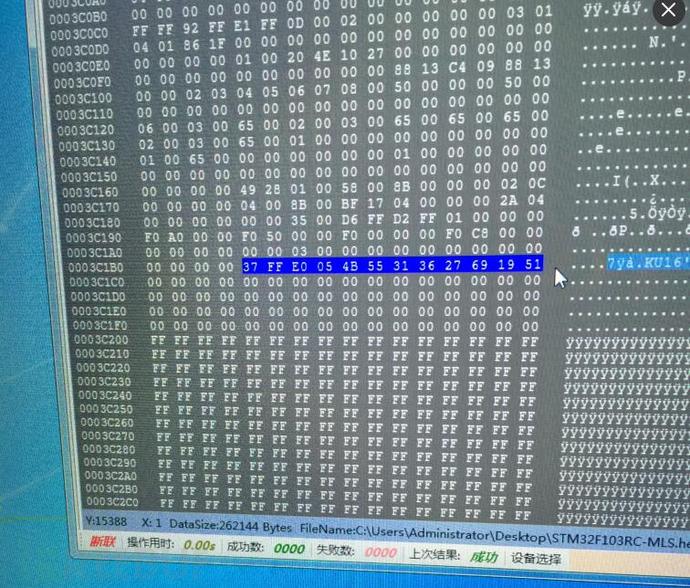
Here, it is important to note that STM32 chips are generally encrypted, and decryption work is also required after reading them out.
Four, the method of extracting the ROM program outside the chip:
The types of external storage are very diverse, common types include:
EEPROM, SPI FLASH, NOR FLASH, SD card, hard drive, etc., here only a simple list is made.
There is also classification through interfaces:
Such as SPI interface, I2C interface, serial port, parallel bus for C51, SD card's sdio, hard drive's sata, and even PCIe in Android phones
Firmware extraction of this type is very convenient, and can be read directly using a programmer or read using a card reader with a universal storage interface on the computer.
4.1 spiflash firmware extraction
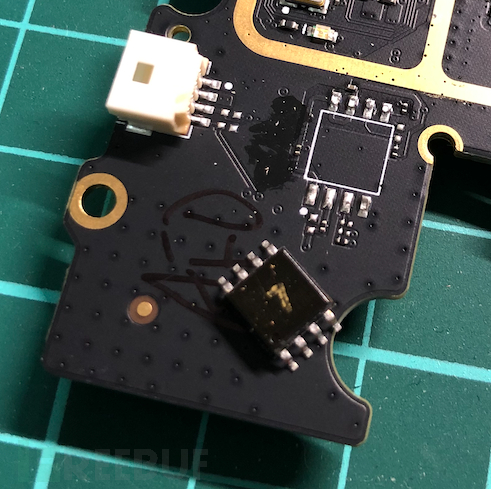
spiflash can be easily extracted, and the chip can be removed and placed in a card reader or directly read using a clip to access the firmware in the flash.
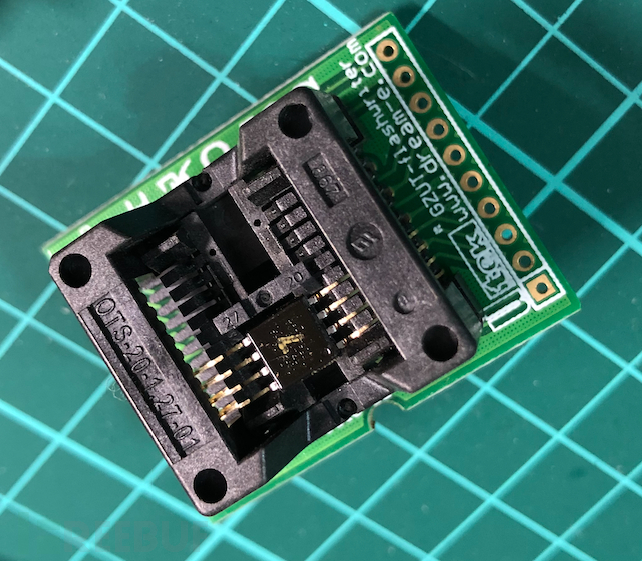
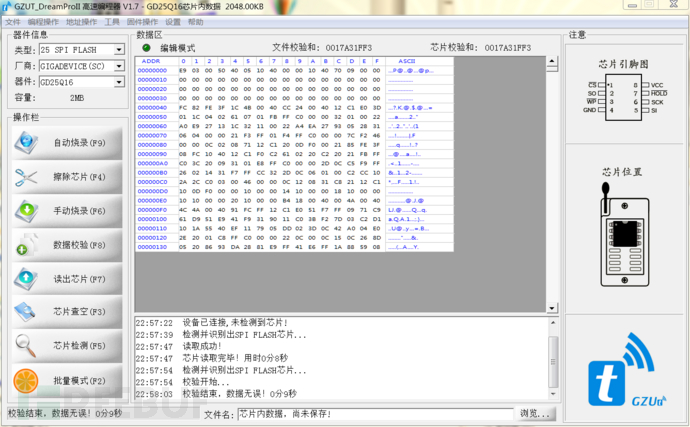
4.2 ROM extraction for Android devices:
Applicable when there is no root permission and Recovery cannot be accessed

4.3 Firmware extraction for x86 devices
x86 devices are generally hard drives, whether mechanical hard drives or SSDs, they are all standard PC interfaces, and these are generally found on firewalls and audit devices.

5. Contact physical devices but have permission to extract firmware:
5.1 For those that can be accessed through network links and have the corresponding permissions:
With a complete set of busybox commands, operations are very convenient. You can use the dd command directly or back up to a file using mtd and then transfer it out using scp
I have encountered a relatively streamlined system, where commands like dd are streamlined, which is very common in embedded devices, as flash sometimes has 1m, 2m, and other situations.
In many cases, the firmware can be directly transmitted using tftp
tftp -p -r /dev/mtdblock1 192.168.200.28
5.2 Download the upgrade package through the manufacturer's website:
There are many situations here, many manufacturers provide firmware download directly. Now that the safety awareness has been improved, many of the downloaded firmware are encrypted, and decryption is required after download. Some firmware no longer provide downloads, and firmware updates need to be performed through the device management interface by connecting to the network. This can be analyzed to determine the firmware address through packet capture, and the firmware can also be extracted.
6. Summary:
These are the devices encountered in daily work, and the explanation is relatively simple. I will have the opportunity to explain the simulation and disassembly operations after firmware extraction. Please like more. The writing is not good enough, and the explanation is not comprehensive enough, and there are also places that are not explained correctly. Please forgive the greats.
*Author: question, please indicate the source as FreeBuf.COM when reproduced
评论已关闭