Over the years, engineering and technology have rapidly transformed, generating and processing a large amount of data that needs to be protected due to the high risk of cyberattacks and breaches. To protect enterprise data, organizations must adopt proactive data security methods, understand the best practices for protecting data, and use the necessary tools and platforms to achieve data security.

This article will discuss what sensitive data is, guide you through some basic knowledge of data security, discuss the risks and challenges of data breaches, provide some best practices for protecting sensitive data, and explain how to use data security platforms to ensure the protection of sensitive data.
1. Understanding Sensitive Data
Sensitive data refers to any type of information that is processed or stored by individuals or organizations, which must be kept confidential and avoid unauthorized access or disclosure.
If the information contained in the data could lead to serious consequences if inadvertently disclosed to unauthorized parties, such as identity theft, economic loss, legal penalties, etc., then the data is considered sensitive.
Common examples of sensitive data include:
- Personal Identifiable Information (PII):This includes any data explicitly used to identify an individual's identity. They include personal addresses, names, driver's licenses, social security numbers, passport numbers, and other information such as biometric data. They are considered sensitive data because attackers can use them to impersonate someone; therefore, they must be protected.
- Health records:This includes any data related to an individual's mental or physical health, such as medical diagnoses, laboratory tests, and medication histories. They are usually protected by laws and regulations and are handled only by medical professionals subject to medical confidentiality obligations.
- Intellectual property:Intellectual property (IP) refers to the creation of ideas, which can be inventions, artistic works, patents, trade secrets, or literary works. Intellectual property is generally considered sensitive because unauthorized access or disclosure may lead to loss of income, financial loss, and damage to the reputation of individuals and enterprises. For example, if a competitor mistakenly obtains a company's patent, the company may not be able to compete in the market because the competitor can quickly produce the same product or service without incurring the costs associated with research and development.
- Business Information:Certain business information (such as business plans, financial information, investments, trade secrets, customer data, marketing strategies, etc.) is considered sensitive information because it is crucial for the success of the organization. Incorrect access to sensitive information about the business can lead to damage or financial loss. For example, this is why most companies require new employees to sign confidentiality agreements (NDA) to protect business information and ensure the confidentiality of their employees.
- Financial Data:Bank account numbers, bank statements, and credit card numbers, and other information are sensitive data and are often targeted by cybercriminals for fraud and other mischief. Strict measures must be taken to protect financial data to prevent unauthorized access.
- Customer Data:Businesses collect certain sensitive information from customers, including their date of birth, name, address, phone number, and financial information. Although all this information is necessary for providing services and maintaining customer relationships, businesses must protect this information from unauthorized access to ensure customer privacy and security.
To ensure confidentiality, integrity, and availability, individuals and organizations must identify sensitive data and use appropriate measures to classify it. Organizations must implement specific related data classification strategies and processes to determine which data is sensitive and classify it according to different categories to determine the appropriate protection level and ensure its secure storage and transmission.
The discussion of protecting sensitive data has always been a problem between organizations and individuals, especially with the increase in cyber attacks and fraud, impersonation, and other crimes. Protecting sensitive data is crucial for protecting individuals and businesses from these cyber attacks and other crimes that can lead to significant reputational and financial losses. Therefore, individuals and organizations must prioritize data security and ensure the safety and secure transmission of their sensitive data.
In the next section, we will introduce the basics of data security and define different terms.
2. Data Security Basics
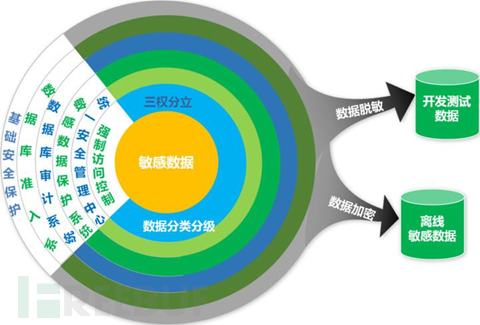
It is necessary to discuss some basic concepts to ensure the security of sensitive data. Some of these are:
1. The CIA (Confidentiality, Integrity, and Availability) Triad
The CIA triad is a widely accepted and used security model designed to guide organizations in their efforts to ensure data security and forms the foundation for developing secure systems.
- C represents confidentiality, which refers to maintaining the privacy of sensitive data and ensuring that only authorized individuals can access it.
- I represents integrity, ensuring that information is accurate and not altered or tampered with.
- A for availability ensures that authorized users can access the data when needed. It includes providing information in a timely manner and ensuring that systems and devices start and run with minimal or no interruption.
2. Data Encryption
Encrypted data is one of the most important steps in data security. It involves using algorithms to convert plain data into encoded or unreadable formats to obfuscate it, so that it can only be deciphered with the key and password. The most common types of encryption include hashing, symmetric, and asymmetric encryption.
Use strong encryption algorithms to encrypt sensitive data, ensuring that only authorized personnel can decrypt and access the data. This way, even if the data is stolen or leaked, sensitive information cannot be directly obtained.
Data encryption is a process of converting original data into ciphertext through a specific algorithm to ensure the security of data during transmission, storage, or processing.
- Symmetric Encryption:Symmetric encryption uses the same key to encrypt and decrypt data. The sender uses the key to encrypt the original data into ciphertext, and the recipient uses the same key to decrypt the ciphertext to recover the original data. Common symmetric encryption algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
- Asymmetric Encryption:Asymmetric encryption uses a pair of different but related public and private keys to encrypt and decrypt data. The sender uses the recipient's public key to encrypt data, and the recipient uses their own private key to decrypt the ciphertext to recover the original data. Asymmetric encryption is commonly used to protect the transmission of keys and digital signatures, etc. Common asymmetric encryption algorithms include RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography).
- Hash Functions:Hash functions convert data of any length into a unique fixed-length hash value. Hash functions are irreversible, meaning that it is impossible to recover the original data from the hash value. Hash functions are commonly used to verify data integrity and prevent tampering, such as using hash functions to encrypt and verify user passwords in password storage.
- Obfuscation Techniques:Obfuscation techniques rearrange, replace, or transform the structure of data through operations such as reordering, substitution, or structural transformation, forming a chaotic state. Obfuscation techniques can increase the difficulty of attackers' analysis of data and improve data security.
These encryption techniques can be used individually or in combination to provide higher security. For example, symmetric encryption can be combined with asymmetric encryption, first using asymmetric encryption to transmit the symmetric encryption key, and then using symmetric encryption algorithms to encrypt actual data.
3. Access Control Mechanism
Establish a strict access control mechanism to limit access to sensitive data to authorized personnel only, and ensure that each person's access permissions are consistent with their responsibilities.
This security measure limits access to sensitive data by specifying who can view or perform specific operations on the data, thereby maintaining confidentiality. Role-based access control (RBAC) and attribute-based access control (ABAC) are the most popular access control mechanisms.
The RBAC mechanism allocates permissions to users in the organization based on their roles. For example, administrators in the organization will have more permissions than ordinary users to perform certain operations.
Unlike RBAC that uses roles, ABAC uses attributes (also known as tags) to determine which users are granted access to resources. Tags can be based on department, location, time, etc. For example, an organization can set a policy stipulating that only users tagged as 'department=finance' can access financial records.
Other access control mechanisms used in data security include Mandatory Access Control (MAC),Discretionary Access Control (DAC)etc.
4. Authorization and Authentication
Although these two terms can be used interchangeably, there are differences and meanings. Authentication involves verifying the identity of the user before granting them access to a specific entity. It requires users to provide a unique identifier (such as a password) or biometric data (such as a fingerprint). Other forms of authentication includeTwo-Factor Authentication (2FA),Single Sign-On System (SSO) and One-Time Password (OTP). Although authentication verifies the identity of the user, authorization ensures that they can only perform operations and actions on the resources they are allowed to access. These two terms are an important part of data security, providing sufficient protection for sensitive data to prevent unauthorized access and abuse.
Understanding the basics of CIA, encryption, access control mechanisms, authorization, and authentication will ensure that organizations and individuals implement strong data security measures to protect sensitive data.
The following section focuses on the challenges and risks of data breaches.
III. Risks and Challenges of Data Breaches
“Data breach” refers to an event that occurs when sensitive data or protected information is accessed, viewed, or stolen by unauthorized entities. It has become very important in today's digital world and poses significant risks to organizations and individuals. Attackers can use the data leaked in data breaches for fraudulent activities and other malicious purposes.
Cybercriminals use phishing, malware, and social engineering to access sensitive data. They launch attacks on software or hardware systems to steal data. Another reason for data breaches is human error. Employees may mistakenly send sensitive data to the wrong recipient or misconfigure security settings, which may lead to sensitive leaks. Other reasons include weak organizational security measures, internal threats, or physical theft.
Data breaches pose serious consequences for organizations, and both organizations and individuals need to fully understand these risks in order to mitigate them and fully defend against such attacks.
Some consequences include:
- Loss of customer trust:Organizations that leak sensitive customer data may cause customers to lose confidence in their ability to protect their safety and data. This may damage the organization's reputation and lead to business losses.
- Operational disruption:Data breaches may cause interruptions in organizational activities, as it may be necessary to shut down specific systems to investigate the incident. This may result in a loss of productivity and income.
- Loss of sensitive information:Financial records, personal information, and intellectual property data may be lost due to data breaches. The loss of this information may damage the organization's finances and reputation, and reduce its competitiveness.
Other consequences may include fraud, regulatory fines, financial losses, recovery costs for theft, etc.
Organizations and individuals can proactively protect their sensitive data by understanding these consequences.
The significance of protecting sensitive data lies in:
- Protect personal privacy:Personal sensitive data includes identity numbers, bank account information, etc. If not protected, it may lead to exposure of personal privacy, financial losses, or the risk of identity theft.
- Maintain trade secrets:For businesses, protecting trade secrets is crucial. This includes research and development results, market strategies, customer information, etc. Leaking this data can lead to a decline in business competitiveness, which in turn can affect the long-term development of the enterprise.
- Avoid legal liability and fines:According to relevant regulations, organizations must protect users' sensitive data, otherwise they may face legal liability and substantial fines.
The following section discusses various methods and best practices that organizations and individuals can use to ensure adequate data security.
Four, Best Practices for Protecting Sensitive Data
The following are some best practices that organizations and individuals can adopt to protect their data:
- Data Discovery:To clearly understand the data they own and who has access to it, organizations first need to understand their entire data through regular data discovery exercises (such as data analysis, team questioning, data storage scanning, and tracking data flows).Datalocation. Discovering data helps identify sensitive data and apply necessary controls.
- The security of dataStorage: Encryption, access control, and other security measures should be implemented to ensure the secure storage of sensitive data.
- Protecting Data Transmission:Data leakage and breaches can occur during data transmission. Organizations should ensure that sensitive data is transmitted securely over the network to prevent such situations. The network can use Transport Layer Security (TLS) for web traffic or dedicated virtual private networks (VPN) to protect remote access during data transmission.
- Data Monitoring:Organizations should regularly track their data by checking past activities in the system, log files, etc.Data. Modern technology even allows for runtime monitoring of data - from data creation to the applications that process the data, and until storage. Monitoring data helps quickly identify abnormal activities, potential security incidents, and how best to correct data violations.
- Data Classification:can be classified according to the sensitivity of the data and regulatory requirementsData classificationso that it can be properly secured.
Best Practices:
- Implement data privacy controls across all data platforms and consumption methods:Data privacy methods implemented to protect, control, and manage access to sensitive data are strictly regulated. While it is important to ensure that these control measures remain compliant and legal at all times, it is also important to manage them consistently across all consumption methods and platforms. Ultimately, data access should remain consistent regardless of the platform. This is the best way to prevent potential leaks that may occur when users with different permissions access data across different data platforms.
- Strengthening data sharing processes:Although data security issues are increasingly serious, it is clear that data sharing is crucial in today's business environment. With the continuous growth of data volume, organizations are sharing more data internally and externally, and teams are facing the challenge of ensuring that every exchange is secure. This is particularly important if the enterprise strives to comply with specific data usage and licensing agreements to profit from data products. Therefore, organizations should ensure that their data sharing processes are adequately strengthened to avoid any data loss or leakage. The joint model for access control management can help teams share data in a controlled manner. Regulatory compliance rules implemented centrally can be enhanced by business and contract compliance rules defined by data owners.
- Maintaining visibility into sensitive data management to ensure compliance:To meet the mandatory regulations and compliance laws for sensitive data, organizations need to continuously understand the types of data they own, the locations of the data, and the specific rules or requirements applicable. It is particularly useful to have this information as regulations evolve or are created. To best understand the sensitive data management practices of the organization, this requires coordination between the legal team handling data and application strategies, and the business team writing these strategies. This visibility not only helps demonstrate compliance with regulatory requirements but also allows for easier changes to access control when needed.
- Expanding data access control based on organizational needs:With the continuous growth and development of data volume, users, technology, and regulations, it is becoming more complex to control who can access sensitive data, especially when trying to consistently execute policies across platforms and access requests. Not only are the data evolving, but organizations are also evolving. Newcomers will join, employees will be promoted, and others may change teams internally. The human resources department usually has JLM (Joiners, Leavers, Movers) processes, but the data platform should also have such safeguards. Why should users be able to access data once they are approved for manual access requests, regardless of which other team they may join in the future? However, by leveraging attributes, you can automatically grant users the necessary data access permissions as they join and move within the organization.
- Using data security platforms: Flow Security and other data security platforms are used to control all organizational data in all cloud, on-premises, and SaaS environments, including shadow data storage and applications. Such platforms can automatically identify and classify sensitive data (such as PII, PHI, PCI), detect and repair data risks, and effectively respond in real-time to data violations.
Other best practices include:
- Access Control
- Regular Data Backups
- Data Retention and Disposal Policy
- Employee Training and Awareness
5. Exploring Flow Security: Data Security Platform
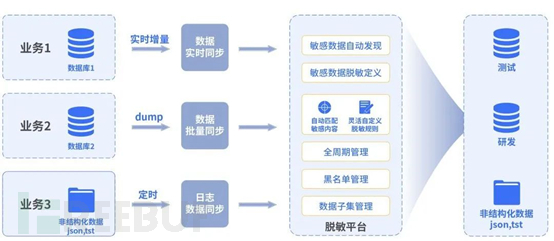
Flow Security is a comprehensive data security platform that provides various solutions to help organizations protect their sensitive data. It can help organizations discover, classify, and protect their data in the cloud, on-premises, and externally shared environments.
Flow Security's solutions include:
- Automation of data discovery and classificationFlow Security can automatically discover and classify data, providing a comprehensive view of all data in the organization. Then, it automatically classifies and builds a catalog of all sensitive data (such as PII, PHI, PCI).
- Automatic mapping of data streams:Flow Security automatically maps data streams within the organization's network, discovers various data, and provides insights into data processing, shadow data storage, and data streams.
- Risk mitigation and data condition managementFlow Security provides a centralized dashboard that allows organizations to manage their security posture and mitigate risks.
- Real-time data detection and response:Flow Security provides real-time detection and response to security events, enabling organizations to respond quickly to threats by providing comprehensive context: who, what, when, where, and why.
Conclusion
In summary, protecting sensitive data is crucial for any organization that wants to protect data from data breaches and cyber attacks. In this article, we discuss what sensitive data is and its common examples, the basics of data security, the risks and challenges of data breaches, and the best practices for protecting sensitive data.
Various technologies (such as encryption and access control mechanisms) can help protect data. However, more is needed to identify and classify sensitive data to understand what control measures to take in the event of a data breach and to respond effectively.
To effectively protect sensitive data, organizations need comprehensive and resolute data security strategies to address security threats in increasingly decentralized cloud data environments such as data lakes and data grids.
Similarly, security must be maintained in all architectures to prevent unauthorized access or violations. Strategies of different enterprises may vary greatly, but the most common are some combination of encryption, data masking, identity access management, authentication, data backup, and elasticity as well as data erasure.
In the end, there is no magic bullet that can guarantee data security and access success. Each organization's approach will be somewhat different and will continue to evolve based on current data and security needs. These basic best practices are a good starting point and are also the key to building strong, flexible, and scalable data security strategies in the years to come.
Reference:https://www.flowsecurity.com/sensitive-data/
Detailed explanation of house of emma exploitation techniques (analysis of 21 Huxiang Cup instances)
Detailed explanation of the exploitation of Windows default shares
Build an information security visualization platform with your own hands
How to deploy and implement (cloud) host EDR + situation awareness platform for large enterprises
Fhex: A powerful all-platform hexadecimal editor
How does Wine implement the cross-platform compatibility layer for Windows?
IOSSecuritySuite: a security anti-tampering protection tool for the iOS platform
评论已关闭