(。・∀・)ノ゙Hi everyone, I am fhoenix
Exploit Pack is a multi-platform vulnerability exploitation framework, containing more than 39,000 vulnerabilities, implants, and proxies that cannot be detected. It can help you plant the next target at any time. Like any such tool, it requires some basic knowledge and professional expertise. Exploit Pack is intended for use by actual security professionals to support their testing process.


Crack tutorial
Declaration:
I was not happy to use your md kali, but there is a problem with this thing in blackarch. Including the trouble of running https in blackarch. I don't know if you will use blackarch
So it's still using kali. This software is cracked by pwn3rzs.
Channel @Pwn3rzs big shot: @PNP6666
But there is a problem with this thing. First, it's a java problem that causes it to fail to start. Second, you need to set up an https exploitpack official website locally... I'll teach you how to do it below
First install kali-linux-everything. Beware of java errors later on!!!!!
Set the /etc/hosts file and add
127.0.0.1 exploitpack.com
127.0.0.1 www.exploitpack.com

Execute the command
mkdir /var/www/html/changelog
touch /var/www/html/changelog/public
echo "17.07" >> /var/www/html/changelog/appversion
cd /var/www/html/
openssl req -new -x509 -noenc -subj "/CN=exploitpack.com/L=San Francisco/ST=California/C=US" -keyout key.pem -out crt.pem -days 365

Next, configure apache2 to prepare for HTTPS
Add the following code at the end of /etc/apache2/apache.conf
<VirtualHost *:443>
ServerName exploitpack.com
DocumentRoot /var/www/html
SSLEngine on
SSLCertificateFile /var/www/html/crt.pem
SSLCertificateKeyFile /var/www/html/key.pem
</VirtualHost>
Then configure /etc/apache2/ports.conf
Listen 80
<IfModule ssl_module>
Listen 443
</IfModule>
<IfModule mod_gnutls.c>
Listen 443
</IfModule>

Execute the command
cd /usr/lib/jvm/java-1.17.0-openjdk-amd64/lib/security
cp cacerts cacerts.bak
keytool -import -alias exploitpack -keystore cacerts -file /var/www/html/crt.pem
Enter library key password: changeit (default password)
Then press Enter after typing Y
Done, now get ready to start!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
source /etc/apache2/envvars to import apache environment variables
###########################################################################
###########################################################################
sudo service apache2 start
sudo java -jar ExploitPack.jar
Features of Exploit Pack
① Developer
The Exploit Pack is designed by a team of experienced software developers and exploit writers to automate processes, so that security professionals can focus on what is truly important.PwnAs if there is no tomorrow.
② Attack detection and vulnerability mitigation:
Use Exploit Pack to make quick responses to offensive and defensive security integration, objectively measure threats, vulnerabilities, impacts, and risks related to specific network security incidents.
③ Easy to use
Exploit Pack uses an easy-to-use advanced software-defined interface, supports quick reconfiguration, so that exploit code, payloads, and utilities can adapt to the evolving threat environment.
④ 0day available
Most importantly, as an advanced package user, once our research team discovers these vulnerabilities and updates, we can access all our zero-day exploits and updates.
⑤ Many exploits
Contains more than 39,000 vulnerabilities, exploits, and proxies
Let me vent my frustration
This is cracked by pwn3 (your awvs, bs, cs are also done by them)
But it didn't work a few days after it was released
I chatted with them in the communication group for a long time, and it took a lot of time to fix it
What problems did I encounter?
At first, it was a java version, I tried various methods, jdk11, 7 could not be opened, always reported an error
Later, I successfully used Kali everything。。。。。。。。。。。。。。。。。。。
Then this software will access its official website every time it starts. What to do? Set up a local copy of its official website. Add to the hosts file
Then I encountered a problem, it is https
I saw the things they posted in the group, using python to set up https, but the problem is that when accessing files, they are not displayed in the browser but directly downloaded。。。。。。。。。。。。。。。。。。
Later, I went to the school library on Wednesday and spent 40 minutes looking for related https materials, but the garbage library had no such materials。。。。
In the end, I still chose apache, but encountered this problem, the conf file was modified and could not be started. I started to find out why it reported an error. Later, I refreshed the variables. Then it still didn't work, so I modified the ports file and changed the port to 80. Later, I was so frustrated that I was in a hurry. Shit.
Finally successful. Of course, during this period, I tried various operating systems and used various py https servers。。。。
Anyway, I折腾 for more than ten days, finally got it done. I decided in advance that if I can fix the exploit pack, I will confess to my junior high school girlfriend as soon as her college entrance examination is over!!!!!!! Everyone wish me good luck!!!!!!!!!
I put the link below, why not use Baidu Netdisk? qtmd, Ali Drive is so fast!
Next, let's see the image!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Image
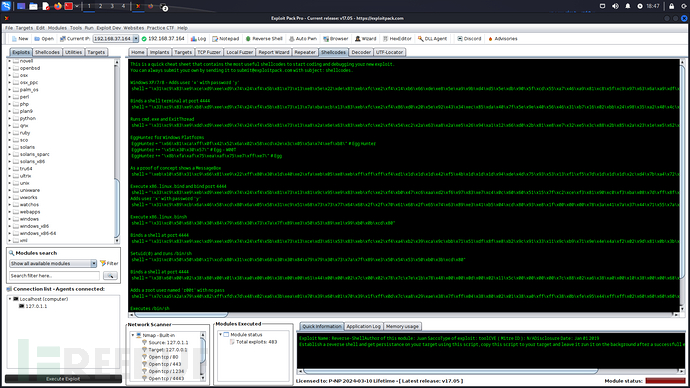

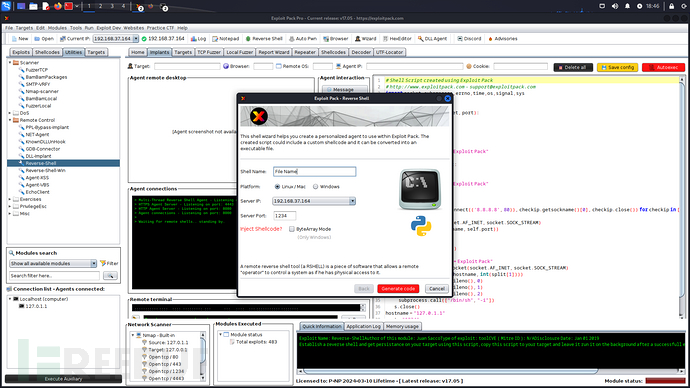
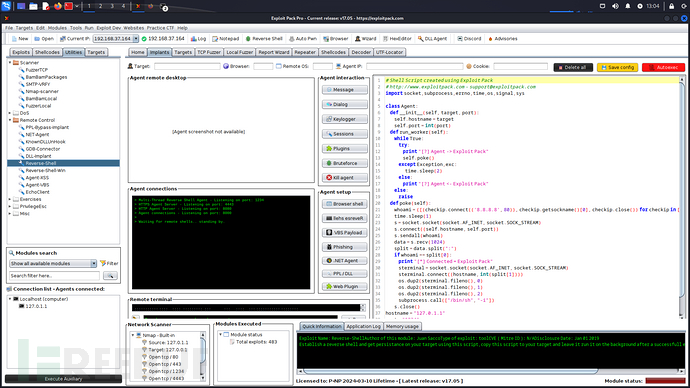
Download link
https://www.aliyundrive.com/s/upK2aDSfLsi by FhoeniX42S~
评论已关闭