Author: Jingdong Logistics, Yin Shijie
Nginx has been widely used in J-one and Jdos environment deployment. This article explains the commonly used configurations and basic functions of Nginx, suitable for beginners learning Nginx.
1 Core Configuration

Find the nginx.conf file under the conf directory in the Nginx installation directory, which provides the basic configuration of Nginx basic functions.
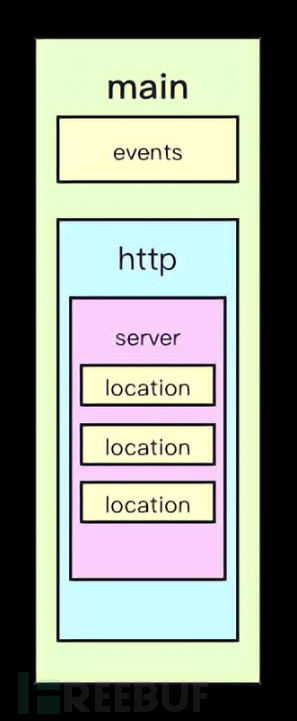
The Nginx configuration file (conf/nginx.conf) is generally divided into the following parts: :
| Area | Responsibility |
|---|---|
| Global block | Configure global configurations related to Nginx operation |
| events block | Configure network link-related configurations |
| http block | Configure proxy, cache, log recording, virtual hosts, and other configurations |
| server block | Configure parameters related to virtual hosts, one http block can have multiple server blocks |
| location block | Configure the routing of requests and the processing of various pages |
The configuration hierarchy diagram is as follows.
1.2 Configuration File Example
The following is an example of a relatively complete configuration file.
# The following is the global section configuration
#user administrator administrators; # Configure the user or group, default is nobody nobody.
#worker_processes 2; # Set the number of processes, default is 1
#pid /nginx/pid/nginx.pid; # Specify the storage address of the Nginx process running file
error_log log/error.log debug; # Set the log path, level: debug|info|notice|warn|error|crit|alert|emerg
# Configuration information of events block
events {
accept_mutex on; #Set network connection serialization to prevent the occurrence of the thundering herd phenomenon, default is on
multi_accept on; #Set whether a process can accept multiple network connections at the same time, default is off
#use epoll; #Event-driven model, select|poll|kqueue|epoll|resig|/dev/poll|eventport
worker_connections 1024; #Maximum number of connections, default is 512
}
# http, configure request information
http {
include mime.types; #File extension to file type mapping table
default_type application/octet-stream; #Default file type, default is text/plain
#access_log off; #Disable service logging
log_format myFormat '$remote_addr–$remote_user [$time_local] $request $status $body_bytes_sent $http_referer $http_user_agent $http_x_forwarded_for'; #Custom format
access_log log/access.log myFormat; #combined is the default log format
sendfile on; #Allow sendfile file transfer, default is off, can be set in http block, server block, location block
sendfile_max_chunk 100k; # Each process cannot call the transmission amount more than the set value, the default is 0, that is, no limit is set
keepalive_timeout 65; #Connection timeout, default is 75s, can be set in http, server, location blocks
upstream mysvr {
server 127.0.0.1:7878;
server 192.168.10.121:3333 backup; #hot backup
}
error_page 404 https://www.baidu.com; #Error page
# The beginning of the first Server block, indicating an independent virtual host site
server {
keepalive_requests 120; #Maximum number of requests per connection
listen 4545; #Listen port
server_name 127.0.0.1; #Listening address
location ~*^.+$ { #Request URL filtering, regular expression matching, ~ is case-sensitive, ~* is case-insensitive.
#root path; #Root directory
#index vv.txt; #Set default page
proxy_pass http://mysvr; #Request redirection to the server list defined by mysvr
deny 127.0.0.1; #Rejected IP
allow 172.18.5.54; #Allowed IP
}
}
}
1.3 Explanation of locat path mapping
1.3.1 Format:
location [ = | ~ | ~* | !~ | !~* | @ ] uri {...}
1.3.2 Explanation:
= means exact matching, if found, stop searching immediately and process this request immediately.
~ means to perform a regular expression match, case-sensitive matching
~* means to perform a regular expression match, case-insensitive matching
!~ distinguishes between uppercase and lowercase for non-matching
!~* does not distinguish between uppercase and lowercase for non-matching
^~ means to match only ordinary characters (spaces). Use prefix matching, ^ means 'not', that is, do not query the regular expression. If the match is successful, no other location will be matched.
@ Specifies a named location, generally used only for internal redirection requests. For example error_page, try_files
uri is the request string to be matched, it can contain regular expressions or not;
1.3.3 Priority and Example:
[No] < [~/~*] < [^~] < [=]
Example as follows:
location = / {
# Exact match of /, no string can be appended after the hostname /
# Only matches http://abc.com
# http://abc.com [Match Success]
# http://abc.com/index [Match Failure]
}
location ^~ /img/ {
# Requests starting with /img/ will match
#http://abc.com/img/a.jpg [Success]
#http://abc.com/img/b.mp4 [Success]
}
location ~* /Example/ {
# It will ignore the case of the uri part
#http://abc.com/test/Example/ [Match Success]
#http://abc.com/example/ [Match Success]
}
location /documents {
# If there is a regular expression that can be matched, it is matched first.
#http://abc.com/documentsabc [Match successful]
}
location / {
#http://abc.com/abc [Match successful]
}
2 Reverse Proxy
2.1 Concept of Reverse Proxy:
Reverse Proxy (Reverse Proxy) refers to accepting connection requests from the internet through a proxy server, then forwarding the requests to the servers inside the internal network, and returning the results obtained from the servers to the clients that request connection from the internet. The real server cannot be accessed directly from the external network, so a proxy server is needed, and the proxy server can be accessed from the external network while being in the same network environment as the real server, of course, it may also be the same server but with different ports.
Reverse proxy is implemented through the proxy_pass directive.
2.2 Reverse Proxy Example:
server {
listen 80;
server_name localhost;
location / {
proxy_pass http://localhost:8081;
proxy_set_header Host $host:$server_port;# Add the Host field to the request header, used to specify the domain/IP address and port number of the request server.
# Set the user's IP address
proxy_set_header X-Forwarded-For $remote_addr;# Add the XFF field to the request header, with the value being the client's IP address.
# When the request server fails, find other servers
proxy_next_upstream error timeout invalid_header http_500 http_502 http_503;
When we access localhost, ngnix will redirect our request to localhost:8081
3 Load Balancing
3.1 Concept of Load Balancing:
When there are 2 or more servers, the proxy server distributes requests to the specified servers for processing according to the rules.
3.2 Load Balancing Strategies and Examples:
Nginx currently supports a variety of load balancing strategies, and here we explain the commonly used 6 types.
3.2.1 RR (round robin: round-robin default):
Each request is allocated to a different backend server in chronological order, which means the first request is allocated to the first server, the second request to the second server, and if there are only two servers, the third request continues to be allocated to the first server, and so on in a circular manner, which is that the ratio of server receiving requests is 1:1. If the backend server goes down, it can be automatically excluded. The round-robin is the default configuration and does not require too much configuration
The same project is started using ports 8081 and 8082 respectively.
upstream web_servers {
server localhost:8081;
server localhost:8082;
}
server {
listen 80;
server_name localhost;
#access_log logs/host.access.log main;
location / {
proxy_pass http://web_servers;
proxy_set_header Host $host:$server_port;
}
3.2.2 Hot Backup:
Assuming there are 2 servers, the second server is only enabled to provide services when one server fails. The order of server request handling: AAAAA suddenly A fails, the order of server request handling: BBBBBBBBBBBBBBB.....
upstream web_servers {
server 127.0.0.1:7878;
server 192.168.10.121:3333 backup; #hot backup
}
3.2.3 Weight
Requests are distributed to different servers in different numbers according to the size of the configured weights. If not set, the default is 1. The request sequence of the server is: ABBABBABBABBABB.....
upstream web_servers {
server localhost:8081 weight=1;
server localhost:8082 weight=2;
}
3.2.4 ip_hash
This way, each IP address is fixed to access a backend server, which can solve the session problem.
upstream test {
ip_hash;
server localhost:8080;
server localhost:8081;
}
3.2.5 fair(Third-party)
Requests are allocated based on the response time of the backend server, with shorter response times given priority. This configuration is for faster user response.
upstream backend {
fair;
server localhost:8080;
server localhost:8081;
}
3.2.6 url_hash(Third-party)
Requests are allocated based on the hash result of the accessed URL, so that each URL is directed to the same backend server, which is effective when the backend server is used as a cache. Adding the hash statement to the upstream, hash_method is the hash algorithm used.
upstream backend {
hash_method crc32;
hash $request_uri;
server localhost:8080;
server localhost:8081;
}
The above 6 types of load balancing are applicable to different situations and can be used singly or in combination. They can be selected according to actual conditions, and fair and url_hash require the installation of third-party modules to use.
4 Separation of Static and Dynamic Pages:
4.1 Concept of Separation of Static and Dynamic Pages:
Separation of static and dynamic pages refers to the architectural design method of separating static pages from dynamic pages or static content interfaces and dynamic content interfaces in web server architecture, thereby improving the overall service access performance and maintainability.
4.2 Example of dynamic-static separation:
upstream web_servers {
server localhost:8081;
server localhost:8082;
}
server {
listen 80;
server_name localhost;
set $doc_root /usr/local/var/www;
location ~* \.(gif|jpg|jpeg|png|bmp|ico|swf|css|js)$ {
root $doc_root/img;
}
location / {
proxy_pass http://web_servers;
proxy_set_header Host $host:$server_port;
}
error_page 500 502 503 504 /50x.html; # Redirect internally when 500 502 503 504 errors occur
location = /50x.html {
root $doc_root;
}
}
Result: When accessing http://localhost/test.jpg, the image in the /usr/local/var/www/img path is returned directly.
Accessing http://localhost/index.html will access the backend server (tomcat, etc.)
5 Other commonly used directives:
5.1.return directive
Return HTTP status code and an optional second parameter that can be a redirect URL
return code [text];
return code URL;
return URL;
For example:
location / {
return 404; # Return status code directly
}
location / {
return 404 "pages not found"; # Return status code + a piece of text
}
location / {
return 302 /bbs ; # Return status code + redirect address
}
location / {
return https://www.baidu.com ; # Redirect to this address
}
5.2 rewrite directive
Rewrite URI request rewrite, which can modify the request URI multiple times during request processing using the rewrite directive, the directive has one optional parameter and two required parameters.
The first (required) parameter is the regular expression that the request URI must match.
The second parameter is used to replace the matched URI.
Optional third parameter rewrite strategy
last The rewritten URL initiates a new request, enters the server block again, and retries the matching in the location block;
break Directly use the rewritten URL, and no longer match other location statements;
redirect Returns 302 temporary redirect;
permanent Returns 301 permanent redirect;
location /users/ {
rewrite ^/users/(.*)$ /show?user=$1 break;
}
5.3 error_page directive
Using the error_page directive, you can configure NGINX to return custom pages and error codes, replace other error codes in the response, or redirect the browser to other URIs. In the following example, the error_page directive specifies the page (/404.html) to return the 404 page error code.
server{
error_page 500 502 503 504 /50x.html;
location =/50x.html{
root html;
}
}
5.4 Logs
Access logs: gzip must be enabled; otherwise, no log files will be generated. Uncomment log_format and access_log.
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /usr/local/etc/nginx/logs/host.access.log main;
gzip
5.5 deny, allow directives
# Ban access to a directory
location / {
allow 192.168.0.0;
allow 127.0.0.1;
deny all;
# This configuration allows requests from the 192.168.0 network segment and 127.0.0.1, and rejects all other source IPs.
}
5.6 Built-in Variables
The built-in variables that can be used in the nginx configuration file start with the dollar sign $. Most of the predefined variable values are carried by the client.
$args: This variable is equal to the parameters in the request line, the same as $query_string
$content_length: The Content-length field in the request header.
$content_type: The Content-Type field in the request header.
$document_root: The value specified by the root directive for the current request.
$host: The hostname in the request line, if it is empty, it is the hostname in the Host request header, and if it is empty, it matches the server_name
$http_user_agent: The client's agent information
$http_cookie: The client's cookie information
$limit_rate: This variable can limit the connection rate.
$request_method: The action of the client's request, usually GET or POST.
$remote_addr: The IP address of the client.
$remote_port: The port of the client.
$remote_user: The username that has been authenticated by the Auth Basic Module.
$request_filename: The file path of the current request, generated by the root or alias directive and the URI request.
$scheme: HTTP method (such as http, https).
$server_protocol: The protocol used by the request, usually HTTP/1.0 or HTTP/1.1.
$server_addr: The server address, which can be determined after a system call is completed.
$server_name: The server name.
$server_port: The port number of the request reaching the server.
$request_uri: The original URI containing request parameters, does not contain the hostname, such as: ”/foo/bar.php?arg=baz”.
$uri: The current URI without request parameters, $uri does not contain the hostname, such as ”/foo/bar.html”.
$document_uri: It is the same as $uri
6 Summary
Ngnix is a high-performance reverse proxy server, and it is very necessary to learn it. This article explains the core configuration of Ngnix, introduces the three major functions of reverse proxy, load balancing, and static and dynamic separation, and finally expands some commonly used commands. This article introduces the basic usage of Ngnix, and the subsequent core and principle parts of Ngnix are yet to be studied.
评论已关闭