Recently, experts have discovered a phishing campaign impersonating security company Proofpoint. The phishers are sending emails in the name of the cybersecurity company Proofpoint to potential victims. These phishing emails use mortgages as bait to lure victims into providing their Microsoft Office 365 and Gmail account passwords.
An article posted by Armorblox reads: "The email contains a security file link sent by Proofpoint." When users actually click on the link, the page will automatically jump to the Proofpoint brand launch page, along with multiple login links from various email providers.

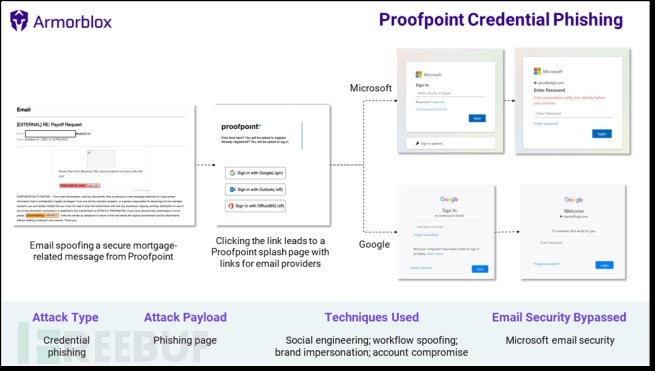
The phishing attack also includes dedicated login pages for Microsoft and Google. Clicking on the link with Google and Office 365 logos will take potential victims to carefully designed Google and Microsoft phishing pages, requiring users to provide their login account and password.
The investigation found that the phishing emails were sent from a stolen private account, the sender's domain (sdis34[.]fr) is the French Southern Fire and Rescue Department. These phishing web pages are hosted on the "greenleafproperties[.]co[.]uk" domain, which was updated in April 2021. Currently, the website has been redirected to "cvgproperties[.]co[.]uk".
The following are the main findings of this phishing campaign:
Social engineering techniques: The email title and content are designed to create a sense of trust and urgency in the victims. The sense of trust comes from the fact that the email contains a file sent by Proofpoint; urgency comes from the information it contains about mortgages and other family-related activities.
Impersonating well-known brands: Both the email and the login page are imitating Proofpoint, Google Workspace, and Office 365 login pages, which are filled with their respective email provider brand logos.
Copying existing workflows: The email attack steps are also simulating existing workflows in daily life, such as email notifications received when sharing files online. When people see emails they have seen before, they tend to quickly click to view them.
Using a stolen email address: The email sending address comes from a stolen personal account of the French Fire and Rescue Department.
Reference source: https://securityaffairs.co/wordpress/124298/cyber-crime/phishing-campaign-proofpoint.html
评论已关闭