Ma Yunlong, Tsinghua University Information Technology Center
Author's introduction:
Ma Yunlong, male, senior engineer of Tsinghua University Information Technology Center; Coremail administrator community big shot guest
Deeply involved in the post of university computer network, informationization, and network security for 20 years, with a profound understanding of large-scale computer network and information system planning, development/construction, and operation and maintenance.
Currently, more and more universities, enterprises, and government agencies are implementing 2FA two-factor identity authentication for email systems to improve the security of email accounts, which can effectively prevent malicious attacks or misuse of email accounts.Two-factor authenticationIt is a system that uses time synchronization technology, generating a one-time password based on the three variables of time, event, and key to replace the traditional static password. Each dynamic password card has a unique key, which is also stored on the server side. During each authentication, the dynamic password card and the server calculate the dynamic password to be authenticated based on the same key, the same random parameters (time, event), and the same algorithm, thereby ensuring the consistency of the password. Two-factor identity authentication usually refers to the need to provide two or more identity verification factors when logging in to an account, such as adding dynamic passwords, scanning codes, message push, email authentication, fingerprints, faces, irises, voices, USB certificates, and other authentication methods outside the user name.
The core of two-factor authentication lies in 'identity determination'. Simply put, any factor that can be added to the basis of username + static password to determine identity can be called two-factor authentication. This can effectively prevent hackers from breaking into accounts through brute force attacks or illegal password theft, thereby improving account security. At the same time, two-factor authentication conforms to relevant security regulations and compliance requirements, effectively protecting user data and privacy.
Dynamic password is the most widely used two-factor authentication method currently. When we log in to various websites or APPs, we usually need an SMS verification code to determine whether it is the person operating. This is the most common and most effective way among C-end individual users. However, in B-end corporate users, SMS verification codes are rarely used. First, SMS verification codes are completely dependent on operator signals, with poor timeliness. Moreover, there is a risk of SMS being intercepted, which has a low security level.
Although both dynamic password tokens, the authentication logic and process are not the same. Among them, the authentication principles of mobile phone verification codes and WeChat official account tokens are relatively similar. The user side applies for a dynamic password to the authentication server, and the authentication server generates a dynamic password and sends it to the user side in the form of an SMS verification code or a WeChat official account message through the SMS gateway or the WeChat official account service end. The general login process is as follows (take SMS as an example, the picture comes from Zhihu):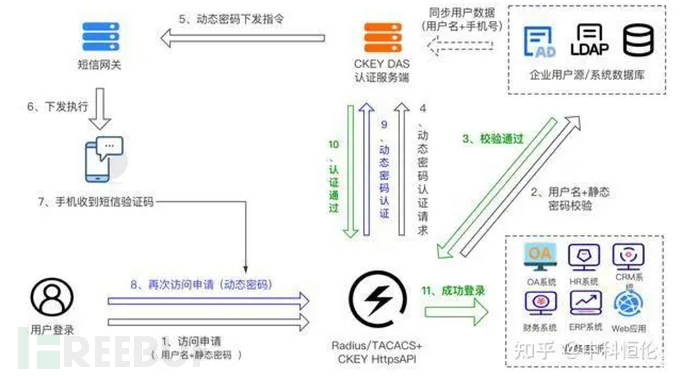
Therefore, before enabling two-factor authentication, the following prerequisites need to be completed: business systems and authentication systems are connected, enterprise user sources and authentication systems are synchronized, and SMS gateways (or SMS platforms) and authentication systems are connected.
The authentication process is as follows:
- Users enter the username + static password to apply for access to the business system;
- The business system sends the request information to the enterprise user source via the API interface for preliminary verification;
- The enterprise user source verification is successful, and the verification passes;
- The business system applies for the dynamic password from the authentication system via the API interface;
- Generate the dynamic password and let the SMS gateway send the dynamic password to the mobile phone number bound to the applicant user;
- The SMS gateway executes the send dynamic password command;
- Users receive the SMS verification code on their mobile phones;
- Users enter the verification code for a second access application (identity secondary verification);
- The business system sends the request information to the authentication system via the API interface for dynamic password verification;
- The authentication system verifies successfully, and the verification passes;
- Successfully log in to the business system.
Note: 1 The WeChat official account authentication process is consistent with SMS authentication. The user account is bound on the WeChat service end, and the SMS gateway is replaced with the WeChat service end; the email authentication process is the same as SMS authentication, replacing the SMS gateway with the email server;
Hardware tokens, APP tokens, WeChat Mini Program tokens, DingTalk tokens, and PC tokens are very similar, with the logic of: built-in encryption algorithm, clock, and key, which continuously generate new passwords with time changes. By comparing passwords with the authentication server that has the same encryption algorithm, clock, and key, dynamic password verification is realized. The general login process is as follows: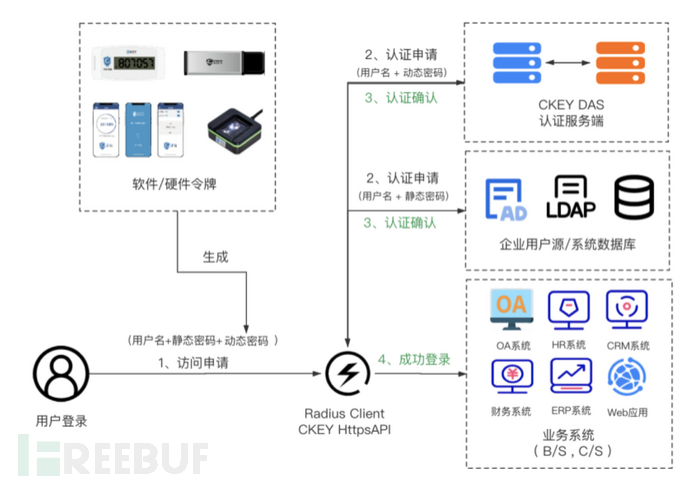
Taking the Coremail email system as an example, the following prerequisites need to be completed before enabling two-factor authentication: business systems and authentication servers are connected; enterprise user sources are connected; authentication tokens and users are bound;
The authentication process is as follows:
- Users enter 'username + static password + dynamic password' to access the target host;
- The target host sends the username + static password to the enterprise user source for static authentication via Radius Client or API, and sends the username + dynamic password to the authentication server for dynamic authentication simultaneously;
- Users provide feedback on the authentication separately;
- Access can only be successfully achieved when both static password authentication and dynamic password authentication are passed simultaneously; otherwise, the login will fail.
In addition to scanning for login and biometric recognition, which are also common two-factor authentication methods, there is no need to introduce them one by one. In this implementation of the Tsinghua University email system's two-factor authentication, we have chosen SMS authentication and OTP as one of the two factors, and the following introduces several issues that need to be paid attention to since the implementation.
Question 1: After setting up two-factor authentication, why can the same password be used to log into webmail but not log into third-party clients (such as Outlook, Foxmail, email app, etc.)?
Answer: The client needs to enter the client-specific password. After logging into webmail, go to the 'Settings→Security Settings→Client Security Login' page, click on 'Generate Dedicated Password', copy the dedicated password, and then log in to the third-party client using the dedicated password.
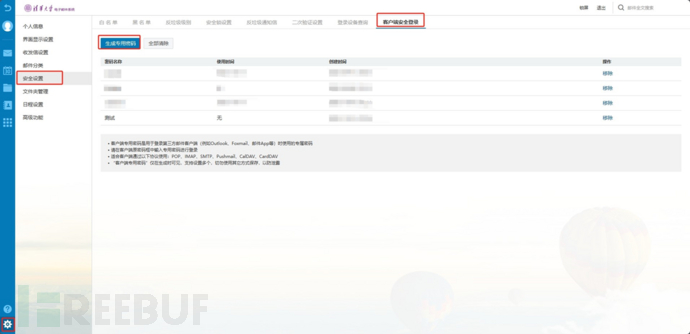
Figure 1
Question 2: Why do I still need to enter a text message verification code each time I log in after setting up a trusted device?
Answer: After restarting the browser, if the trusted device is still not effective, there are several possibilities:
1) It may be that the browser is set to clear cookies each time it is closed, and you need to adjust the browser settings yourself.
2) It may be that the local computer and the server have a time difference, and the time server can be set to:ntp.tuna.tsinghua.edu.cnOr 166.111.8.28.
Path: Right-click on the time and date in the taskbar → Select 'Adjust Date and Time' (Figure 2) → Select 'Add Different Time Zone Clock'/'Additional Clock' (Figure 3) → Click 'Internet Time', select 'Change Settings' → Enter the server address ntp.tuna.tsinghua.edu.cnOr 166.111.8.28 → Click 'Update Now' → Click 'OK' (Figure 4).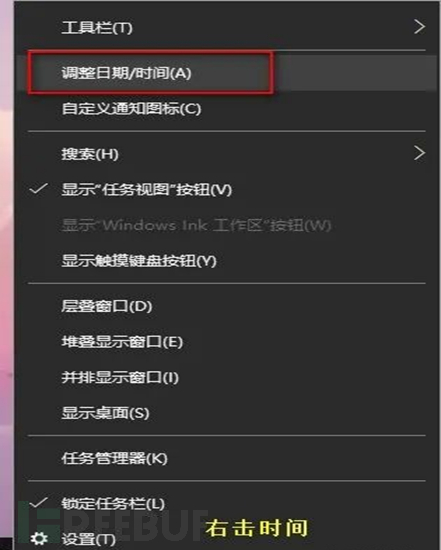
Figure 2
 Figure 3
Figure 3
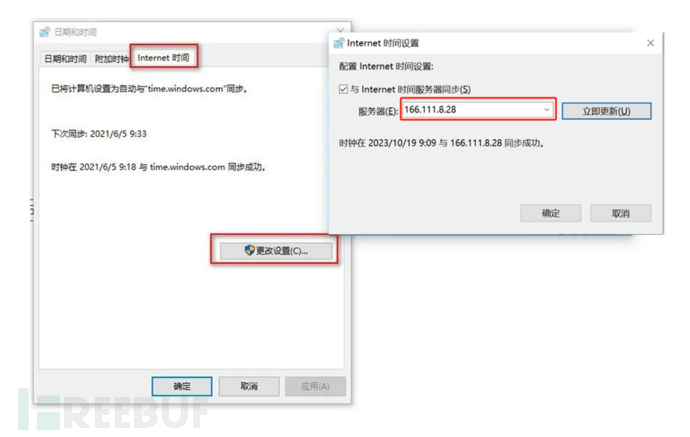
Figure 4
Question 3: How many email addresses can a single phone number be bound to?
Answer: Currently, the two-factor authentication supports binding multiple email addresses to a single phone number.
Question 4: What are the ways to use the email on the mobile phone?
Answer:
1) You can use the email client built into the phone;
3) If the email account is the same as the info account, in the campus network environment, you can access the email without logging in by selecting the new information portal-app-popular through the
Question 5: How to set up a trusted device for mobile browsers?
Answer: If the browser on the phone supports accessing the computer version of the page (or can use the phone as a computer terminal), it is possible to configure a trusted device after web access, but not every browser chosen by the phone can find this option. If the computer version has been set up but the option to configure a trusted device is still not available, please try restarting the browser.
Question 6: When multiple people need to log in from different places to access files and information through the work email, how should this be handled?
Answer: It is recommended to bind the mobile number of the email administrator to the work email. Other teachers can use third-party clients (e.g., foxmail, outlook, and other software) or set the computer as a trusted device when logging in to the web version of the email for the first time, after which they do not need to log in with a verification code.
7. Question: If the email account is no longer in use, is it still necessary to configure two-factor authentication?
Answer: For email accounts that are in abnormal usage states such as overdue payment or frozen status, two-factor authentication can be configured when enabling the email account. If the account is indeed not used for a long time, an application for account cancellation or freezing can be made to ensure security.
8. Question: If the mobile phone is lost, will it cause the password of the mobile email client to be leaked?
Answer: The email password is not stored in plain text on the client, and generally, the mobile password cannot be copied.
9. Question: Can foreign mobile numbers be bound?
Answer: Not yet.
10. Question: Some office email accounts are configured on the system, used for sending external emails. How should such email accounts be configured?
Answer: Please be sure to set up the two-factor authentication for the email system in time, generate the client-specific password, and configure the client-specific password on the system. Otherwise, the email account will not be usable after November 1st; if there are still issues after the configuration, it is recommended to contact the system development vendor to check the program or contact the Information Technology Center.
11. Question: If I couldn't set up the two-factor authentication for the email system in time before the mandatory activation on November 1st, how can I use the email account after November 1st?
Answer: Please be sure to activate the two-factor authentication for the email system and set up the client password before November 1st. Otherwise, the email client will not be usable after the mandatory activation; when logging into the web version of the email, a reminder to bind the mobile number will also pop up. If the mobile number is not bound, the web version of the email cannot be used.
12. Question: After setting up two-factor authentication, when clicking on 'Client Secure Login', there are no buttons such as 'Generate Specific Password' within the page. How should this be resolved?
Answer: It may be related to the browser cache. Please clear the browser cache and try again.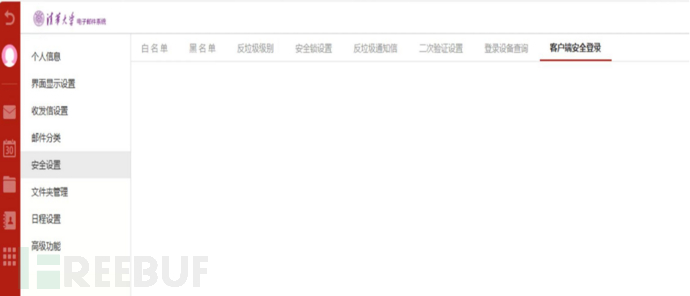
Figure 5
13. Question: Teachers and students who have graduated cannot log in to their email accounts, but they chose to retain the email forwarding permission for half a year when they logged out of their network accounts. How should two-factor authentication be carried out in this case?
Answer: Users who have retained the email forwarding permission for half a year do not need to set up two-factor authentication, and the forwarding permission is not affected.
14. Question: I have set up two-factor authentication, but why can't I still enter the Foxmail client with the client-specific password?
Answer: Due to the update of the Foxmail client. Please disable IPv6 or try to log in after covering the installation with a lower version of the client.
Summary: Since the mandatory implementation of two-factor authentication for the email system 2 weeks ago, a total of 51,575 email users have activated two-factor authentication, accounting for 71% of the total users. From the perspective of user activity, the monthly active users of the entire site's email are also around 70%. This implementation process also has a long-tail effect, and it cannot be expected to be achieved overnight. In short, since the implementation, the theft of email passwords and the precise phishing using the webmail address book have been prevented. At the same time, the mechanism for detecting spam in outgoing emails has been canceled, further improving the user experience.
评论已关闭
