For our daily operation and maintenance personnel, Linux should be something we often deal with (if not, maybe it's not operation and maintenance, but maintenance...just kidding), the status of Linux in the data center is as unbreakable as that of Windows in the office space. The deployment of various software is首选 Linux! The three most commonly used login entries for Linux operation and maintenance are:
Ssh, console, and graphical interface (if any).

To ensure more secure operation and maintenance, two-factor identity authentication system dynamic passwords are usually used to strengthen login security. Let's briefly discuss how to strengthen two-factor authentication for these three entry points?
Firstly, a two-factor identity authentication system will be deployed to bind accounts and tokens one by one, activate tokens, and manage tokens;
Then deploy the pam_radius plugin on the Linux host to create a dynamic password input box;
Finally, modify the Linux file to enable the two-factor authentication module for ssh, console, and graphical interface;
Isn't it simple? Alright, let me take centos7.8 (installed with gnome) as an example:
1、Two-factor authentication server
On this side, I use the Zhongke Helun two-factor identity authentication service, and the specific configuration method is not publicly available. You can enter the Zhongke Helun official website and contact us to obtain the installation package and configuration method
2、Deploy pam_radius plugin on Linux host
There are two packages in the plugin: libCkey.so and pam_radius_auth.so
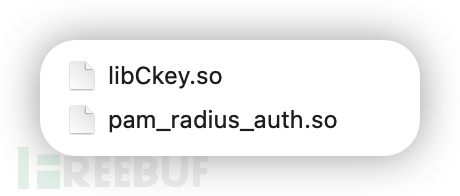
Place the so in /usr/lib64
Place the so in /usr/lib64/security
Up to this point, the plugin is done, isn't it very simple?
3、Modify the corresponding file
Here, although there are 3 entries, actually two files are loaded, among which the file loaded by console is " /etc/pam.d/system-auth ", and the files loaded by ssh and the graphical interface are the same, " /etc/pam.d/password-auth ". Therefore, the focus needs to be paid to these two files, as follows:
Configure authentication server (this step is common!)
# mkdir /etc/raddb //Create the raddb folder (name fixed) # vim /etc/raddb/server //Configure authentication server information, the name of 'server' cannot be changed 172.16.146.132 12345678 10 Authentication server address Shared secret Timeout time
Configureconsole two-factor authentication
# vim /etc/pam.d/system-auth
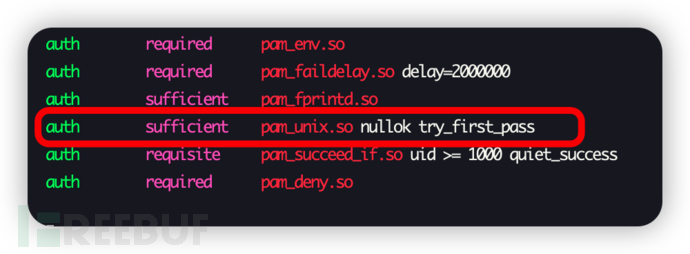
Let's put the comparison diagram of modification before and after directly, as the text description is a bit tedious
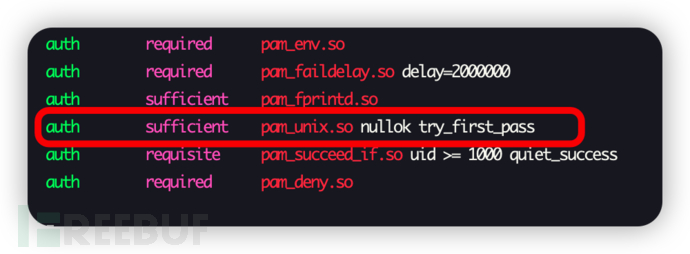
△ Before modification
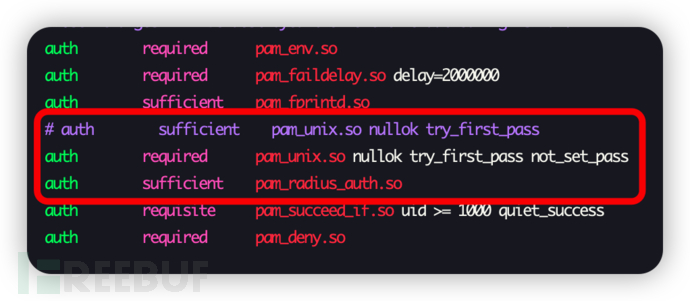
△ After modification
Login effect (console)
Login //Username
Password //Local static password
CkeyPassword //Dynamic password
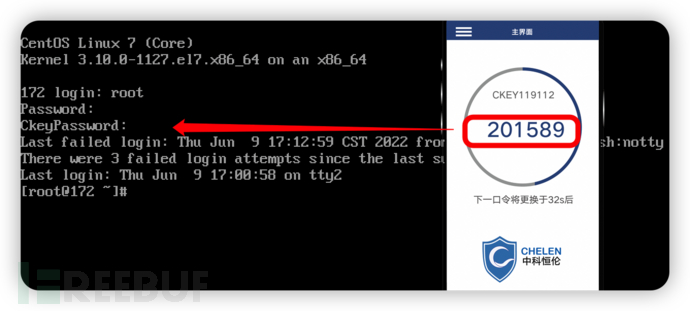
Up to this point, dynamic password login to console is implemented to achieve two-factor authentication.
Configure ssh and graphical interface two-factor authentication
Firstly, you need to modify"/etc/ssh/sshd_config "
# vim /etc/ssh/sshd_config
PasswordAuthentication no
ChallengeResponseAuthentication yes
UsePAM yesThen modify "/etc/pam.d/password-auth"
# vim /etc/pam.d/password-auth
The modification method here is consistent with system-auth
△ Before modification
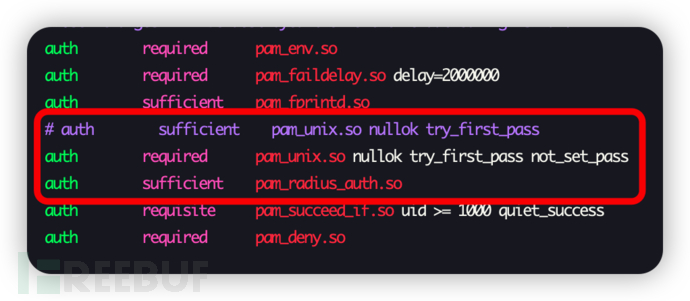
△ After modification
Login effect (ssh)
If it is a graphic tool, select the authentication method: Keyboard Interactive, and use ssh directly in the command line
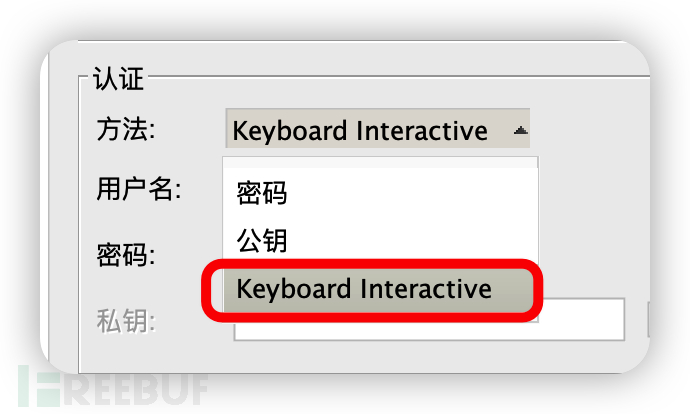
1. Enter the username
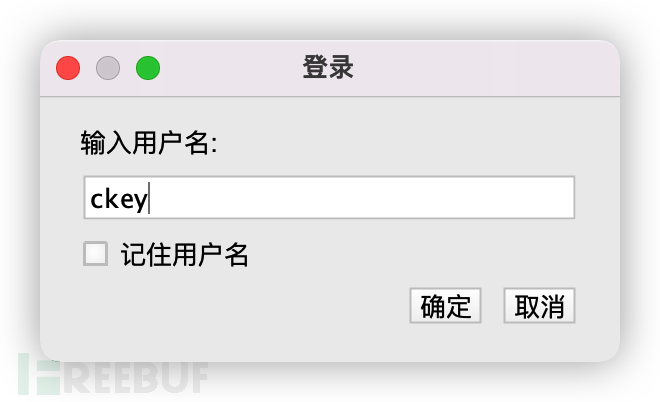
2. Enter the local static password
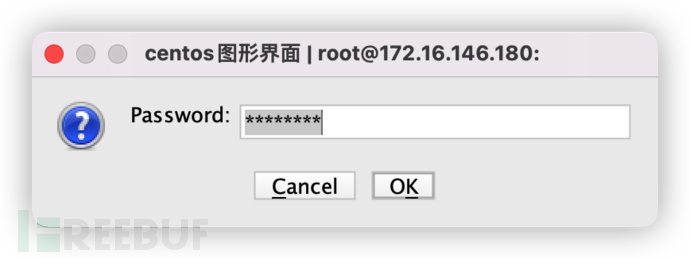
3. Enter the dynamic password
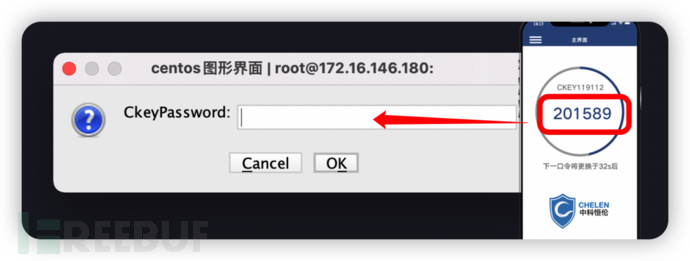
Login effect (graphical interface)
1. Enter the username
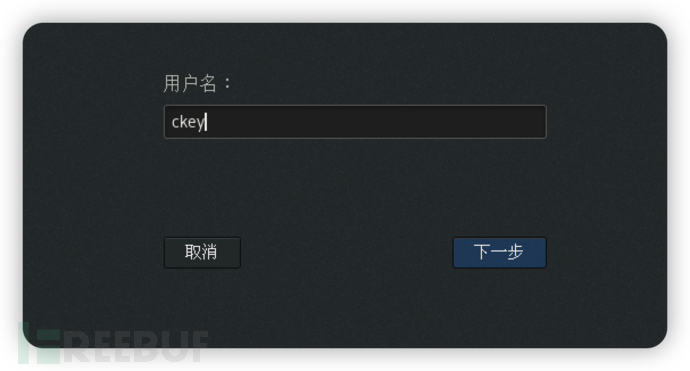
2. Enter the local static password
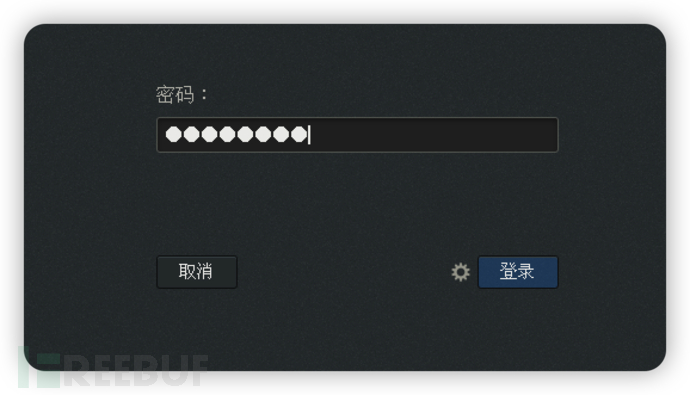
3. Enter the dynamic password

Up to this point, double-factor authentication has been implemented on all 3 login entries, achieving secure access to Linux hosts.
There are many resources online about the benefits of using dynamic passwords, and I will not elaborate on this here. I will also write a dedicated article later, tentatively titled "The Principle and Advantages of Two-Factor Authentication Dynamic Password Technology" for your reference!
评论已关闭