The information security community often ignores network devices at the endpoint. Most people focus on protecting systems and detecting threats in Windows domain environments, including threats on endpoints running MacOS and Linux systems.
Common log recording tools used for these tasks include Sysmon on Windows, Auditd and Auditbeat on Linux and MacOS. For network purposes, NIDS systems such as Snort or Suricata are typically used to analyze network traffic, and tools like Zeek and PCAP are used to parse relevant protocols for future analysis.

All this data is usually centralized into a log analysis tool, such as ELK or Splunk, where analysts run search queries or perform analyses to detect attack behaviors in their environment. The MITRE ATT&CK framework provides a good starting point for measuring and shaping the techniques used by analysts in data detection, based on the strategies that attackers may take at each step of the kill chain.Read more about the MITRE ATT&CK framework here.)
However, what the Enterprise ATT&CK matrix does not cover is the network devices themselves and the strategies and techniques that attackers may perform on such devices. Some may say that this attack surface is small and not a reasonable target, but I disagree. In the network, Windows accounts for about 75-90% of the total number of devices, Linux about 1-3% of the total number of devices, and network devices usually account for 10-20% of the total number of devices. This includes routers, switches, firewalls, VPN concentrators, wireless access points, and wireless LAN controllers, among others.
These network devices have CVEs like Windows, Linux, and MacOS, and these high vulnerabilities make it possible to obtain 'system' or 'root' access permissions (level 15). Administrators usually patch these vulnerabilities less often, as they are not as automated as the Linux yum/apt commands, nor as simple as the SCCM/WSUS servers. Network infrastructure devices are almost always older because they are replaced infrequently and are not within the supplier's support scope. Network devices typically have non-changeable default credentials and insecure configurations (such as enabled Web GUI). Potential attackers can exploit these misconfigurations and vulnerabilities.
These network devices provide more than just the network traffic to be analyzed. Like Linux syslog, they also have logs that can be forwarded to a SIEM. Syslog is a good starting point; it's not about the 'Network Operations Center,' but about the 'Security Operations Center.' Syslog is very useful and can find valuable events at the warning, error, and debugging levels, but these logs are mainly about the operations being performed by the devices.
Most modern network devices deployed in enterprises support remote logging. Cisco, Brocade, Juniper Networks, Dell, and others all support AAA with TACACS or RADIUS. AAA stands for Authentication, Authorization, and Accounting. When access permissions to these network endpoints are opened, administrators can view what is happening on these devices. Are administrators adding local users? Analyzing these logs using the MITRE ATT&CK model will help detect whether the operations performed on the network infrastructure are legitimate.
Currently, the MITRE ATT&CK model has not categorized network devices and their operating systems as 'Platform'. And only one 'Technique' references 'Network Device Logging' as a data source. The required analytical methods for detection depend on network device logs, especially on AAA authentication and accounting logs. Authorization will mainly be used to mitigate risks and ensure that network administrator accounts have the minimum privileges required to perform their functions.
Of the current 244 Enterprise ATT&CK techniques, 64 can be applied to network devices. Using AAA, Netflow, IDS, and Syslog, administrators will be able to detect most events on network devices, whether they are legitimate management or malicious activities.
The statement of the U.S. CERT
Russian cyber attackers have exploited many outdated or weak protocols and service ports related to network management activities. The vulnerabilities exploited by these attackers include:
Identify vulnerable devices;
Extract device configuration;
Map internal network architecture;
Collect login credentials;
Masquerade as privileged users;
Modify device firmware, operating system, and configuration;
And replicate or redirect victim traffic through infrastructure controlled by Russian cyber attackers.
In addition, Russian cyber attackers may modify or deny traffic passing through routers.
The U.S. CERT believes that routers and switches are being targeted as attack vectors:
APT and Malware Targeting Network Devices:
SYNful Knock — Cisco Router Injection
https://www.fireeye.com/blog/threat-research/2015/09/synfulknock-_acis.html
Dragon fly 2.0 / Berserk Bear https://www.darkreading.com/endpoint/privacy/russian-apt-compromised-cisco-router-in-energy-sector-attacks/d/d-id/1331306
Gekko Jackal — Activist Group https://go.crowdstrike.com/rs/281-OBQ-266/images/15GlobalThreatReport.pdf
Symantec - Hacking routers 101 https://www.symantec.com/connect/articles/exploiting-cisco-routers-part-1
Data Source:
Currently, MITRE has a data source called 'Network Device Logs', but there is not much information about it, just a technology that can be used currently. This article proposes the following categories of network device logging:
1. Network device (system) logs - through Syslog protocol
2. AAA logs - through TACACS or RADIUS protocol
The following figure is a layer in the ATT&CK Navigator, representing all the technologies applicable to network devices and color-coded by the data sources available for detection data. The 'Accounting' data source (blue) is further divided into high, medium, and low confidence to indicate the ease of determining whether the operation is a legitimate administrative operation or an adversary's operation.
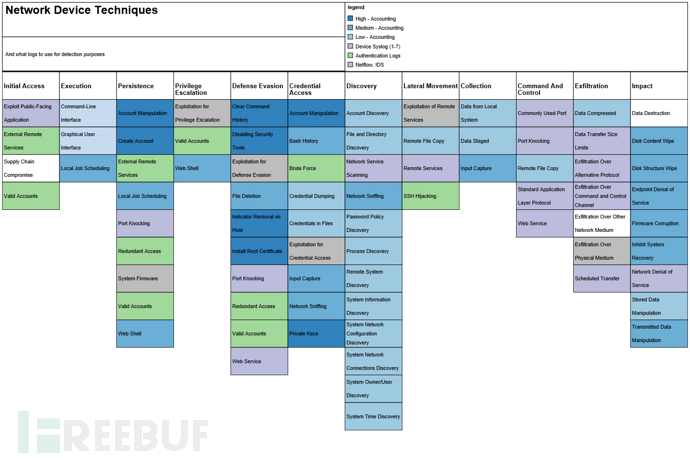
For data sources, please refer to the JSON of ATT&CK Navigator)
Analysis
Twelve 'Sigma' rules were written using 'billing' data from AAA of network devices. Many operations performed on network devices are typically performed by administrators, so there are some methods to reduce the false positive rate. Baseline network administrators regularly perform operations on the system, which are usually represented by who performs the function and when it is performed. By enabling rules, observing and recording common behavior, you can adjust the rules to reduce the number of alerts.
Read more about the Sigma project (SIEM system's universal signature format) here!)
Some notes on the rules. Usually in network operating systems, commands can be shortened and the command will still run, for example, 'show history all' can be shortened to 's hi a', and the same results will still be given. However, when logging in with AAA, TACACS will record the complete expected command. Therefore, when writing detection analysis for certain commands that are currently running, only the complete command must be considered. When the | (pipe) command is used with 'include' to filter results, the results that are not displayed in the AAA accounting log are not displayed. Only filter the content displayed in the terminal output.
Mitigation Measures
Most of the mitigation measures listed on the MITRE ATT&CK Wiki are generally applicable to networked devices. However, the main mitigation measures that are not listed overall and are specifically applicable to network operating systems are the authorization aspects that are necessary when applying AAA, which involve granting limited user privilege level access permissions. Enterprise policies can even restrict the commands allowed for administrators to run.
Segment network devices across different VLANs, securely configure devices according to best business practices, change default credentials, appropriately apply patches, apply the principle of least privilege, enable remote logging, and follow the NIST governance framework.
An overview of 12 strategies in the enterprise matrix applicable to network devices
Initial Access
The four technologies mainly related to network devices are mainly exploiting vulnerabilities or using stolen credentials to log in remotely. The network infrastructure is likely not the initial access vector to enter the network, but it indeed provides an attack surface that attackers can use as a foothold.
Execution
Attackers have two main vectors: either using the command line or using GUI (if enabled). View the operations being performed using billing logs.
Maintaining Access
Like Windows or Linux computers, attackers can create a new account, schedule tasks, use valid accounts, and even replace firmware (like SYNful Knock malware).
Defense Evasion
Attackers can clear command history records, even close remote logging with appropriate access permissions, which is achievable. This is why alerts for these analyses should be issued with high confidence and priority. Train network administrators not to perform these functions to reduce the rate of false positives.
Credential Access
Similar to maintaining access, credentials can be recovered by viewing the history (including plaintext passwords), the files saved on the device (old configurations), or even by packet sniffing the device itself.
Discovery
These are commands that ordinary administrators can run. By creating a baseline from the creation point and viewing the frequency of use of these commands, custom baselines can be created. Some commands may have never been used, and these may become more useful alerts. Find a common time when an administrator can perform these functions, or when always performed by the same person. Then customize alerts for the network environment.
Lateral Movement
Files are usually copied between devices using scp, tftp, or ftp.
Collection
The configuration of network devices provides a lot of information about the network, including the keys and passwords that attackers want to collect.
Command and Control
Web services and common ports can be used to communicate with the C2 servers owned by attackers in their cloud infrastructure.
Leakage
Data can be easily exported through file transfer or through common ports, even by pasting and copying!
Impact
The impact is most suitable for network devices, as it can affect a large part of the network. You can place ACLs on the device to discard or reduce traffic. You can erase the configuration, and restarting will cause the DOS to enter the network device. You can modify the configuration, erase the file system, delete files, and write firmware, etc. All of these may cause damage to the device and network.
Technology
Check out the detailed classification of 64 types of ATT&CK technologies applicable to network devices here!It provides a detailed introduction to the technology, data source, example network device commands (if applicable), and comments on why it is applicable.
*Author of this article:makaisghr, please note the source from FreeBuf.COM when转载
评论已关闭