Docker uses privileged mode to escape and obtain host permissions.
During the process of tracing and countermeasures, one often encounters some interesting methods. Here, I would like to share a method of docker escaping in privileged mode and obtaining host permissions.
Preface
During a process of tracing and countermeasures, a host was found, and after asset collection, several assets were found as follows.

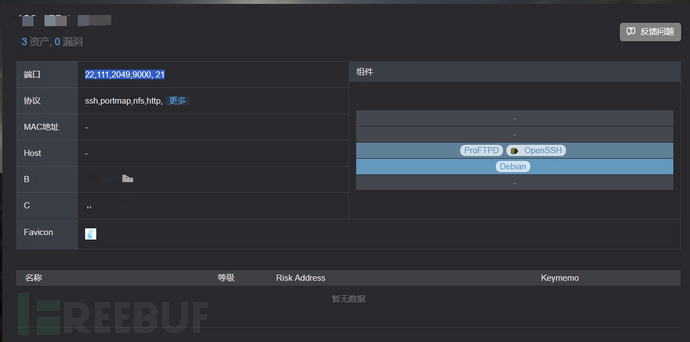
Among them, 9000 is a web service, so I visited and checked it out.
It was found to be the Portainer backend, and there was a weak password login.

Generally, when encountering such a login page, people tend to input admin/admin, admin/password, admin/123456. Then, one of them is found to work.
Portainer
Portainer is a graphical management tool for Docker, providing a status display panel, quick deployment of application templates, basic operations of container image network data volumes (including operations such as uploading and downloading images, creating containers, etc.), event log display, container console operations, centralized management and operations of Swarm clusters and services, and login user management and control functions. Its functions are very comprehensive and can basically meet all the needs of container management for small and medium-sized units.
This is the first time I encountered this background in the tracing process, and I briefly browsed through it
The background looks like this 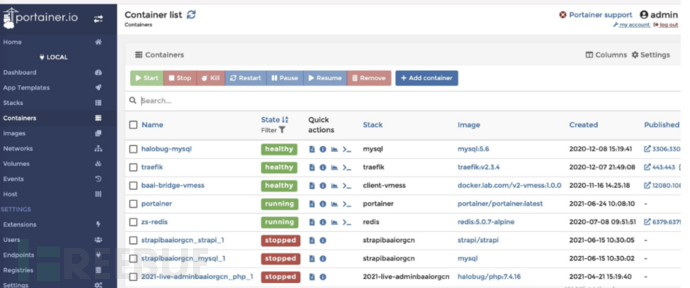
There are many pre-created Docker containers here. You can also download custom images and build containers
Utilize
I thought that if I added the --privileged parameter (privileged mode) to the Docker container startup, I could use disk mounting. After mounting, I can replace local host files, such as writing a public key to getshell. Thinking of this, I clicked to create a new container. I selected the nginx:latest image
Note that you must check the following option to enable privileged mode
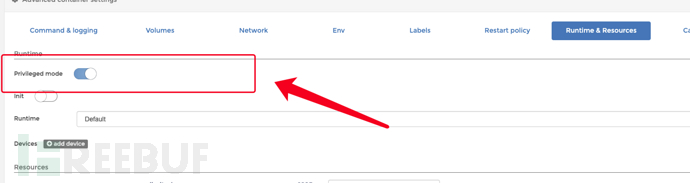
After checking this option, the privileged mode will be enabled.
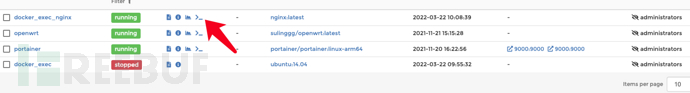
After creating the container, click here to enter the container console.
Now we need to mount the disk to the container's directory. This is different from the container data volume settings, as this step is a real disk mount.
View the disk using the df -h command, create a folder /abcd, and then mount the host machine's filesystem onto the /abcd directory within the Docker container.
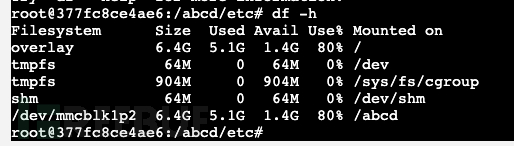
Then, the /abcd directory is the actual host file of the host machine, and we normally write the public key file under root.
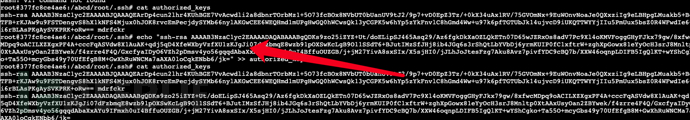
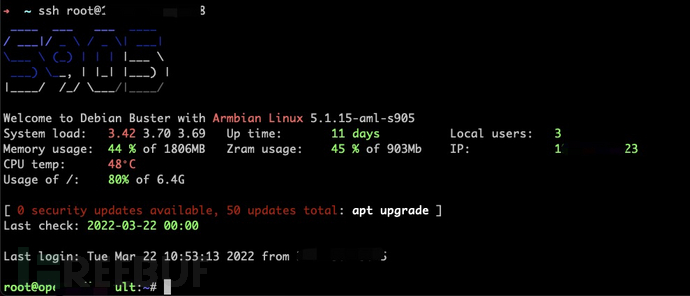
You can directly log in via ssh after that
Summary
This is a real situation I encountered in the process of tracing and counteracting. As a cautionary tale, if you are deploying a Docker environment yourself, please do not use the privileged mode!
评论已关闭