This article is the second in the 'Do what you can with what you have' series, and the subject of study isMiao Pan Standard EditionThe focus is onFirmware Flashing,Reverse Engineering of Mining ProgramsandMining Trojan Detection and Prevention。
Compared to the previous article on the bracelet, Miao Pan can be considered a more complex device with stronger playability.The online tutorials mainly focus on brick recovery,Contents related to NAS construction (flashing Synology) and other development-related topics. This article will also briefly touch on this topic, as one of my friends' Miao Pan turned into a brick, and flashing the firmware is also part of the task, but I don't want to repeat others' words, so this article focuses on exploring the technical implementation of Miao Pan's so-called mining technologyand discuss in a way that is out of tune with the topic挖矿木马的检测与防范。

Previous Review:Do what you can with what you have (Part 1) — Xiaomi Mi Band 3
0x00 Basic Knowledge
0x00 - 00 Introduction to Miao Pan
Miao Pan is a private cloud server for the ARM platform, the official website indicates that it can be used for mining. Due to its high hardware versatility, many firmware versions can be adapted to Miao Pan. The main systems currently compatible with Miao Pan are: onespace (X3P), synology (Qunyuan), and openwrt (router). Miao Pan can be used as a downloader or a light backup file server.

0x00 - 01 What is mining
First and most importantly, mining activities are currently prohibited in China!!! The purpose of studying the characteristics of mining activities is to better implement the detection and prevention of mining malware.
BTC concept:
In simple terms, blockchain is (due to various reasons, the author is now more反感 the word decentralized, so it is replaced with distributed) distributed database, or distributed ledger (of course, web3 is constantly evolving, this is not mentioned here, only for Bitcoin). Everyone has a ledger, with strong anti-attack capability, not easy to break, not easy to lose, but the ledger will not be recorded for free, and the reward is Bitcoin. BorrowingHunzi Said comicAs follows:

IPFS concept:
Computer professionals may not agree, it is just distributed, a technology that has been popularized. The most familiar isDistributed storage。
Interstellar File System IPFS(InterPlanetary File System) is a global, point-to-point distributed version control file system, aiming to supplement the current dominant HTTP protocol on the Internet, connecting all computing devices with the same file system together.
 The principle uses content-based addresses instead of domain-based addresses, that is, users do not find an address but content stored somewhere, and it is not necessary to verify the sender's identity, but only to verify the hash of the content. In this way, web pages can be faster, safer, more robust, and more durable. IPFS is a decentralized storage network based on blockchain technology.
The principle uses content-based addresses instead of domain-based addresses, that is, users do not find an address but content stored somewhere, and it is not necessary to verify the sender's identity, but only to verify the hash of the content. In this way, web pages can be faster, safer, more robust, and more durable. IPFS is a decentralized storage network based on blockchain technology.
0x01 Standing on the shoulders of giants
0x01 - 00 Hardware disassembly
The cat disk is also an advanced device, disassembly is very simple, flashing and debugging mainly use the network portUARTandUSBTwo interfaces.
Because the multimeter was borrowed, another efficient pin identification method was chosen - search online~
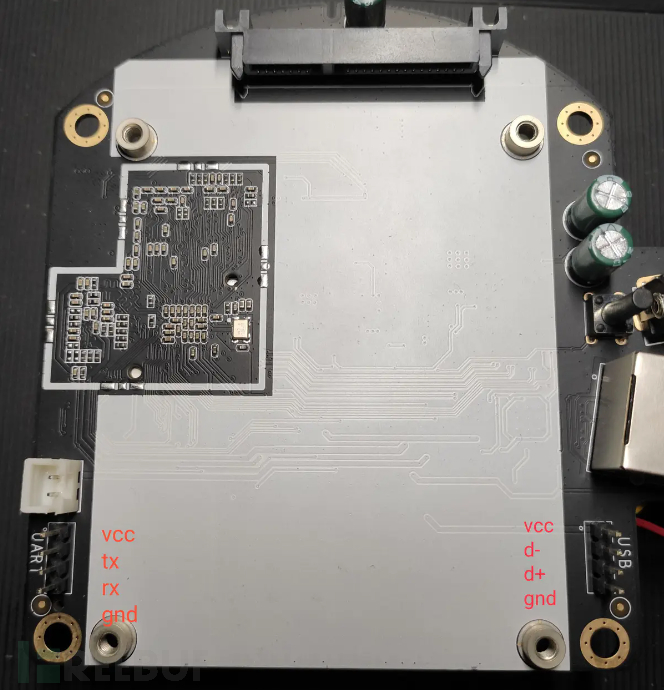
The above diagram has marked the corresponding pins of UART and USB, note that do not connect VCC when flashing (debugging), and the USB interface needs a ttl to USB female adapter to plug in the USB flash drive-.-.
0x01- 01 Firmware and resources
There is nothing much to say, just put the link directly:
Original factory data backup, Extraction code: qc7c
0x02 Do it yourself
0x02 - 00 Flashing with the left hand
Disassemble
A screwdriver can handle it.
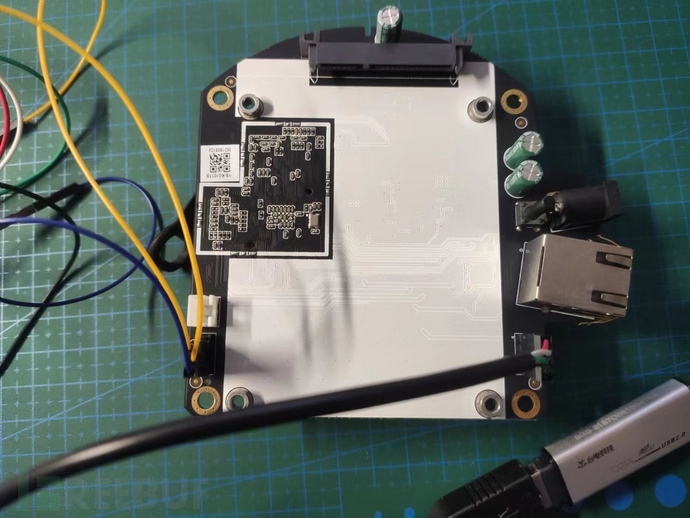
 Connect the UART interface,Emphasize again not to connect VCC!
Connect the UART interface,Emphasize again not to connect VCC!
 Baud rate115200,UARTOutput error, systempanic:
Baud rate115200,UARTOutput error, systempanic:

The first step is to save the bricks.
Rescue brick
First, format the USB drive as MBRext4 or fat32Partition, andflash-image.binCopy it to the root directory and then insert it into the Cat Disk, and spent a fortune of 2.8 yuan on a converter. (UbootIt can also be used, and you can directly flashall.bin)
Enter the following commands in sequence on the U-boot console:
setenv bootargs "console=ttyMV0,115200 root=/dev/mmcblk0p1 rootwait rw init=/bin/sh"
ext4load mmc 0:1 0x1000000 boot/armada-3720-customer0.dtb
ext4load mmc 0:1 0x2000000 boot/Image
booti 0x2000000 - 0x1000000
Takeflash-image.binCopy tommcblk0p2Up:
mount -t proc /proc
mount /dev/mmcblk0p2 /media
mount /dev/sda1 /mnt
cp -f /mnt/flash-image.bin /media
umount /media
umount /mnt
在ubootEnter the following commands in sequence on the console:
ext4load mmc 0:2 0x1000000 flash-image.bin
sf probe
sf erase 0x0 0x200000
sf write 0x1000000 0x0 0x200000
EnterresetReset, then enter the new U-boot flashmac
env default -a
setenv ethaddr "mac_addr"
saveenv
Restart and flashall.bin:
bubt full.bin spi usb
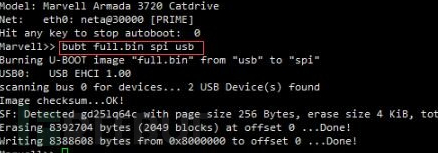
After booting up, you can install the hard disk, network cable, and flash the desired NAS system. There are many tutorials online, so I will not elaborate here.
0x02 - 01 Reverse engineering with the right hand
Stagnant in place
Since seeing binary code makes me want to open and take a look, forflash-image.binIt's all aboutIDAAfter a series of operations, the functions and strings were restored:

While trying to resolve the symbols, it was found to be open sourceU-bootThere is source code -.-, so the analysis work is stillThink twice before actingLet's go.
Reverse engineering of the mining process
The following screenshots are fromUnboxing Review:
 Is the mining process of the Cat Disk the same as that of the miner? You can roughly guess it through hardware configuration~
Is the mining process of the Cat Disk the same as that of the miner? You can roughly guess it through hardware configuration~

A simple search reveals that the principle of mining on the Cat Disk is described as follows:Share the idle storage space of the shared cat disk and utilize the idle upstream bandwidth resources of the home network to form a blockchain storage service platform, output to content, video, game, blockchain and other companies, and obtain various digital currencies paid by these companies. Then exchange them for BTC and return the rewards to the users. The technical details are basically without materials ~.~
In simple terms, it is to use your cat disk asResource node, which can be simplified asP2P sharing economy。So what is the specific implementation??IPFS?FIL?
There are two ideas, one is toProcess list,Port informationLocate what program is running; secondlyStatic analysis of firmware, locate the position of the executable file.
Since the mining service has collapsed and the cat disk is restored after flashing, it is reluctantly chosen for static analysis.
The firmware structure is very simple,binwalkThe following are the partial results of the analysis:
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
8192 0x2000 Linux EXT filesystem, blocks count: 500024, image size: 512024576, rev 1.0, ext4 filesystem data, UUID=81f53685-f951-4b38-bac7-fc009baa9baa
512032768 0x1E850000 Linux EXT filesystem, blocks count: 500032, image size: 512032768, rev 1.0, ext4 filesystem data, UUID=bdf85562-5165-4ec4-8a93-1c6379a479a4
1024065536 0x3D0A0000 Linux EXT filesystem, blocks count: 1658720, image size: 1698529280, rev 1.0, ext4 filesystem data, UUID=a6ce57aa-5432-4047-bf6e-7d5b24142414
......
After unpacking the partial directory:
# tree -d -L 2
.
├── ext-root
├── ext-root-0
│ ├── local
│ ├── opt
│ └── root
└── ext-root-1
├── bin
├── boot
├── dev
├── etc
├── lib
├── lib32
├── libexec
├── opt
├── root
├── sbin
├── usr
└── var
The old method is still used, first learn the positive implementation, and then do reverse engineering. First, understand the construction of IPFS, Fil construction, etc., and then search in the firmware, which is basically some deviant information:
# grep -r ipfs
Binary file ext-root-1/usr/lib/python2.7/site-packages/pygments/lexers/igor.pyc matches
Binary file ext-root-1/usr/lib/python2.7/site-packages/pygments/lexers/_mapping.pyc matches
ext-root-1/usr/share/nmap/nmap-service-probes:match ipfs m|^\\0\\0\\0\\x04\\0\\0(..)\\0\\0\\1\\n\\x10................\\x12.*\\x1a.(?:P-\\d+,?)+".[\\w.,_-]+\\*.[\\w.,_-]+$|s p/InterPlanetary File System peer/
ext-root-1/usr/share/nmap/nmap-service-probes:match ipfs m|^\\0\\0..\\n\\x10................\\x12.*\\x1a.(?:P-\\d+,?)+".[\\w.,_-]+\\*.[\\w.,_-]+$|s p/InterPlanetary File System peer/
Since there are too many files, it takes too much time to go through them one by one, after all, one still needs to do manual labor. Generally, this is started from the web interface and traced back, but an unexpected command was used here to open the situation:
# grep -r -P '[\\p{Han}]' # Search for Chinese string
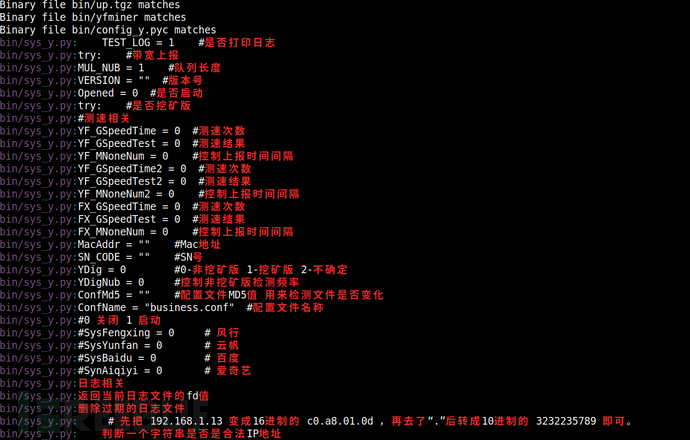 It is necessary to praise the developers for their serious and responsible attitude. If those malicious software authors also had such a good conscience, reverse engineering would be much simpler. It can be seen that the code related to mining is in/opt/bindirectory. Guessing that Python is used as a glue language, it should be used for configuration and judgment, and finally call an ELF to implement the function. There may be a program with a name containing miner as the main function program. From the Chinese comments,yf是Yunfanmeans ~.~.
It is necessary to praise the developers for their serious and responsible attitude. If those malicious software authors also had such a good conscience, reverse engineering would be much simpler. It can be seen that the code related to mining is in/opt/bindirectory. Guessing that Python is used as a glue language, it should be used for configuration and judgment, and finally call an ELF to implement the function. There may be a program with a name containing miner as the main function program. From the Chinese comments,yf是Yunfanmeans ~.~.
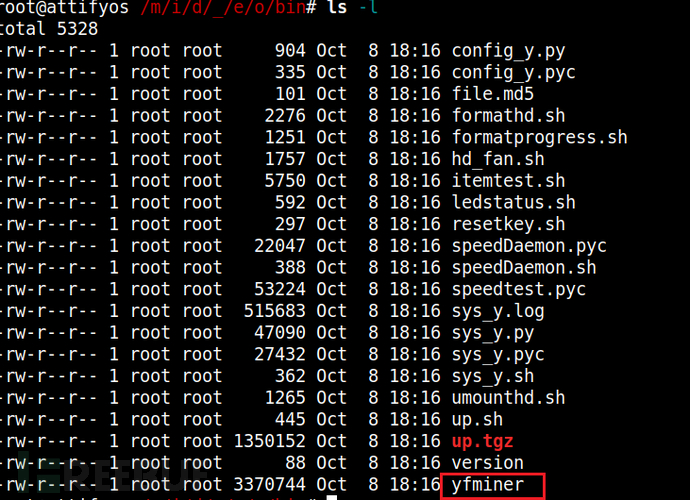
Let's analyze the process briefly.
Firstlysys_y.pyNoticed that it appears multiple timesspeedDaemon,yfminer、andfungeekerThree process calls, for functional processes.
def killalls():
try:
os.system("kill -9 `ps -ef|grep speedDaemon |grep -v grep|awk '{print $2}'`")
os.system("kill -9 `ps -ef|grep yfminer |grep -v grep|awk '{print $2}'`")
os.system("kill -9 `ps -ef|grep fungeeker |grep -v grep|awk '{print $2}'`")
The function logic is very simple, the flowchart is as follows:

mainFunction loop callPrepareStart
def main():
signal.signal(signal.SIGINT, quit)
signal.signal(signal.SIGTERM, quit)
if((datetime.datetime.now()).strftime('%Y') == "1970"):
sys.exit(0)
while True:
LOG("NOTICE", "MAIN", "\\n****************************\\n********** START! **********\\n****************************")
try:
PrepareStart()
except:
pass
time.sleep(3600)
PrepareStartCollect information and judge whether it is a mining version before callingSysStartStart the main function, inMultiMngfunction before starting the thread mentionedspeedDaemon,yfminer、andfungeekerThree processes. Some key code is as follows:
def PrepareStart():
...
try:
LineIp = GetIp()
MacAddr = GetMacAddr()
...
try:
MacAddr = MacAddr.replace(':', '')
...
SPACE = get_space()
...
while(0 == YDig):
PrNode = prove_sncode() #Verify if the cat disk is a mining version
if(PrNode == 0):
YDig = 1
continue
elif(PrNode == -1):
killalls()
else:#((PrNode == -3) or (PrNode == -2))
YDig = 2
continue
SysStart()
def SysStart():
...
MultiMng()
while True:
if(1 != YDig):
if(dignum > 480):
PrNode = prove_sncode() #Verify if the cat disk is a mining version
if(0 == PrNode):
YDig = 1
dignum = 0
dignum += 1
def MultiMng():
for i in range(MUL_NUB):
thds.append(work_thd_mng(MAGE_QUE))
...
class work_thd_mng (threading.Thread):
...
Execute()
EchSys2()
del_logfiles()
#Check if the program is started
def Execute():
...
try:
if((SpeedCode == 2) and (Opened == 1)): #0:speedtest 1:yunfan 2:fengxing
FX_GetMsg()
if((SpeedCode == 1) and (Opened == 1)): #0:speedtest 1:yunfan 2:fengxing
#YF_GetMsg()
YF_GetMsg2()
...
sys_fx = commands.getoutput('ps -ef|grep fungeeker|grep -v grep | wc -l')
sys_yf = commands.getoutput('ps -ef|grep yfminer|grep -v grep | wc -l')
sys_sp = commands.getoutput('ps -ef|grep speedDaemon.sh|grep -v grep | wc -l')
Below is the analysis of the three key processes, through the analysis we find outspeedDaemonandfungeekerJust an auxiliary, all are scripts, the scope is limited and will not be elaborated further, the core program is stillyfminer。
# file yfminer
yfminer: ELF 64-bit LSB executable, ARM aarch64, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux-aarch64.so.1, for GNU/Linux 3.7.0, BuildID[sha1]=3415dd67a0e45f0f3286001f43406b9abff3b912, stripped
This ARM64 program is still very smooth to open, basically automatically recognized:
 Find the main function,
Find the main function,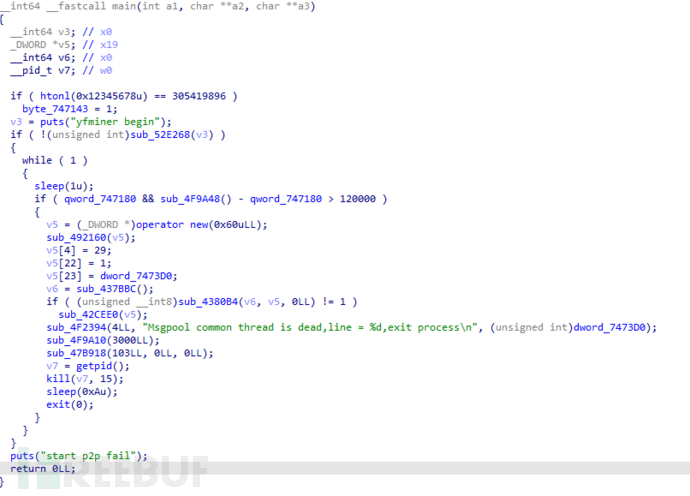
A general analysis of the process:
__int64 __fastcall main(int a1, char **a2, char **a3)
{
__int64 v3; // x0
_DWORD *v5; // x19
__int64 v6; // x0
__pid_t v7; // w0
if ( htonl(0x12345678u) == 305419896 ) // Byte order judgment
byte_747143 = 1;
v3 = puts("yfminer begin"); // Program starts
if ( !(unsigned int)sub_52E268(v3) ) // Key function
{
while ( 1 ) // Infinite loop, for time to meet conditions
{
sleep(1u);
if ( qword_747180 && sub_4F9A48() - qword_747180 > 120000 ) // clock_gettime detection
{
v5 = (_DWORD *)operator new(0x60uLL);
sub_492160(v5);
v5[4] = 29;
v5[22] = 1;
v5[23] = dword_7473D0;
v6 = sub_437BBC();
if ( (unsigned __int8)sub_4380B4(v6, v5, 0LL) != 1 )
sub_42CEE0(v5);
sub_4F2394(4LL, "Msgpool common thread is dead,line = %d,exit process\\n", (unsigned int)dword_7473D0); //sprintf
sub_4F9A10(3000LL); // usleep 1000 * 3000LL
sub_47B918(103LL, 0LL, 0LL);
v7 = getpid(); // 获取当前 pid
kill(v7, 15); // kill pid
sleep(0xAu);
exit(0);
}
}
}
puts("start p2p fail"); // 程序启动失败
return 0LL;
}
main函数十分简洁,给人以程序逻辑很简单的假象,毕竟是个p2p node程序,逻辑并没有那么简单;只管看来while循环是主功能,实际sub_52E268才是关键函数。
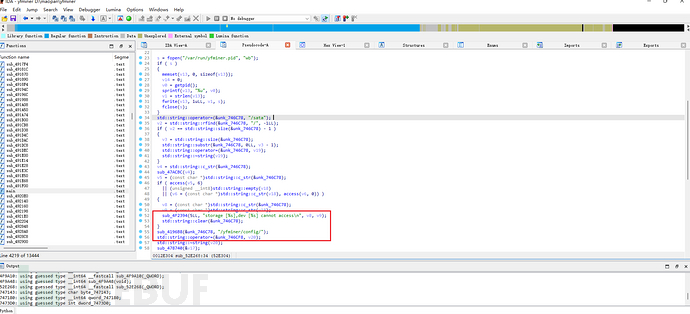 上图为sub_52E268伪代码,红框部分为检测与配置。
上图为sub_52E268伪代码,红框部分为检测与配置。
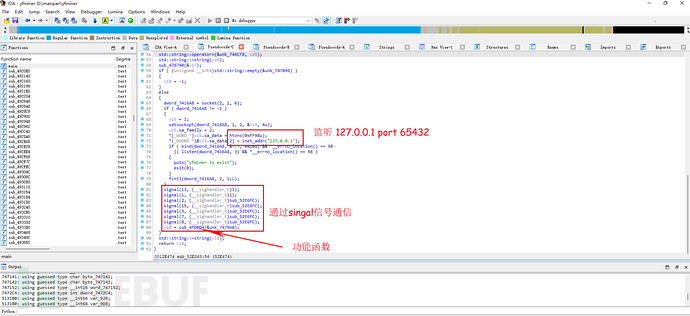
然后通过signal信号实现通信,sub_52E6FC为处理函数,用到的信号解释如下:
SIGHUP 1 Term 终端的挂断或进程死亡
SIGINT 2 Term 来自键盘的中断信号
SIGQUIT 3 Core 来自键盘的离开信号
SIGFPE 8 Core 浮点例外
SIGKILL 9 Term 杀死
SIGPIPE 13 Term 管道损坏:向一个没有读进程的管道写数据
SIGTERM 15 Term 终止
由于后续程序过程较复杂,下主要分析sub_4FDBD4函数一条主线回溯(被调用→调用):
sub_513100→sub_512FF8→sub_4FFF78→sub_4FDBD4
在sub_4FDBD4函数中值得注意的是各类实例的初始化:
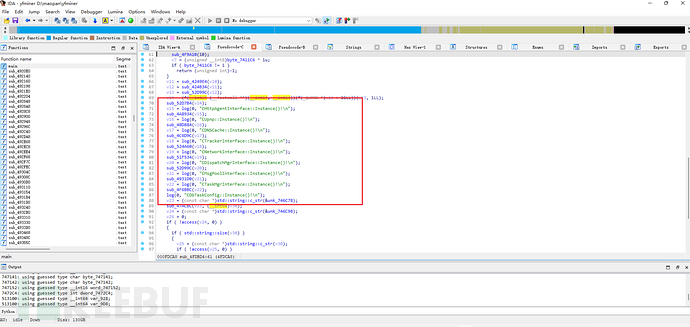 vtable结构如下,红框内为成员函数列表:
vtable结构如下,红框内为成员函数列表:
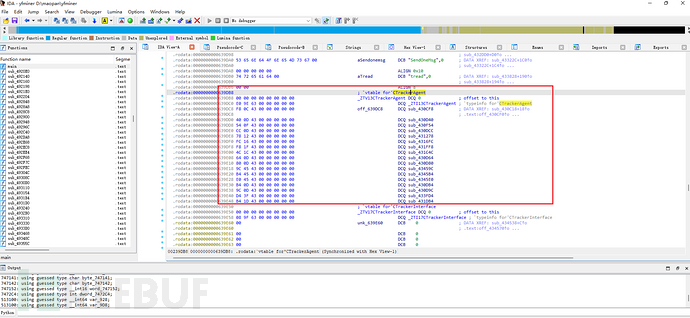 略过 sub_512FF8,sub_4FFF78直接看复杂的 sub_513100函数:
略过 sub_512FF8,sub_4FFF78直接看复杂的 sub_513100函数:
 是p2p node的一些功能具体实现:
是p2p node的一些功能具体实现:
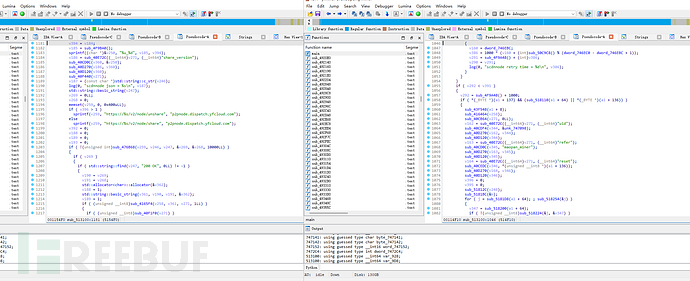
猜测激励机制是根据绑定账号具体贡献在云端计算反馈,由于已经失(pao)效(lu)这里就不作分析。
- 挖矿木马的检测与防范
猫盘所谓的挖矿与想象的并不相同,但仍借此荒腔走板聊一聊挖矿木马的检测防范。
由于虚拟货币(价格)兴起,挖矿木马、勒索软件也随之流行,成为网络安全重要威胁之一。挖矿木马主要分有以下几种形式:
可执行文件:存储在机器上的典型恶意程序,通常通过设置计划任务或修改注册表项实现持久化。
Based on the browser: Mining malware using JavaScript (or similar technology) is executed in the browser.
Fileless mining malware: Utilizing legitimate tools such as PowerShell to execute mining tasks in the memory of the machine, with characteristics such as non-landing and difficult detection.
Mining malwareMain characteristicsThere are:
Abnormal network connections: Connect to mining-related websites or IP addresses.
Special protocol traffic characteristics: Communication process uses a special communication protocol, so there are certain network communication characteristics.
Extremely high CPU or GPU resource usage: Server response speed is slow, crashes, or frequently restarts, device temperature is too high.
From the characteristics, it can be combined with threat intelligence to detect network connections, such as some mining pool address detection:
Bitcoin:mine.btcguid.com:8332,pit.deepbit.net:8332...
Monero:xmr-us-east1.nanopool.org:14444,pool.supportxmr.com:7777,pool.minexmr.com:5555...
Detect protocol keywords:
id,method,jsonrpc,params,result,login,pass,agent,job_id,seed_hashblob,target,rigid...
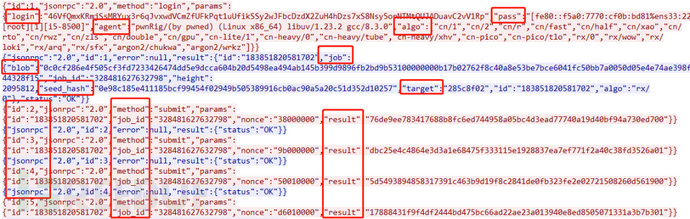 Detect host resources:
Detect host resources:
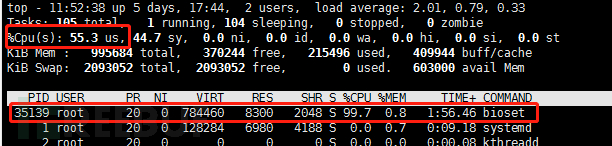 Preventive measures are also some of the old generation's points:Patch vulnerabilities;Strong password;Strong protection;Be cautious onlineUnfortunately, this is also very difficult.
Preventive measures are also some of the old generation's points:Patch vulnerabilities;Strong password;Strong protection;Be cautious onlineUnfortunately, this is also very difficult.
0x03 Make a summary
This article focuses on the firmware flashing and reverse engineering of the mining program of the cat drive. The equipment is relatively high-end, with both hardware and firmware being standardized, so the difficulty and value of reverse engineering are not high, and it is more suitable for development. In the research of the mining process, it did not use the guessed IPFS method to implement, but used the device to make a traditional p2p node, and then the income was converted into BTC and returned to the users. At the end of the article, it mentioned the detection and prevention of mining malware in a very abrupt manner. Every time it mentions Web3, it is hoped that there will be both joy and sorrow, and finally laugh a little, see you next device (lan).

0x04 References
Ultra detailed cat drive Docker application clarification
Hunzi says|One minute to understand Bitcoin & blockchain
Cat drive--Blockchain technology implementation, mining version unboxing review
https://github.com/hanwckf/build-catdrive
Cat drive (mining version) - Blockchain hard drive that can earn Bitcoin
Cat drive launches mining version application distributed storage technology
评论已关闭