

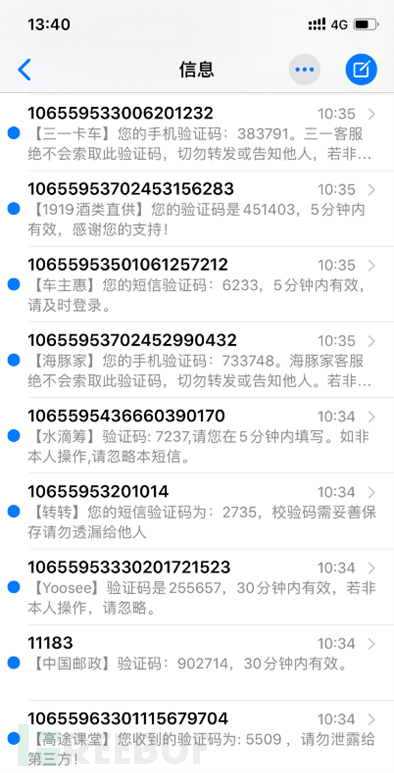
Well, actually, I have no impression of whether the weather was sunny that day, I only remember that my younger brother said in WeChat that there was something fun for me to try... Unexpectedly, my phone kept receiving various strange SMS messages, most of which were from common company registration codes and verification codes. It turned out that he had found a 'Death Call' platform on the Internet and wanted to study it, but was at a loss for a harassment target, so he targeted me. Even worse, when I realized it, I immediately called him, but he didn't answer my phone, causing me to keep receiving spam messages and unable to use my phone normally.

Turn back to April 2020, Mr. Huang from Qingyuan City, Guangdong, took a ride-sharing car to travel. After arriving at the destination, Mr. Huang found that the fare was too high, far exceeding his usual experience. He suspected that the driver 'detoured'. Therefore, Mr. Huang had an argument with the driver, and they parted ways without a smile. After returning home, Mr. Huang gave the driver a bad review on the platform. Not long after, Mr. Huang's phone started receiving strange calls, and the frequency was getting higher and higher. In just half a day, there were tens of thousands of different numbers calling in, causing his phone to be directly 'overloaded', severely affecting his daily life and work. It was only after reporting to the police that the problem was solved.
In July 2020, Ms. Yin also encountered a similar problem. Her phone received more than 40 SMS verification codes during working hours, and the sending platforms were all regular enterprises and institutions, including Alipay, Tencent Technology, Amap, Dianping, Sina Weibo, Ele.me, Alibaba, Meituan, Ctrip, 58.com, and Baoguo. Ms. Yin suspected that she was maliciously harassed.
Baidu search keywords: 'Death Call', it can be seen that there are still a large number of related events happening this year:
Explanation of terms
'Death Call' (Call you to death) refers to the use of low-cost Internet phones as a calling platform, which adopts advanced international Internet phone communication technology for information (voice phone calls, SMS) bombing. The following screenshot is from a news article this year, from which it can be seen that the systems exploited by the black industry are not only for small and medium-sized enterprises, but also include banks, government agencies and other units.
Note: The news content and screenshots are from the Internet and are for reference only.
Attack principle
Complete attack flowchart of 'Death Call'
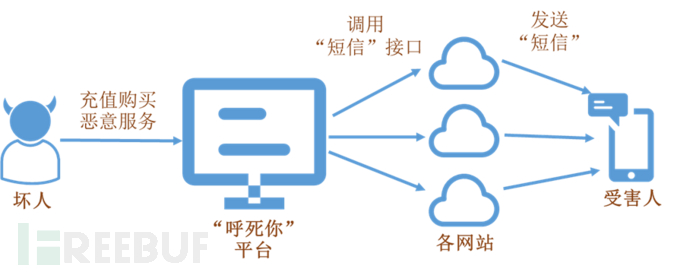
1. The bad guys recharge and purchase malicious services, and specify the 'target' victim's mobile phone number;
2. The 'Suicide Call' platform simulates normal SMS call requests from various websites, calls the 'SMS' interface of various websites, and requests to send SMS to the 'target' mobile phone number;
3. Websites handle client requests and send SMS to the victim's mobile phone;
4. The victim's mobile phone receives a number of SMS messages and is subjected to SMS bombing attacks.
Send SMS via SMS interface
The most important step in the 'Suicide Call' attack process is: calling the SMS interface to send SMS, which is relatively simple in technical implementation, and just the following few steps:
① Find pages that can send SMS verification codes.
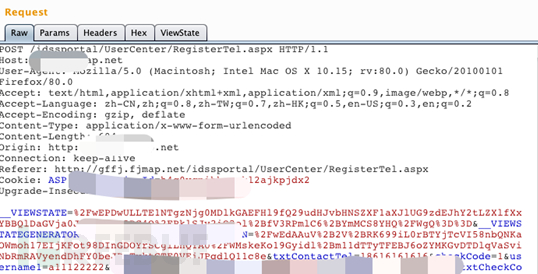
② Construct HTTP packet request, example:
#!/usr/bin/python
import httplib
headers = {
"User-Agent": Mozilla/5.0 "(compatible; MSIE 9.0;XXXXXX)",
"Referer": " ",
"Host": " "}
params = " "
con = httplib.HTTPConnection("www.abc.com") #
con.request("POST", "/send_mes.jsp?xxxxxx=aaaaa",params,headers)
response = con.getresponse()
con.close() |
③ Using a single machine IP or distributed proxy IP, frequently calling the SMS sending interface.

Enterprise Hazards
To prevent such network attacks, coordination efforts are needed among public security organs, operators, and enterprises. Over the years, the Ministry of Public Security's 'Clean Network Action' has been continuously cracking down on such criminal offenses. In June 2018, under the coordination of the Ministry of Public Security, the Public Security Bureaus of Guangzhou, Shenzhen, and 15 other cities in Guangdong Province organized simultaneous operations across multiple provinces and cities in Sichuan, Henan, and Guangdong to crack down on the black and gray industrial chain of 'Suicide Call' through the 'Security Network 2' special operation. They successfully eliminated two 'Suicide Call' criminal gangs, namely 'Crazy Cloud Call' and 'Puke Call'. For example, in April this year, the Guangdong Cyber Police cracked down on a criminal gang led by Xiong, who used the internet to manufacture and sell 'Suicide Call' software. In addition, operators have always held a zero-tolerance attitude towards 'Suicide Call' platforms.

Figure: News screenshot
Although the Ministry of Public Security's 'Clean Network Action' has eliminated a number of 'Suicide Call' platforms, operators are also committed to actively defending against such attack behaviors. However, driven by interests, 'Suicide Call' platforms tend to be more changeable and concealed, and malicious harassment will not be completely eliminated.
Therefore, enterprises also need to do a good job in network security protection. Good network security work for enterprise systems can not only prevent resources from being maliciously exploited, but also fulfill the obligations stipulated in the Cybersecurity Law, and also avoid affecting the company's brand image.

How Enterprises Can Defend Against
For such attack behavior, general defense measures such as the following are generally considered:
First, add a graphic verification code at the point where the system sends SMS verification codes to prevent high-frequency calls from machines;
Second, detect malicious interface call behavior and block it in a timely manner.
At present, most enterprise customer platforms can increase verification methods themselves, but there is no effective way to detect such malicious call behavior. In response to this pain point, enterprises can consider using SIEM, SOC, situation awareness platforms, big data analysis platforms, and other means to help implement timely detection functions.
Detect malicious interface call behavior
Here are some detection ideas for security partners. Through analysis, it is found that such attacks have the following common characteristics:
1. A single source IP frequently calls the SMS interface in a short period of time.
2. Different source IPs frequently send requests to the same target mobile phone number in a short period of time.
For the above features, we can adopt the following technical means for detection:
Technical one: configure a special 'business interface' detection rule
① Sort out business interfaces:URLs with SMS sending business points, including but not limited to login entry, password recovery entry, registration entry, order viewing interface, etc.;
② Select data source:web middleware log, full traffic analysis data;
③ Set alert trigger conditions:The same source IP exceeds 10 calls to the same interface within 60 seconds or different source IPs exceed 10 calls to the same mobile phone number within 60 seconds; (set according to specific circumstances);
④ Select alert notification method:You can choose to alert the source IP through email or SMS;
⑤ Linkage processing:Through SOAR or one-click handling and other methods, link and block processing with firewall, WAF, DDoS and other equipment.
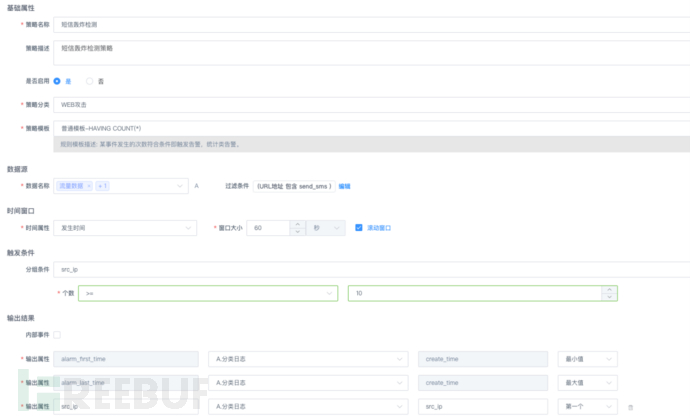
Figure: screenshot of detection rule
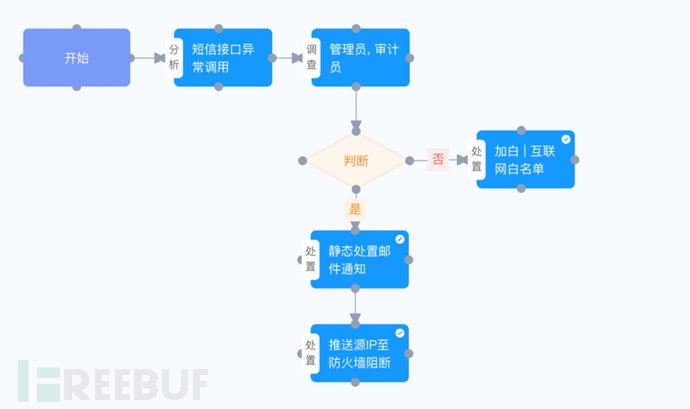
Figure: screenshot of automated orchestration
Technical two: configure a special 'business interface' monitoring instrument panel
① Sort out business interfaces:URLs with SMS sending business points, including but not limited to login entry, password recovery entry, registration entry, order viewing interface, etc.;
② Select data source:web middleware log, full traffic analysis data;
③ Select display chart:Bar charts, pie charts, line charts, and other options are available;
④ Configure display theme:Trend charts of data volume, charts of attack proportion, charts of attack IP distribution, and top N charts of attack events.
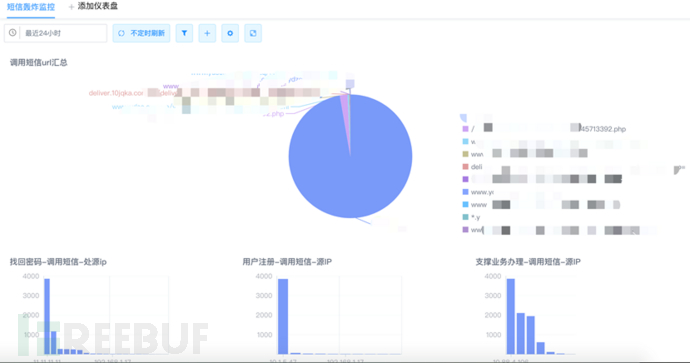
Figure: screenshot of monitoring instrument panel
Written at the end
With the application and popularization of network services, network operators (enterprises) occupy a large amount of social resources and should also assume corresponding obligations. In addition, the Cybersecurity Law also clearly stipulates the obligations of network operators in terms of network operation safety, network product and service safety, key information infrastructure security protection, personal information protection of citizens, and network information security management.
Everyone in society should start with themselves and not purchase such harassment services. Of course, it is also not recommended to download so-called 'death you' software from the internet. Many software programs are not only unusable, but may also be Trojan horse programs that 'sell dogs with sheep's heads', bringing more security risks. Finally, I wish everyone will never encounter the same painful experience as mine!
评论已关闭